Petros Spachos
Federated Kalman Filter for Secure IoT-based Device Monitoring Services
Apr 03, 2023Abstract:Device monitoring services have increased in popularity with the evolution of recent technology and the continuously increased number of Internet of Things (IoT) devices. Among the popular services are the ones that use device location information. However, these services run into privacy issues due to the nature of data collection and transmission. In this work, we introduce a platform incorporating Federated Kalman Filter (FKF) with a federated learning approach and private blockchain technology for privacy preservation. We analyze the accuracy of the proposed design against a standard Kalman Filter (KF) implementation of localization based on the Received Signal Strength Indicator (RSSI). The experimental results reveal significant potential for improved data estimation for RSSI-based localization in device monitoring.
Federated Learning and Blockchain-enabled Fog-IoT Platform for Wearables in Predictive Healthcare
Jan 11, 2023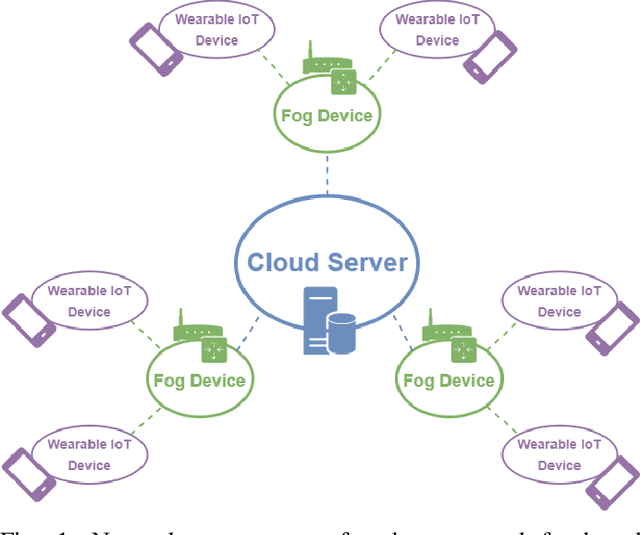
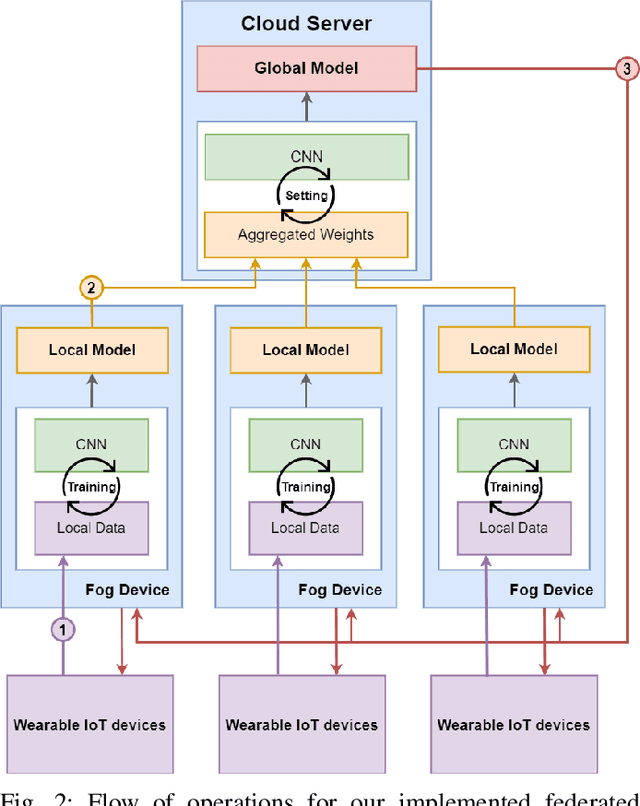
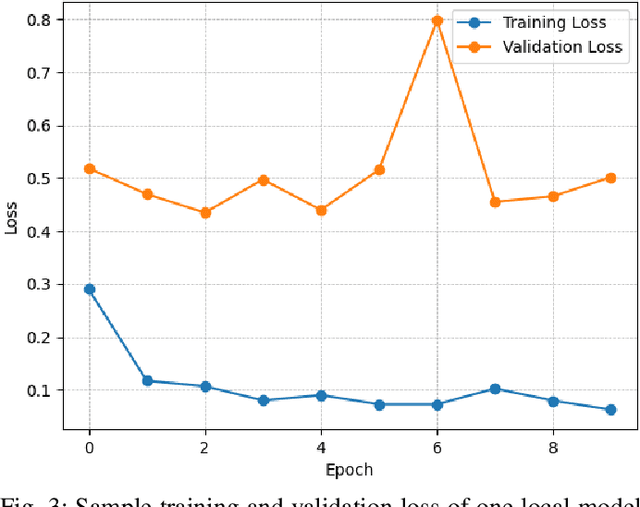
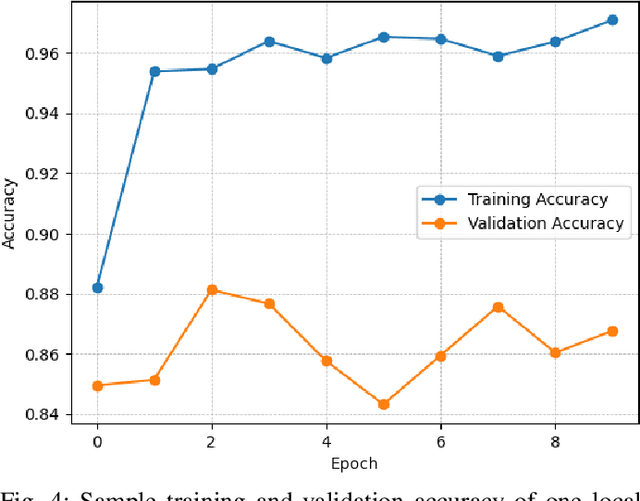
Abstract:Over the years, the popularity and usage of wearable Internet of Things (IoT) devices in several healthcare services are increased. Among the services that benefit from the usage of such devices is predictive analysis, which can improve early diagnosis in e-health. However, due to the limitations of wearable IoT devices, challenges in data privacy, service integrity, and network structure adaptability arose. To address these concerns, we propose a platform using federated learning and private blockchain technology within a fog-IoT network. These technologies have privacy-preserving features securing data within the network. We utilized the fog-IoT network's distributive structure to create an adaptive network for wearable IoT devices. We designed a testbed to examine the proposed platform's ability to preserve the integrity of a classifier. According to experimental results, the introduced implementation can effectively preserve a patient's privacy and a predictive service's integrity. We further investigated the contributions of other technologies to the security and adaptability of the IoT network. Overall, we proved the feasibility of our platform in addressing significant security and privacy challenges of wearable IoT devices in predictive healthcare through analysis, simulation, and experimentation.
A Kernel Method to Nonlinear Location Estimation with RSS-based Fingerprint
Apr 07, 2022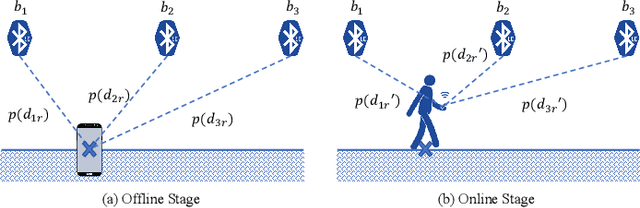
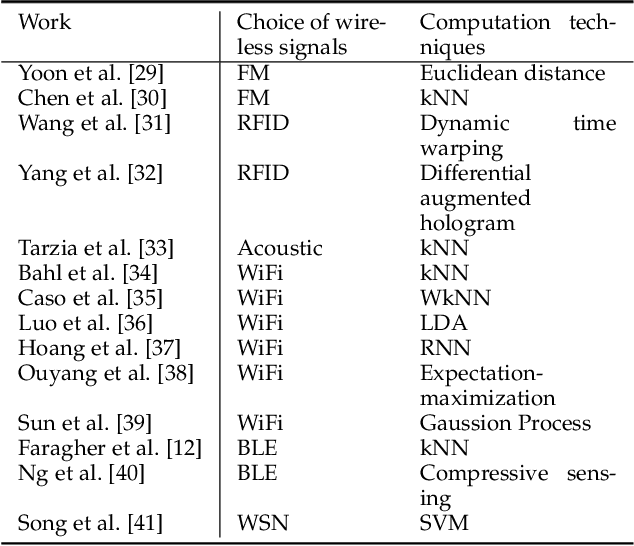
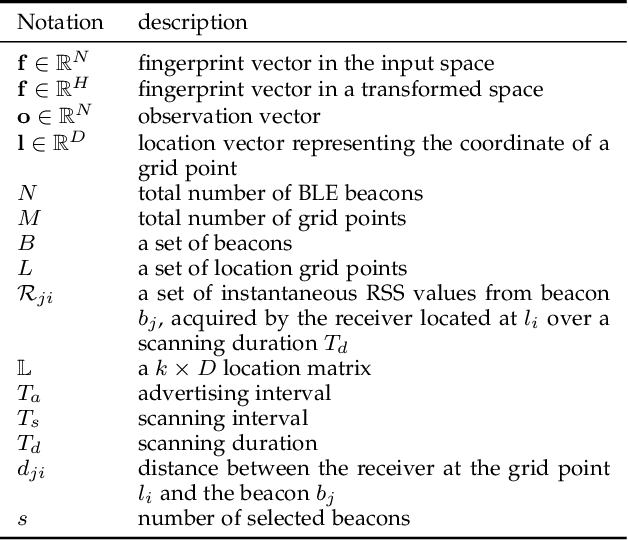
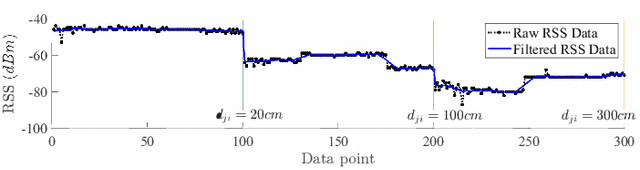
Abstract:This paper presents a nonlinear location estimation to infer the position of a user holding a smartphone. We consider a large location with $M$ number of grid points, each grid point is labeled with a unique fingerprint consisting of the received signal strength (RSS) values measured from $N$ number of Bluetooth Low Energy (BLE) beacons. Given the fingerprint observed by the smartphone, the user's current location can be estimated by finding the top-k similar fingerprints from the list of fingerprints registered in the database. Besides the environmental factors, the dynamicity in holding the smartphone is another source to the variation in fingerprint measurements, yet there are not many studies addressing the fingerprint variability due to dynamic smartphone positions held by human hands during online detection. To this end, we propose a nonlinear location estimation using the kernel method. Specifically, our proposed method comprises of two steps: 1) a beacon selection strategy to select a subset of beacons that is insensitive to the subtle change of holding positions, and 2) a kernel method to compute the similarity between this subset of observed signals and all the fingerprints registered in the database. The experimental results based on large-scale data collected in a complex building indicate a substantial performance gain of our proposed approach in comparison to state-of-the-art methods. The dataset consisting of the signal information collected from the beacons is available online.
Personal Devices for Contact Tracing: Smartphones and Wearables to Fight Covid-19
Aug 02, 2021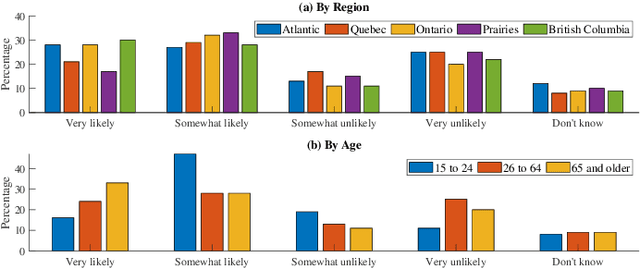
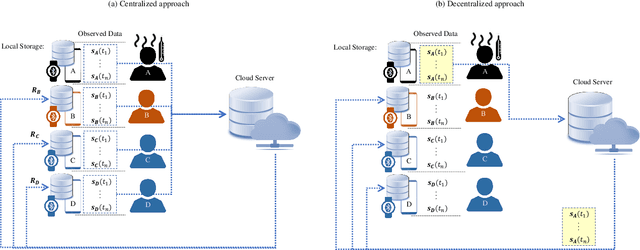
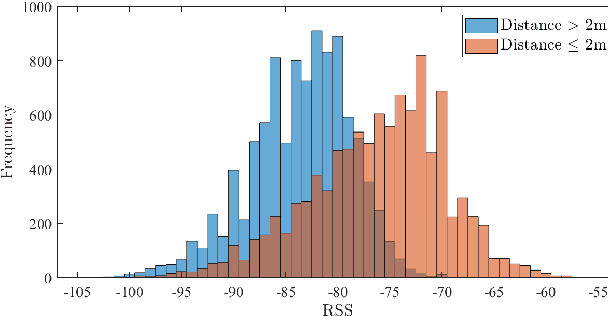
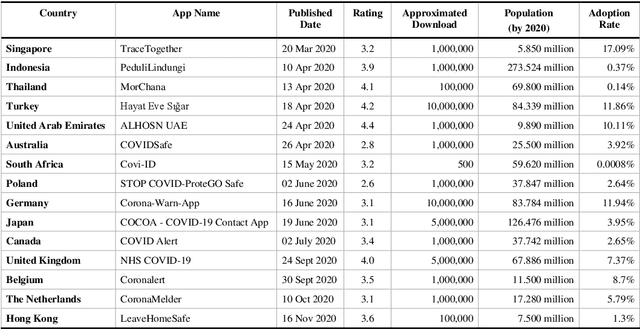
Abstract:Digital contact tracing has emerged as a viable tool supplementing manual contact tracing. To date, more than 100 contact tracing applications have been published to slow down the spread of highly contagious Covid-19. Despite subtle variabilities among these applications, all of them achieve contact tracing by manipulating the following three components: a) use a personal device to identify the user while designing a secure protocol to anonymize the user's identity; b) leverage networking technologies to analyze and store the data; c) exploit rich sensing features on the user device to detect the interaction among users and thus estimate the exposure risk. This paper reviews the current digital contact tracing based on these three components. We focus on two personal devices that are intimate to the user: smartphones and wearables. We discuss the centralized and decentralized networking approaches that use to facilitate the data flow. Lastly, we investigate the sensing feature available on smartphones and wearables to detect the proximity between any two users and present experiments comparing the proximity sensing performance between these two personal devices.
Internet-of-Things Devices and Assistive Technologies for Healthcare: Applications, Challenges, and Opportunities
Jul 11, 2021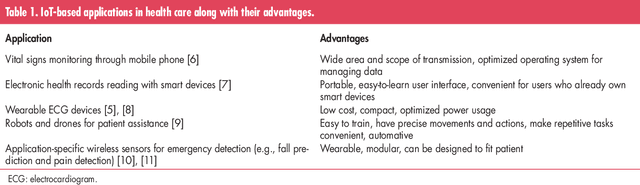
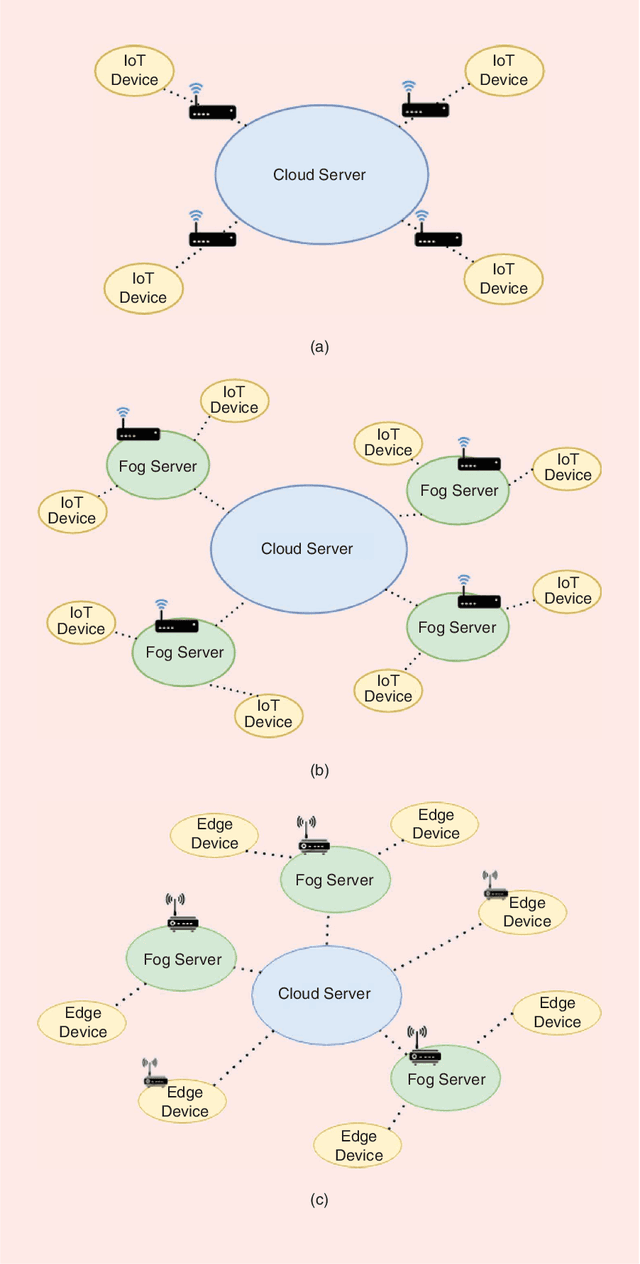
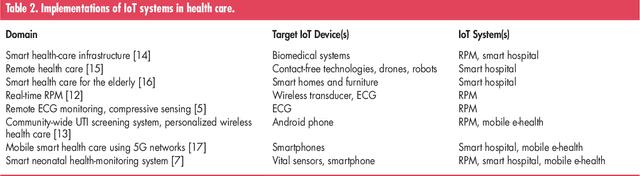
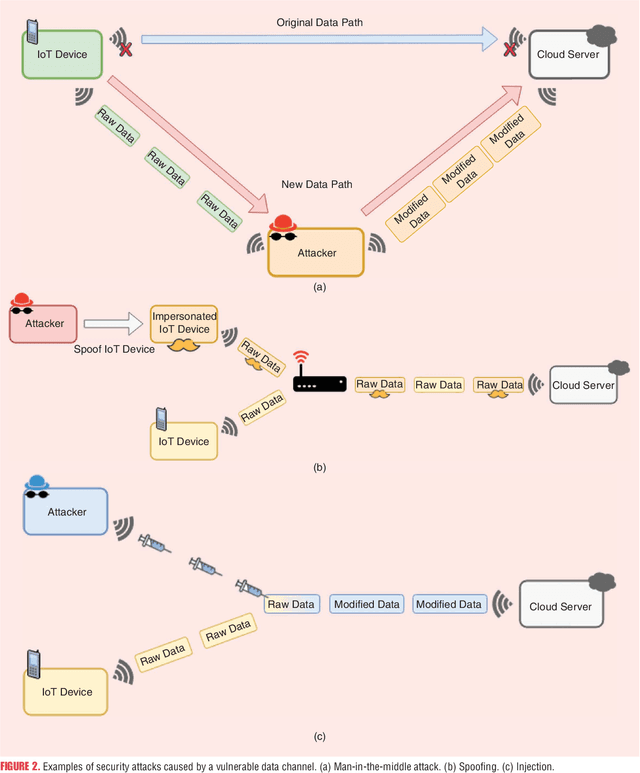
Abstract:Medical conditions and cases are growing at a rapid pace, where physical space is starting to be constrained. Hospitals and clinics no longer have the ability to accommodate large numbers of incoming patients. It is clear that the current state of the health industry needs to improve its valuable and limited resources. The evolution of the Internet of Things (IoT) devices along with assistive technologies can alleviate the problem in healthcare, by being a convenient and easy means of accessing healthcare services wirelessly. There is a plethora of IoT devices and potential applications that can take advantage of the unique characteristics that these technologies can offer. However, at the same time, these services pose novel challenges that need to be properly addressed. In this article, we review some popular categories of IoT-based applications for healthcare along with their devices. Then, we describe the challenges and discuss how research can properly address the open issues and improve the already existing implementations in healthcare. Further possible solutions are also discussed to show their potential in being viable solutions for future healthcare applications
Deep Learning and Machine Vision for Food Processing: A Survey
Mar 30, 2021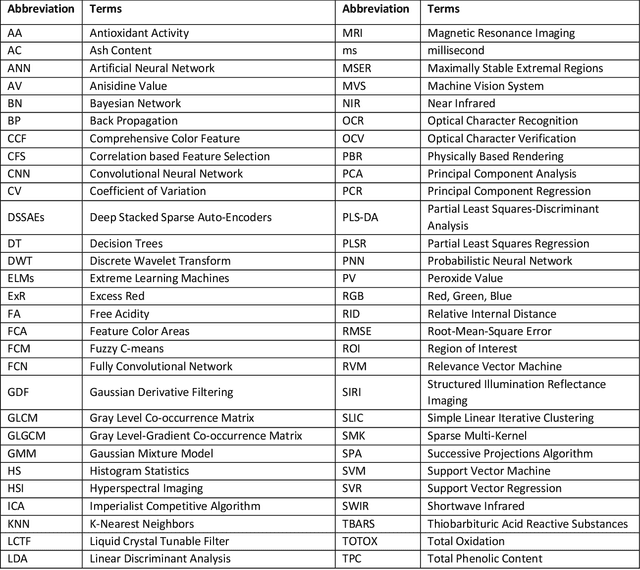
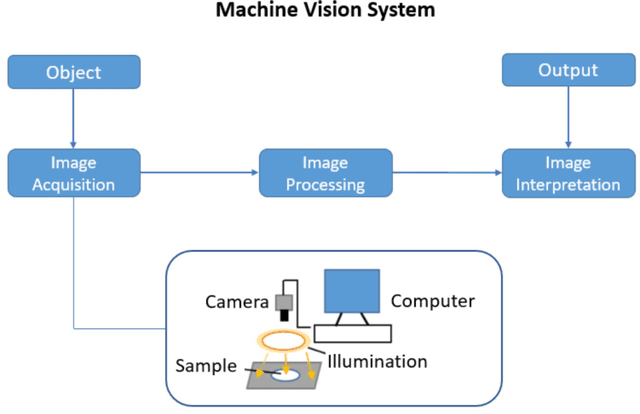
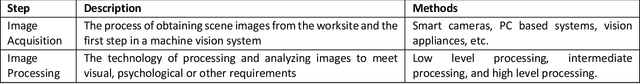
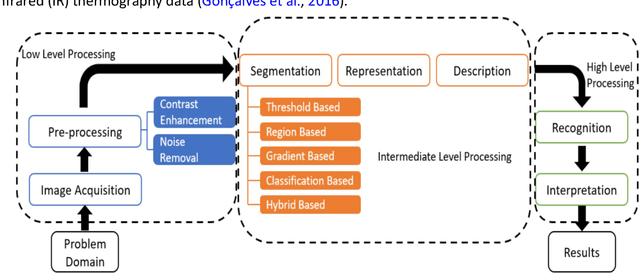
Abstract:The quality and safety of food is an important issue to the whole society, since it is at the basis of human health, social development and stability. Ensuring food quality and safety is a complex process, and all stages of food processing must be considered, from cultivating, harvesting and storage to preparation and consumption. However, these processes are often labour-intensive. Nowadays, the development of machine vision can greatly assist researchers and industries in improving the efficiency of food processing. As a result, machine vision has been widely used in all aspects of food processing. At the same time, image processing is an important component of machine vision. Image processing can take advantage of machine learning and deep learning models to effectively identify the type and quality of food. Subsequently, follow-up design in the machine vision system can address tasks such as food grading, detecting locations of defective spots or foreign objects, and removing impurities. In this paper, we provide an overview on the traditional machine learning and deep learning methods, as well as the machine vision techniques that can be applied to the field of food processing. We present the current approaches and challenges, and the future trends.
Support Vector Machine and YOLO for a Mobile Food Grading System
Jan 05, 2021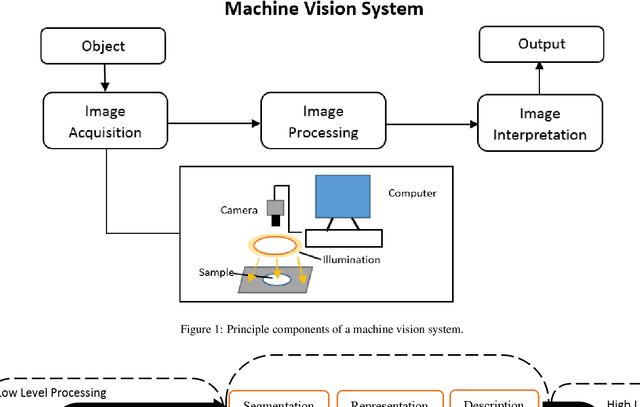

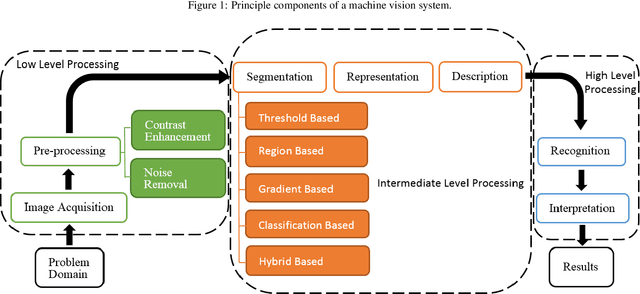
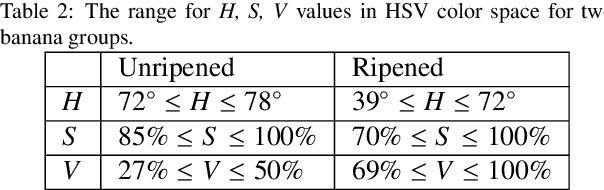
Abstract:Food quality and safety are of great concern to society since it is an essential guarantee not only for human health but also for social development, and stability. Ensuring food quality and safety is a complex process. All food processing stages should be considered, from cultivating, harvesting and storage to preparation and consumption. Grading is one of the essential processes to control food quality. This paper proposed a mobile visual-based system to evaluate food grading. Specifically, the proposed system acquires images of bananas when they are on moving conveyors. A two-layer image processing system based on machine learning is used to grade bananas, and these two layers are allocated on edge devices and cloud servers, respectively. Support Vector Machine (SVM) is the first layer to classify bananas based on an extracted feature vector composed of color and texture features. Then, the a You Only Look Once (YOLO) v3 model further locating the peel's defected area and determining if the inputs belong to the mid-ripened or well-ripened class. According to experimental results, the first layer's performance achieved an accuracy of 98.5% while the accuracy of the second layer is 85.7%, and the overall accuracy is 96.4%.
Epidemic Exposure Notification with Smartwatch: A Proximity-Based Privacy-Preserving Approach
Jul 08, 2020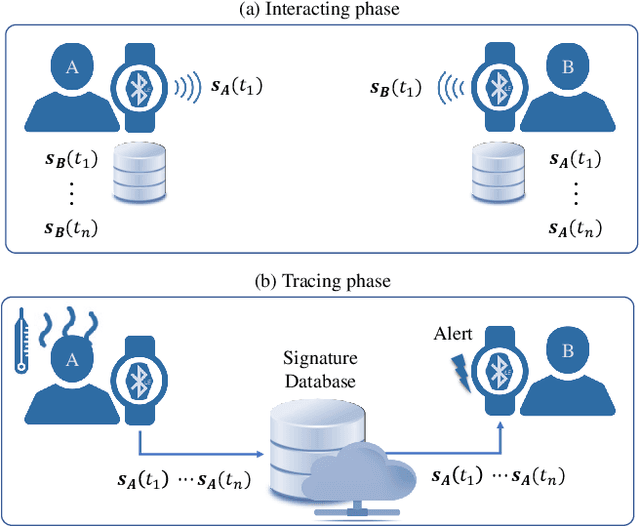
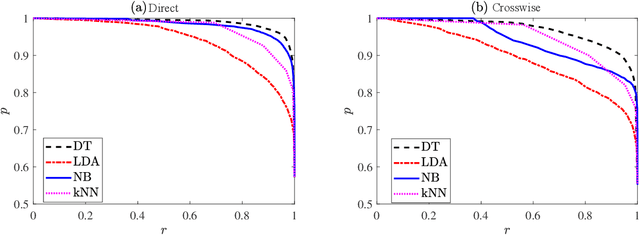
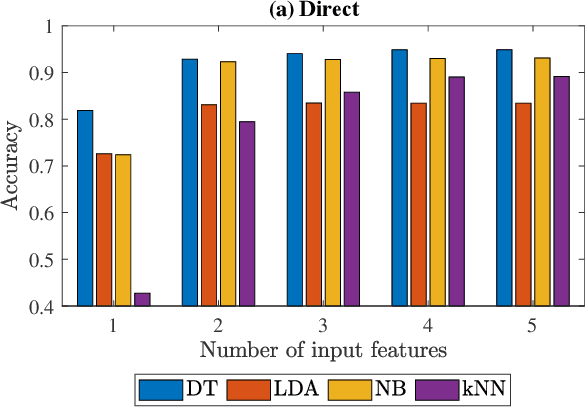
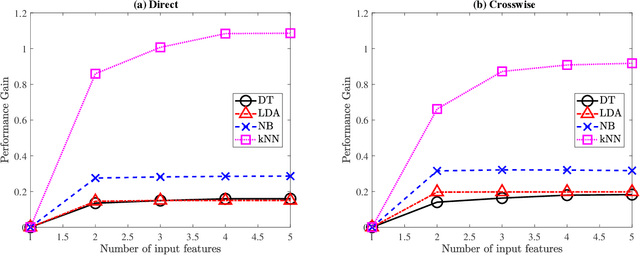
Abstract:Businesses planning for the post-pandemic world are looking for innovative ways to protect the health and welfare of their employees and customers. Wireless technologies can play a key role in assisting contact tracing to quickly halt a local infection outbreak and prevent further spread. In this work, we present a wearable proximity and exposure notification solution based on a smartwatch that also promotes safe physical distancing in business, hospitality, or recreational facilities. Our proximity-based privacy-preserving contact tracing (P$^3$CT) leverages the Bluetooth Low Energy (BLE) technology for reliable proximity sensing, and an ambient signature protocol for preserving identity. Proximity sensing exploits the received signal strength (RSS) to detect the user's interaction and thus classifying them into low- or high-risk with respect to a patient diagnosed with an infectious disease. More precisely, a user is notified of their exposure based on their interactions, in terms of distance and time, with a patient. Our privacy-preserving protocol uses the ambient signatures to ensure that users' identities be anonymized. We demonstrate the feasibility of our proposed solution through extensive experimentation.
COVID-19 and Your Smartphone: BLE-based Smart Contact Tracing
May 28, 2020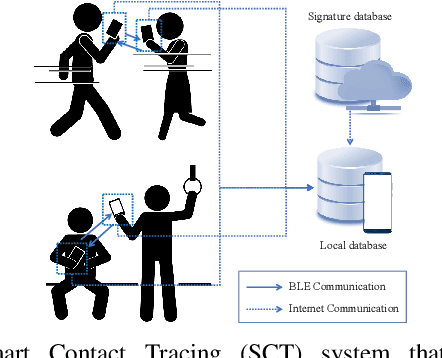
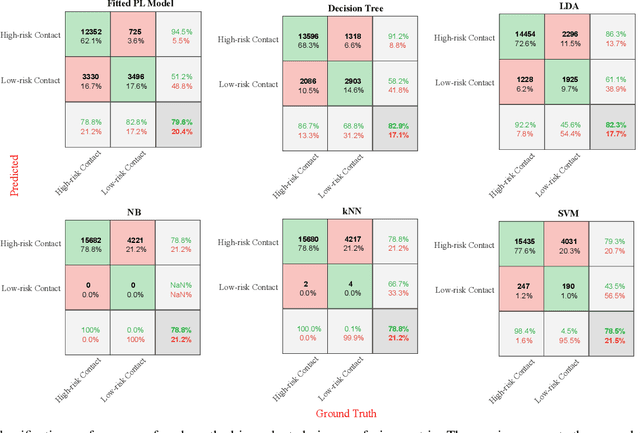
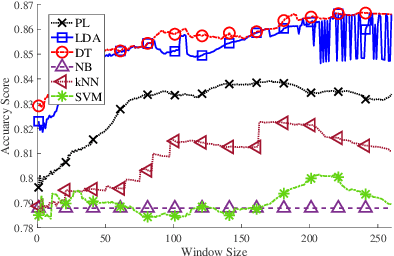
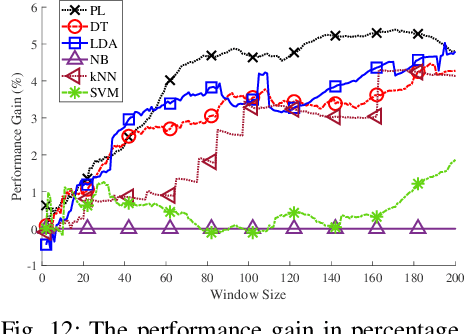
Abstract:Contact tracing is of paramount importance when it comes to preventing the spreading of infectious diseases. Contact tracing is usually performed manually by authorized personnel. Manual contact tracing is an inefficient, error-prone, time-consuming process of limited utility to the population at large as those in close contact with infected individuals are informed hours, if not days, later. This paper introduces an alternative way to manual contact tracing. The proposed Smart Contact Tracing (SCT) system utilizes the smartphone's Bluetooth Low Energy (BLE) signals and machine learning classifier to accurately and quickly determined the contact profile. SCT's contribution is two-fold: a) classification of the user's contact as high/low-risk using precise proximity sensing, and b) user anonymity using a privacy-preserving communications protocol. SCT leverages BLE's non-connectable advertising feature to broadcast a signature packet when the user is in the public space. Both broadcasted and observed signatures are stored in the user's smartphone and they are only uploaded to a secure signature database when a user is confirmed by public health authorities to be infected. Using received signal strength (RSS) each smartphone estimates its distance from other user's phones and issues real-time alerts when social distancing rules are violated. The paper includes extensive experimentation utilizing real-life smartphone positions and a comparative evaluation of five machine learning classifiers. Reported results indicate that a decision tree classifier outperforms other states of the art classification methods in terms of accuracy. Lastly, to facilitate research in this area, and to contribute to the timely development of advanced solutions the entire data set of six experiments with about 123,000 data points is made publicly available.
Machine Learning Based Solutions for Security of Internet of Things (IoT): A Survey
Apr 11, 2020
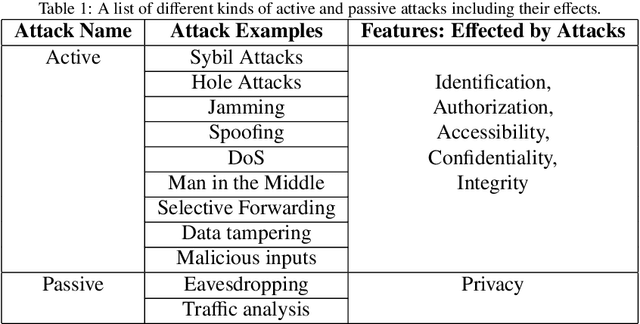
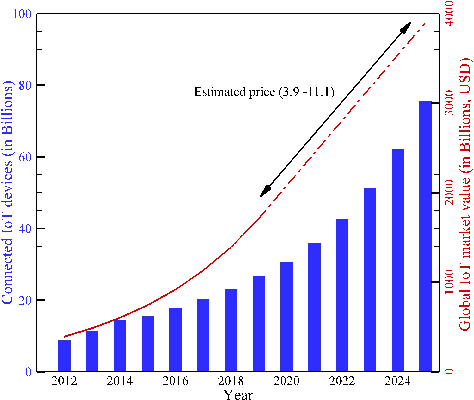
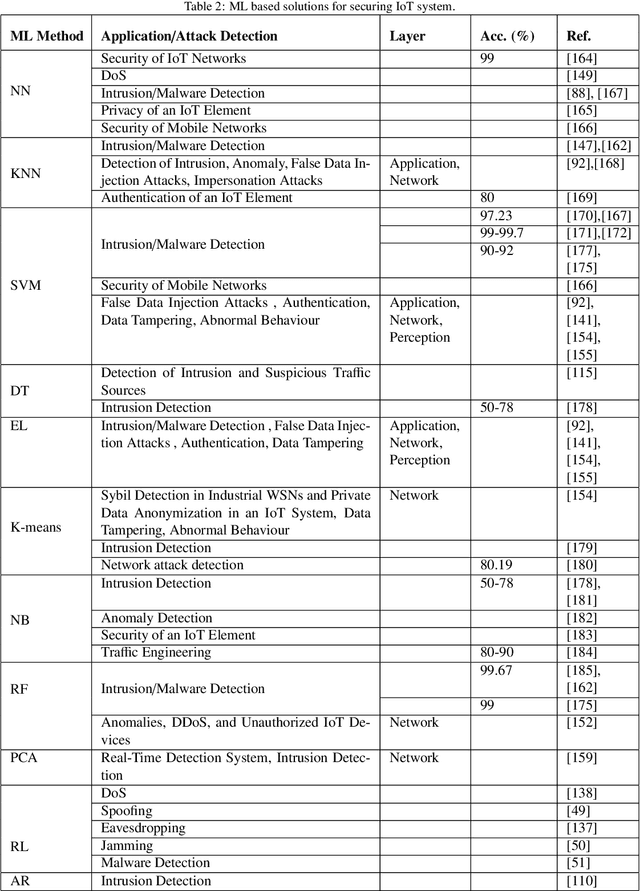
Abstract:Over the last decade, IoT platforms have been developed into a global giant that grabs every aspect of our daily lives by advancing human life with its unaccountable smart services. Because of easy accessibility and fast-growing demand for smart devices and network, IoT is now facing more security challenges than ever before. There are existing security measures that can be applied to protect IoT. However, traditional techniques are not as efficient with the advancement booms as well as different attack types and their severeness. Thus, a strong-dynamically enhanced and up to date security system is required for next-generation IoT system. A huge technological advancement has been noticed in Machine Learning (ML) which has opened many possible research windows to address ongoing and future challenges in IoT. In order to detect attacks and identify abnormal behaviors of smart devices and networks, ML is being utilized as a powerful technology to fulfill this purpose. In this survey paper, the architecture of IoT is discussed, following a comprehensive literature review on ML approaches the importance of security of IoT in terms of different types of possible attacks. Moreover, ML-based potential solutions for IoT security has been presented and future challenges are discussed.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge