Konstantinos Plataniotis
Distribution Alignment for Fully Test-Time Adaptation with Dynamic Online Data Streams
Jul 16, 2024Abstract:Given a model trained on source data, Test-Time Adaptation (TTA) enables adaptation and inference in test data streams with domain shifts from the source. Current methods predominantly optimize the model for each incoming test data batch using self-training loss. While these methods yield commendable results in ideal test data streams, where batches are independently and identically sampled from the target distribution, they falter under more practical test data streams that are not independent and identically distributed (non-i.i.d.). The data batches in a non-i.i.d. stream display prominent label shifts relative to each other. It leads to conflicting optimization objectives among batches during the TTA process. Given the inherent risks of adapting the source model to unpredictable test-time distributions, we reverse the adaptation process and propose a novel Distribution Alignment loss for TTA. This loss guides the distributions of test-time features back towards the source distributions, which ensures compatibility with the well-trained source model and eliminates the pitfalls associated with conflicting optimization objectives. Moreover, we devise a domain shift detection mechanism to extend the success of our proposed TTA method in the continual domain shift scenarios. Our extensive experiments validate the logic and efficacy of our method. On six benchmark datasets, we surpass existing methods in non-i.i.d. scenarios and maintain competitive performance under the ideal i.i.d. assumption.
Test-Time Personalization with Meta Prompt for Gaze Estimation
Jan 03, 2024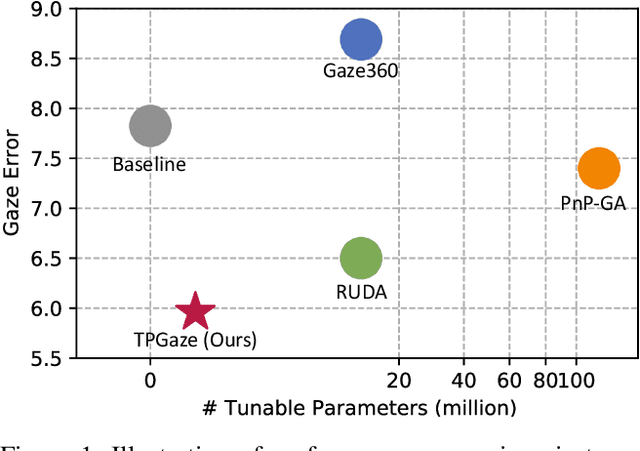
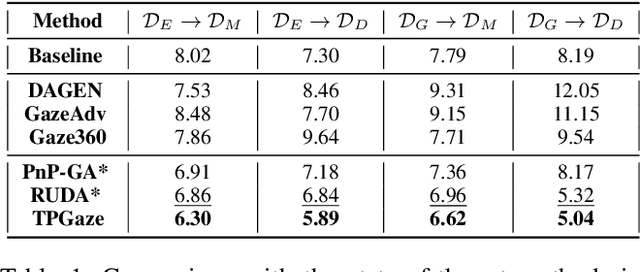

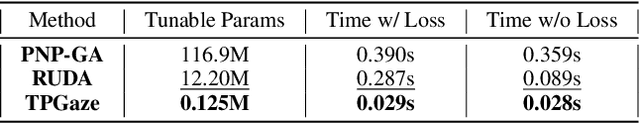
Abstract:Despite the recent remarkable achievement in gaze estimation, efficient and accurate personalization of gaze estimation without labels is a practical problem but rarely touched on in the literature. To achieve efficient personalization, we take inspiration from the recent advances in Natural Language Processing (NLP) by updating a negligible number of parameters, "prompts", at the test time. Specifically, the prompt is additionally attached without perturbing original network and can contain less than 1% of a ResNet-18's parameters. Our experiments show high efficiency of the prompt tuning approach. The proposed one can be 10 times faster in terms of adaptation speed than the methods compared. However, it is non-trivial to update the prompt for personalized gaze estimation without labels. At the test time, it is essential to ensure that the minimizing of particular unsupervised loss leads to the goals of minimizing gaze estimation error. To address this difficulty, we propose to meta-learn the prompt to ensure that its updates align with the goal. Our experiments show that the meta-learned prompt can be effectively adapted even with a simple symmetry loss. In addition, we experiment on four cross-dataset validations to show the remarkable advantages of the proposed method.
Federated Learning and Blockchain-enabled Fog-IoT Platform for Wearables in Predictive Healthcare
Jan 11, 2023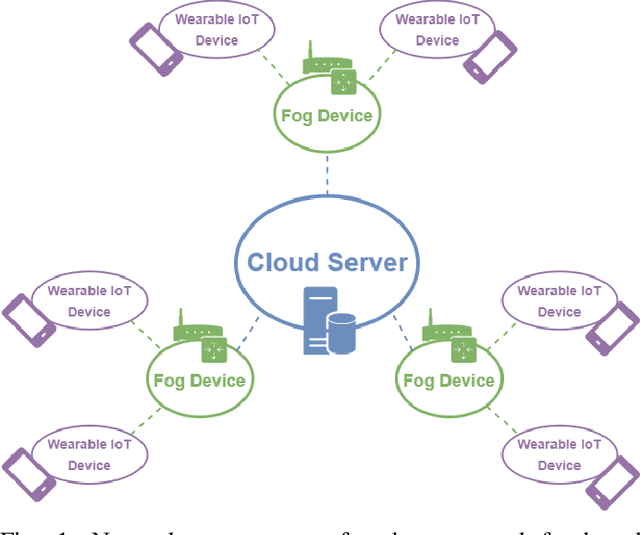
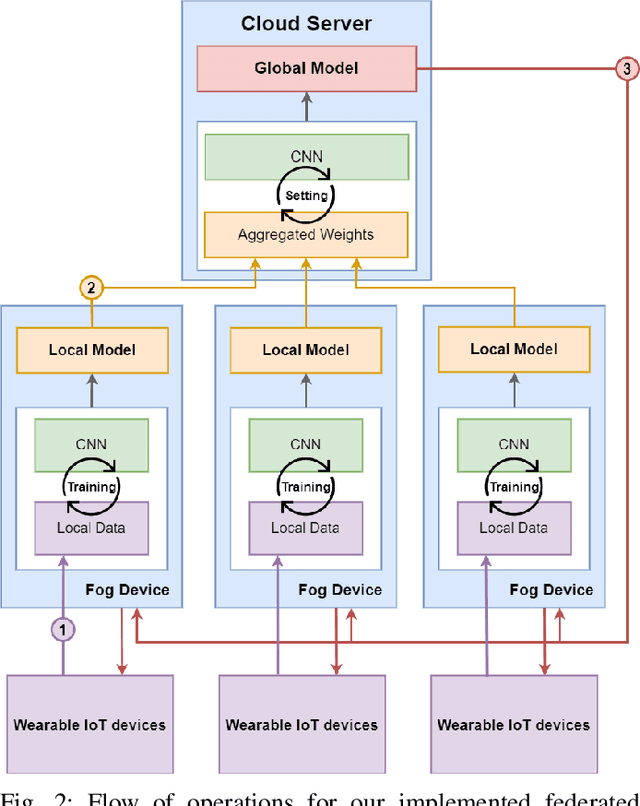
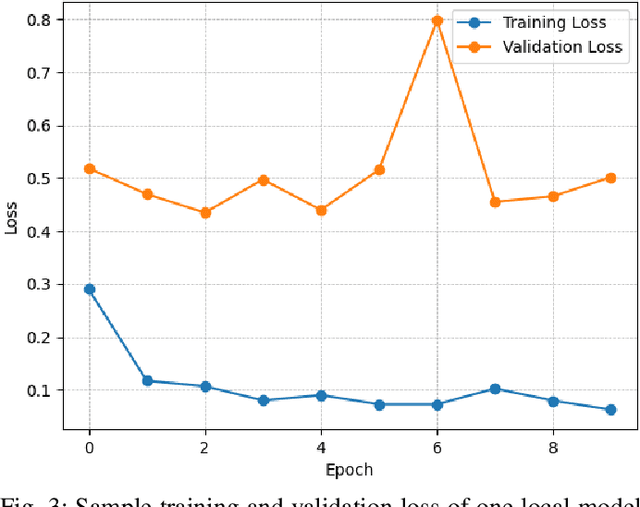
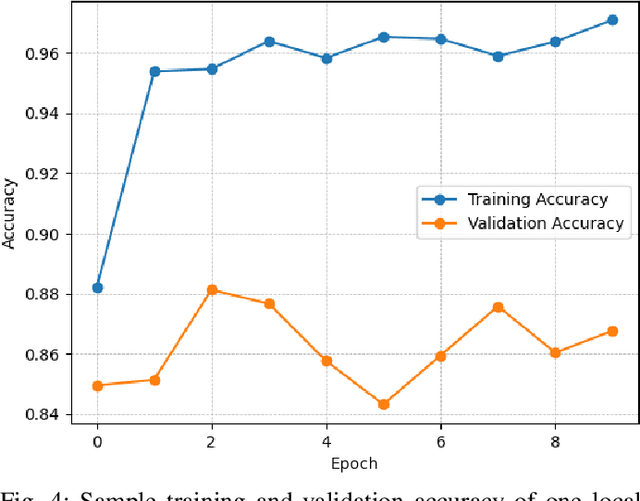
Abstract:Over the years, the popularity and usage of wearable Internet of Things (IoT) devices in several healthcare services are increased. Among the services that benefit from the usage of such devices is predictive analysis, which can improve early diagnosis in e-health. However, due to the limitations of wearable IoT devices, challenges in data privacy, service integrity, and network structure adaptability arose. To address these concerns, we propose a platform using federated learning and private blockchain technology within a fog-IoT network. These technologies have privacy-preserving features securing data within the network. We utilized the fog-IoT network's distributive structure to create an adaptive network for wearable IoT devices. We designed a testbed to examine the proposed platform's ability to preserve the integrity of a classifier. According to experimental results, the introduced implementation can effectively preserve a patient's privacy and a predictive service's integrity. We further investigated the contributions of other technologies to the security and adaptability of the IoT network. Overall, we proved the feasibility of our platform in addressing significant security and privacy challenges of wearable IoT devices in predictive healthcare through analysis, simulation, and experimentation.
Spatio-Temporal Hybrid Fusion of CAE and SWIn Transformers for Lung Cancer Malignancy Prediction
Oct 27, 2022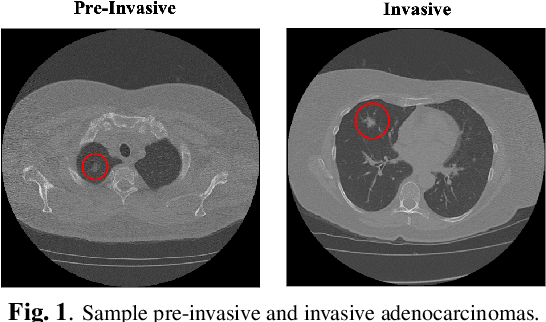
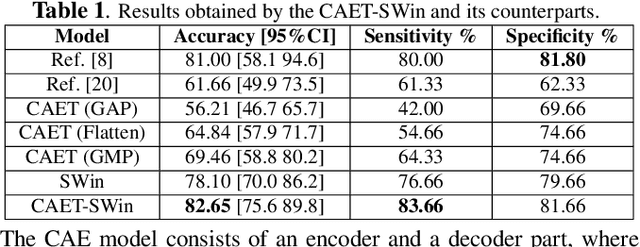
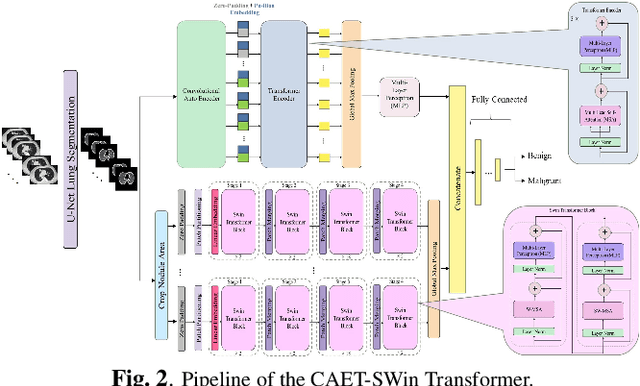
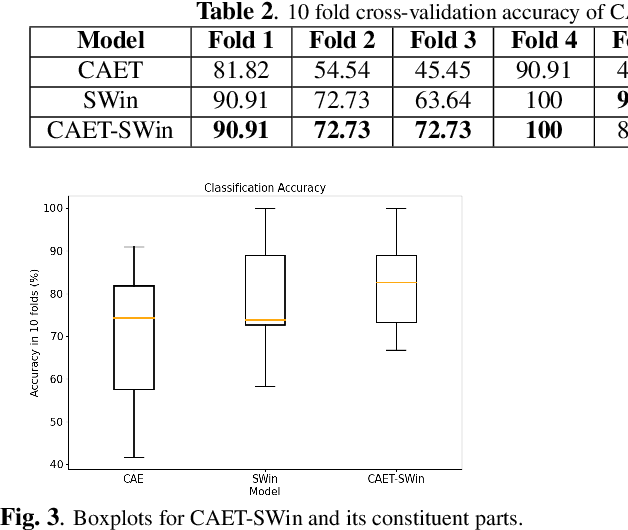
Abstract:The paper proposes a novel hybrid discovery Radiomics framework that simultaneously integrates temporal and spatial features extracted from non-thin chest Computed Tomography (CT) slices to predict Lung Adenocarcinoma (LUAC) malignancy with minimum expert involvement. Lung cancer is the leading cause of mortality from cancer worldwide and has various histologic types, among which LUAC has recently been the most prevalent. LUACs are classified as pre-invasive, minimally invasive, and invasive adenocarcinomas. Timely and accurate knowledge of the lung nodules malignancy leads to a proper treatment plan and reduces the risk of unnecessary or late surgeries. Currently, chest CT scan is the primary imaging modality to assess and predict the invasiveness of LUACs. However, the radiologists' analysis based on CT images is subjective and suffers from a low accuracy compared to the ground truth pathological reviews provided after surgical resections. The proposed hybrid framework, referred to as the CAET-SWin, consists of two parallel paths: (i) The Convolutional Auto-Encoder (CAE) Transformer path that extracts and captures informative features related to inter-slice relations via a modified Transformer architecture, and; (ii) The Shifted Window (SWin) Transformer path, which is a hierarchical vision transformer that extracts nodules' related spatial features from a volumetric CT scan. Extracted temporal (from the CAET-path) and spatial (from the Swin path) are then fused through a fusion path to classify LUACs. Experimental results on our in-house dataset of 114 pathologically proven Sub-Solid Nodules (SSNs) demonstrate that the CAET-SWin significantly improves reliability of the invasiveness prediction task while achieving an accuracy of 82.65%, sensitivity of 83.66%, and specificity of 81.66% using 10-fold cross-validation.
Personal Devices for Contact Tracing: Smartphones and Wearables to Fight Covid-19
Aug 02, 2021
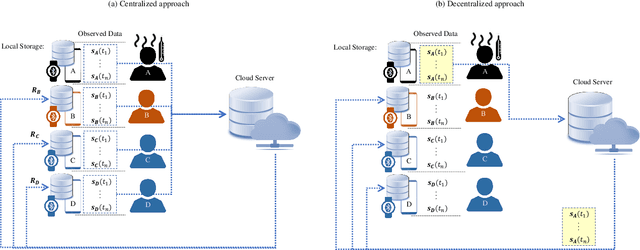
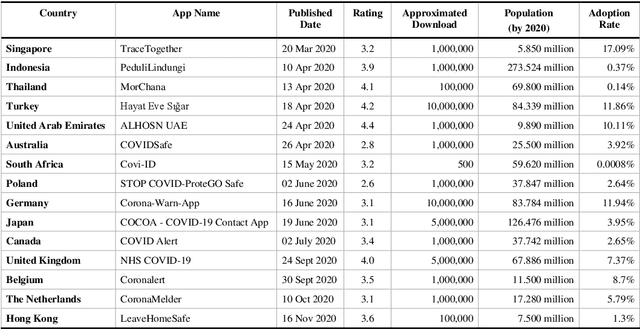
Abstract:Digital contact tracing has emerged as a viable tool supplementing manual contact tracing. To date, more than 100 contact tracing applications have been published to slow down the spread of highly contagious Covid-19. Despite subtle variabilities among these applications, all of them achieve contact tracing by manipulating the following three components: a) use a personal device to identify the user while designing a secure protocol to anonymize the user's identity; b) leverage networking technologies to analyze and store the data; c) exploit rich sensing features on the user device to detect the interaction among users and thus estimate the exposure risk. This paper reviews the current digital contact tracing based on these three components. We focus on two personal devices that are intimate to the user: smartphones and wearables. We discuss the centralized and decentralized networking approaches that use to facilitate the data flow. Lastly, we investigate the sensing feature available on smartphones and wearables to detect the proximity between any two users and present experiments comparing the proximity sensing performance between these two personal devices.
Deep Learning and Machine Vision for Food Processing: A Survey
Mar 30, 2021
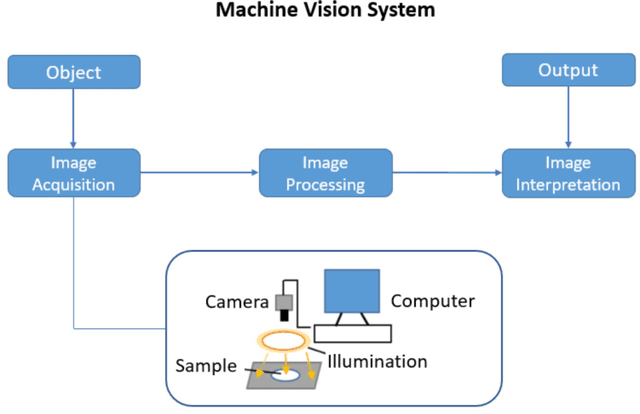
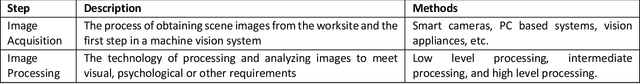
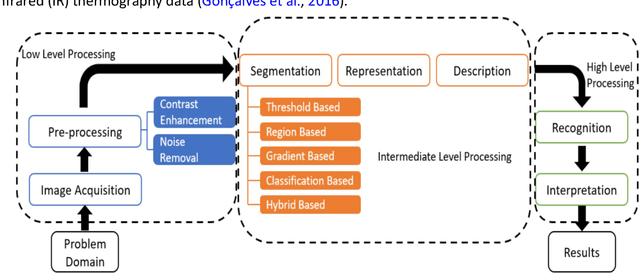
Abstract:The quality and safety of food is an important issue to the whole society, since it is at the basis of human health, social development and stability. Ensuring food quality and safety is a complex process, and all stages of food processing must be considered, from cultivating, harvesting and storage to preparation and consumption. However, these processes are often labour-intensive. Nowadays, the development of machine vision can greatly assist researchers and industries in improving the efficiency of food processing. As a result, machine vision has been widely used in all aspects of food processing. At the same time, image processing is an important component of machine vision. Image processing can take advantage of machine learning and deep learning models to effectively identify the type and quality of food. Subsequently, follow-up design in the machine vision system can address tasks such as food grading, detecting locations of defective spots or foreign objects, and removing impurities. In this paper, we provide an overview on the traditional machine learning and deep learning methods, as well as the machine vision techniques that can be applied to the field of food processing. We present the current approaches and challenges, and the future trends.
Energy-based Surprise Minimization for Multi-Agent Value Factorization
Oct 05, 2020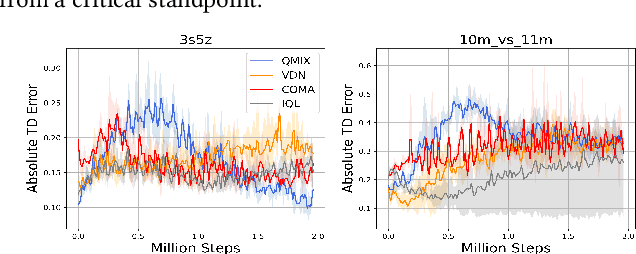
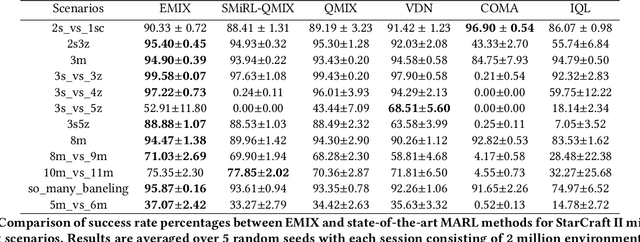
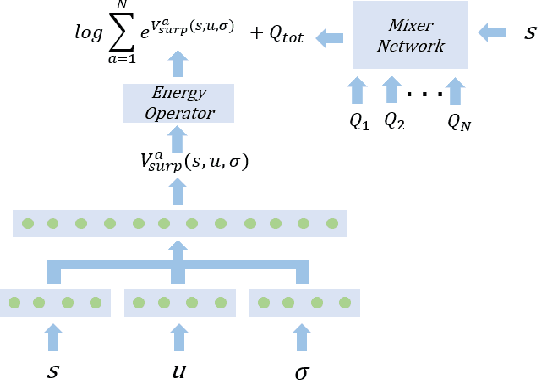
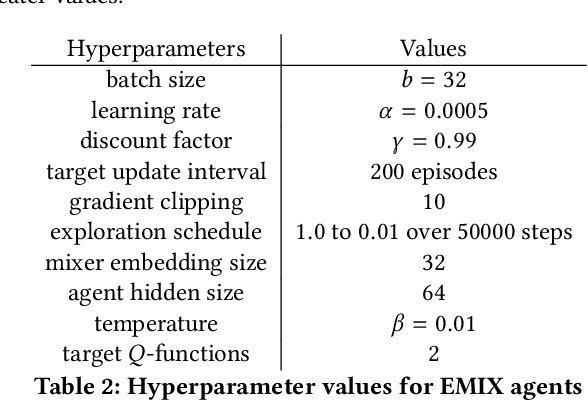
Abstract:Multi-Agent Reinforcement Learning (MARL) has demonstrated significant success in training decentralised policies in a centralised manner by making use of value factorization methods. However, addressing surprise across spurious states and approximation bias remain open problems for multi-agent settings. We introduce the Energy-based MIXer (EMIX), an algorithm which minimizes surprise utilizing the energy across agents. Our contributions are threefold; (1) EMIX introduces a novel surprise minimization technique across multiple agents in the case of multi-agent partially-observable settings. (2) EMIX highlights the first practical use of energy functions in MARL (to our knowledge) with theoretical guarantees and experiment validations of the energy operator. Lastly, (3) EMIX presents a novel technique for addressing overestimation bias across agents in MARL. When evaluated on a range of challenging StarCraft II micromanagement scenarios, EMIX demonstrates consistent state-of-the-art performance for multi-agent surprise minimization. Moreover, our ablation study highlights the necessity of the energy-based scheme and the need for elimination of overestimation bias in MARL. Our implementation of EMIX and videos of agents are available at https://karush17.github.io/emix-web/.
Epidemic Exposure Notification with Smartwatch: A Proximity-Based Privacy-Preserving Approach
Jul 08, 2020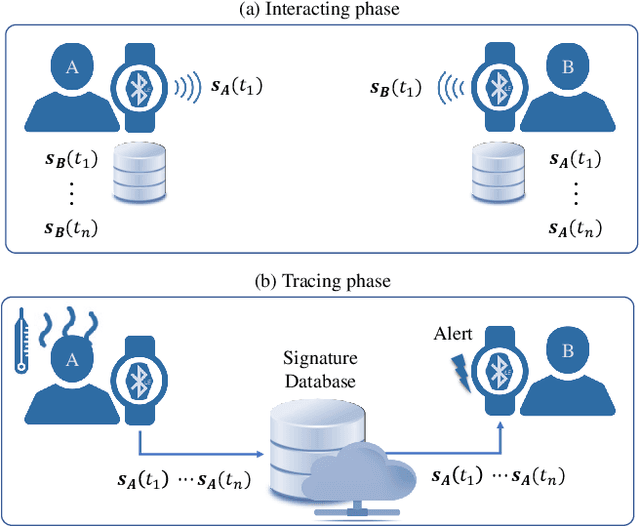
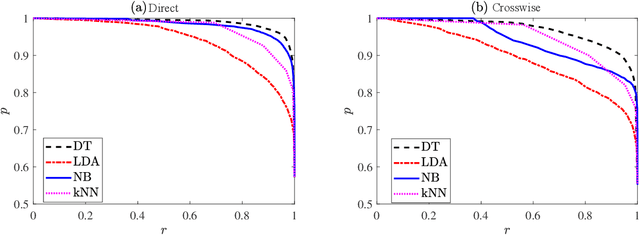
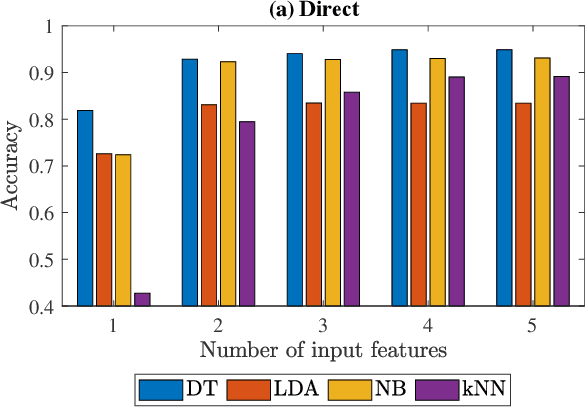
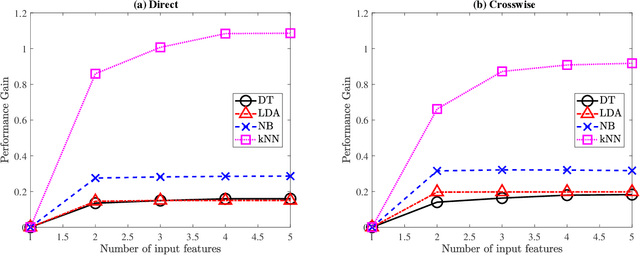
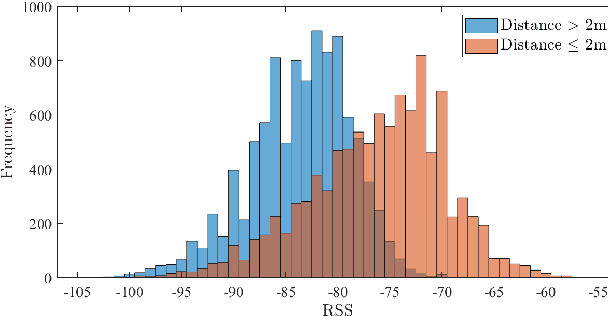
Abstract:Businesses planning for the post-pandemic world are looking for innovative ways to protect the health and welfare of their employees and customers. Wireless technologies can play a key role in assisting contact tracing to quickly halt a local infection outbreak and prevent further spread. In this work, we present a wearable proximity and exposure notification solution based on a smartwatch that also promotes safe physical distancing in business, hospitality, or recreational facilities. Our proximity-based privacy-preserving contact tracing (P$^3$CT) leverages the Bluetooth Low Energy (BLE) technology for reliable proximity sensing, and an ambient signature protocol for preserving identity. Proximity sensing exploits the received signal strength (RSS) to detect the user's interaction and thus classifying them into low- or high-risk with respect to a patient diagnosed with an infectious disease. More precisely, a user is notified of their exposure based on their interactions, in terms of distance and time, with a patient. Our privacy-preserving protocol uses the ambient signatures to ensure that users' identities be anonymized. We demonstrate the feasibility of our proposed solution through extensive experimentation.
COVID-19 and Your Smartphone: BLE-based Smart Contact Tracing
May 28, 2020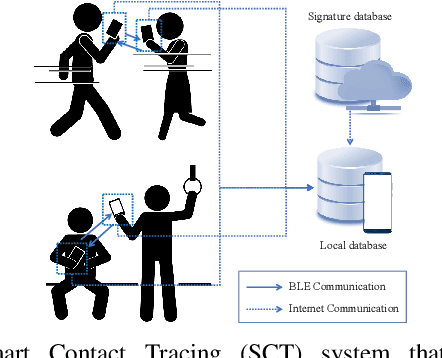
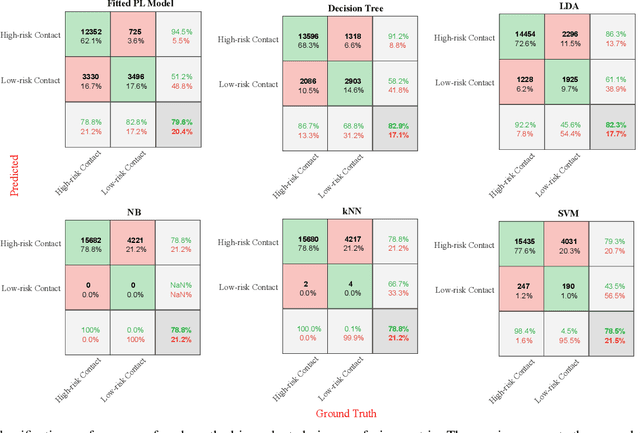
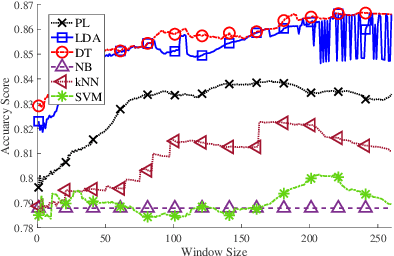
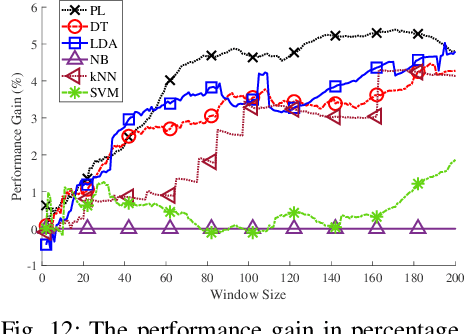
Abstract:Contact tracing is of paramount importance when it comes to preventing the spreading of infectious diseases. Contact tracing is usually performed manually by authorized personnel. Manual contact tracing is an inefficient, error-prone, time-consuming process of limited utility to the population at large as those in close contact with infected individuals are informed hours, if not days, later. This paper introduces an alternative way to manual contact tracing. The proposed Smart Contact Tracing (SCT) system utilizes the smartphone's Bluetooth Low Energy (BLE) signals and machine learning classifier to accurately and quickly determined the contact profile. SCT's contribution is two-fold: a) classification of the user's contact as high/low-risk using precise proximity sensing, and b) user anonymity using a privacy-preserving communications protocol. SCT leverages BLE's non-connectable advertising feature to broadcast a signature packet when the user is in the public space. Both broadcasted and observed signatures are stored in the user's smartphone and they are only uploaded to a secure signature database when a user is confirmed by public health authorities to be infected. Using received signal strength (RSS) each smartphone estimates its distance from other user's phones and issues real-time alerts when social distancing rules are violated. The paper includes extensive experimentation utilizing real-life smartphone positions and a comparative evaluation of five machine learning classifiers. Reported results indicate that a decision tree classifier outperforms other states of the art classification methods in terms of accuracy. Lastly, to facilitate research in this area, and to contribute to the timely development of advanced solutions the entire data set of six experiments with about 123,000 data points is made publicly available.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge