Hao Song
EG-ConMix: An Intrusion Detection Method based on Graph Contrastive Learning
Mar 24, 2024



Abstract:As the number of IoT devices increases, security concerns become more prominent. The impact of threats can be minimized by deploying Network Intrusion Detection System (NIDS) by monitoring network traffic, detecting and discovering intrusions, and issuing security alerts promptly. Most intrusion detection research in recent years has been directed towards the pair of traffic itself without considering the interrelationships among them, thus limiting the monitoring of complex IoT network attack events. Besides, anomalous traffic in real networks accounts for only a small fraction, which leads to a severe imbalance problem in the dataset that makes algorithmic learning and prediction extremely difficult. In this paper, we propose an EG-ConMix method based on E-GraphSAGE, incorporating a data augmentation module to fix the problem of data imbalance. In addition, we incorporate contrastive learning to discern the difference between normal and malicious traffic samples, facilitating the extraction of key features. Extensive experiments on two publicly available datasets demonstrate the superior intrusion detection performance of EG-ConMix compared to state-of-the-art methods. Remarkably, it exhibits significant advantages in terms of training speed and accuracy for large-scale graphs.
A Federated Parameter Aggregation Method for Node Classification Tasks with Different Graph Network Structures
Mar 24, 2024
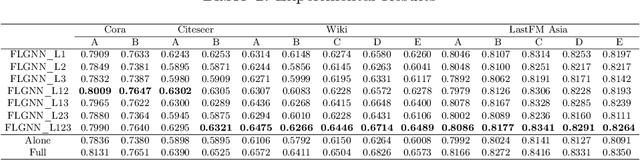
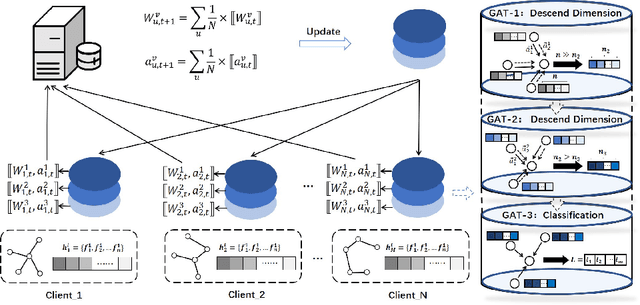
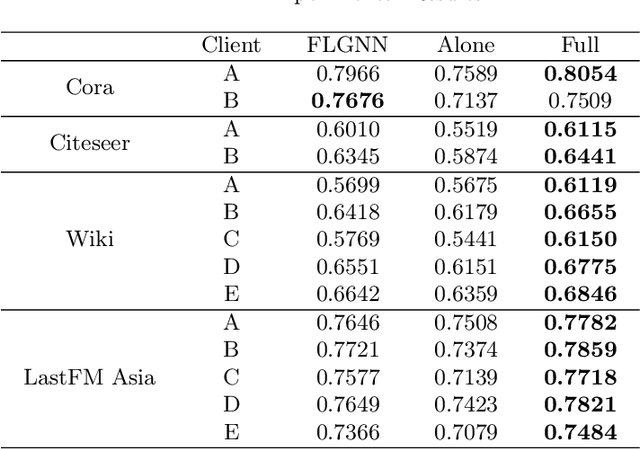
Abstract:Over the past few years, federated learning has become widely used in various classical machine learning fields because of its collaborative ability to train data from multiple sources without compromising privacy. However, in the area of graph neural networks, the nodes and network structures of graphs held by clients are different in many practical applications, and the aggregation method that directly shares model gradients cannot be directly applied to this scenario. Therefore, this work proposes a federated aggregation method FLGNN applied to various graph federation scenarios and investigates the aggregation effect of parameter sharing at each layer of the graph neural network model. The effectiveness of the federated aggregation method FLGNN is verified by experiments on real datasets. Additionally, for the privacy security of FLGNN, this paper designs membership inference attack experiments and differential privacy defense experiments. The results show that FLGNN performs good robustness, and the success rate of privacy theft is further reduced by adding differential privacy defense methods.
Target Recognition Algorithm for Monitoring Images in Electric Power Construction Process
Feb 09, 2024



Abstract:To enhance precision and comprehensiveness in identifying targets in electric power construction monitoring video, a novel target recognition algorithm utilizing infrared imaging is explored. This algorithm employs a color processing technique based on a local linear mapping method to effectively recolor monitoring images. The process involves three key steps: color space conversion, color transfer, and pseudo-color encoding. It is designed to accentuate targets in the infrared imaging. For the refined identification of these targets, the algorithm leverages a support vector machine approach, utilizing an optimal hyperplane to accurately predict target types. We demonstrate the efficacy of the algorithm, which achieves high target recognition accuracy in both outdoor and indoor electric power construction monitoring scenarios. It maintains a false recognition rate below 3% across various environments.
Classifier Calibration: How to assess and improve predicted class probabilities: a survey
Dec 20, 2021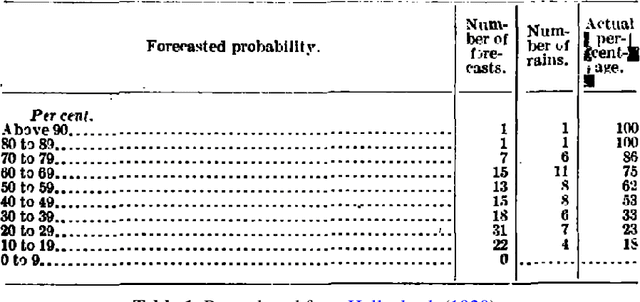
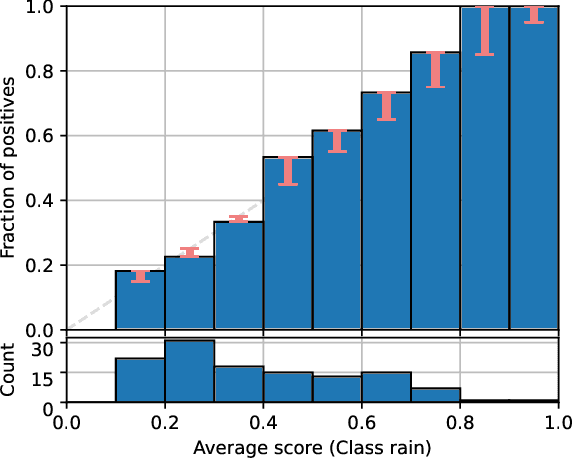
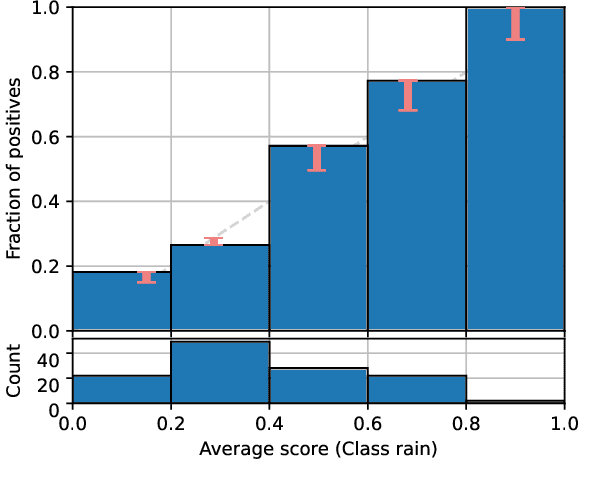
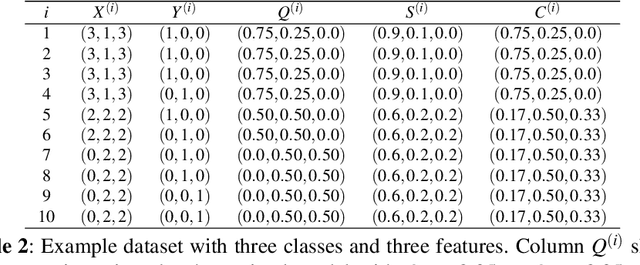
Abstract:This paper provides both an introduction to and a detailed overview of the principles and practice of classifier calibration. A well-calibrated classifier correctly quantifies the level of uncertainty or confidence associated with its instance-wise predictions. This is essential for critical applications, optimal decision making, cost-sensitive classification, and for some types of context change. Calibration research has a rich history which predates the birth of machine learning as an academic field by decades. However, a recent increase in the interest on calibration has led to new methods and the extension from binary to the multiclass setting. The space of options and issues to consider is large, and navigating it requires the right set of concepts and tools. We provide both introductory material and up-to-date technical details of the main concepts and methods, including proper scoring rules and other evaluation metrics, visualisation approaches, a comprehensive account of post-hoc calibration methods for binary and multiclass classification, and several advanced topics.
Turbulence-Resilient Coherent Free-Space Optical Communications using Automatic Power-Efficient Pilot-Assisted Optoelectronic Beam Mixing of Many Modes
Jan 25, 2021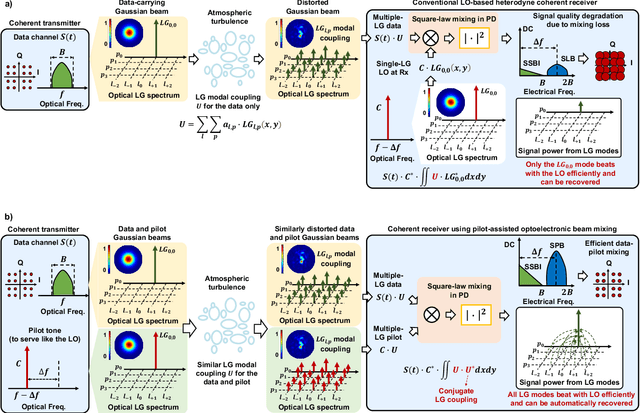


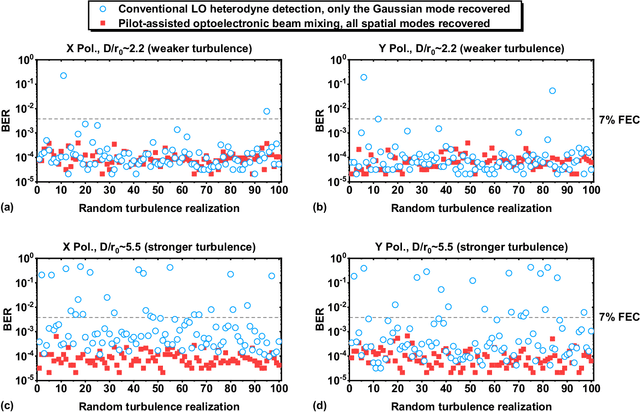
Abstract:Atmospheric turbulence generally limits free-space optical (FSO) communications, and this problem is severely exacerbated when implementing highly sensitive and spectrally efficient coherent detection. Specifically, turbulence induces power coupling from the transmitted Gaussian mode to higher-order Laguerre-Gaussian (LG) modes, resulting in a significant decrease of the power that mixes with a single-mode local oscillator (LO). Instead, we transmit a frequency-offset Gaussian pilot tone along with the data signal, such that both experience similar turbulence and modal power coupling. Subsequently, the photodetector (PD) optoelectronically mixes all corresponding pairs of the beams' modes. During mixing, a conjugate of the turbulence experienced by the pilot tone is automatically generated and compensates the turbulence experienced by the data, and nearly all orders of the same corresponding modes efficiently mix. We demonstrate a 12-Gbit/s 16-quadrature-amplitude-modulation (16-QAM) polarization-multiplexed (PolM) FSO link that exhibits resilience to emulated turbulence. Experimental results for turbulence D/r_0~5.5 show up to ~20 dB reduction in the mixing power loss over a conventional coherent receiver. Therefore, our approach automatically recovers nearly all the captured data power to enable high-performance coherent FSO systems.
A Multi-oriented Chinese Keyword Spotter Guided by Text Line Detection
Jan 06, 2020



Abstract:Chinese keyword spotting is a challenging task as there is no visual blank for Chinese words. Different from English words which are split naturally by visual blanks, Chinese words are generally split only by semantic information. In this paper, we propose a new Chinese keyword spotter for natural images, which is inspired by Mask R-CNN. We propose to predict the keyword masks guided by text line detection. Firstly, proposals of text lines are generated by Faster R-CNN;Then, text line masks and keyword masks are predicted by segmentation in the proposals. In this way, the text lines and keywords are predicted in parallel. We create two Chinese keyword datasets based on RCTW-17 and ICPR MTWI2018 to verify the effectiveness of our method.
Beyond temperature scaling: Obtaining well-calibrated multiclass probabilities with Dirichlet calibration
Oct 28, 2019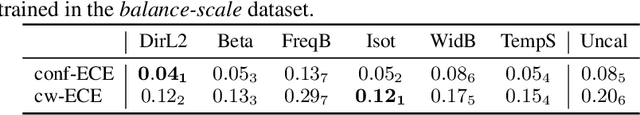
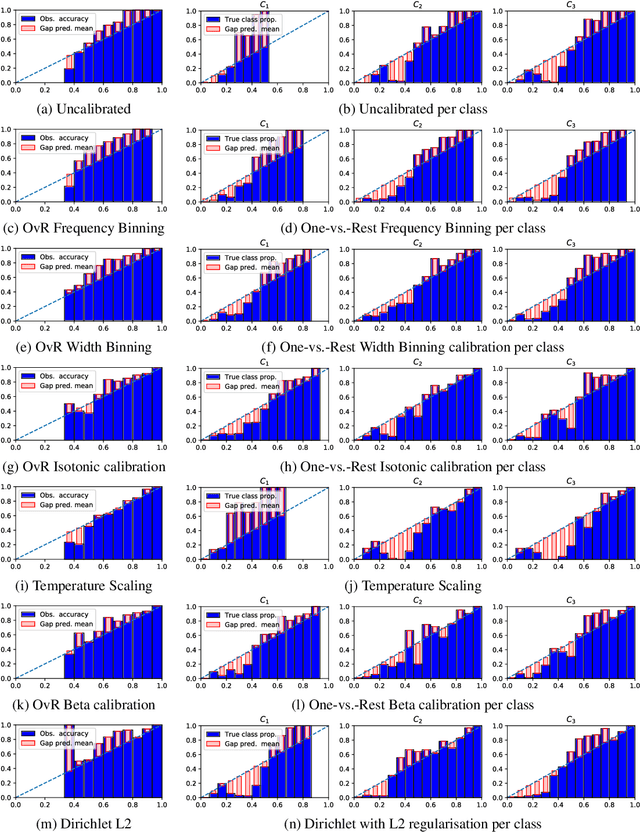
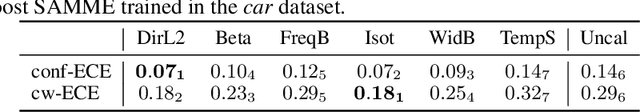
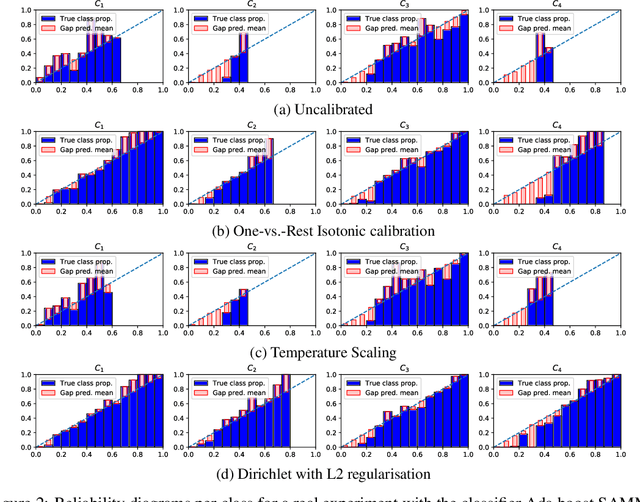
Abstract:Class probabilities predicted by most multiclass classifiers are uncalibrated, often tending towards over-confidence. With neural networks, calibration can be improved by temperature scaling, a method to learn a single corrective multiplicative factor for inputs to the last softmax layer. On non-neural models the existing methods apply binary calibration in a pairwise or one-vs-rest fashion. We propose a natively multiclass calibration method applicable to classifiers from any model class, derived from Dirichlet distributions and generalising the beta calibration method from binary classification. It is easily implemented with neural nets since it is equivalent to log-transforming the uncalibrated probabilities, followed by one linear layer and softmax. Experiments demonstrate improved probabilistic predictions according to multiple measures (confidence-ECE, classwise-ECE, log-loss, Brier score) across a wide range of datasets and classifiers. Parameters of the learned Dirichlet calibration map provide insights to the biases in the uncalibrated model.
HyperStream: a Workflow Engine for Streaming Data
Aug 07, 2019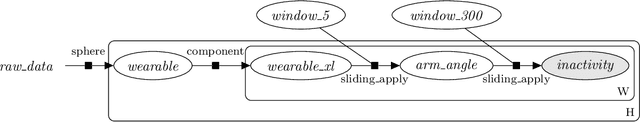
Abstract:This paper describes HyperStream, a large-scale, flexible and robust software package, written in the Python language, for processing streaming data with workflow creation capabilities. HyperStream overcomes the limitations of other computational engines and provides high-level interfaces to execute complex nesting, fusion, and prediction both in online and offline forms in streaming environments. HyperStream is a general purpose tool that is well-suited for the design, development, and deployment of Machine Learning algorithms and predictive models in a wide space of sequential predictive problems. Source code, installation instructions, examples, and documentation can be found at: https://github.com/IRC-SPHERE/HyperStream.
Distribution Calibration for Regression
May 15, 2019


Abstract:We are concerned with obtaining well-calibrated output distributions from regression models. Such distributions allow us to quantify the uncertainty that the model has regarding the predicted target value. We introduce the novel concept of distribution calibration, and demonstrate its advantages over the existing definition of quantile calibration. We further propose a post-hoc approach to improving the predictions from previously trained regression models, using multi-output Gaussian Processes with a novel Beta link function. The proposed method is experimentally verified on a set of common regression models and shows improvements for both distribution-level and quantile-level calibration.
Distributive Dynamic Spectrum Access through Deep Reinforcement Learning: A Reservoir Computing Based Approach
Oct 28, 2018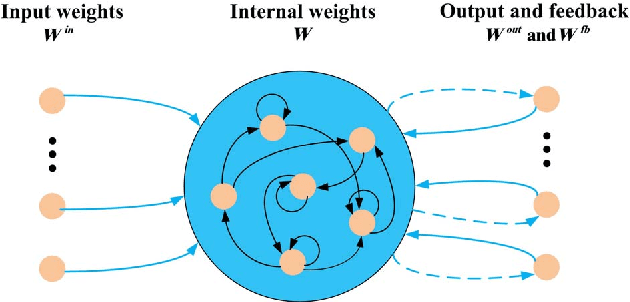



Abstract:Dynamic spectrum access (DSA) is regarded as an effective and efficient technology to share radio spectrum among different networks. As a secondary user (SU), a DSA device will face two critical problems: avoiding causing harmful interference to primary users (PUs), and conducting effective interference coordination with other secondary users. These two problems become even more challenging for a distributed DSA network where there is no centralized controllers for SUs. In this paper, we investigate communication strategies of a distributive DSA network under the presence of spectrum sensing errors. To be specific, we apply the powerful machine learning tool, deep reinforcement learning (DRL), for SUs to learn "appropriate" spectrum access strategies in a distributed fashion assuming NO knowledge of the underlying system statistics. Furthermore, a special type of recurrent neural network (RNN), called the reservoir computing (RC), is utilized to realize DRL by taking advantage of the underlying temporal correlation of the DSA network. Using the introduced machine learning-based strategy, SUs could make spectrum access decisions distributedly relying only on their own current and past spectrum sensing outcomes. Through extensive experiments, our results suggest that the RC-based spectrum access strategy can help the SU to significantly reduce the chances of collision with PUs and other SUs. We also show that our scheme outperforms the myopic method which assumes the knowledge of system statistics, and converges faster than the Q-learning method when the number of channels is large.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge