Jonathon M. Smereka
Multi-Agent Deep Reinforcement Learning Under Constrained Communications
Jan 22, 2026Abstract:Centralized training with decentralized execution (CTDE) has been the dominant paradigm in multi-agent reinforcement learning (MARL), but its reliance on global state information during training introduces scalability, robustness, and generalization bottlenecks. Moreover, in practical scenarios such as adding/dropping teammates or facing environment dynamics that differ from the training, CTDE methods can be brittle and costly to retrain, whereas distributed approaches allow agents to adapt using only local information and peer-to-peer communication. We present a distributed MARL framework that removes the need for centralized critics or global information. Firstly, we develop a novel Distributed Graph Attention Network (D-GAT) that performs global state inference through multi-hop communication, where agents integrate neighbor features via input-dependent attention weights in a fully distributed manner. Leveraging D-GAT, we develop the distributed graph-attention MAPPO (DG-MAPPO) -- a distributed MARL framework where agents optimize local policies and value functions using local observations, multi-hop communication, and shared/averaged rewards. Empirical evaluation on the StarCraftII Multi-Agent Challenge, Google Research Football, and Multi-Agent Mujoco demonstrates that our method consistently outperforms strong CTDE baselines, achieving superior coordination across a wide range of cooperative tasks with both homogeneous and heterogeneous teams. Our distributed MARL framework provides a principled and scalable solution for robust collaboration, eliminating the need for centralized training or global observability. To the best of our knowledge, DG-MAPPO appears to be the first to fully eliminate reliance on privileged centralized information, enabling agents to learn and act solely through peer-to-peer communication.
Generalized Advantage Estimation for Distributional Policy Gradients
Jul 23, 2025Abstract:Generalized Advantage Estimation (GAE) has been used to mitigate the computational complexity of reinforcement learning (RL) by employing an exponentially weighted estimation of the advantage function to reduce the variance in policy gradient estimates. Despite its effectiveness, GAE is not designed to handle value distributions integral to distributional RL, which can capture the inherent stochasticity in systems and is hence more robust to system noises. To address this gap, we propose a novel approach that utilizes the optimal transport theory to introduce a Wasserstein-like directional metric, which measures both the distance and the directional discrepancies between probability distributions. Using the exponentially weighted estimation, we leverage this Wasserstein-like directional metric to derive distributional GAE (DGAE). Similar to traditional GAE, our proposed DGAE provides a low-variance advantage estimate with controlled bias, making it well-suited for policy gradient algorithms that rely on advantage estimation for policy updates. We integrated DGAE into three different policy gradient methods. Algorithms were evaluated across various OpenAI Gym environments and compared with the baselines with traditional GAE to assess the performance.
Characterizing gaussian mixture of motion modes for skid-steer state estimation
Apr 30, 2025Abstract:Skid-steered wheel mobile robots (SSWMRs) are characterized by the unique domination of the tire-terrain skidding for the robot to move. The lack of reliable friction models cascade into unreliable motion models, especially the reduced ordered variants used for state estimation and robot control. Ensemble modeling is an emerging research direction where the overall motion model is broken down into a family of local models to distribute the performance and resource requirement and provide a fast real-time prediction. To this end, a gaussian mixture model based modeling identification of model clusters is adopted and implemented within an interactive multiple model (IMM) based state estimation. The framework is adopted and implemented for angular velocity as the estimated state for a mid scaled skid-steered wheel mobile robot platform.
Online identification of skidding modes with interactive multiple model estimation
Sep 30, 2024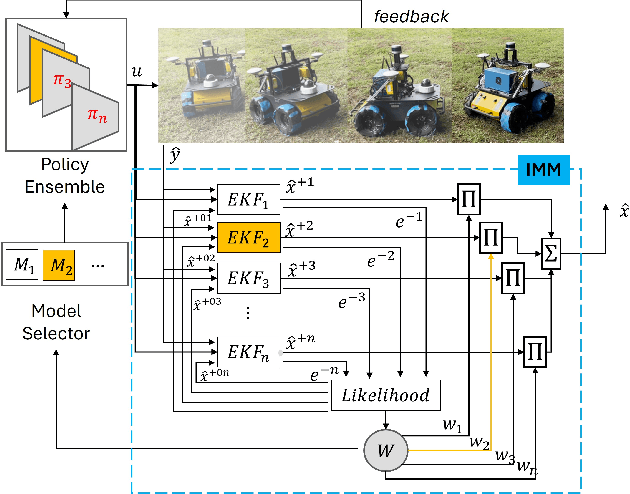
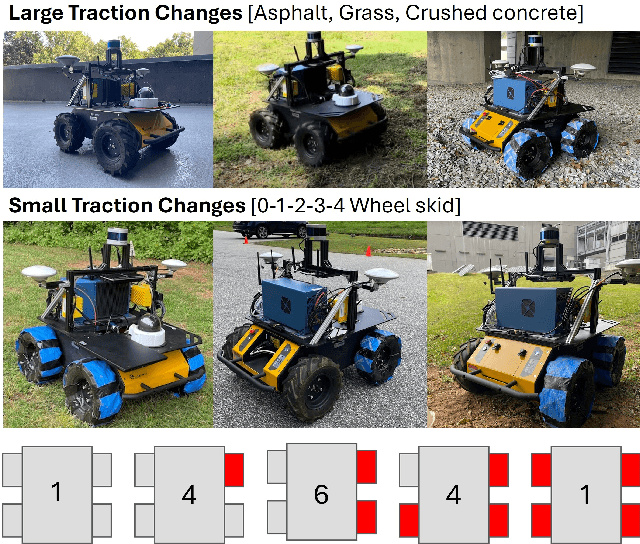
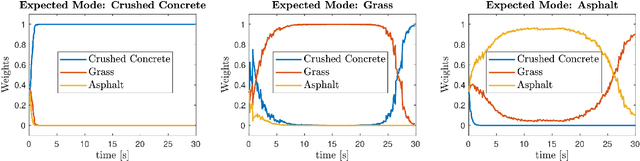
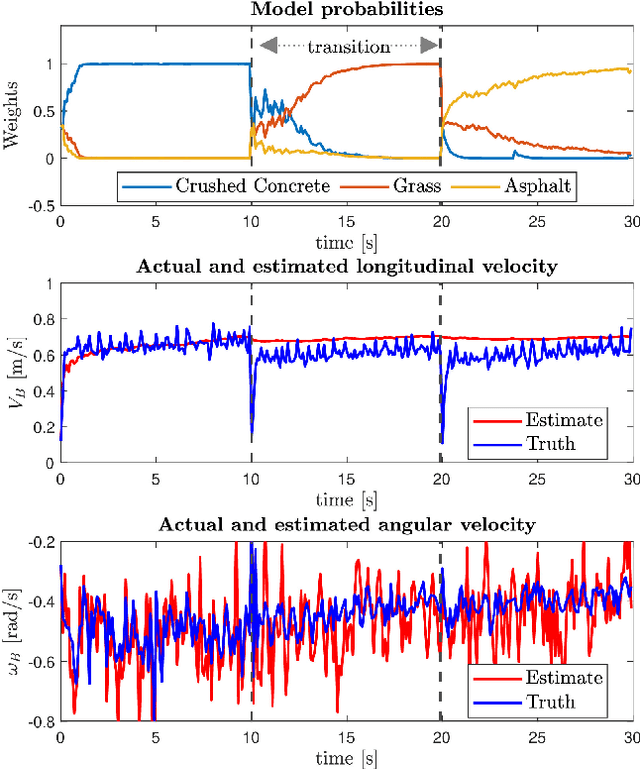
Abstract:Skid-steered wheel mobile robots (SSWMRs) operate in a variety of outdoor environments exhibiting motion behaviors dominated by the effects of complex wheel-ground interactions. Characterizing these interactions is crucial both from the immediate robot autonomy perspective (for motion prediction and control) as well as a long-term predictive maintenance and diagnostics perspective. An ideal solution entails capturing precise state measurements for decisions and controls, which is considerably difficult, especially in increasingly unstructured outdoor regimes of operations for these robots. In this milieu, a framework to identify pre-determined discrete modes of operation can considerably simplify the motion model identification process. To this end, we propose an interactive multiple model (IMM) based filtering framework to probabilistically identify predefined robot operation modes that could arise due to traversal in different terrains or loss of wheel traction.
Reinforcement Learning Compensated Model Predictive Control for Off-road Driving on Unknown Deformable Terrain
Aug 17, 2024Abstract:This study presents an Actor-Critic reinforcement learning Compensated Model Predictive Controller (AC2MPC) designed for high-speed, off-road autonomous driving on deformable terrains. Addressing the difficulty of modeling unknown tire-terrain interaction and ensuring real-time control feasibility and performance, this framework integrates deep reinforcement learning with a model predictive controller to manage unmodeled nonlinear dynamics. We evaluate the controller framework over constant and varying velocity profiles using high-fidelity simulator Project Chrono. Our findings demonstrate that our controller statistically outperforms standalone model-based and learning-based controllers over three unknown terrains that represent sandy deformable track, sandy and rocky track and cohesive clay-like deformable soil track. Despite varied and previously unseen terrain characteristics, this framework generalized well enough to track longitudinal reference speeds with the least error. Furthermore, this framework required significantly less training data compared to purely learning based controller, converging in fewer steps while delivering better performance. Even when under-trained, this controller outperformed the standalone controllers, highlighting its potential for safer and more efficient real-world deployment.
Task Allocation with Load Management in Multi-Agent Teams
Jul 17, 2022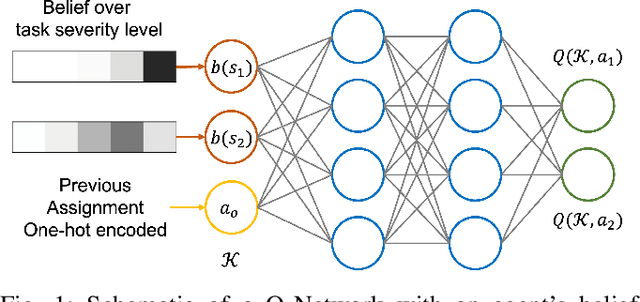
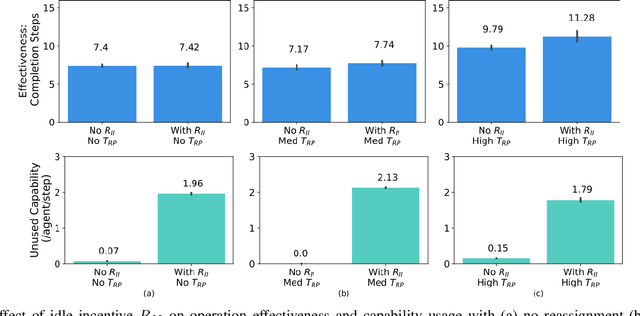
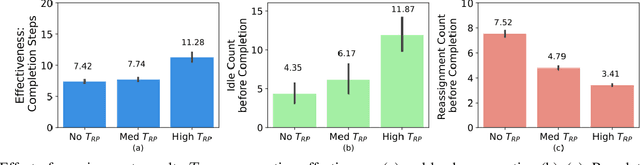
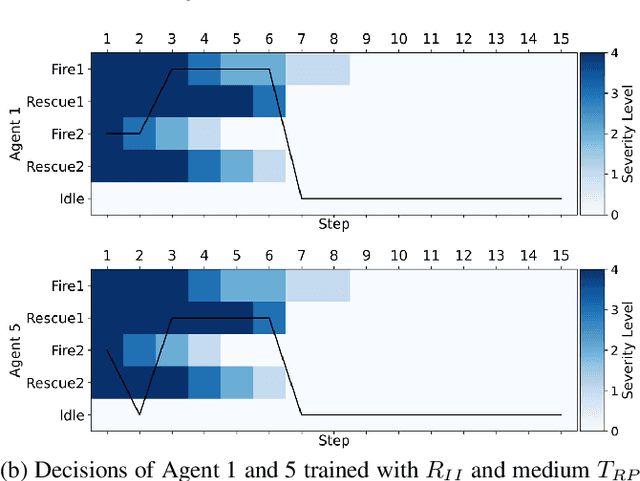
Abstract:In operations of multi-agent teams ranging from homogeneous robot swarms to heterogeneous human-autonomy teams, unexpected events might occur. While efficiency of operation for multi-agent task allocation problems is the primary objective, it is essential that the decision-making framework is intelligent enough to manage unexpected task load with limited resources. Otherwise, operation effectiveness would drastically plummet with overloaded agents facing unforeseen risks. In this work, we present a decision-making framework for multi-agent teams to learn task allocation with the consideration of load management through decentralized reinforcement learning, where idling is encouraged and unnecessary resource usage is avoided. We illustrate the effect of load management on team performance and explore agent behaviors in example scenarios. Furthermore, a measure of agent importance in collaboration is developed to infer team resilience when facing handling potential overload situations.
* 8 pages, 5 figures, 2022 IEEE International Conference on Robotics and Automation
Trust-based Symbolic Motion Planning for Multi-robot Bounding Overwatch
Jan 06, 2022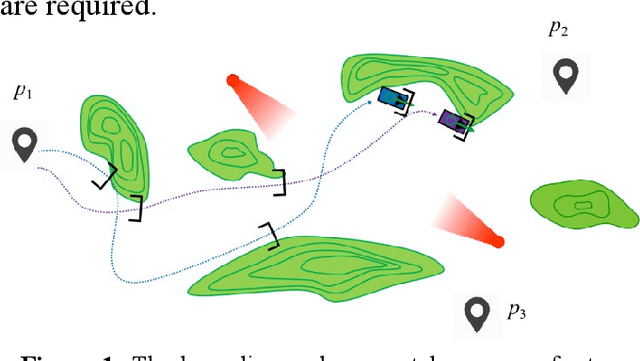
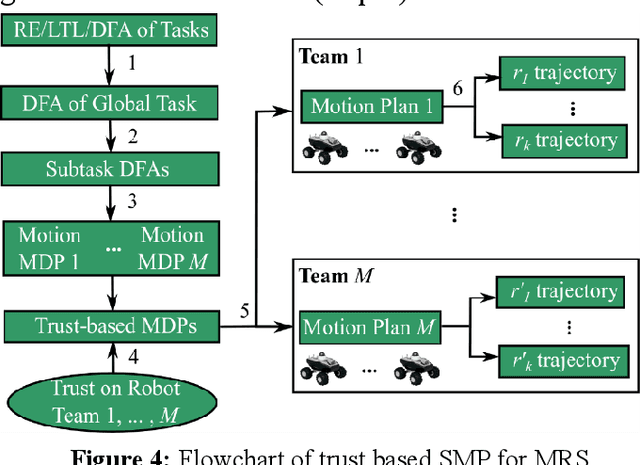
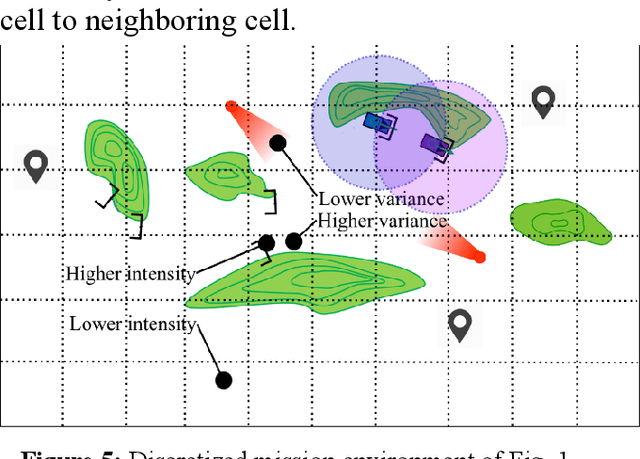
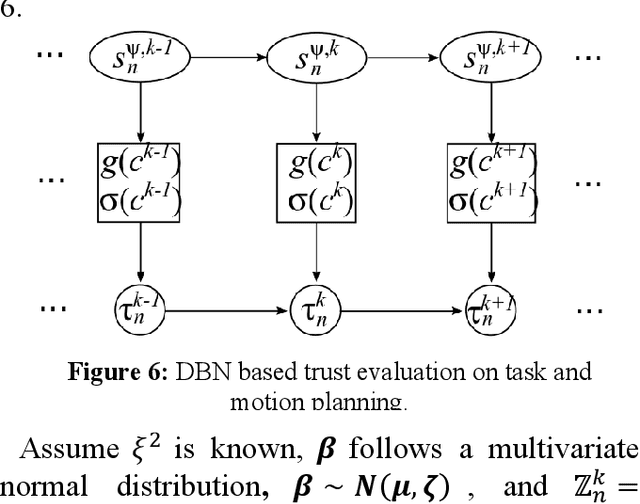
Abstract:Multi-robot bounding overwatch requires timely coordination of robot team members. Symbolic motion planning (SMP) can provide provably correct solutions for robot motion planning with high-level temporal logic task requirements. This paper aims to develop a framework for safe and reliable SMP of multi-robot systems (MRS) to satisfy complex bounding overwatch tasks constrained by temporal logics. A decentralized SMP framework is first presented, which guarantees both correctness and parallel execution of the complex bounding overwatch tasks by the MRS. A computational trust model is then constructed by referring to the traversability and line of sight of robots in the terrain. The trust model predicts the trustworthiness of each robot team's potential behavior in executing a task plan. The most trustworthy task and motion plan is explored with a Dijkstra searching strategy to guarantee the reliability of MRS bounding overwatch. A robot simulation is implemented in ROS Gazebo to demonstrate the effectiveness of the proposed framework.
Bayesian Optimization Based Trustworthiness Model for Multi-robot Bounding Overwatch
Jan 06, 2022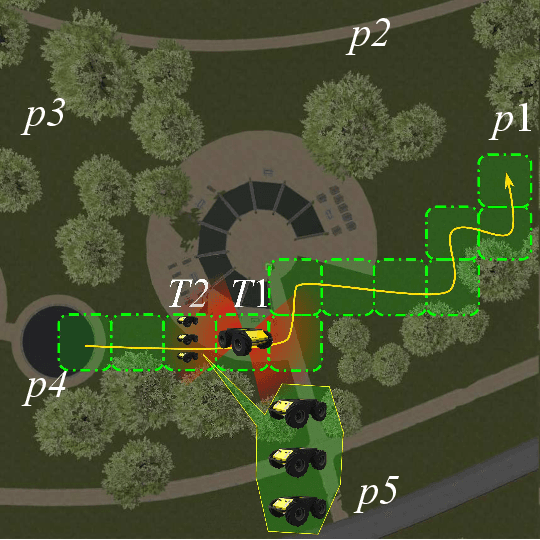
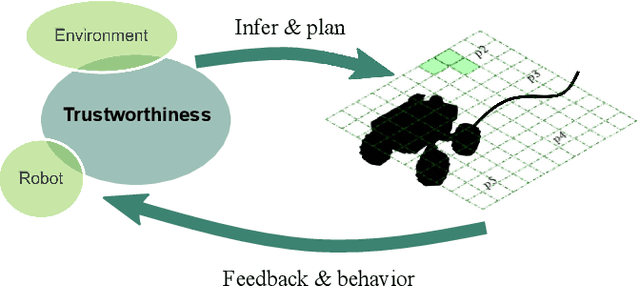
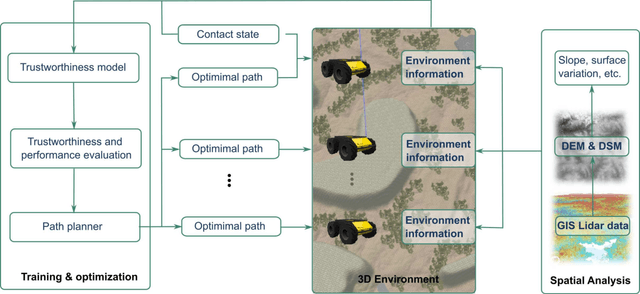
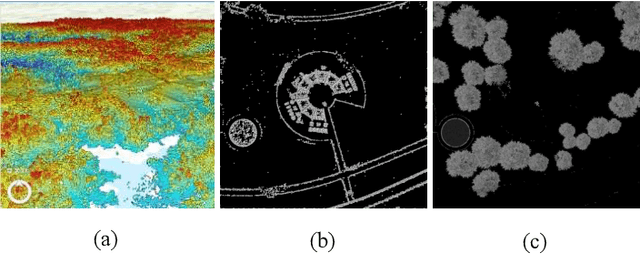
Abstract:In multi-robot system (MRS) bounding overwatch, it is crucial to determine which point to choose for overwatch at each step and whether the robots' positions are trustworthy so that the overwatch can be performed effectively. In this paper, we develop a Bayesian optimization based computational trustworthiness model (CTM) for the MRS to select overwatch points. The CTM can provide real-time trustworthiness evaluation for the MRS on the overwatch points by referring to the robots' situational awareness information, such as traversability and line of sight. The evaluation can quantify each robot's trustworthiness in protecting its robot team members during the bounding overwatch. The trustworthiness evaluation can generate a dynamic cost map for each robot in the workspace and help obtain the most trustworthy bounding overwatch path. Our proposed Bayesian based CTM and motion planning can reduce the number of explorations for the workspace in data collection and improve the CTM learning efficiency. It also enables the MRS to deal with the dynamic and uncertain environments for the multi-robot bounding overwatch task. A robot simulation is implemented in ROS Gazebo to demonstrate the effectiveness of the proposed framework.
Efficient algorithms for autonomous electric vehicles' min-max routing problem
Aug 07, 2020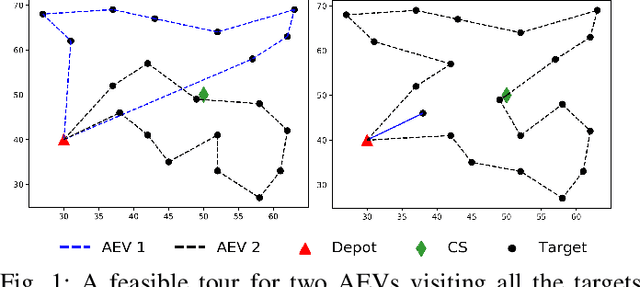
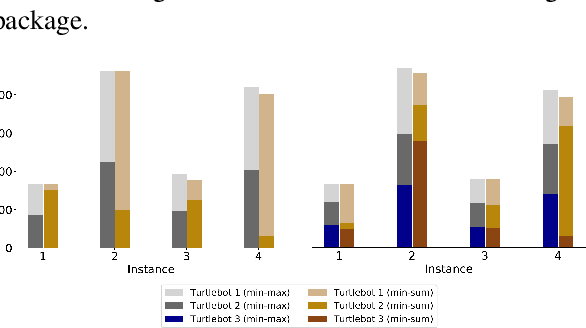
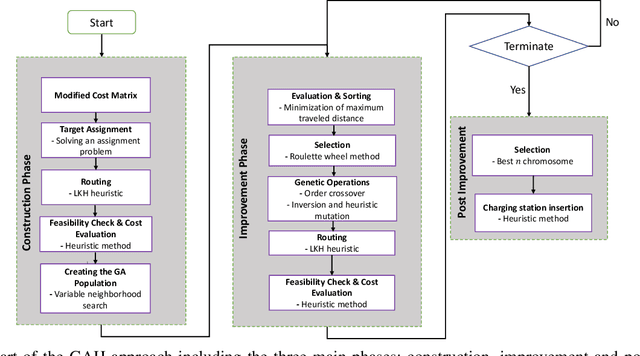
Abstract:Increase in greenhouse gases emission from the transportation sector has led companies and government to elevate and support the production of electric vehicles. The natural synergy between increased support for electric and emergence of autonomous vehicles possibly can relieve the limitations regarding access to charging infrastructure, time management, and range anxiety. In this work, a fleet of Autonomous Electric Vehicles (AEV) is considered for transportation and logistic capabilities with limited battery capacity and scarce charging station availability are considered while planning to avoid inefficient routing strategies. We introduce a min-max autonomous electric vehicle routing problem (AEVRP) where the maximum distance traveled by any AEV is minimized while considering charging stations for recharging. We propose a genetic algorithm based meta-heuristic that can efficiently solve a variety of instances. Extensive computational results, sensitivity analysis, and data-driven simulation implemented with the robot operating system (ROS) middleware are performed to corroborate the efficiency of the proposed approach, both quantitatively and qualitatively.
Two-stage stochastic programming approach for path planning problems under travel time and availability uncertainties
Oct 08, 2019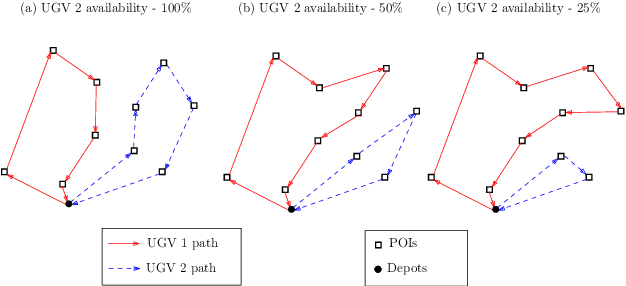
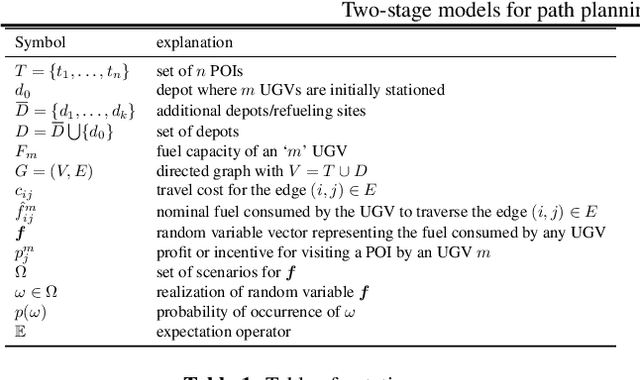
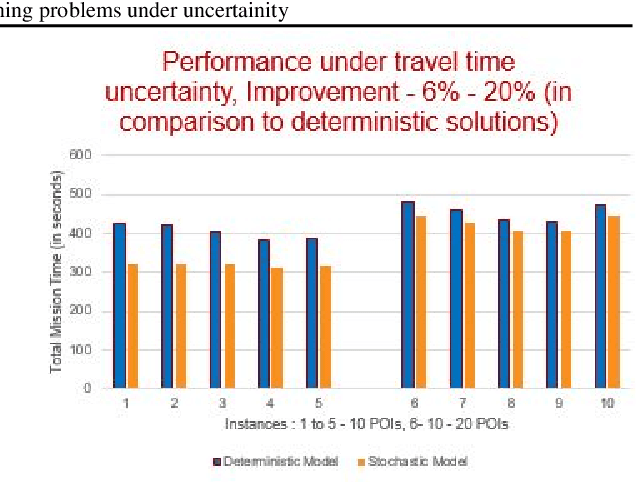
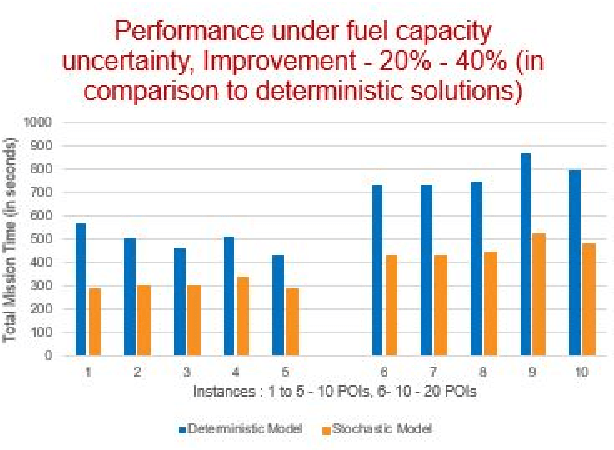
Abstract:Significant advances in sensing, robotics, and wireless networks have enabled the collaborative utilization of autonomous aerial, ground and underwater vehicles for various applications. However, to successfully harness the benefits of these unmanned ground vehicles (UGVs) in homeland security operations, it is critical to efficiently solve UGV path planning problem which lies at the heart of these operations. Furthermore, in the real-world applications of UGVs, these operations encounter uncertainties such as incomplete information about the target sites, travel times, and the availability of vehicles, sensors, and fuel. This research paper focuses on developing algebraic-based-modeling framework to enable the successful deployment of a team of vehicles while addressing uncertainties in the distance traveled and the availability of UGVs for the mission.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge