Linda Senigagliesi
AoA-Based Physical Layer Authentication in Analog Arrays under Impersonation Attacks
Jul 11, 2024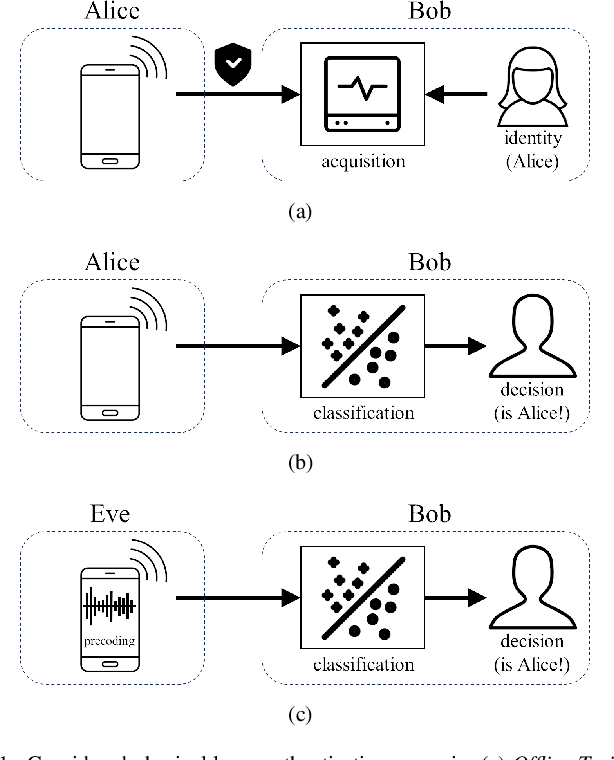
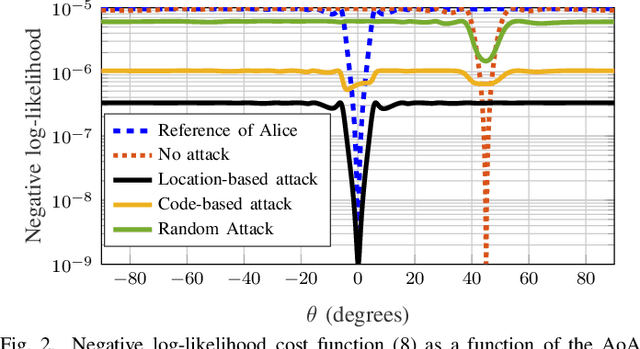
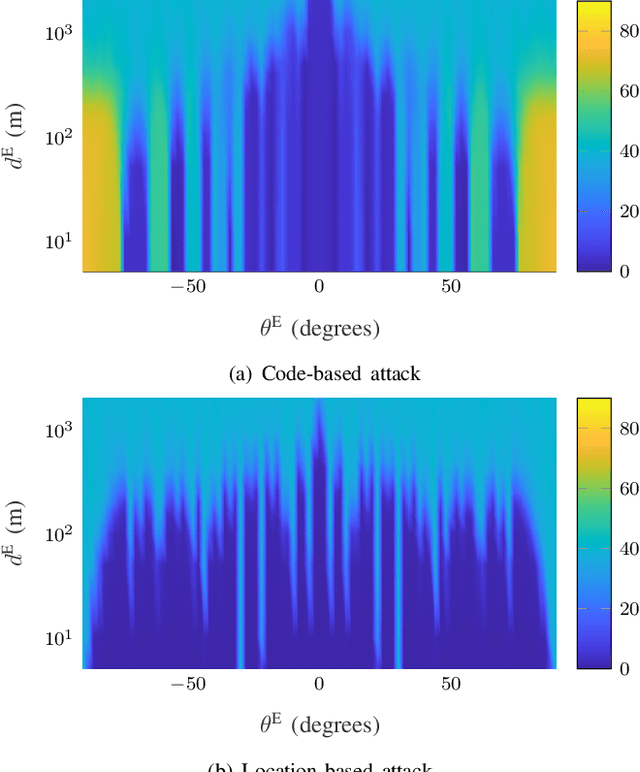
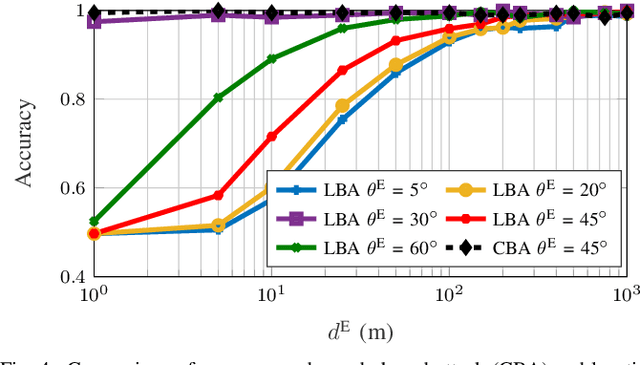
Abstract:We discuss the use of angle of arrival (AoA) as an authentication measure in analog array multiple-input multiple-output (MIMO) systems. A base station equipped with an analog array authenticates users based on the AoA estimated from certified pilot transmissions, while active attackers manipulate their transmitted signals to mount impersonation attacks. We study several attacks of increasing intensity (captured through the availability of side information at the attackers) and assess the performance of AoA-based authentication using one-class classifiers. Our results show that some attack techniques with knowledge of the combiners at the verifier are effective in falsifying the AoA and compromising the security of the considered type of physical layer authentication.
Performance of Statistical and Machine Learning Techniques for Physical Layer Authentication
Jan 17, 2020



Abstract:In this paper we consider authentication at the physical layer, in which the authenticator aims at distinguishing a legitimate supplicant from an attacker on the basis of the characteristics of the communication channel. Authentication is performed over a set of parallel wireless channels affected by time-varying fading at the presence of a malicious attacker, whose channel has a spatial correlation with the supplicant's one. We first propose the use of two different statistical decision methods, and we prove that using a large number of references (in the form of channel estimates) affected by different levels of time-varying fading is not beneficial from a security point of view. We then propose to exploit classification methods based on machine learning. In order to face the worst case of an authenticator provided with no forged messages during training, we consider one-class classifiers. When instead the training set includes some forged messages, we resort to more conventional binary classifiers, considering the cases in which such messages are either labelled or not. For the latter case, we exploit clustering algorithms to label the training set. The performance of both nearest neighbor (NN) and support vector machine (SVM) classification techniques is assessed. Through numerical examples, we show that under the same probability of false alarm, one-class classification (OCC) algorithms achieve the lowest probability of missed detection when a small spatial correlation exists between the main channel and the adversary one, while statistical methods are advantageous when the spatial correlation between the two channels is large.
Statistical and Machine Learning-based Decision Techniques for Physical Layer Authentication
Sep 16, 2019



Abstract:In this paper we assess the security performance of key-less physical layer authentication schemes in the case of time-varying fading channels, considering both partial and no channel state information (CSI) on the receiver's side. We first present a generalization of a well-known protocol previously proposed for flat fading channels and we study different statistical decision methods and the corresponding optimal attack strategies in order to improve the authentication performance in the considered scenario. We then consider the application of machine learning techniques in the same setting, exploiting different one-class nearest neighbor (OCNN) classification algorithms. We observe that, under the same probability of false alarm, one-class classification (OCC) algorithms achieve the lowest probability of missed detection when a low spatial correlation exists between the main channel and the adversary one, while statistical methods are advantageous when the spatial correlation between the two channels is higher.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge