Petar Popovski
Department of Electronic Systems, Aalborg University, Denmark
Interference Detection and Exploitation for Multi-User Radar Sensing
Jan 29, 2026Abstract:Integrated sensing and communication is a key feature in next-generation wireless networks, enabling joint data transmission and environmental radar sensing on shared spectrum. In multi-user scenarios, simultaneous transmissions cause mutual interference on overlapping frequencies, leading to spurious target detections and degraded sensing accuracy. This paper proposes an interference detection and exploitation algorithm for sensing using spectrally interleaved orthogonal frequency division multiplexing. A statistically rigorous procedure is introduced to detect interference while controlling the familywise error rate. We propose an algorithm that estimates the angle by exploiting interference, while estimating the delay by avoiding the interference. Numerical experiments demonstrate that the proposed method reliably detects interference, and that the delay and angle estimation error approaches the Cramér-Rao lower bound.
Tunable Gaussian Pulse for Delay-Doppler ISAC
Dec 16, 2025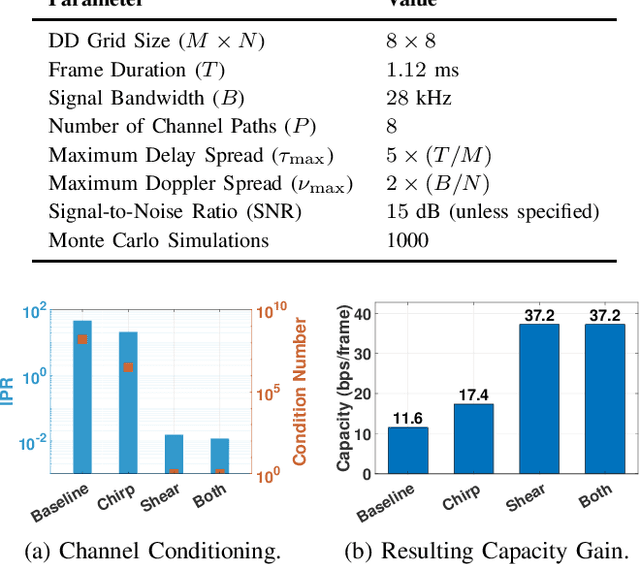
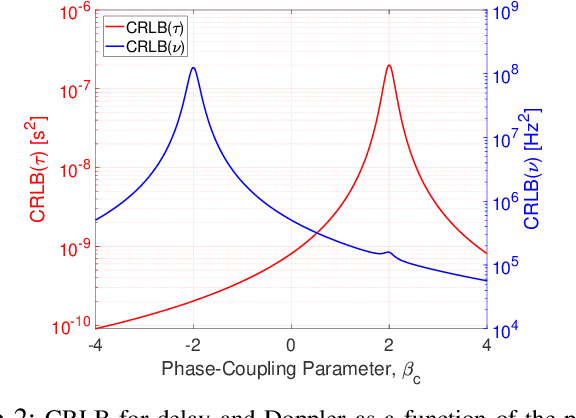
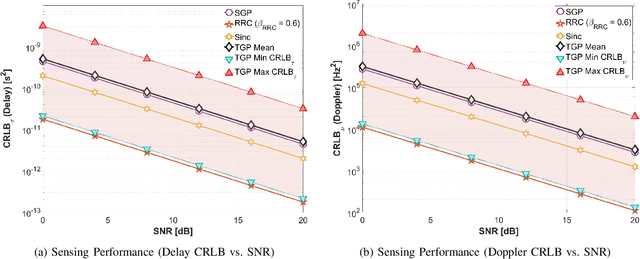
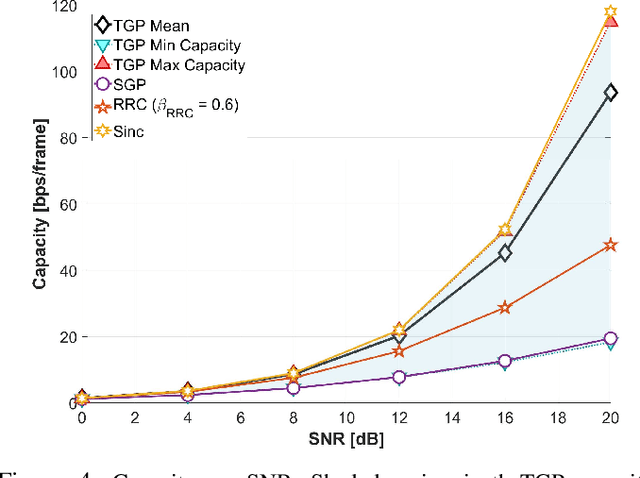
Abstract:Integrated sensing and communication (ISAC) for next-generation networks targets robust operation under high mobility and high Doppler spread, leading to severe inter-carrier interference (ICI) in systems based on orthogonal frequency-division multiplexing (OFDM) waveforms. Delay--Doppler (DD)-domain ISAC offers a more robust foundation under high mobility, but it requires a suitable DD-domain pulse-shaping filter. The prevailing DD pulse designs are either communication-centric or static, which limits adaptation to non-stationary channels and diverse application demands. To address this limitation, this paper introduces the tunable Gaussian pulse (TGP), a DD-native, analytically tunable pulse shape parameterized by its aspect ratio \( γ\), chirp rate \( α_c \), and phase coupling \( β_c \). On the sensing side, we derive closed-form Cramér--Rao lower bounds (CRLBs) that map \( (γ,α_c,β_c) \) to fundamental delay and Doppler precision. On the communications side, we show that \( α_c \) and \( β_c \) reshape off-diagonal covariance, and thus inter-symbol interference (ISI), without changing received power, isolating capacity effects to interference structure rather than power loss. A comprehensive trade-off analysis demonstrates that the TGP spans a flexible operational region from the high capacity of the Sinc pulse to the high precision of the root raised cosine (RRC) pulse. Notably, TGP attains near-RRC sensing precision while retaining over \( 90\% \) of Sinc's maximum capacity, achieving a balanced operating region that is not attainable by conventional static pulse designs.
Temporal Windows of Integration for Multisensory Wireless Systems as Enablers of Physical AI
Dec 10, 2025Abstract:Physical artificial intelligence (AI) refers to the AI that interacts with the physical world in real time. Similar to multisensory perception, Physical AI makes decisions based on multimodal updates from sensors and devices. Physical AI thus operates with a finite spatial footprint of its sensory tributaries. The multimodal updates traverse heterogeneous and unreliable paths, involving wireless links. Throughput or latency guarantees do not ensure correct decision-making, as misaligned, misordered, or stale inputs still yield wrong inferences. Preserving decision-time coherence hinges on three timing primitives at the network-application interface: (i) simultaneity, a short coincidence window that groups measurements as co-temporal, (ii) causality, path-wise delivery that never lets a consequence precede its precursor, and (iii) usefulness, a validity horizon that drops information too stale to influence the current action. In this work, we focus on usefulness and adopt temporal window of integration (TWI)-Causality: the TWI enforces decision-time usefulness by assuming path-wise causal consistency and cross-path simultaneity are handled upstream. We model end-to-end path delay as the sum of sensing/propagation, computation, and access/transmission latencies, and formulate network design as minimizing the validity horizon under a delivery reliability constraint. In effect, this calibrates delay-reliability budgets for a timing-aware system operating over sensors within a finite spatial footprint. The joint choice of horizon and per-path reliability is cast as a convex optimization problem, solved to global optimality to obtain the minimal horizon and per-path allocation of reliability. This is compared favourably to a benchmark based on uniform-after-threshold allocation. Overall, this study contributes to timing-aware Physical AI in next-generation networks.
Dynamic Downlink-Uplink Spectrum Sharing between Terrestrial and Non-Terrestrial Networks
Nov 11, 2025Abstract:6G networks are expected to integrate low Earth orbit satellites to ensure global connectivity by extending coverage to underserved and remote regions. However, the deployment of dense mega-constellations introduces severe interference among satellites operating over shared frequency bands. This is, in part, due to the limited flexibility of conventional frequency division duplex (FDD) systems, where fixed bands for downlink (DL) and uplink (UL) transmissions are employed. In this work, we propose dynamic re-assignment of FDD bands for improved interference management in dense deployments and evaluate the performance gain of this approach. To this end, we formulate a joint optimization problem that incorporates dynamic band assignment, user scheduling, and power allocation in both directions. This non-convex mixed integer problem is solved using a combination of equivalence transforms, alternating optimization, and state-of-the-art industrial-grade mixed integer solvers. Numerical results demonstrate that the proposed approach of dynamic FDD band assignment significantly enhances system performance over conventional FDD, achieving up to 94\% improvement in throughput in dense deployments.
Multilayer Non-Terrestrial Networks with Spectrum Access aided by Beyond-Diagonal RIS
Oct 06, 2025Abstract:In this work, we study a multi-user NTN in which a satellite serves as the primary network and a high-altitude platform station (HAPS) operates as the secondary network, acting as a cognitive radio. To reduce the cost, complexity, and power consumption of conventional antenna arrays, we equip the HAPS with a transmissive BD-RIS antenna front end. We then formulate a joint optimization problem for the BD-RIS phase response and the HAPS transmit power allocation under strict per-user interference temperature constraints. To tackle the resulting highly nonconvex problem, we propose an alternating-optimization framework: the power-allocation subproblem admits a closed-form, water-filling-type solution derived from the Karush-Kuhn-Tucker (KKT) conditions, while the BD-RIS configuration is refined via Riemannian manifold optimization. Simulation results show significant gains in data rate and interference suppression over diagonal RIS-assisted benchmarks, establishing BD-RIS as a promising enabler for future multilayer NTNs.
6G Resilience -- White Paper
Sep 10, 2025
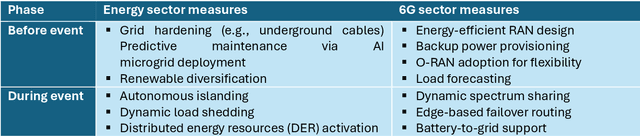

Abstract:6G must be designed to withstand, adapt to, and evolve amid prolonged, complex disruptions. Mobile networks' shift from efficiency-first to sustainability-aware has motivated this white paper to assert that resilience is a primary design goal, alongside sustainability and efficiency, encompassing technology, architecture, and economics. We promote resilience by analysing dependencies between mobile networks and other critical systems, such as energy, transport, and emergency services, and illustrate how cascading failures spread through infrastructures. We formalise resilience using the 3R framework: reliability, robustness, resilience. Subsequently, we translate this into measurable capabilities: graceful degradation, situational awareness, rapid reconfiguration, and learning-driven improvement and recovery. Architecturally, we promote edge-native and locality-aware designs, open interfaces, and programmability to enable islanded operations, fallback modes, and multi-layer diversity (radio, compute, energy, timing). Key enablers include AI-native control loops with verifiable behaviour, zero-trust security rooted in hardware and supply-chain integrity, and networking techniques that prioritise critical traffic, time-sensitive flows, and inter-domain coordination. Resilience also has a techno-economic aspect: open platforms and high-quality complementors generate ecosystem externalities that enhance resilience while opening new markets. We identify nine business-model groups and several patterns aligned with the 3R objectives, and we outline governance and standardisation. This white paper serves as an initial step and catalyst for 6G resilience. It aims to inspire researchers, professionals, government officials, and the public, providing them with the essential components to understand and shape the development of 6G resilience.
On the Deployment of Multiple Radio Stripes for Large-Scale Near-Field RF Wireless Power Transfer
Aug 29, 2025Abstract:This paper investigates the deployment of radio stripe systems for indoor radio-frequency (RF) wireless power transfer (WPT) in line-of-sight near-field scenarios. The focus is on environments where energy demand is concentrated in specific areas, referred to as 'hotspots', spatial zones with higher user density or consistent energy requirements. We formulate a joint clustering and radio stripe deployment problem that aims to maximize the minimum received power across all hotspots. To address the complexity, we decouple the problem into two stages: i) clustering for assigning radio stripes to hotspots based on their spatial positions and near-field propagation characteristics, and ii) antenna element placement optimization. In particular, we propose four radio stripe deployment algorithms. Two are based on general successive convex approximation (SCA) and signomial programming (SGP) methods. The other two are shape-constrained solutions where antenna elements are arranged along either straight lines or regular polygons, enabling simpler deployment. Numerical results show that the proposed clustering method converges effectively, with Chebyshev initialization significantly outperforming random initialization. The optimized deployments consistently outperform baseline benchmarks across a wide range of frequencies and radio stripe lengths, while the polygon-shaped deployment achieves better performance compared to other approaches. Meanwhile, the line-shaped deployment demonstrates an advantage under high boresight gain settings, benefiting from increased spatial diversity and broader angular coverage.
Quantum-Accelerated Wireless Communications: Concepts, Connections, and Implications
Jun 25, 2025Abstract:Quantum computing is poised to redefine the algorithmic foundations of communication systems. While quantum superposition and entanglement enable quadratic or exponential speedups for specific problems, identifying use cases where these advantages yield engineering benefits is, however, still nontrivial. This article presents the fundamentals of quantum computing in a style familiar to the communications society, outlining the current limits of fault-tolerant quantum computing and uncovering a mathematical harmony between quantum and wireless systems, which makes the topic more enticing to wireless researchers. Based on a systematic review of pioneering and state-of-the-art studies, we distill common design trends for the research and development of quantum-accelerated communication systems and highlight lessons learned. The key insight is that classical heuristics can sharpen certain quantum parameters, underscoring the complementary strengths of classical and quantum computing. This article aims to catalyze interdisciplinary research at the frontier of quantum information processing and future communication systems.
Reinforcement Learning-Based Policy Optimisation For Heterogeneous Radio Access
Jun 18, 2025Abstract:Flexible and efficient wireless resource sharing across heterogeneous services is a key objective for future wireless networks. In this context, we investigate the performance of a system where latency-constrained internet-of-things (IoT) devices coexist with a broadband user. The base station adopts a grant-free access framework to manage resource allocation, either through orthogonal radio access network (RAN) slicing or by allowing shared access between services. For the IoT users, we propose a reinforcement learning (RL) approach based on double Q-Learning (QL) to optimise their repetition-based transmission strategy, allowing them to adapt to varying levels of interference and meet a predefined latency target. We evaluate the system's performance in terms of the cumulative distribution function of IoT users' latency, as well as the broadband user's throughput and energy efficiency (EE). Our results show that the proposed RL-based access policies significantly enhance the latency performance of IoT users in both RAN Slicing and RAN Sharing scenarios, while preserving desirable broadband throughput and EE. Furthermore, the proposed policies enable RAN Sharing to be energy-efficient at low IoT traffic levels, and RAN Slicing to be favourable under high IoT traffic.
Multi-User Beamforming with Deep Reinforcement Learning in Sensing-Aided Communication
May 09, 2025Abstract:Mobile users are prone to experience beam failure due to beam drifting in millimeter wave (mmWave) communications. Sensing can help alleviate beam drifting with timely beam changes and low overhead since it does not need user feedback. This work studies the problem of optimizing sensing-aided communication by dynamically managing beams allocated to mobile users. A multi-beam scheme is introduced, which allocates multiple beams to the users that need an update on the angle of departure (AoD) estimates and a single beam to the users that have satisfied AoD estimation precision. A deep reinforcement learning (DRL) assisted method is developed to optimize the beam allocation policy, relying only upon the sensing echoes. For comparison, a heuristic AoD-based method using approximated Cram\'er-Rao lower bound (CRLB) for allocation is also presented. Both methods require neither user feedback nor prior state evolution information. Results show that the DRL-assisted method achieves a considerable gain in throughput than the conventional beam sweeping method and the AoD-based method, and it is robust to different user speeds.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge