Qihui Wu
Corresponding author
Prompt-Driven Low-Altitude Edge Intelligence: Modular Agents and Generative Reasoning
Feb 15, 2026Abstract:The large artificial intelligence models (LAMs) show strong capabilities in perception, reasoning, and multi-modal understanding, and can enable advanced capabilities in low-altitude edge intelligence. However, the deployment of LAMs at the edge remains constrained by some fundamental limitations. First, tasks are rigidly tied to specific models, limiting the flexibility. Besides, the computational and memory demands of full-scale LAMs exceed the capacity of most edge devices. Moreover, the current inference pipelines are typically static, making it difficult to respond to real-time changes of tasks. To address these challenges, we propose a prompt-to-agent edge cognition framework (P2AECF), enabling the flexible, efficient, and adaptive edge intelligence. Specifically, P2AECF transforms high-level semantic prompts into executable reasoning workflows through three key mechanisms. First, the prompt-defined cognition parses task intent into abstract and model-agnostic representations. Second, the agent-based modular execution instantiates these tasks using lightweight and reusable cognitive agents dynamically selected based on current resource conditions. Third, the diffusion-controlled inference planning adaptively constructs and refines execution strategies by incorporating runtime feedback and system context. In addition, we illustrate the framework through a representative low-altitude intelligent network use case, showing its ability to deliver adaptive, modular, and scalable edge intelligence for real-time low-altitude aerial collaborations.
Knowledge-Driven 3D Semantic Spectrum Map: KE-VQ-Transformer Based UAV Semantic Communication and Map Completion
Dec 24, 2025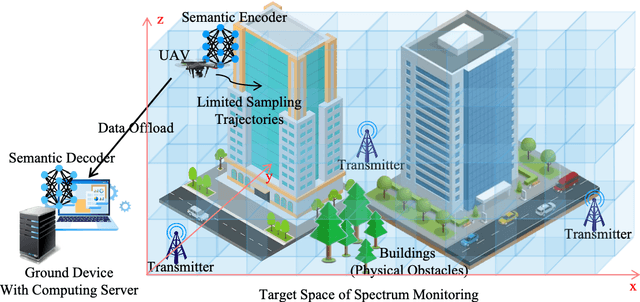
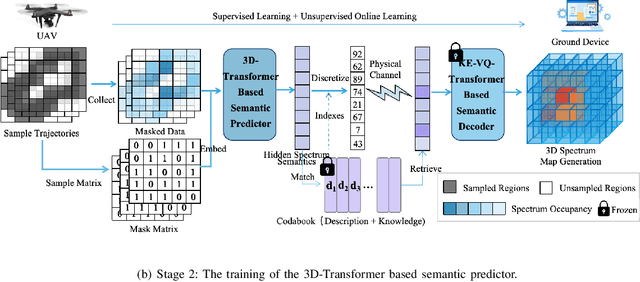
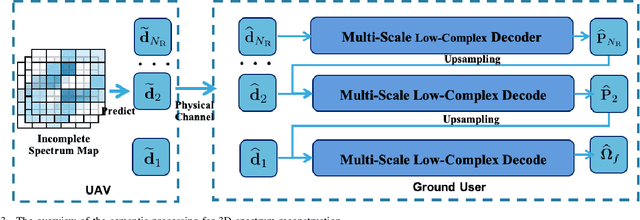
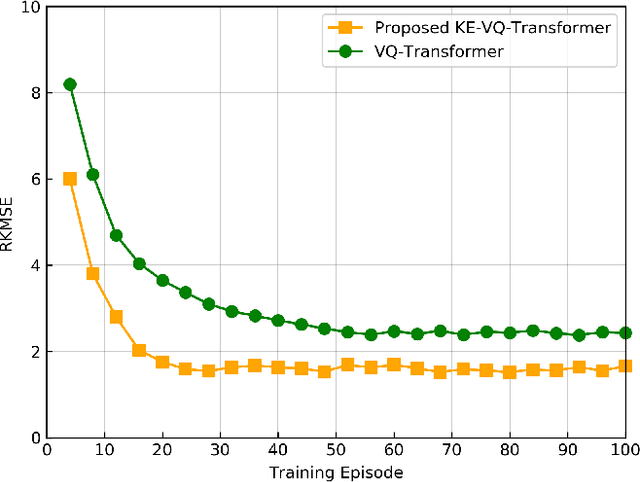
Abstract:Artificial intelligence (AI)-native three-dimensional (3D) spectrum maps are crucial in spectrum monitoring for intelligent communication networks. However, it is challenging to obtain and transmit 3D spectrum maps in a spectrum-efficient, computation-efficient, and AI-driven manner, especially under complex communication environments and sparse sampling data. In this paper, we consider practical air-to-ground semantic communications for spectrum map completion, where the unmanned aerial vehicle (UAV) measures the spectrum at spatial points and extracts the spectrum semantics, which are then utilized to complete spectrum maps at the ground device. Since statistical machine learning can easily be misled by superficial data correlations with the lack of interpretability, we propose a novel knowledge-enhanced semantic spectrum map completion framework with two expert knowledge-driven constraints from physical signal propagation models. This framework can capture the real-world physics and avoid getting stuck in the mindset of superficial data distributions. Furthermore, a knowledge-enhanced vector-quantized Transformer (KE-VQ-Transformer) based multi-scale low-complex intelligent completion approach is proposed, where the sparse window is applied to avoid ultra-large 3D attention computation, and the multi-scale design improves the completion performance. The knowledge-enhanced mean square error (KMSE) and root KMSE (RKMSE) are introduced as novel metrics for semantic spectrum map completion that jointly consider the numerical precision and physical consistency with the signal propagation model, based on which a joint offline and online training method is developed with supervised and unsupervised knowledge loss. The simulation demonstrates that our proposed scheme outperforms the state-of-the-art benchmark schemes in terms of RKMSE.
Distributed Multi-Task Learning for Joint Wireless Signal Enhancement and Recognition
Sep 19, 2025Abstract:Wireless signal recognition (WSR) is crucial in modern and future wireless communication networks since it aims to identify the properties of the received signal in a no-collaborative manner. However, it is challenging to accurately classify signals in low signal-to-noise ratio (SNR) conditions and distributed network settings. In this paper, we propose a novel distributed multi-task learning framework for joint wireless signal enhancement and recognition (WSER), addressing the crucial need for non-collaborative signal identification in modern wireless networks. Our approach integrates a wireless signal enhancement and recognition network (WSERNet) with FedProx+, an enhanced federated learning algorithm designed for heterogeneous data distributions. Specifically, WSERNet leverages an asymmetric convolution block (ACBlock) to capture long-range dependencies in the input signal and improve the performance of the deep learning model. FedProx+ introduces a proximal term to the loss function to encourage the model updates to be closer to the previous model, enhancing the convergence speed and robustness of federated learning. Extensive experiments demonstrate the effectiveness of the proposed framework for joint WSER, achieving superior performance compared to state-of-the-art methods under both centralized and distributed settings including independent and identically distributed (IID) and non-IID data distributions.
* accepted by Transactions on Cognitive Communications and Networking
Explainable Deep Learning Based Adversarial Defense for Automatic Modulation Classification
Sep 19, 2025Abstract:Deep learning (DL) has been widely applied to enhance automatic modulation classification (AMC). However, the elaborate AMC neural networks are susceptible to various adversarial attacks, which are challenging to handle due to the generalization capability and computational cost. In this article, an explainable DL based defense scheme, called SHapley Additive exPlanation enhanced Adversarial Fine-Tuning (SHAP-AFT), is developed in the perspective of disclosing the attacking impact on the AMC network. By introducing the concept of cognitive negative information, the motivation of using SHAP for defense is theoretically analyzed first. The proposed scheme includes three stages, i.e., the attack detection, the information importance evaluation, and the AFT. The first stage indicates the existence of the attack. The second stage evaluates contributions of the received data and removes those data positions using negative Shapley values corresponding to the dominating negative information caused by the attack. Then the AMC network is fine-tuned based on adversarial adaptation samples using the refined received data pattern. Simulation results show the effectiveness of the Shapley value as the key indicator as well as the superior defense performance of the proposed SHAP-AFT scheme in face of different attack types and intensities.
Dynamic Trajectory Optimization and Power Control for Hierarchical UAV Swarms in 6G Aerial Access Network
Aug 26, 2025



Abstract:Unmanned aerial vehicles (UAVs) can serve as aerial base stations (BSs) to extend the ubiquitous connectivity for ground users (GUs) in the sixth-generation (6G) era. However, it is challenging to cooperatively deploy multiple UAV swarms in large-scale remote areas. Hence, in this paper, we propose a hierarchical UAV swarms structure for 6G aerial access networks, where the head UAVs serve as aerial BSs, and tail UAVs (T-UAVs) are responsible for relay. In detail, we jointly optimize the dynamic deployment and trajectory of UAV swarms, which is formulated as a multi-objective optimization problem (MOP) to concurrently minimize the energy consumption of UAV swarms and GUs, as well as the delay of GUs. However, the proposed MOP is a mixed integer nonlinear programming and NP-hard to solve. Therefore, we develop a K-means and Voronoi diagram based area division method, and construct Fermat points to establish connections between GUs and T-UAVs. Then, an improved non-dominated sorting whale optimization algorithm is proposed to seek Pareto optimal solutions for the transformed MOP. Finally, extensive simulations are conducted to verify the performance of proposed algorithms by comparing with baseline mechanisms, resulting in a 50% complexity reduction.
Spectrum Prediction in the Fractional Fourier Domain with Adaptive Filtering
Aug 25, 2025Abstract:Accurate spectrum prediction is crucial for dynamic spectrum access (DSA) and resource allocation. However, due to the unique characteristics of spectrum data, existing methods based on the time or frequency domain often struggle to separate predictable patterns from noise. To address this, we propose the Spectral Fractional Filtering and Prediction (SFFP) framework. SFFP first employs an adaptive fractional Fourier transform (FrFT) module to transform spectrum data into a suitable fractional Fourier domain, enhancing the separability of predictable trends from noise. Subsequently, an adaptive Filter module selectively suppresses noise while preserving critical predictive features within this domain. Finally, a prediction module, leveraging a complex-valued neural network, learns and forecasts these filtered trend components. Experiments on real-world spectrum data show that the SFFP outperforms leading spectrum and general forecasting methods.
Remote ID Based UAV Collision Avoidance Optimization for Low-Altitude Airspace Safety
Aug 11, 2025Abstract:With the rapid development of unmanned aerial vehicles (UAVs), it is paramount to ensure safe and efficient operations in open airspaces. The remote identification (Remote ID) is deemed an effective real-time UAV monitoring system by the federal aviation administration, which holds potentials for enabling inter-UAV communications. This paper deeply investigates the application of Remote ID for UAV collision avoidance while minimizing communication delays. First, we propose a Remote ID based distributed multi-UAV collision avoidance (DMUCA) framework to support the collision detection, avoidance decision-making, and trajectory recovery. Next, the average transmission delays for Remote ID messages are analyzed, incorporating the packet reception mechanisms and packet loss due to interference. The optimization problem is formulated to minimize the long-term average communication delay, where UAVs can flexibly select the Remote ID protocol to enhance the collision avoidance performance. To tackle the problem, we design a multi-agent deep Q-network based adaptive communication configuration algorithm, allowing UAVs to autonomously learn the optimal protocol configurations in dynamic environments. Finally, numerical results verify the feasibility of the proposed DMUCA framework, and the proposed mechanism can reduce the average delay by 32% compared to the fixed protocol configuration.
Joint Resource Optimization Over Licensed and Unlicensed Spectrum in Spectrum Sharing UAV Networks Against Jamming Attacks
Jul 23, 2025Abstract:Unmanned aerial vehicle (UAV) communication is of crucial importance in realizing heterogeneous practical wireless application scenarios. However, the densely populated users and diverse services with high data rate demands has triggered an increasing scarcity of UAV spectrum utilization. To tackle this problem, it is promising to incorporate the underutilized unlicensed spectrum with the licensed spectrum to boost network capacity. However, the openness of unlicensed spectrum makes UAVs susceptible to security threats from potential jammers. Therefore, a spectrum sharing UAV network coexisting with licensed cellular network and unlicensed Wi-Fi network is considered with the anti-jamming technique in this paper. The sum rate maximization of the secondary network is studied by jointly optimizing the transmit power, subchannel allocation, and UAV trajectory. We first decompose the challenging non-convex problem into two subproblems, 1) the joint power and subchannel allocation and 2) UAV trajectory design subproblems. A low-complexity iterative algorithm is proposed in a alternating optimization manner over these two subproblems to solve the formulated problem. Specifically, the Lagrange dual decomposition is exploited to jointly optimize the transmit power and subchannel allocation iteratively. Then, an efficient iterative algorithm capitalizing on successive convex approximation is designed to get a suboptimal solution for UAV trajectory. Simulation results demonstrate that our proposed algorithm can significantly improve the sum transmission rate compared with the benchmark schemes.
Knowledge Graph-Based Explainable and Generalized Zero-Shot Semantic Communications
Jul 03, 2025Abstract:Data-driven semantic communication is based on superficial statistical patterns, thereby lacking interpretability and generalization, especially for applications with the presence of unseen data. To address these challenges, we propose a novel knowledge graph-enhanced zero-shot semantic communication (KGZS-SC) network. Guided by the structured semantic information from a knowledge graph-based semantic knowledge base (KG-SKB), our scheme provides generalized semantic representations and enables reasoning for unseen cases. Specifically, the KG-SKB aligns the semantic features in a shared category semantics embedding space and enhances the generalization ability of the transmitter through aligned semantic features, thus reducing communication overhead by selectively transmitting compact visual semantics. At the receiver, zero-shot learning (ZSL) is leveraged to enable direct classification for unseen cases without the demand for retraining or additional computational overhead, thereby enhancing the adaptability and efficiency of the classification process in dynamic or resource-constrained environments. The simulation results conducted on the APY datasets show that the proposed KGZS-SC network exhibits robust generalization and significantly outperforms existing SC frameworks in classifying unseen categories across a range of SNR levels.
Joint Computation Offloading and Resource Allocation for Uncertain Maritime MEC via Cooperation of UAVs and Vessels
Jun 18, 2025



Abstract:The computation demands from the maritime Internet of Things (MIoT) increase rapidly in recent years, and the unmanned aerial vehicles (UAVs) and vessels based multi-access edge computing (MEC) can fulfill these MIoT requirements. However, the uncertain maritime tasks present significant challenges of inefficient computation offloading and resource allocation. In this paper, we focus on the maritime computation offloading and resource allocation through the cooperation of UAVs and vessels, with consideration of uncertain tasks. Specifically, we propose a cooperative MEC framework for computation offloading and resource allocation, including MIoT devices, UAVs and vessels. Then, we formulate the optimization problem to minimize the total execution time. As for the uncertain MIoT tasks, we leverage Lyapunov optimization to tackle the unpredictable task arrivals and varying computational resource availability. By converting the long-term constraints into short-term constraints, we obtain a set of small-scale optimization problems. Further, considering the heterogeneity of actions and resources of UAVs and vessels, we reformulate the small-scale optimization problem into a Markov game (MG). Moreover, a heterogeneous-agent soft actor-critic is proposed to sequentially update various neural networks and effectively solve the MG problem. Finally, simulations are conducted to verify the effectiveness in addressing computational offloading and resource allocation.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge