Sotiris Skaperas
Misspecified Crame-Rao Bound for AoA Estimation at a ULA under a Spoofing Attack
Dec 18, 2025


Abstract:A framework is presented for analyzing the impact of active attacks to location-based physical layer authentication (PLA) using the machinery of misspecified Cramér--Rao bound (MCRB). In this work, we focus on the MCRB in the angle-of-arrival (AoA) based authentication of a single antenna user when the verifier posseses an $M$ antenna element uniform linear array (ULA), assuming deterministic pilot signals; in our system model the presence of a spoofing adversary with an arbitrary number $L$ of antenna elements is assumed. We obtain a closed-form expression for the MCRB and demonstrate that the attack introduces in it a penalty term compared to the classic CRB, which does not depend on the signal-to-noise ratio (SNR) but on the adversary's location, the array geometry and the attacker precoding vector.
Smart Channel State Information Pre-processing for Joint Authentication and Secret Key Distillation
Jun 01, 2022
Abstract:While the literature on RF fingerprinting-based authentication and key distillation is vast, the two topics have customarily been studied separately. In this paper, starting from the observation that the wireless channel is a composite, deterministic / stochastic process, we propose a power domain decomposition that allows performing the two tasks simultaneously. We devise intelligent pre-processing schemes to decompose channel state information (CSI) observation vectors into "predictable" and "unpredictable" components. The former, primarily due to large-scale fading, can be used for node authentication through RF fingerprinting. The latter, primarily due to small-scale fading, could be used for semantically secure secret key generation (SKG). To perform the decomposition, we propose: (i) a fingerprint "separability" criterion, expressed through the maximisation of the total variation distance between the empirical fingerprint measures; (ii) a statistical independence metric for observations collected at different users, expressed through a normalised version of the $d$-dimensional Hilbert Schmidt independence criterion (dHSIC) test statistic. We propose both explicit implementations, using principal component analysis (PCA) and kernel PCA and black-box, unsupervised learning, using autoencoders. Our experiments on synthetic and real CSI datasets showcase that the incorporation of RF fingerprinting and SKG, with explicit security guarantees, is tangible in future generations of wireless.
On the Use of CSI for the Generation of RF Fingerprints and Secret Keys
Oct 28, 2021



Abstract:This paper presents a systematic approach to use channel state information for authentication and secret key distillation for physical layer security (PLS). We use popular machine learning (ML) methods and signal processing-based approaches to disentangle the large scale fading and be used as a source of uniqueness, from the small scale fading, to be treated as a source of shared entropy secret key generation (SKG). The ML-based approaches are completely unsupervised and hence avoid exhaustive measurement campaigns. We also propose using the Hilbert Schmidt independence criterion (HSIC); our simulation results demonstrate that the extracted stochastic part of the channel state information (CSI) vectors are statistically independent.
Scheduling Optimization of Heterogeneous Services by Resolving Conflicts
Mar 02, 2021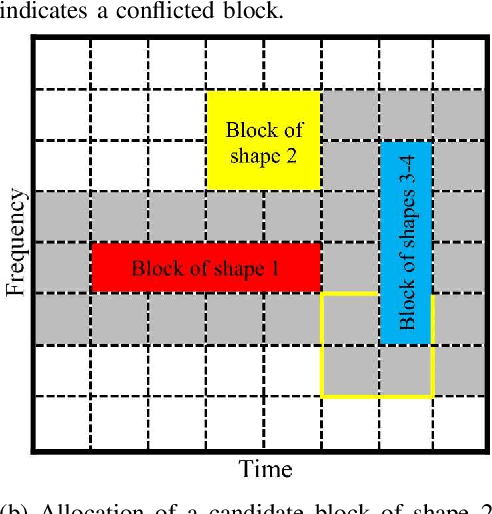
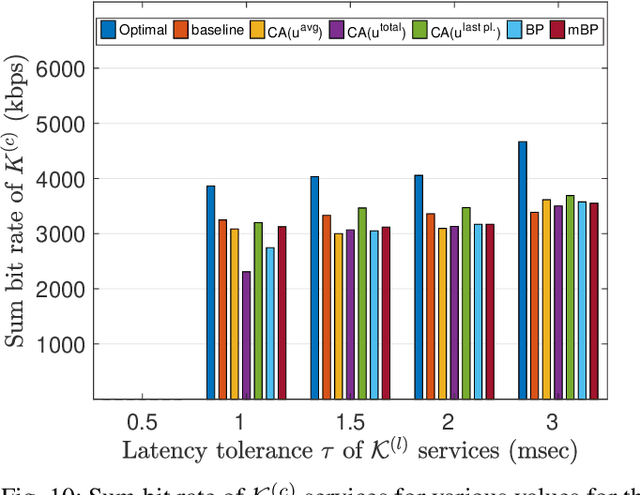
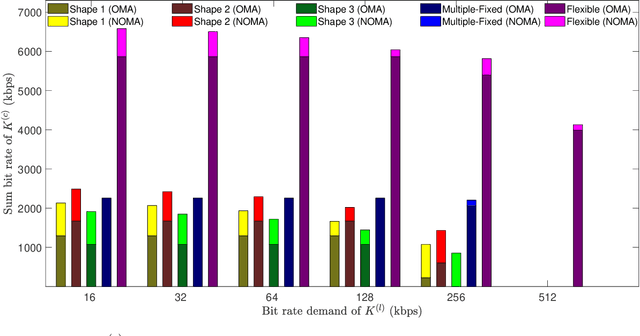
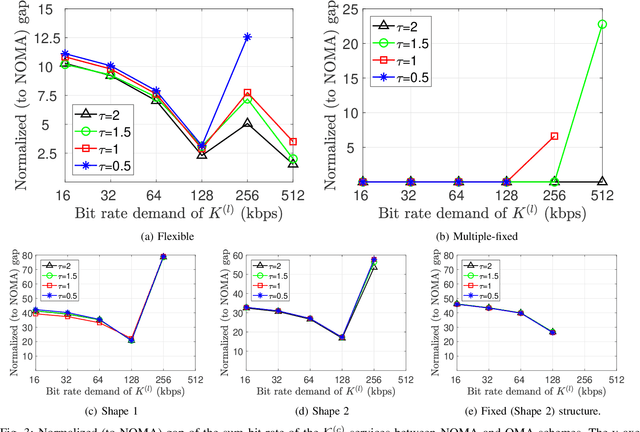
Abstract:Fifth generation (5G) new radio introduced flexible numerology to provide the necessary flexibility for accommodating heterogeneous services. However, optimizing the scheduling of heterogeneous services with differing delay and throughput requirements over 5G new radio is a challenging task. In this paper, we investigate near optimal, low complexity scheduling of radio resources for ultra-reliable low-latency communications (URLLC) when coexisting with enhanced mobile broadband (eMBB) services. We demonstrate that maximizing the sum throughput of eMBB services while servicing URLLC users, is, in the long-term, equivalent to minimizing the number of URLLC placements in the time-frequency grid; this result stems from reducing the number of infeasible placements for eMBB, to which we refer to as "conflicts". To meet this new objective, we propose and investigate new conflict-aware heuristics; a family of "greedy" and a lightweight heuristic inspired by bin packing optimization, all of near optimal performance. Moreover, having shed light on the impact of conflict in layer-2 scheduling, non-orthogonal multiple access (NOMA) emerges as a competitive approach for conflict resolution, in addition to the well established increased spectral efficiency with respect to OMA. The superior performance of NOMA, thanks to alleviating conflicts,is showcased by extensive numerical results.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge