Muralikrishnan Srinivasan
AoA-Based Physical Layer Authentication in Analog Arrays under Impersonation Attacks
Jul 11, 2024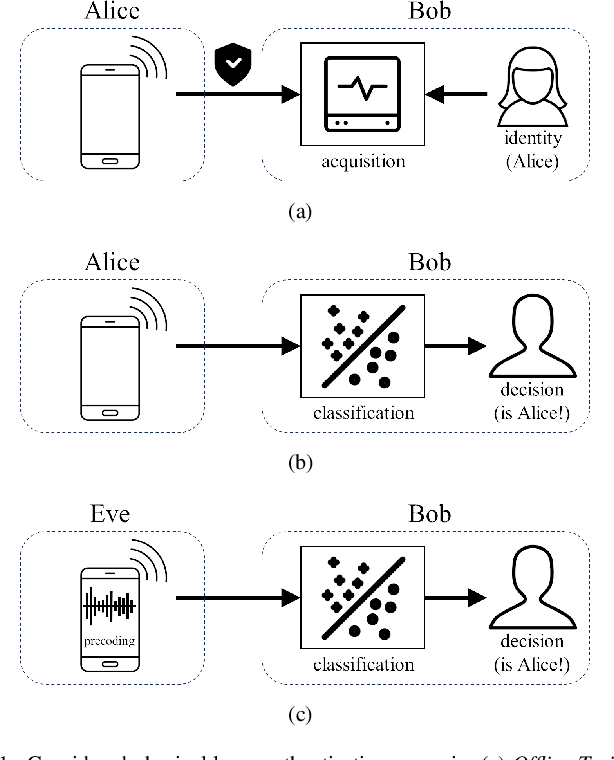
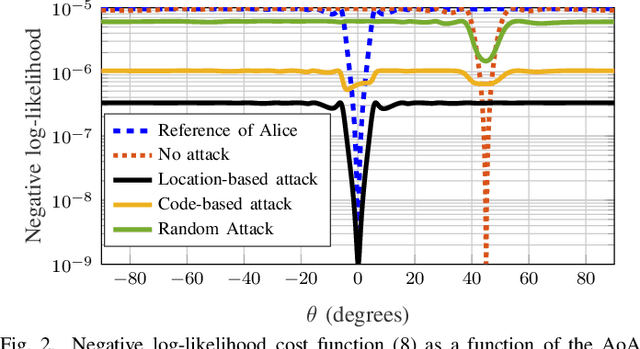
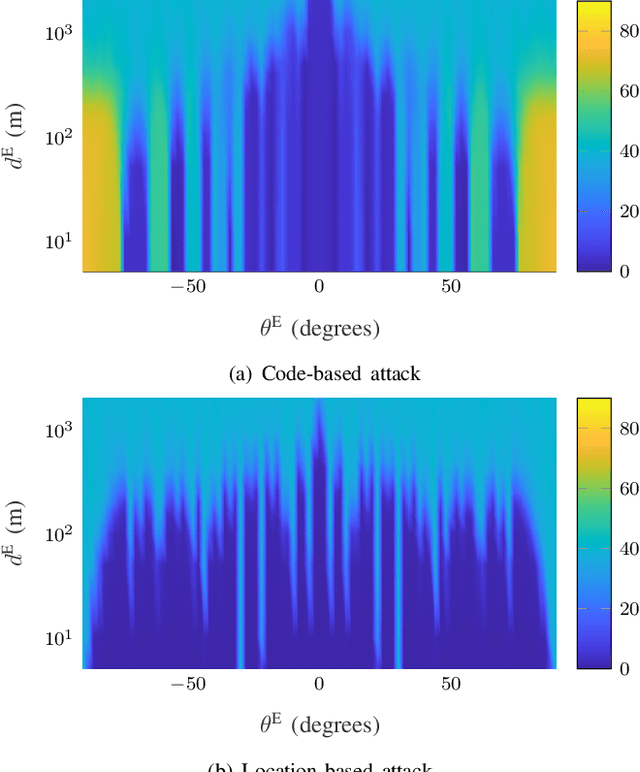
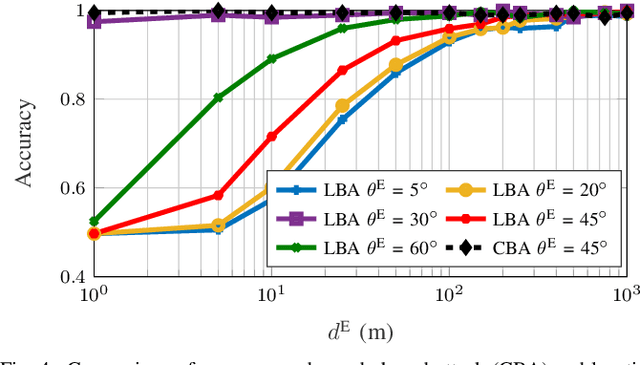
Abstract:We discuss the use of angle of arrival (AoA) as an authentication measure in analog array multiple-input multiple-output (MIMO) systems. A base station equipped with an analog array authenticates users based on the AoA estimated from certified pilot transmissions, while active attackers manipulate their transmitted signals to mount impersonation attacks. We study several attacks of increasing intensity (captured through the availability of side information at the attackers) and assess the performance of AoA-based authentication using one-class classifiers. Our results show that some attack techniques with knowledge of the combiners at the verifier are effective in falsifying the AoA and compromising the security of the considered type of physical layer authentication.
Smart Channel State Information Pre-processing for Joint Authentication and Secret Key Distillation
Jun 01, 2022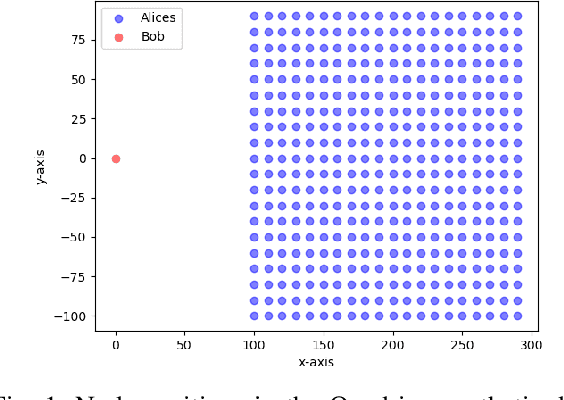
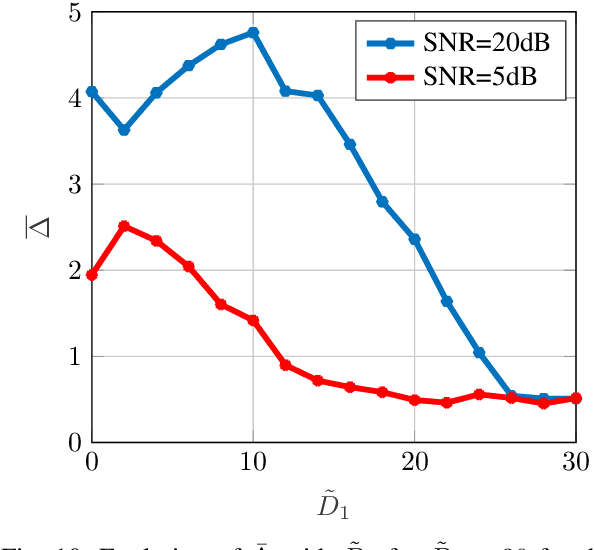
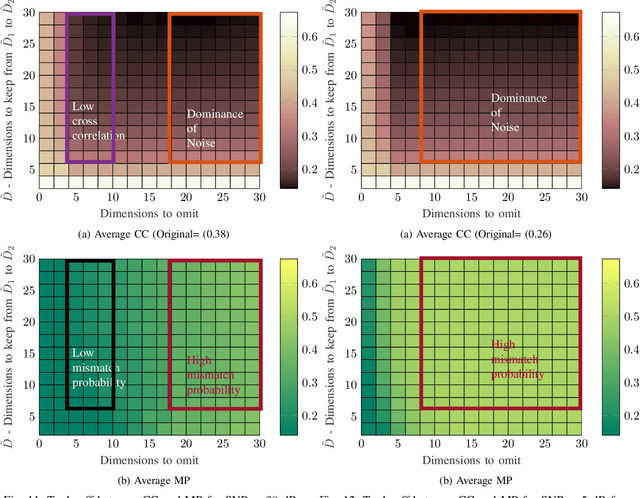
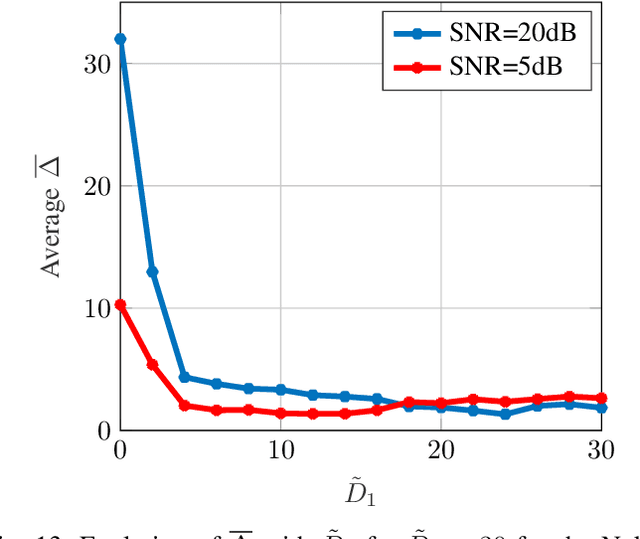
Abstract:While the literature on RF fingerprinting-based authentication and key distillation is vast, the two topics have customarily been studied separately. In this paper, starting from the observation that the wireless channel is a composite, deterministic / stochastic process, we propose a power domain decomposition that allows performing the two tasks simultaneously. We devise intelligent pre-processing schemes to decompose channel state information (CSI) observation vectors into "predictable" and "unpredictable" components. The former, primarily due to large-scale fading, can be used for node authentication through RF fingerprinting. The latter, primarily due to small-scale fading, could be used for semantically secure secret key generation (SKG). To perform the decomposition, we propose: (i) a fingerprint "separability" criterion, expressed through the maximisation of the total variation distance between the empirical fingerprint measures; (ii) a statistical independence metric for observations collected at different users, expressed through a normalised version of the $d$-dimensional Hilbert Schmidt independence criterion (dHSIC) test statistic. We propose both explicit implementations, using principal component analysis (PCA) and kernel PCA and black-box, unsupervised learning, using autoencoders. Our experiments on synthetic and real CSI datasets showcase that the incorporation of RF fingerprinting and SKG, with explicit security guarantees, is tangible in future generations of wireless.
Joint Power-control and Antenna Selection in User-Centric Cell-Free Systems with Mixed Resolution ADC
Dec 16, 2021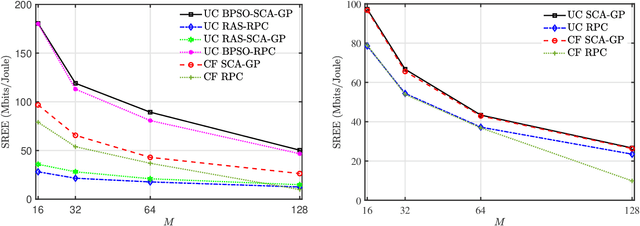
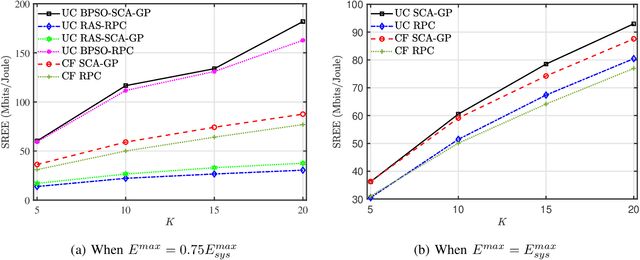
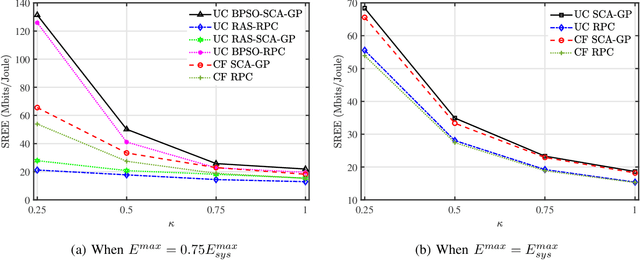
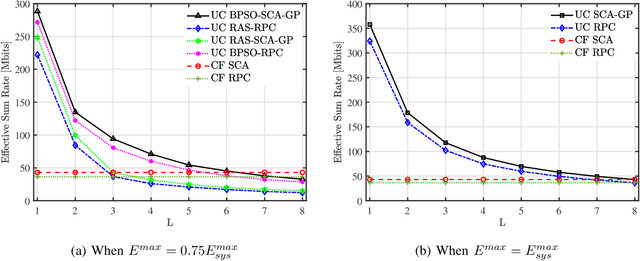
Abstract:In this paper, we propose a scheme for the joint optimization of the user transmit power and the antenna selection at the access points (AP)s of a user-centric cell-free massive multiple-input-multiple-output (UC CF-mMIMO) system. We derive an approximate expression for the achievable uplink rate of the users in a UC CF-mMIMO system in the presence of a mixed analog-to-digital converter (ADC) resolution profile at the APs. Using the derived approximation, we propose to maximize the uplink sum rate of UC CF-mMIMO systems subject to energy constraints at the APs. An alternating-optimization solution is proposed using binary particle swarm optimization (BPSO) and successive convex approximation (SCA). We also study the impact of various system parameters on the performance of the system.
On the Use of CSI for the Generation of RF Fingerprints and Secret Keys
Oct 28, 2021



Abstract:This paper presents a systematic approach to use channel state information for authentication and secret key distillation for physical layer security (PLS). We use popular machine learning (ML) methods and signal processing-based approaches to disentangle the large scale fading and be used as a source of uniqueness, from the small scale fading, to be treated as a source of shared entropy secret key generation (SKG). The ML-based approaches are completely unsupervised and hence avoid exhaustive measurement campaigns. We also propose using the Hilbert Schmidt independence criterion (HSIC); our simulation results demonstrate that the extracted stochastic part of the channel state information (CSI) vectors are statistically independent.
Airplane-Aided Integrated Next-Generation Networking
Jan 03, 2021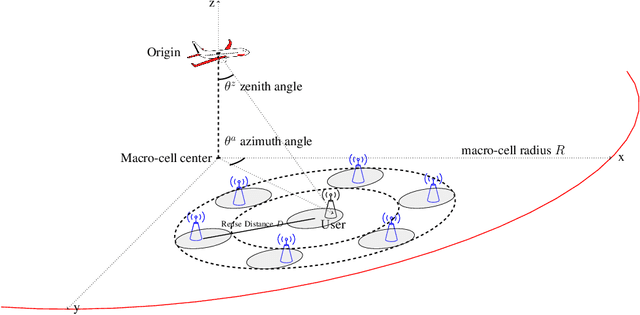
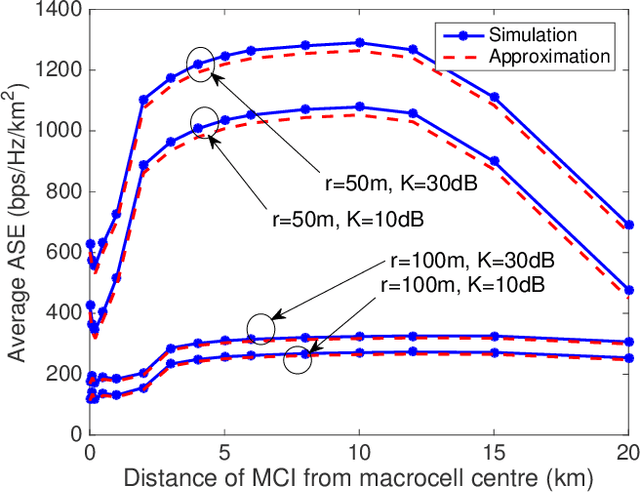
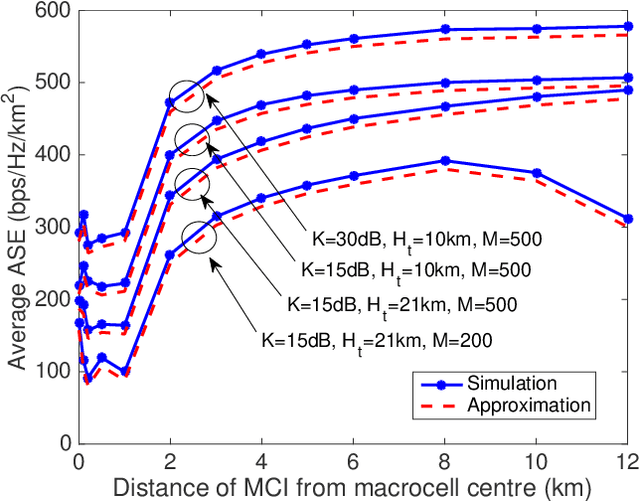
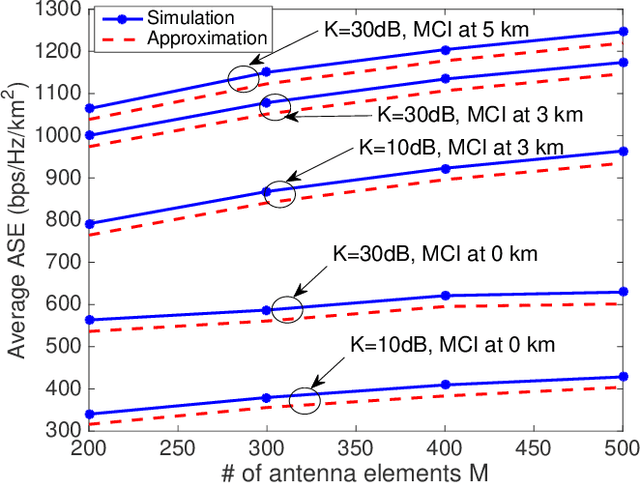
Abstract:A high-rate yet low-cost air-to-ground (A2G) communication backbone is conceived for integrating the space and terrestrial network by harnessing the opportunistic assistance of the passenger planes or high altitude platforms (HAPs) as mobile base stations (BSs) and millimetre wave communication. The airliners act as the network-provider for the terrestrial users while relying on satellite backhaul. A null-steered beamforming technique relying on a large-scale planar array is used for transmission by the airliner/HAP for achieving a high directional gain, hence minimizing the interference between the users. Furthermore, approximate spectral efficiency (SE) and area spectral efficiency (ASE) expressions are derived and quantified for diverse system parameters.
What is the optimal depth for deep-unfolding architectures at deployment?
Mar 20, 2020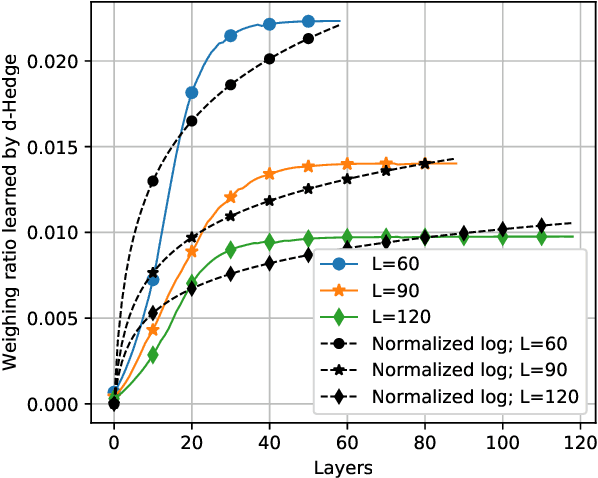
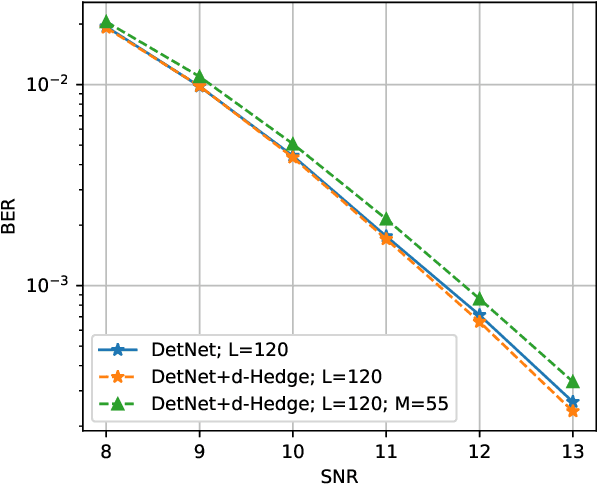
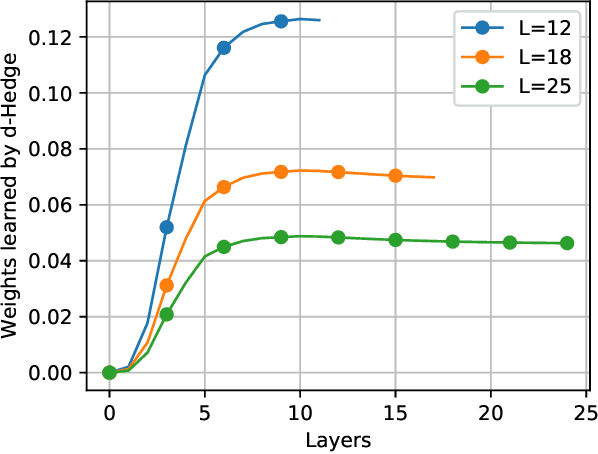
Abstract:Recently, many iterative algorithms proposed for various applications such as compressed sensing, MIMO Detection, etc. have been unfolded and presented as deep networks; these networks are shown to produce better results than the algorithms in their iterative forms. However, deep networks are highly sensitive to the hyperparameters chosen. Especially for a deep unfolded network, using more layers may lead to redundancy and hence, excessive computation during deployment. In this work, we consider the problem of determining the optimal number of layers required for such unfolded architectures. We propose a method that treats the networks as experts and measures the relative importance of the expertise provided by layers using a variant of the popular Hedge algorithm. Based on the importance of the different layers, we determine the optimal layers required for deployment. We study the effectiveness of this method by applying it to two recent and popular deep-unfolding architectures, namely DetNet and TISTANet.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge