Sotiris Ioannidis
Physics-Aware RIS Codebook Compilation for Near-Field Beam Focusing under Mutual Coupling and Specular Reflections
Jan 19, 2026Abstract:Next-generation wireless networks are envisioned to achieve reliable, low-latency connectivity within environments characterized by strong multipath and severe channel variability. Programmable wireless environments (PWEs) address this challenge by enabling deterministic control of electromagnetic (EM) propagation through software-defined reconfigurable intelligent surfaces (RISs). However, effectively configuring RISs in real time remains a major bottleneck, particularly under near-field conditions where mutual coupling and specular reflections alter the intended response. To overcome this limitation, this paper introduces MATCH, a physics-based codebook compilation algorithm that explicitly accounts for the EM coupling among RIS unit cells and the reflective interactions with surrounding structures, ensuring that the resulting codebooks remain consistent with the physical characteristics of the environment. Finally, MATCH is evaluated under a full-wave simulation framework incorporating mutual coupling and secondary reflections, demonstrating its ability to concentrate scattered energy within the focal region, confirming that physics-consistent, codebook-based optimization constitutes an effective approach for practical and efficient RIS configuration.
A novel RF-enabled Non-Destructive Inspection Method through Machine Learning and Programmable Wireless Environments
Jan 10, 2026Abstract:Contemporary industrial Non-Destructive Inspection (NDI) methods require sensing capabilities that operate in occluded, hazardous, or access restricted environments. Yet, the current visual inspection based on optical cameras offers limited quality of service to that respect. In that sense, novel methods for workpiece inspection, suitable, for smart manufacturing are needed. Programmable Wireless Environments (PWE) could help towards that direction, by redefining the wireless Radio Frequency (RF) wave propagation as a controllable inspector entity. In this work, we propose a novel approach to Non-Destructive Inspection, leveraging an RF sensing pipeline based on RF wavefront encoding for retrieving workpiece-image entries from a designated database. This approach combines PWE-enabled RF wave manipulation with machine learning (ML) tools trained to produce visual outputs for quality inspection. Specifically, we establish correlation relationships between RF wavefronts and target industrial assets, hence yielding a dataset which links wavefronts to their corresponding images in a structured manner. Subsequently, a Generative Adversarial Network (GAN) derives visual representations closely matching the database entries. Our results indicate that the proposed method achieves an SSIM 99.5% matching score in visual outputs, paving the way for next-generation quality control workflows in industry.
How Many Pinching Antennas Are Enough?
Dec 21, 2025
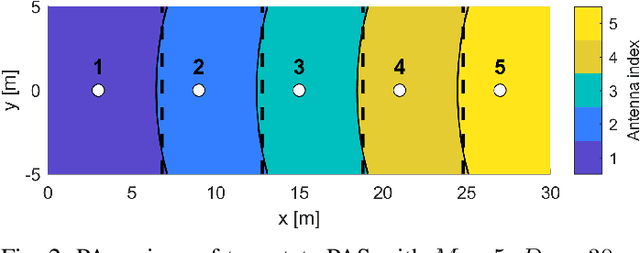
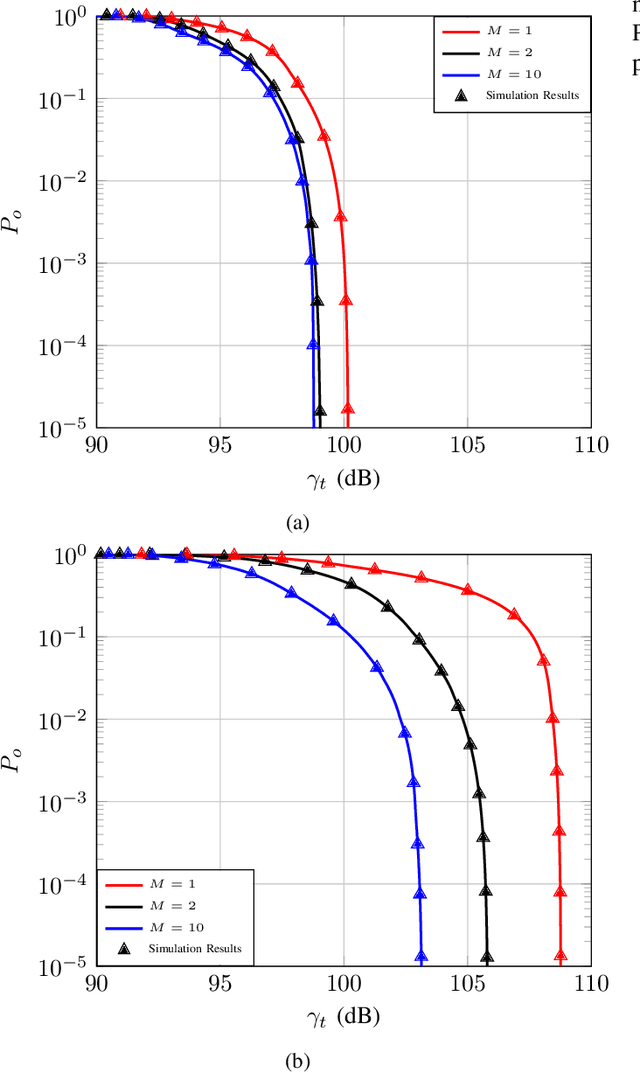
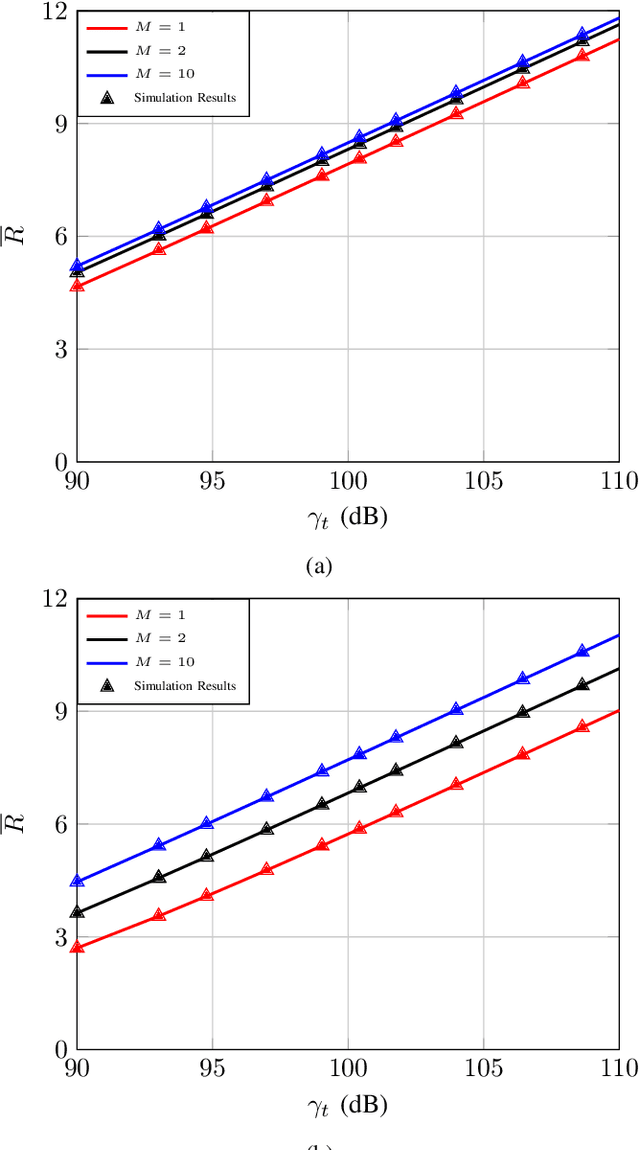
Abstract:Programmable wireless environments (PWEs) have emerged as a key paradigm for next-generation communication networks, aiming to transform wireless propagation from an uncontrollable phenomenon into a reconfigurable process that can adapt to diverse service requirements. In this framework, pinching-antenna systems (PASs) have recently been proposed as a promising enabling technology, as they allow the radiation location and effective propagation distance to be adjusted by selectively exciting radiating points along a dielectric waveguide. However, most existing studies on PASs rely on the idealized assumption that pinching-antenna (PA) positions can be continuously adjusted along the waveguide, while realistically only a finite set of pinching locations is available. Motivated by this, this paper analyzes the performance of two-state PASs, where the PA positions are fixed and only their activation state can be controlled. By explicitly accounting for the spatial discreteness of the available pinching points, closed-form analytical expressions for the outage probability and the ergodic achievable data rate are derived. In addition, we introduce the pinching discretization efficiency to quantify the performance gap between discrete and continuous pinching configurations, enabling a direct assessment of the number of PAs required to approximate the ideal continuous case. Finally, numerical results validate the analytical framework and show that near-continuous performance can be achieved with a limited number of PAs, offering useful insights for the design and deployment of PASs in PWEs.
Realizing RF Wavefront Copying with RIS for Future Extended Reality Applications
Jun 11, 2024



Abstract:Lately a new approach to Extended Reality (XR), denoted as XR-RF, has been proposed which is realized by combining Radio Frequency (RF) Imaging and programmable wireless environments (PWEs). RF Imaging is a technique that aims to detect geometric and material features of an object through RF waves. On the other hand, the PWE focuses on the the conversion of the wireless RF propagation in a controllable, by software, entity through the utilization of Reconfigurable Intelligent Surfaces (RISs), which can have a controllable interaction with impinging RF waves. In that sense, this dynamic synergy leverages the potential of RF Imaging to detect the structure of an object through RF wavefronts and the PWE's ability to selectively replicate those RF wavefronts from one spatial location to wherever an XR-RF mobile user is presently located. Then the captured wavefront, through appropriate hardware, is mapped to the visual representation of the object through machine learning models. As a key aspect of the XR-RF's system workflow is the wavefront copying mechanism, this work introduces a new PWE configuration algorithm for XR-RF. Moreover, it is shown that the waveform replication process inevitably yields imprecision in the replication process. After statistical analysis, based on simulation results, it is shown that this imprecision can be effectively modeled by the gamma distribution.
Energy-aware Trajectory Optimization for UAV-mounted RIS and Full-duplex Relay
Jan 22, 2024Abstract:In the evolving landscape of sixth-generation (6G) wireless networks, unmanned aerial vehicles (UAVs) have emerged as transformative tools for dynamic and adaptive connectivity. However, dynamically adjusting their position to offer favorable communication channels introduces operational challenges in terms of energy consumption, especially when integrating advanced communication technologies like reconfigurable intelligent surfaces (RISs) and full-duplex relays (FDRs). To this end, by recognizing the pivotal role of UAV mobility, the paper introduces an energy-aware trajectory design for UAV-mounted RISs and UAV-mounted FDRs using the decode and forward (DF) protocol, aiming to maximize the network minimum rate and enhance user fairness, while taking into consideration the available on-board energy. Specifically, this work highlights their distinct energy consumption characteristics and their associated integration challenges by developing appropriate energy consumption models for both UAV-mounted RISs and FDRs that capture the intricate relationship between key factors such as weight, and their operational characteristics. Furthermore, a joint time-division multiple access (TDMA) user scheduling-UAV trajectory optimization problem is formulated, considering the power dynamics of both systems, while assuring that the UAV energy is not depleted mid-air. Finally, simulation results underscore the importance of energy considerations in determining the optimal trajectory and scheduling and provide insights into the performance comparison of UAV-mounted RISs and FDRs in UAV-assisted wireless networks.
Russo-Ukrainian War: Prediction and explanation of Twitter suspension
Jun 06, 2023



Abstract:On 24 February 2022, Russia invaded Ukraine, starting what is now known as the Russo-Ukrainian War, initiating an online discourse on social media. Twitter as one of the most popular SNs, with an open and democratic character, enables a transparent discussion among its large user base. Unfortunately, this often leads to Twitter's policy violations, propaganda, abusive actions, civil integrity violation, and consequently to user accounts' suspension and deletion. This study focuses on the Twitter suspension mechanism and the analysis of shared content and features of the user accounts that may lead to this. Toward this goal, we have obtained a dataset containing 107.7M tweets, originating from 9.8 million users, using Twitter API. We extract the categories of shared content of the suspended accounts and explain their characteristics, through the extraction of text embeddings in junction with cosine similarity clustering. Our results reveal scam campaigns taking advantage of trending topics regarding the Russia-Ukrainian conflict for Bitcoin and Ethereum fraud, spam, and advertisement campaigns. Additionally, we apply a machine learning methodology including a SHapley Additive explainability model to understand and explain how user accounts get suspended.
BotArtist: Twitter bot detection Machine Learning model based on Twitter suspension
Jun 02, 2023Abstract:Twitter as one of the most popular social networks, offers a means for communication and online discourse, which unfortunately has been the target of bots and fake accounts, leading to the manipulation and spreading of false information. Towards this end, we gather a challenging, multilingual dataset of social discourse on Twitter, originating from 9M users regarding the recent Russo-Ukrainian war, in order to detect the bot accounts and the conversation involving them. We collect the ground truth for our dataset through the Twitter API suspended accounts collection, containing approximately 343K of bot accounts and 8M of normal users. Additionally, we use a dataset provided by Botometer-V3 with 1,777 Varol, 483 German accounts, and 1,321 US accounts. Besides the publicly available datasets, we also manage to collect 2 independent datasets around popular discussion topics of the 2022 energy crisis and the 2022 conspiracy discussions. Both of the datasets were labeled according to the Twitter suspension mechanism. We build a novel ML model for bot detection using the state-of-the-art XGBoost model. We combine the model with a high volume of labeled tweets according to the Twitter suspension mechanism ground truth. This requires a limited set of profile features allowing labeling of the dataset in different time periods from the collection, as it is independent of the Twitter API. In comparison with Botometer our methodology achieves an average 11% higher ROC-AUC score over two real-case scenario datasets.
Zero-Energy Reconfigurable Intelligent Surfaces (zeRIS)
May 12, 2023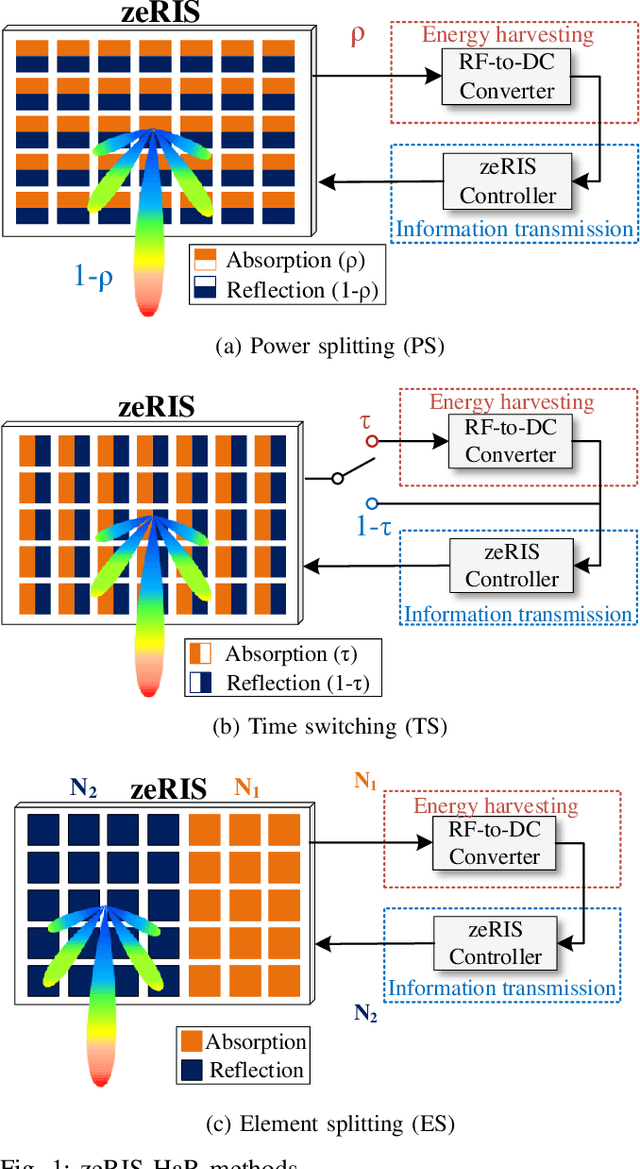
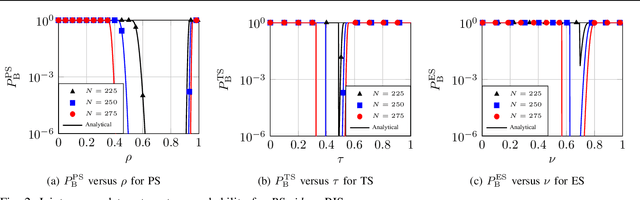
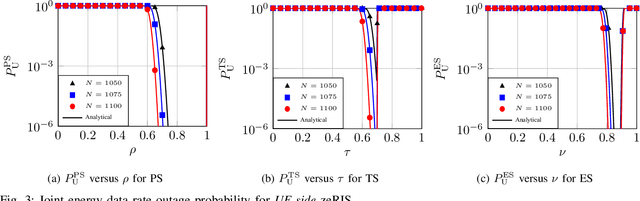
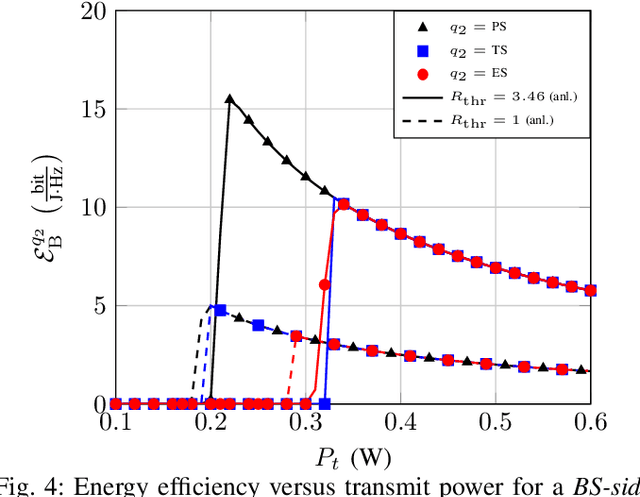
Abstract:A primary objective of the forthcoming sixth generation (6G) of wireless networking is to support demanding applications, while ensuring energy efficiency. Programmable wireless environments (PWEs) have emerged as a promising solution, leveraging reconfigurable intelligent surfaces (RISs), to control wireless propagation and deliver exceptional quality-ofservice. In this paper, we analyze the performance of a network supported by zero-energy RISs (zeRISs), which harvest energy for their operation and contribute to the realization of PWEs. Specifically, we investigate joint energy-data rate outage probability and the energy efficiency of a zeRIS-assisted communication system by employing three harvest-and-reflect (HaR) methods, i) power splitting, ii) time switching, and iii) element splitting. Furthermore, we consider two zeRIS deployment strategies, namely BS-side zeRIS and UE-side zeRIS. Simulation results validate the provided analysis and examine which HaR method performs better depending on the zeRIS placement. Finally, valuable insights and conclusions for the performance of zeRISassisted wireless networks are drawn from the presented results.
An Open Platform for Simulating the Physical Layer of 6G Communication Systems with Multiple Intelligent Surfaces
Nov 03, 2022Abstract:Reconfigurable Intelligent Surfaces (RIS) constitute a promising technology that could fulfill the extreme performance and capacity needs of the upcoming 6G wireless networks, by offering software-defined control over wireless propagation phenomena. Despite the existence of many theoretical models describing various aspects of RIS from the signal processing perspective (e.g., channel fading models), there is no open platform to simulate and study their actual physical-layer behavior, especially in the multi-RIS case. In this paper, we develop an open simulation platform, aimed at modeling the physical-layer electromagnetic coupling and propagation between RIS pairs. We present the platform by initially designing a basic unit cell, and then proceeding to progressively model and simulate multiple and larger RISs. The platform can be used for producing verifiable stochastic models for wireless communication in multi-RIS deployments, such as vehicle-to-everything (V2X) communications in autonomous vehicles and cybersecurity schemes, while its code is freely available to the public.
Evaluating Short-Term Forecasting of Multiple Time Series in IoT Environments
Jun 15, 2022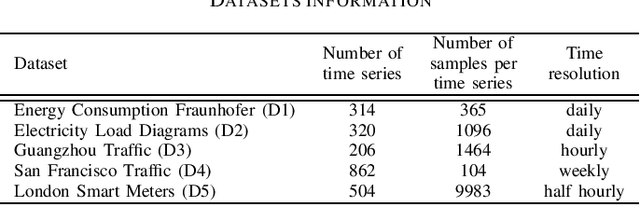
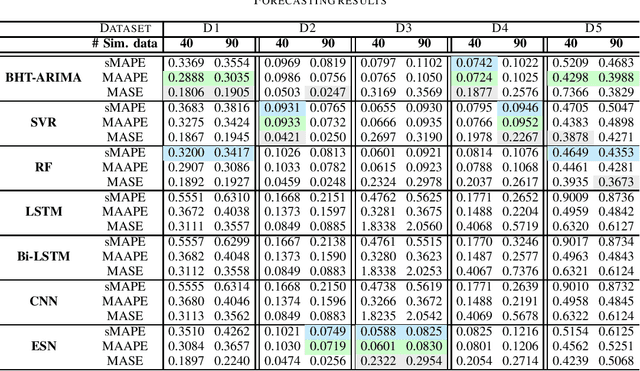
Abstract:Modern Internet of Things (IoT) environments are monitored via a large number of IoT enabled sensing devices, with the data acquisition and processing infrastructure setting restrictions in terms of computational power and energy resources. To alleviate this issue, sensors are often configured to operate at relatively low sampling frequencies, yielding a reduced set of observations. Nevertheless, this can hamper dramatically subsequent decision-making, such as forecasting. To address this problem, in this work we evaluate short-term forecasting in highly underdetermined cases, i.e., the number of sensor streams is much higher than the number of observations. Several statistical, machine learning and neural network-based models are thoroughly examined with respect to the resulting forecasting accuracy on five different real-world datasets. The focus is given on a unified experimental protocol especially designed for short-term prediction of multiple time series at the IoT edge. The proposed framework can be considered as an important step towards establishing a solid forecasting strategy in resource constrained IoT applications.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge