Arsenia Chorti
Misspecified Crame-Rao Bound for AoA Estimation at a ULA under a Spoofing Attack
Dec 18, 2025


Abstract:A framework is presented for analyzing the impact of active attacks to location-based physical layer authentication (PLA) using the machinery of misspecified Cramér--Rao bound (MCRB). In this work, we focus on the MCRB in the angle-of-arrival (AoA) based authentication of a single antenna user when the verifier posseses an $M$ antenna element uniform linear array (ULA), assuming deterministic pilot signals; in our system model the presence of a spoofing adversary with an arbitrary number $L$ of antenna elements is assumed. We obtain a closed-form expression for the MCRB and demonstrate that the attack introduces in it a penalty term compared to the classic CRB, which does not depend on the signal-to-noise ratio (SNR) but on the adversary's location, the array geometry and the attacker precoding vector.
Channel State Information Preprocessing for CSI-based Physical-Layer Authentication Using Reconciliation
Dec 18, 2025



Abstract:This paper introduces an adaptive preprocessing technique to enhance the accuracy of channel state information-based physical layer authentication (CSI-PLA) alleviating CSI variations and inconsistencies in the time domain. To this end, we develop an adaptive robust principal component analysis (A-RPCA) preprocessing method based on robust principal component analysis (RPCA). The performance evaluation is then conducted using a PLA framework based on information reconciliation, in which Gaussian approximation (GA) for Polar codes is leveraged for the design of short codelength Slepian Wolf decoders. Furthermore, an analysis of the proposed A-RPCA methods is carried out. Simulation results show that compared to a baseline scheme without preprocessing and without reconciliation, the proposed A-RPCA method substantially reduces the error probability after reconciliation and also substantially increases the detection probabilities that is also 1 in both line-of-sight (LOS) and non-line-of-sight (NLOS) scenarios. We have compared against state-of the-art preprocessing schemes in both synthetic and real datasets, including principal component analysis (PCA) and robust PCA, autoencoders and the recursive projected compressive sensing (ReProCS) framework and we have validated the superior performance of the proposed approach.
AoA-Based Physical Layer Authentication in Analog Arrays under Impersonation Attacks
Jul 11, 2024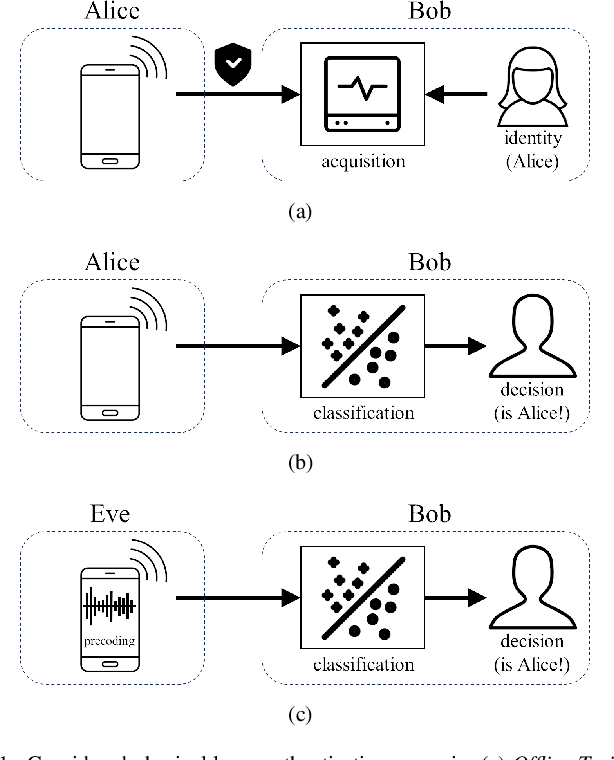
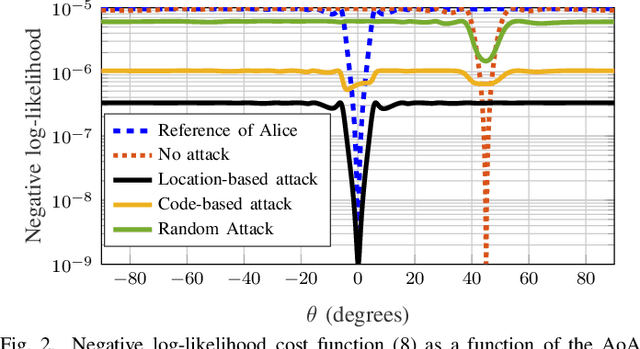
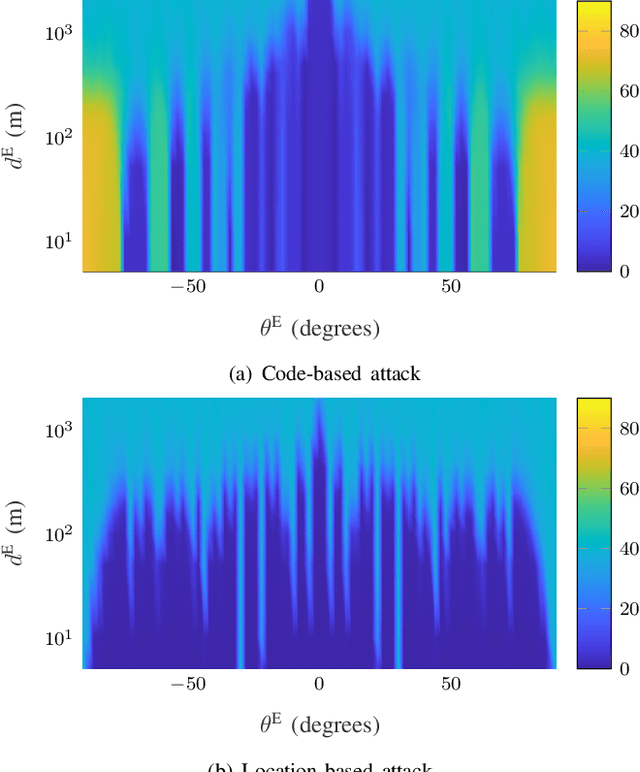
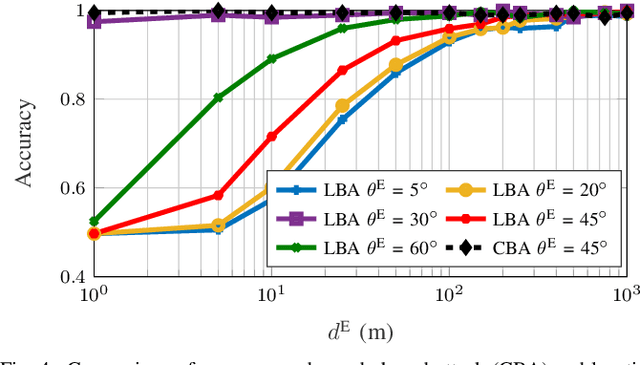
Abstract:We discuss the use of angle of arrival (AoA) as an authentication measure in analog array multiple-input multiple-output (MIMO) systems. A base station equipped with an analog array authenticates users based on the AoA estimated from certified pilot transmissions, while active attackers manipulate their transmitted signals to mount impersonation attacks. We study several attacks of increasing intensity (captured through the availability of side information at the attackers) and assess the performance of AoA-based authentication using one-class classifiers. Our results show that some attack techniques with knowledge of the combiners at the verifier are effective in falsifying the AoA and compromising the security of the considered type of physical layer authentication.
Secret Key Generation Rates for Line of Sight Multipath Channels in the Presence of Eavesdroppers
Apr 25, 2024



Abstract:In this paper, the feasibility of implementing a lightweight key distribution scheme using physical layer security for secret key generation (SKG) is explored. Specifically, we focus on examining SKG with the received signal strength (RSS) serving as the primary source of shared randomness. Our investigation centers on a frequency-selective line-of-sight (LoS) multipath channel, with a particular emphasis on assessing SKG rates derived from the distributions of RSS. We derive the received signal distributions based on how the multipath components resolve at the receiver. The mutual information (MI) is evaluated based on LoS 3GPP channel models using a numerical estimator. We study how the bandwidth, delay spread, and Rician K-factor impact the estimated MI. This MI then serves as a benchmark setting bounds for the SKG rates in our exploration.
Physical Layer Authentication Using Information Reconciliation
Apr 19, 2024Abstract:User authentication in future wireless communication networks is expected to become more complicated due to their large scale and heterogeneity. Furthermore, the computational complexity of classical cryptographic approaches based on public key distribution can be a limiting factor for using in simple, low-end Internet of things (IoT) devices. This paper proposes physical layer authentication (PLA) expected to complement existing traditional approaches, e.g., in multi-factor authentication protocols. The precision and consistency of PLA is impacted because of random variations of wireless channel realizations between different time slots, which can impair authentication performance. In order to address this, a method based on error-correcting codes in the form of reconciliation is considered in this work. In particular, we adopt distributed source coding (Slepian-Wolf) reconciliation using polar codes to reconcile channel measurements spread in time. Hypothesis testing is then applied to the reconciled vectors to accept or reject the device as authenticated. Simulation results show that the proposed PLA using reconciliation outperforms prior schemes even in low signal-to-noise ratio scenarios.
How Physicality Enables Trust: A New Era of Trust-Centered Cyberphysical Systems
Nov 13, 2023



Abstract:Multi-agent cyberphysical systems enable new capabilities in efficiency, resilience, and security. The unique characteristics of these systems prompt a reevaluation of their security concepts, including their vulnerabilities, and mechanisms to mitigate these vulnerabilities. This survey paper examines how advancement in wireless networking, coupled with the sensing and computing in cyberphysical systems, can foster novel security capabilities. This study delves into three main themes related to securing multi-agent cyberphysical systems. First, we discuss the threats that are particularly relevant to multi-agent cyberphysical systems given the potential lack of trust between agents. Second, we present prospects for sensing, contextual awareness, and authentication, enabling the inference and measurement of ``inter-agent trust" for these systems. Third, we elaborate on the application of quantifiable trust notions to enable ``resilient coordination," where ``resilient" signifies sustained functionality amid attacks on multiagent cyberphysical systems. We refer to the capability of cyberphysical systems to self-organize, and coordinate to achieve a task as autonomy. This survey unveils the cyberphysical character of future interconnected systems as a pivotal catalyst for realizing robust, trust-centered autonomy in tomorrow's world.
Smart Channel State Information Pre-processing for Joint Authentication and Secret Key Distillation
Jun 01, 2022
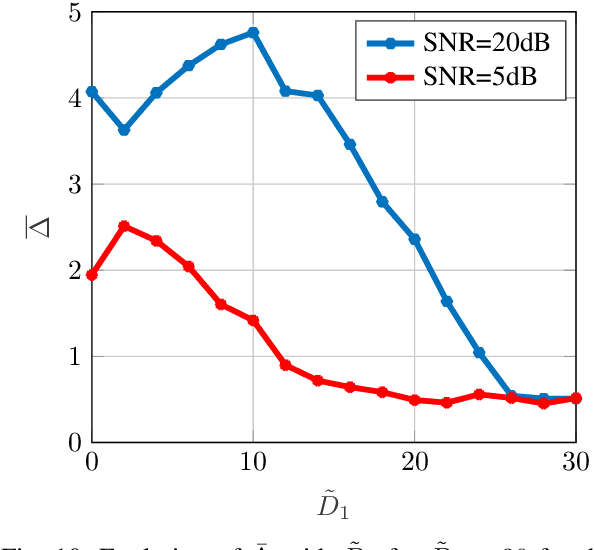
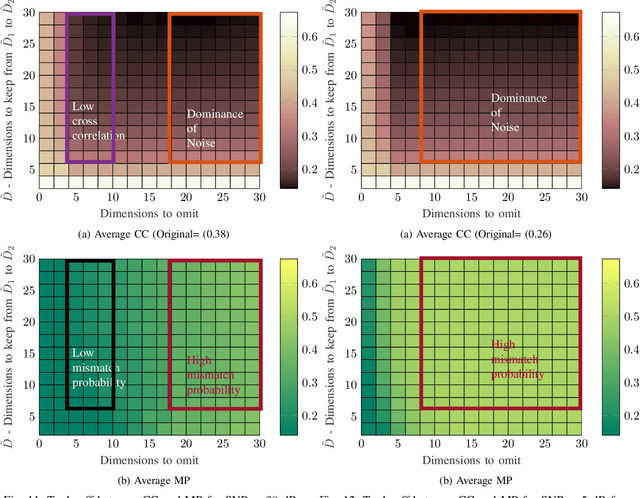
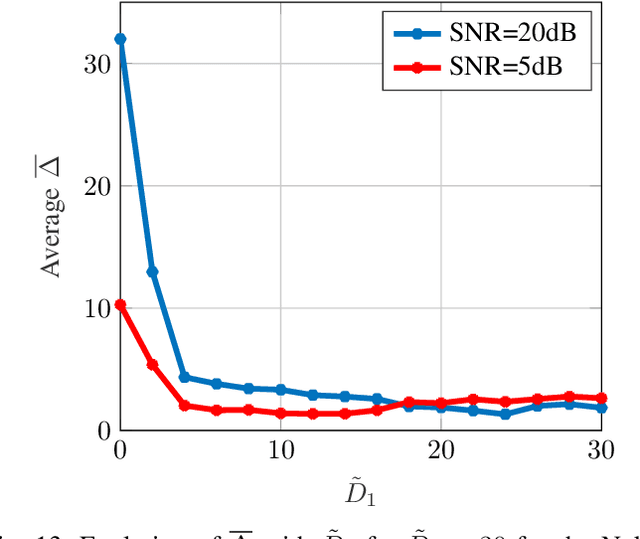
Abstract:While the literature on RF fingerprinting-based authentication and key distillation is vast, the two topics have customarily been studied separately. In this paper, starting from the observation that the wireless channel is a composite, deterministic / stochastic process, we propose a power domain decomposition that allows performing the two tasks simultaneously. We devise intelligent pre-processing schemes to decompose channel state information (CSI) observation vectors into "predictable" and "unpredictable" components. The former, primarily due to large-scale fading, can be used for node authentication through RF fingerprinting. The latter, primarily due to small-scale fading, could be used for semantically secure secret key generation (SKG). To perform the decomposition, we propose: (i) a fingerprint "separability" criterion, expressed through the maximisation of the total variation distance between the empirical fingerprint measures; (ii) a statistical independence metric for observations collected at different users, expressed through a normalised version of the $d$-dimensional Hilbert Schmidt independence criterion (dHSIC) test statistic. We propose both explicit implementations, using principal component analysis (PCA) and kernel PCA and black-box, unsupervised learning, using autoencoders. Our experiments on synthetic and real CSI datasets showcase that the incorporation of RF fingerprinting and SKG, with explicit security guarantees, is tangible in future generations of wireless.
Physical Layer Security for 6G Systems why it is needed and how to make it happen
May 03, 2022Abstract:Sixth generations (6G) systems will be required to meet diverse constraints in an integrated ground-air-space global network. In particular, meeting overly aggressive latency constraints, operating in massive connectivity regimes, with low energy footprint and low computational effort, while providing explicit security guarantees, can be challenging. In this setting, quality of security (QoSec) is envisioned as a flexible security framework for future networks with highly diverse non-functional requirements. Mirroring the differentiated services (DiffServ) networking paradigm, different security levels could be conceptualized, moving away from static security controls, captured currently in zero-trust security architectures. In parallel, the integration of communications and sensing, along with embedded (on-device) AI, can provide the foundations for building autonomous and adaptive security controls, orchestrated by a vertical security plane in coordination with a vertical semantic plane. It is in this framework, that we envision the incorporation of physical layer security (PLS) schemes in 6G security protocols, introducing security controls at all layers, for the first time.
On the Use of CSI for the Generation of RF Fingerprints and Secret Keys
Oct 28, 2021



Abstract:This paper presents a systematic approach to use channel state information for authentication and secret key distillation for physical layer security (PLS). We use popular machine learning (ML) methods and signal processing-based approaches to disentangle the large scale fading and be used as a source of uniqueness, from the small scale fading, to be treated as a source of shared entropy secret key generation (SKG). The ML-based approaches are completely unsupervised and hence avoid exhaustive measurement campaigns. We also propose using the Hilbert Schmidt independence criterion (HSIC); our simulation results demonstrate that the extracted stochastic part of the channel state information (CSI) vectors are statistically independent.
Finite Blocklength Secrecy Analysis of Polar and Reed-Muller Codes in BEC Semi-Deterministic Wiretap Channels
May 22, 2021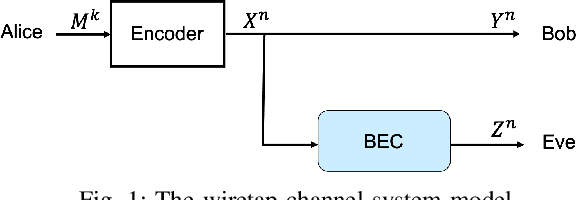
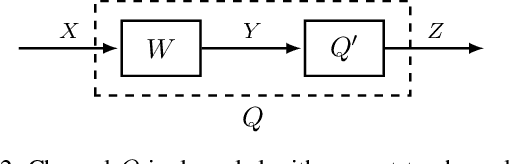
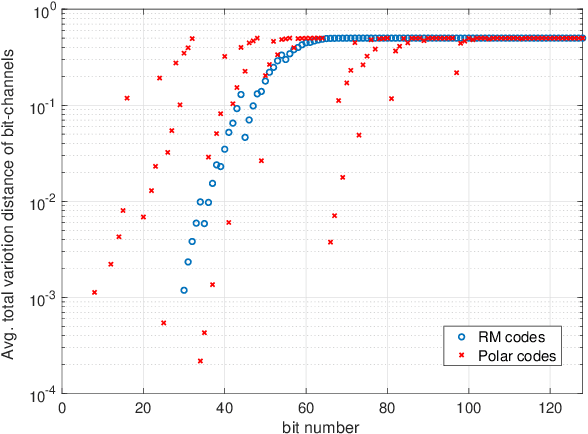
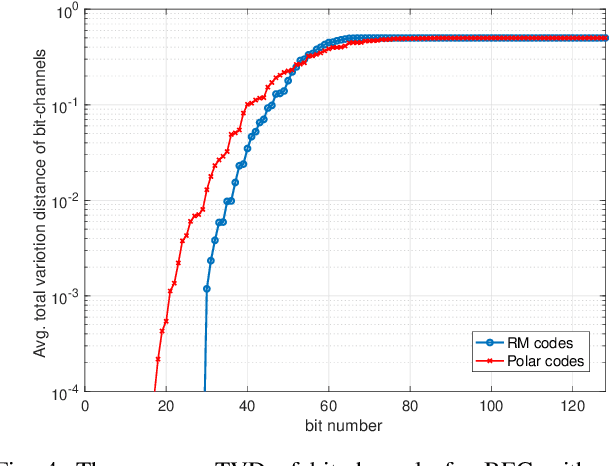
Abstract:In this paper, we consider a semi-deterministic wiretap channel where the main channel is noiseless and the eavesdropper's channel is a binary erasure channel (BEC). We provide a lower bound for the achievable secrecy rates of polar and Reed Muller codes and compare it to the second order coding rate for the semi-deterministic wiretap channel. To the best of our knowledge, this is the first work which demonstrates the secrecy performance of polar and Reed-Muller codes in short blocklengths. The results show that under a total variation secrecy metric, Reed Muller codes can achieve secrecy rates very close to the second order approximation rate. On the other hand, we observe a significant gap between the lower bound for the achievable rates of polar codes and the the second order approximation rate for short blocklengths.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge