Hadis Karimipour
A Deep Multi-Modal Cyber-Attack Detection in Industrial Control Systems
Apr 04, 2023Abstract:The growing number of cyber-attacks against Industrial Control Systems (ICS) in recent years has elevated security concerns due to the potential catastrophic impact. Considering the complex nature of ICS, detecting a cyber-attack in them is extremely challenging and requires advanced methods that can harness multiple data modalities. This research utilizes network and sensor modality data from ICS processed with a deep multi-modal cyber-attack detection model for ICS. Results using the Secure Water Treatment (SWaT) system show that the proposed model can outperform existing single modality models and recent works in the literature by achieving 0.99 precision, 0.98 recall, and 0.98 f-measure, which shows the effectiveness of using both modalities in a combined model for detecting cyber-attacks.
CRL+: A Novel Semi-Supervised Deep Active Contrastive Representation Learning-Based Text Classification Model for Insurance Data
Feb 08, 2023



Abstract:Financial sector and especially the insurance industry collect vast volumes of text on a daily basis and through multiple channels (their agents, customer care centers, emails, social networks, and web in general). The information collected includes policies, expert and health reports, claims and complaints, results of surveys, and relevant social media posts. It is difficult to effectively extract label, classify, and interpret the essential information from such varied and unstructured material. Therefore, the Insurance Industry is among the ones that can benefit from applying technologies for the intelligent analysis of free text through Natural Language Processing (NLP). In this paper, CRL+, a novel text classification model combining Contrastive Representation Learning (CRL) and Active Learning is proposed to handle the challenge of using semi-supervised learning for text classification. In this method, supervised (CRL) is used to train a RoBERTa transformer model to encode the textual data into a contrastive representation space and then classify using a classification layer. This (CRL)-based transformer model is used as the base model in the proposed Active Learning mechanism to classify all the data in an iterative manner. The proposed model is evaluated using unstructured obituary data with objective to determine the cause of the death from the data. This model is compared with the CRL model and an Active Learning model with the RoBERTa base model. The experiment shows that the proposed method can outperform both methods for this specific task.
An Ensemble Deep Convolutional Neural Network Model for Electricity Theft Detection in Smart Grids
Feb 10, 2021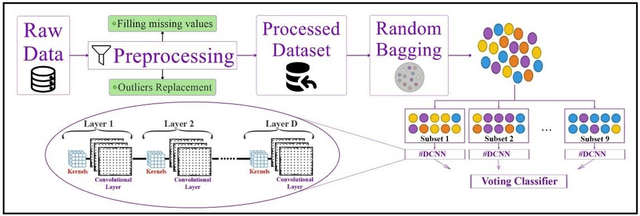


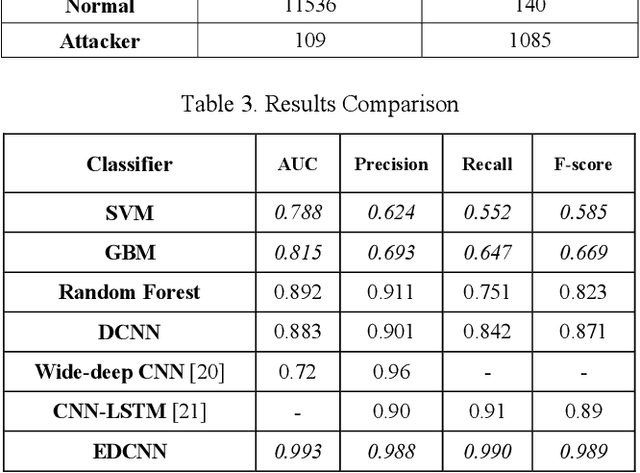
Abstract:Smart grids extremely rely on Information and Communications Technology (ICT) and smart meters to control and manage numerous parameters of the network. However, using these infrastructures make smart grids more vulnerable to cyber threats especially electricity theft. Electricity Theft Detection (EDT) algorithms are typically used for such purpose since this Non-Technical Loss (NTL) may lead to significant challenges in the power system. In this paper, an Ensemble Deep Convolutional Neural Network (EDCNN) algorithm for ETD in smart grids has been proposed. As the first layer of the model, a random under bagging technique is applied to deal with the imbalance data, and then Deep Convolutional Neural Networks (DCNN) are utilized on each subset. Finally, a voting system is embedded, in the last part. The evaluation results based on the Area Under Curve (AUC), precision, recall, f1-score, and accuracy verify the efficiency of the proposed method compared to the existing method in the literature.
Machine Learning Based Solutions for Security of Internet of Things (IoT): A Survey
Apr 11, 2020
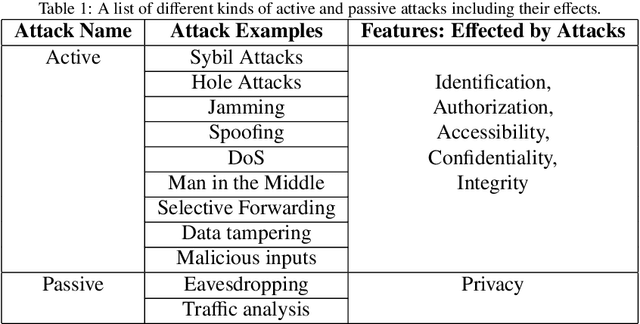
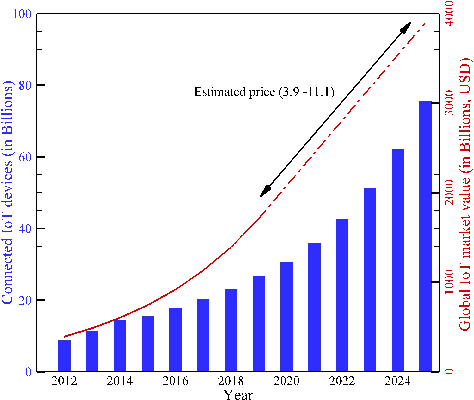
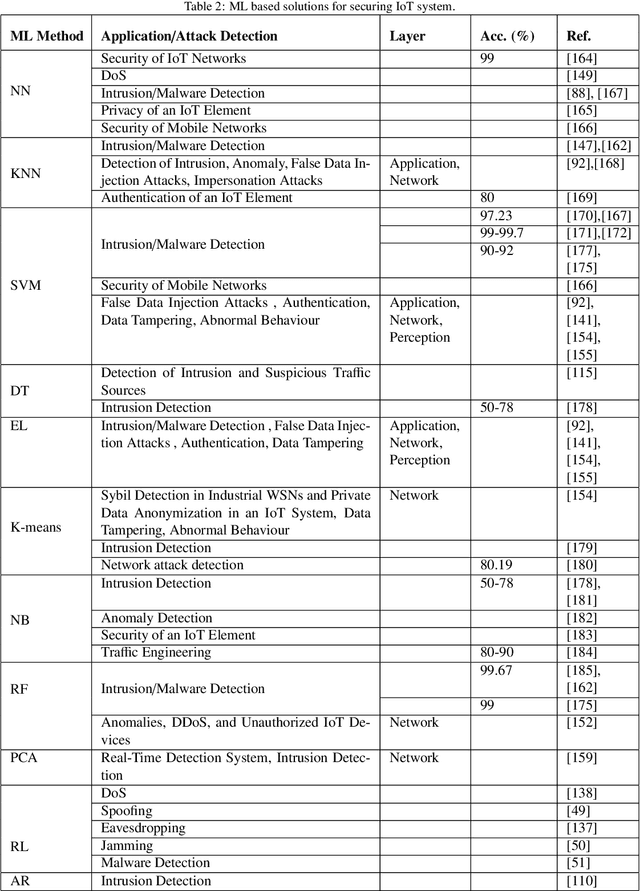
Abstract:Over the last decade, IoT platforms have been developed into a global giant that grabs every aspect of our daily lives by advancing human life with its unaccountable smart services. Because of easy accessibility and fast-growing demand for smart devices and network, IoT is now facing more security challenges than ever before. There are existing security measures that can be applied to protect IoT. However, traditional techniques are not as efficient with the advancement booms as well as different attack types and their severeness. Thus, a strong-dynamically enhanced and up to date security system is required for next-generation IoT system. A huge technological advancement has been noticed in Machine Learning (ML) which has opened many possible research windows to address ongoing and future challenges in IoT. In order to detect attacks and identify abnormal behaviors of smart devices and networks, ML is being utilized as a powerful technology to fulfill this purpose. In this survey paper, the architecture of IoT is discussed, following a comprehensive literature review on ML approaches the importance of security of IoT in terms of different types of possible attacks. Moreover, ML-based potential solutions for IoT security has been presented and future challenges are discussed.
Smart Households Demand Response Management with Micro Grid
Jul 08, 2019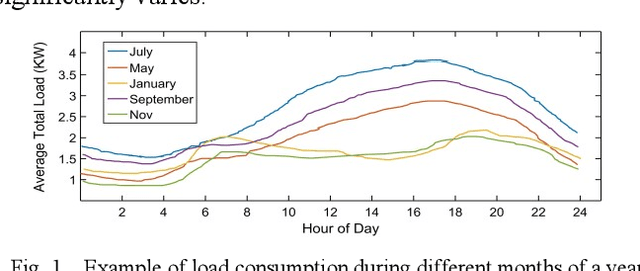
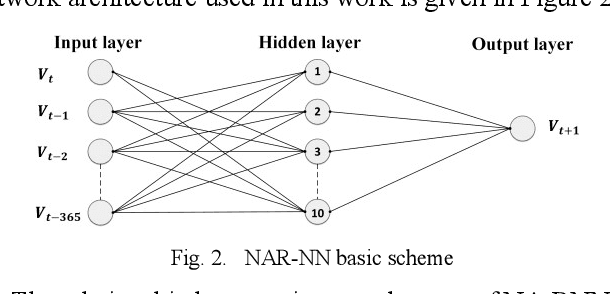
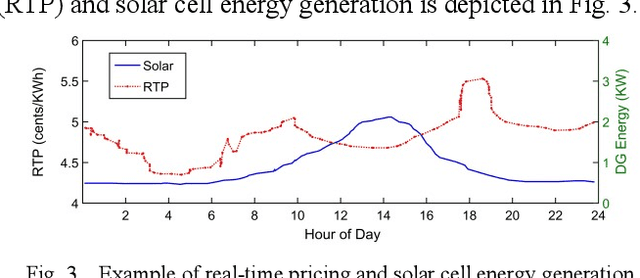
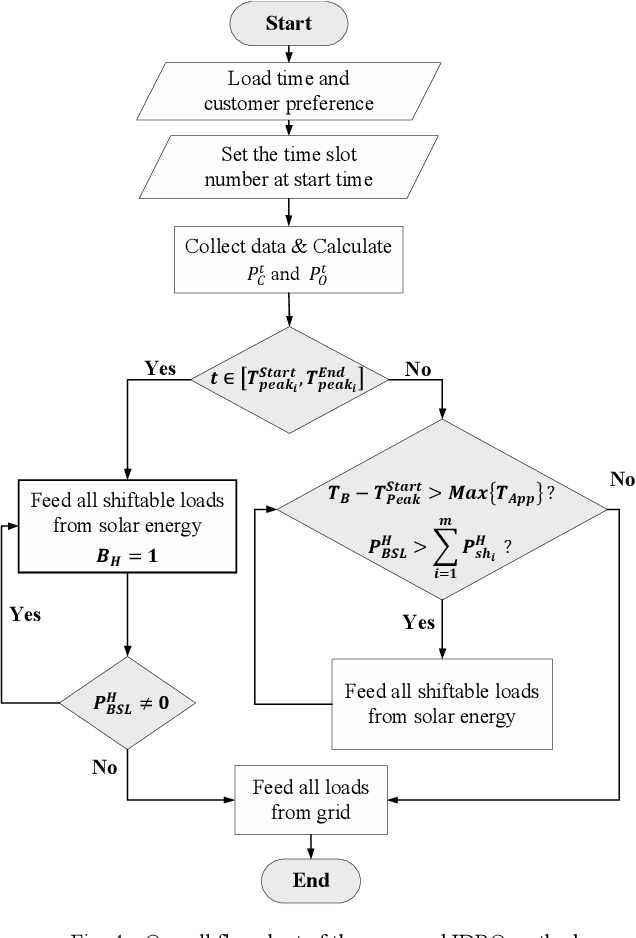
Abstract:Nowadays the emerging smart grid technology opens up the possibility of two-way communication between customers and energy utilities. Demand Response Management (DRM) offers the promise of saving money for commercial customers and households while helps utilities operate more efficiently. In this paper, an Incentive-based Demand Response Optimization (IDRO) model is proposed to efficiently schedule household appliances for minimum usage during peak hours. The proposed method is a multi-objective optimization technique based on Nonlinear Auto-Regressive Neural Network (NAR-NN) which considers energy provided by the utility and rooftop installed photovoltaic (PV) system. The proposed method is tested and verified using 300 case studies (household). Data analysis for a period of one year shows a noticeable improvement in power factor and customers bill.
Smart Grid Cyber Attacks Detection using Supervised Learning and Heuristic Feature Selection
Jul 07, 2019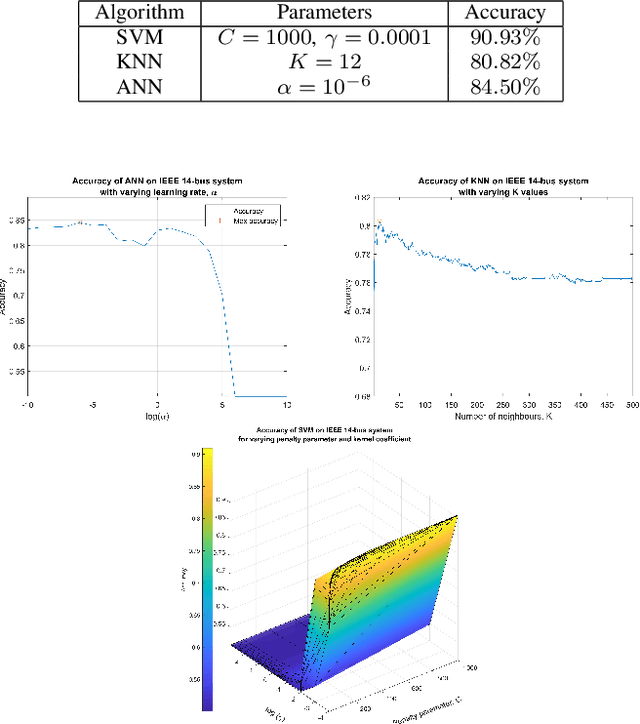

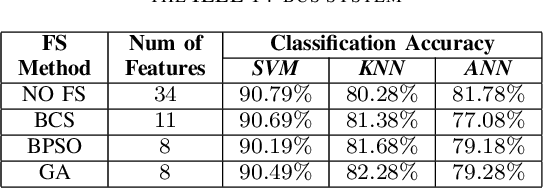
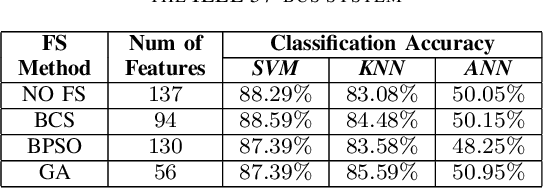
Abstract:False Data Injection (FDI) attacks are a common form of Cyber-attack targetting smart grids. Detection of stealthy FDI attacks is impossible by the current bad data detection systems. Machine learning is one of the alternative methods proposed to detect FDI attacks. This paper analyzes three various supervised learning techniques, each to be used with three different feature selection (FS) techniques. These methods are tested on the IEEE 14-bus, 57-bus, and 118-bus systems for evaluation of versatility. Accuracy of the classification is used as the main evaluation method for each detection technique. Simulation study clarify the supervised learning combined with heuristic FS methods result in an improved performance of the classification algorithms for FDI attack detection.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge