Marco Baldi
AoA-Based Physical Layer Authentication in Analog Arrays under Impersonation Attacks
Jul 11, 2024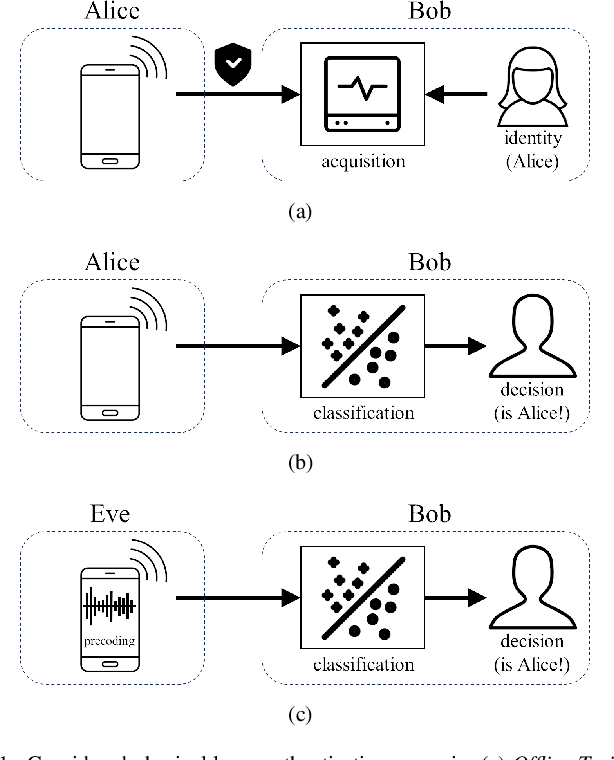
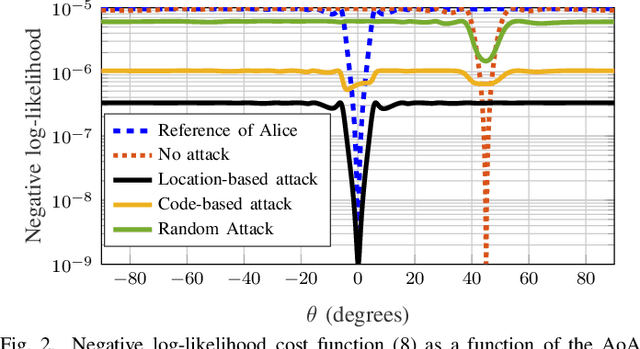
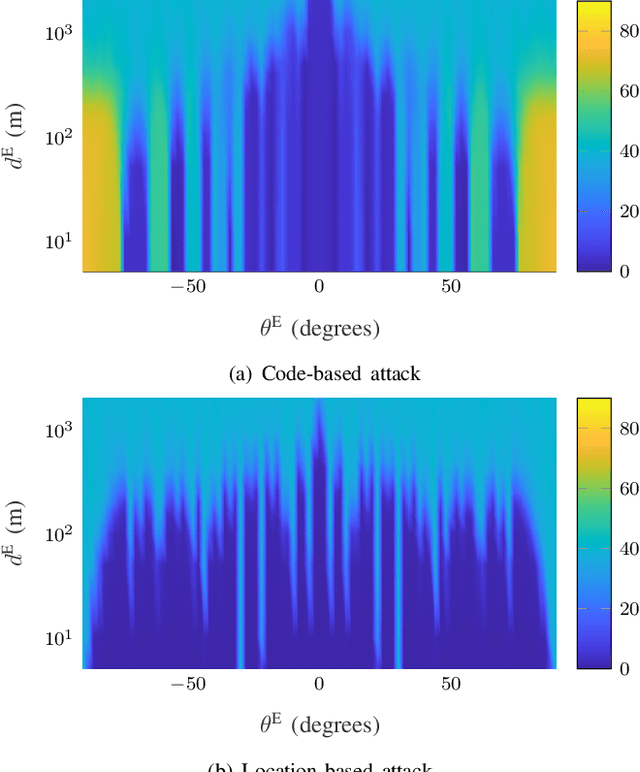
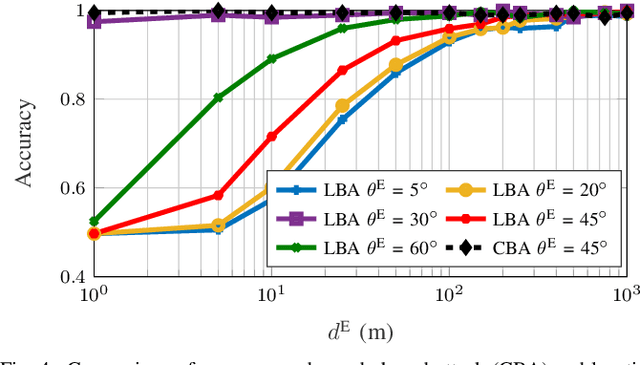
Abstract:We discuss the use of angle of arrival (AoA) as an authentication measure in analog array multiple-input multiple-output (MIMO) systems. A base station equipped with an analog array authenticates users based on the AoA estimated from certified pilot transmissions, while active attackers manipulate their transmitted signals to mount impersonation attacks. We study several attacks of increasing intensity (captured through the availability of side information at the attackers) and assess the performance of AoA-based authentication using one-class classifiers. Our results show that some attack techniques with knowledge of the combiners at the verifier are effective in falsifying the AoA and compromising the security of the considered type of physical layer authentication.
When Does Your Brain Know You? Segment Length and Its Impact on EEG-based Biometric Authentication Accuracy
Mar 19, 2024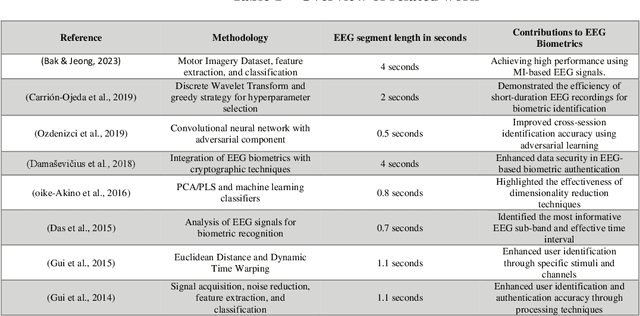
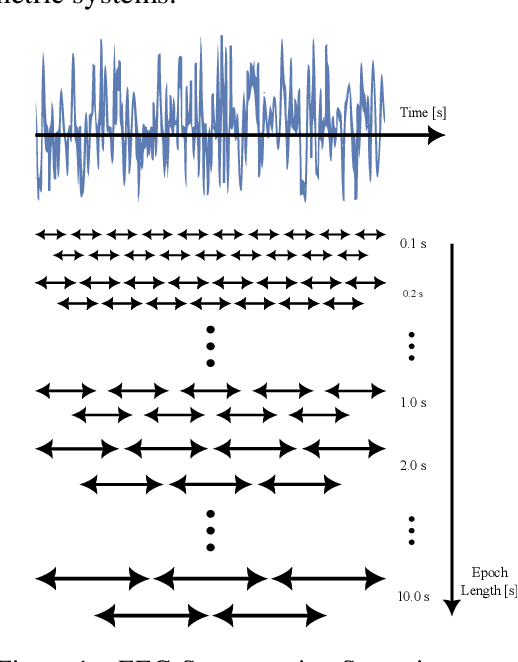
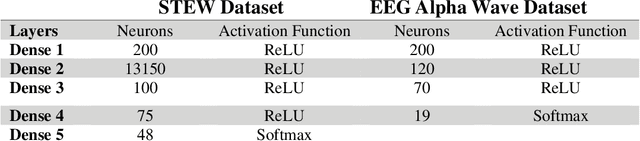
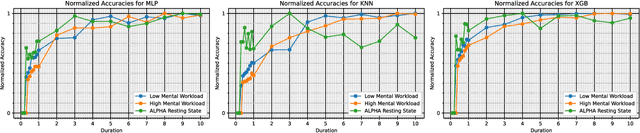
Abstract:In the quest for optimal EEG-based biometric authentication, this study investigates the pivotal balance for accurate identification without sacrificing performance or adding unnecessary computational complexity. Through a methodical exploration of segment durations, and employing a variety of sophisticated machine learning models, the research seeks to pinpoint a threshold where EEG data provides maximum informational yield for authentication purposes. The findings are set to advance the field of non-invasive biometric technologies, proposing a practical approach to secure and user-friendly identity verification systems while also raising considerations for the real-world application of EEG-based biometric authentication beyond controlled environments.
Using Graph Theory for Improving Machine Learning-based Detection of Cyber Attacks
Feb 12, 2024Abstract:Early detection of network intrusions and cyber threats is one of the main pillars of cybersecurity. One of the most effective approaches for this purpose is to analyze network traffic with the help of artificial intelligence algorithms, with the aim of detecting the possible presence of an attacker by distinguishing it from a legitimate user. This is commonly done by collecting the traffic exchanged between terminals in a network and analyzing it on a per-packet or per-connection basis. In this paper, we propose instead to perform pre-processing of network traffic under analysis with the aim of extracting some new metrics on which we can perform more efficient detection and overcome some limitations of classical approaches. These new metrics are based on graph theory, and consider the network as a whole, rather than focusing on individual packets or connections. Our approach is validated through experiments performed on publicly available data sets, from which it results that it can not only overcome some of the limitations of classical approaches, but also achieve a better detection capability of cyber threats.
Performance of Statistical and Machine Learning Techniques for Physical Layer Authentication
Jan 17, 2020



Abstract:In this paper we consider authentication at the physical layer, in which the authenticator aims at distinguishing a legitimate supplicant from an attacker on the basis of the characteristics of the communication channel. Authentication is performed over a set of parallel wireless channels affected by time-varying fading at the presence of a malicious attacker, whose channel has a spatial correlation with the supplicant's one. We first propose the use of two different statistical decision methods, and we prove that using a large number of references (in the form of channel estimates) affected by different levels of time-varying fading is not beneficial from a security point of view. We then propose to exploit classification methods based on machine learning. In order to face the worst case of an authenticator provided with no forged messages during training, we consider one-class classifiers. When instead the training set includes some forged messages, we resort to more conventional binary classifiers, considering the cases in which such messages are either labelled or not. For the latter case, we exploit clustering algorithms to label the training set. The performance of both nearest neighbor (NN) and support vector machine (SVM) classification techniques is assessed. Through numerical examples, we show that under the same probability of false alarm, one-class classification (OCC) algorithms achieve the lowest probability of missed detection when a small spatial correlation exists between the main channel and the adversary one, while statistical methods are advantageous when the spatial correlation between the two channels is large.
Statistical and Machine Learning-based Decision Techniques for Physical Layer Authentication
Sep 16, 2019



Abstract:In this paper we assess the security performance of key-less physical layer authentication schemes in the case of time-varying fading channels, considering both partial and no channel state information (CSI) on the receiver's side. We first present a generalization of a well-known protocol previously proposed for flat fading channels and we study different statistical decision methods and the corresponding optimal attack strategies in order to improve the authentication performance in the considered scenario. We then consider the application of machine learning techniques in the same setting, exploiting different one-class nearest neighbor (OCNN) classification algorithms. We observe that, under the same probability of false alarm, one-class classification (OCC) algorithms achieve the lowest probability of missed detection when a low spatial correlation exists between the main channel and the adversary one, while statistical methods are advantageous when the spatial correlation between the two channels is higher.
On the dissection of degenerate cosmologies with machine learning
Oct 25, 2018



Abstract:Based on the DUSTGRAIN-pathfinder suite of simulations, we investigate observational degeneracies between nine models of modified gravity and massive neutrinos. Three types of machine learning techniques are tested for their ability to discriminate lensing convergence maps by extracting dimensional reduced representations of the data. Classical map descriptors such as the power spectrum, peak counts and Minkowski functionals are combined into a joint feature vector and compared to the descriptors and statistics that are common to the field of digital image processing. To learn new features directly from the data we use a Convolutional Neural Network (CNN). For the mapping between feature vectors and the predictions of their underlying model, we implement two different classifiers; one based on a nearest-neighbour search and one that is based on a fully connected neural network. We find that the neural network provides a much more robust classification than the nearest-neighbour approach and that the CNN provides the most discriminating representation of the data. It achieves the cleanest separation between the different models and the highest classification success rate of 59% for a single source redshift. Once we perform a tomographic CNN analysis, the total classification accuracy increases significantly to 76% with no observational degeneracies remaining. Visualising the filter responses of the CNN at different network depths provides us with the unique opportunity to learn from very complex models and to understand better why they perform so well.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge