Hamid Behroozi
Enhancing Energy and Spectral Efficiency in IoT-Cellular Networks via Active SIM-Equipped LEO Satellites
Aug 23, 2025



Abstract:This paper investigates a low Earth orbit (LEO) satellite communication system enhanced by an active stacked intelligent metasurface (ASIM), mounted on the backplate of the satellite solar panels to efficiently utilize limited onboard space and reduce the main satellite power amplifier requirements. The system serves multiple ground users via rate-splitting multiple access (RSMA) and IoT devices through a symbiotic radio network. Multi-layer sequential processing in the ASIM improves effective channel gains and suppresses inter-user interference, outperforming active RIS and beyond-diagonal RIS designs. Three optimization approaches are evaluated: block coordinate descent with successive convex approximation (BCD-SCA), model-assisted multi-agent constraint soft actor-critic (MA-CSAC), and multi-constraint proximal policy optimization (MCPPO). Simulation results show that BCD-SCA converges fast and stably in convex scenarios without learning, MCPPO achieves rapid initial convergence with moderate stability, and MA-CSAC attains the highest long-term spectral and energy efficiency in large-scale networks. Energy-spectral efficiency trade-offs are analyzed for different ASIM elements, satellite antennas, and transmit power. Overall, the study demonstrates that integrating multi-layer ASIM with suitable optimization algorithms offers a scalable, energy-efficient, and high-performance solution for next-generation LEO satellite communications.
Energy Efficient RSMA-Based LEO Satellite Communications Assisted by UAV-Mounted BD-Active RIS: A DRL Approach
May 07, 2025



Abstract:This paper proposes an advanced non-terrestrial communication architecture that integrates Rate-Splitting Multiple Access (RSMA) with a Beyond-Diagonal Active Reconfigurable Intelligent Surface (BD-ARIS) mounted on a UAV under the coverage of a Low Earth Orbit (LEO) satellite. The BD-ARIS adopts a group-connected structure to enhance signal amplification and adaptability, while RSMA enables efficient multi-user access by dividing messages into common and private components. The system jointly optimizes satellite beamforming, UAV positioning, power allocation, and rate-splitting ratios to maximize the overall energy efficiency (EE). To solve the resulting non-convex and high-dimensional problem, we employ three state-of-the-art deep reinforcement learning (DRL) algorithms: Trust Region Policy Optimization (TRPO), Twin Delayed Deep Deterministic Policy Gradient (TD3), and Asynchronous Advantage Actor-Critic (A3C). Moreover, realistic models for the power consumption of both the UAV and the BD-ARIS are considered. Simulation results reveal that TRPO consistently achieves the best performance in terms of EE and sum rate, especially under high transmit powers and challenging deployment scenarios. TD3 converges faster and performs competitively in moderate settings, while A3C suffers from instability due to its high variance. Additionally, the robustness of each algorithm under channel state information (CSI) uncertainty is evaluated, confirming TRPO resilience to imperfect observations. Overall, the proposed RSMA-BD-ARIS framework significantly outperforms conventional RIS-assisted designs and provides a scalable, energy-efficient solution for 6G and massive IoT applications in non-terrestrial networks.
Deep Joint Source Channel Coding for Secure End-to-End Image Transmission
Dec 22, 2024Abstract:Deep neural network (DNN)-based joint source and channel coding is proposed for end-to-end secure image transmission against multiple eavesdroppers. Both scenarios of colluding and non-colluding eavesdroppers are considered. Instead of idealistic assumptions of perfectly known and i.i.d. source and channel distributions, the proposed scheme assumes unknown source and channel statistics. The goal is to transmit images with minimum distortion, while simultaneously preventing eavesdroppers from inferring private attributes of images. Simultaneously generalizing the ideas of privacy funnel and wiretap coding, a multi-objective optimization framework is expressed that characterizes the trade-off between image reconstruction quality and information leakage to eavesdroppers, taking into account the structural similarity index (SSIM) for improving the perceptual quality of image reconstruction. Extensive experiments over CIFAR-10 and CelebFaces Attributes (CelebA) datasets, together with ablation studies are provided to highlight the performance gain in terms of SSIM, adversarial accuracy, and cross-entropy metric compared with benchmarks. Experiments show that the proposed scheme restrains the adversarially-trained eavesdroppers from intercepting privatized data for both cases of eavesdropping a common secret, as well as the case in which eavesdroppers are interested in different secrets. Furthermore, useful insights on the privacy-utility trade-off are also provided.
Emo3D: Metric and Benchmarking Dataset for 3D Facial Expression Generation from Emotion Description
Oct 02, 2024
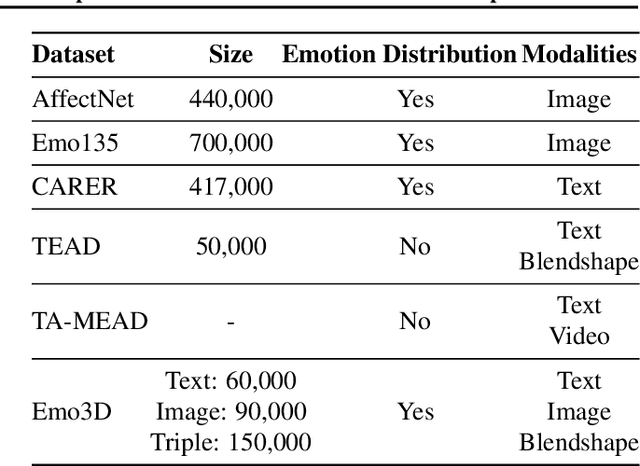

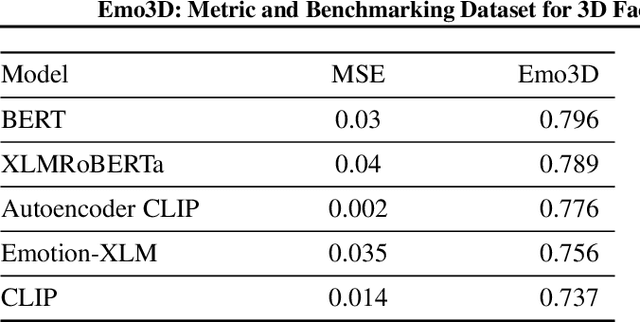
Abstract:Existing 3D facial emotion modeling have been constrained by limited emotion classes and insufficient datasets. This paper introduces "Emo3D", an extensive "Text-Image-Expression dataset" spanning a wide spectrum of human emotions, each paired with images and 3D blendshapes. Leveraging Large Language Models (LLMs), we generate a diverse array of textual descriptions, facilitating the capture of a broad spectrum of emotional expressions. Using this unique dataset, we conduct a comprehensive evaluation of language-based models' fine-tuning and vision-language models like Contranstive Language Image Pretraining (CLIP) for 3D facial expression synthesis. We also introduce a new evaluation metric for this task to more directly measure the conveyed emotion. Our new evaluation metric, Emo3D, demonstrates its superiority over Mean Squared Error (MSE) metrics in assessing visual-text alignment and semantic richness in 3D facial expressions associated with human emotions. "Emo3D" has great applications in animation design, virtual reality, and emotional human-computer interaction.
Secure Deep-JSCC Against Multiple Eavesdroppers
Aug 05, 2023Abstract:In this paper, a generalization of deep learning-aided joint source channel coding (Deep-JSCC) approach to secure communications is studied. We propose an end-to-end (E2E) learning-based approach for secure communication against multiple eavesdroppers over complex-valued fading channels. Both scenarios of colluding and non-colluding eavesdroppers are studied. For the colluding strategy, eavesdroppers share their logits to collaboratively infer private attributes based on ensemble learning method, while for the non-colluding setup they act alone. The goal is to prevent eavesdroppers from inferring private (sensitive) information about the transmitted images, while delivering the images to a legitimate receiver with minimum distortion. By generalizing the ideas of privacy funnel and wiretap channel coding, the trade-off between the image recovery at the legitimate node and the information leakage to the eavesdroppers is characterized. To solve this secrecy funnel framework, we implement deep neural networks (DNNs) to realize a data-driven secure communication scheme, without relying on a specific data distribution. Simulations over CIFAR-10 dataset verifies the secrecy-utility trade-off. Adversarial accuracy of eavesdroppers are also studied over Rayleigh fading, Nakagami-m, and AWGN channels to verify the generalization of the proposed scheme. Our experiments show that employing the proposed secure neural encoding can decrease the adversarial accuracy by 28%.
Intelligent Reflecting Surface Assisted Secret Key Generation Under Spatially Correlated Channels in Quasi-Static Environments
Dec 03, 2022Abstract:Physical layer key generation (PLKG) can significantly enhance the security of classic encryption schemes by enabling them to change their secret keys significantly faster and more efficient. However, due to the reliance of PLKG techniques on channel medium, reaching a high secret key rate is challenging in static environments. Recently, exploiting intelligent reflecting surface (IRS) as a means to induce randomness in static wireless channels has received significant research interest. However, the impact of spatial correlation between the IRS elements is rarely studied. To be specific, for the first time, in this contribution, we take into account a spatially correlated IRS which intends to enhance the secret key generation (SKG) rate in a static medium. Closed form analytical expressions for SKG rate are derived for the two cases of random phase shift and equal random phase shift for all the IRS elements. We also analyze the temporal correlation between the channel samples to ensure the randomness of the generated secret key sequence. We further formulate an optimization problem in which we determine the optimal portion of time within a coherence interval dedicated for the direct and indirect channel estimation. We show the accuracy and the fast convergence of our proposed sequential convex programming (SCP) based algorithm and discuss the various parameters affecting spatially correlated IRS assisted PLKG.
Secure SWIPT in STAR-RIS Aided Downlink MISO Rate-Splitting Multiple Access Networks
Nov 16, 2022Abstract:Recently, simultaneously transmitting and reflecting reconfigurable intelligent surfaces (STAR-RISs) have emerged as a novel technology that facilitates sustainable communication by providing 360 coverage and new degrees-of-freedom (DoF) for manipulating signal propagation as well as simultaneous wireless information and power transfer (SWIPT). Inspired by these applications, this paper presents a novel STAR-RIS-aided secure SWIPT system for downlink multiple input single output (MISO) Rate-Splitting multiple access (RSMA) networks. The transmitter concurrently communicates with the information receivers (IRs) and sends energy to untrusted energy receivers (UERs). UERs are also able to wiretap the IR streams. The paper assumes that the channel state information (CSI) of the IRs is known at the transmitter. However, only imperfect CSI (ICSI) for the UERs is available at the transmitter. The paper aims to maximize the achievable worst-case sum secrecy rate (WCSSR) of the IRs under a total transmit power constraint, a sum energy constraint for the UERs, and constraints on the transmission and reflection coefficients by jointly optimizing the precoders and the transmission and reflection beamforming at the STAR-RIS. The formulated problem is non-convex with intricately coupled variables, and to tackle this challenge a suboptimal two-step iterative algorithm based on the sequential parametric convex approximation (SPCA) method is proposed. Specifically, the precoders and the transmission and reflection beamforming vectors are optimized alternatingly. Simulations are conducted to show that the proposed RSMA-based algorithm in a STAR-RIS aided network can improve the secrecy of the confidential information and the overall spectral efficiency.
Secrecy Rate of the Cooperative RSMA-Aided UAV Downlink Relying on Optimal Relay Selection
Oct 08, 2022
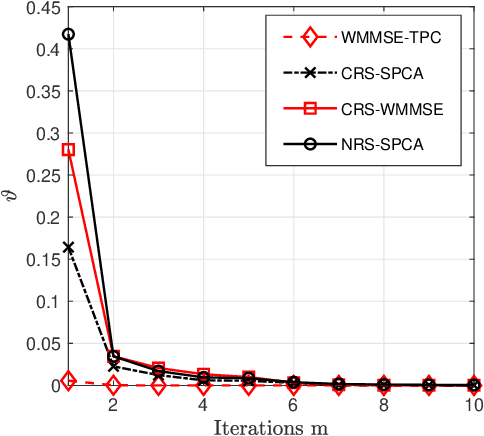
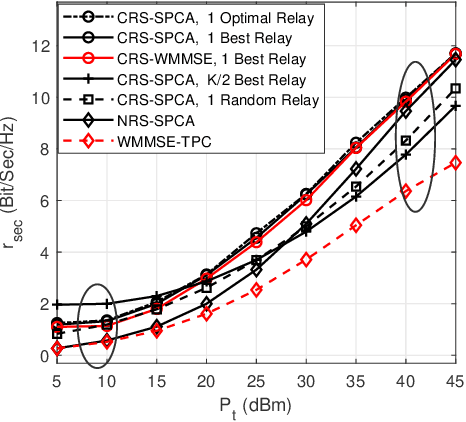
Abstract:The Cooperative Rate-Splitting (CRS) scheme, proposed evolves from conventional Rate Splitting (RS) and relies on forwarding a portion of the RS message by the relaying users. In terms of secrecy enhancement, it has been shown that CRS outperforms its non-cooperative counterpart for a two-user Multiple Input Single Output (MISO) Broadcast Channel (BC). Given the massive connectivity requirement of 6G, we have generalized the existing secure two-user CRS framework to the multi-user framework, where the highest-security users must be selected as the relay nodes. This paper addresses the problem of maximizing the Worst-Case Secrecy Rate (WCSR) in a UAV-aided downlink network where a multi-antenna UAV Base-Station (UAV-BS) serves a group of users in the presence of an external eavesdropper (Eve). We consider a practical scenario in which only imperfect channel state information of Eve is available at the UAV-BS. Accordingly, we conceive a robust and secure resource allocation algorithm, which maximizes the WCSR by jointly optimizing both the Secure Relaying User Selection (SRUS) and the network parameter allocation problem, including the RS transmit precoders, message splitting variables, time slot sharing and power allocation. To circumvent the resultant non-convexity owing to the discrete variables imposed by SRUS, we propose a two-stage algorithm where the SRUS and network parameter allocation are accomplished in two consecutive stages. With regard to the SRUS, we study both centralized and distributed protocols. On the other hand, for jointly optimizing the network parameter allocation we resort to the Sequential Parametric Convex Approximation (SPCA) algorithm. Our numerical results show that the proposed solution significantly outperforms the existing benchmarks for a wide range of network loads in terms of the WCSR.
Large-Scale Rate-Splitting Multiple Access in Uplink UAV Networks: Effective Secrecy Throughput Maximization Under Limited Feedback Channel
Sep 26, 2022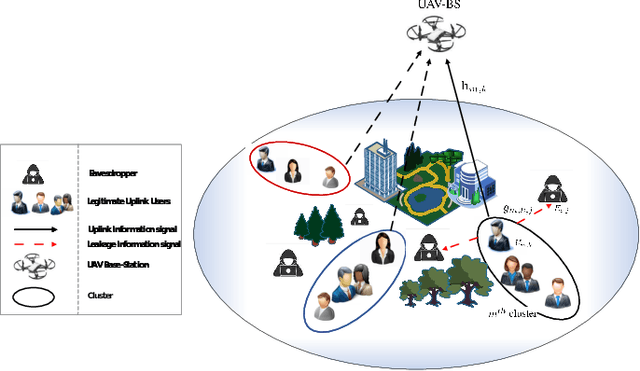
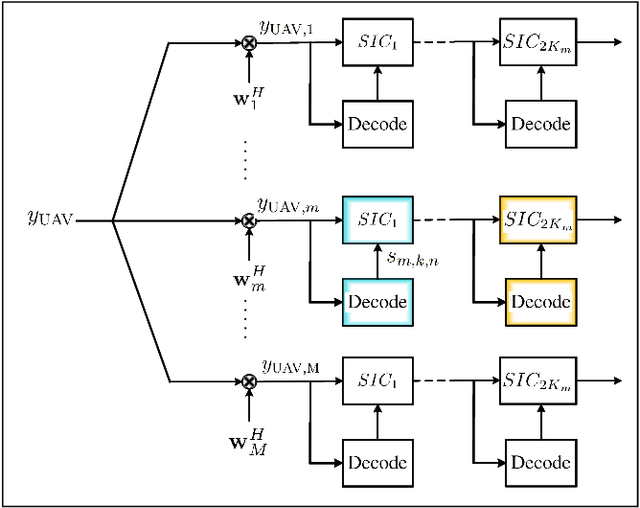
Abstract:UAVs are capable of improving the performance of next generation wireless systems. Specifically, UAVs can be exploited as aerial base-stations (UAV-BS) for supporting legitimate ground users in remote uncovered areas or in environments temporarily requiring high capacity. However, their communication performance is prone to both channel estimation errors and potential eavesdropping. Hence, we investigate the effective secrecy throughput of the UAV-aided uplink, in which rate-splitting multiple access (RSMA) is employed by each legitimate user for secure transmission under the scenario of massive access. To maximize the effective network secrecy throughput in the uplink, the transmission rate vs. power allocation relationship is formulated as a max-min optimization problem, relying on realistic imperfect CSI of both the legitimate users and of the potential eavesdroppers (Eves). We then propose a novel transformation of the associated probabilistic constraints for decoupling the variables, so that our design problem can be solved by alternatively activating the related block coordinate decent programming. In the model considered, each user transmits a superposition of two messages to a UAV-BS, each having different transmit power and the UAV-BS uses a SIC technique to decode the received messages. Given the non-convexity of the problem, it is decoupled into a pair of sub-problems. In particular, we derive a closed form expression for the optimal rate-splitting fraction of each user. Then, given the optimal rate-splitting fraction of each user, the \epsilon-constrainted transmit power of each user is calculated by harnessing SPCA programming.
Temporal Action Localization Using Gated Recurrent Units
Aug 07, 2021

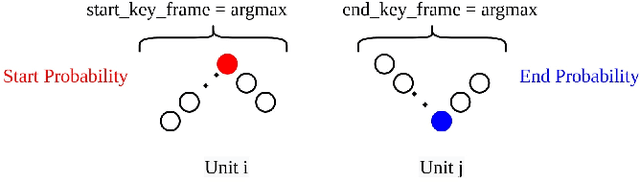
Abstract:Temporal Action Localization (TAL) task in which the aim is to predict the start and end of each action and its class label has many applications in the real world. But due to its complexity, researchers have not reached great results compared to the action recognition task. The complexity is related to predicting precise start and end times for different actions in any video. In this paper, we propose a new network based on Gated Recurrent Unit (GRU) and two novel post-processing ideas for TAL task. Specifically, we propose a new design for the output layer of the GRU resulting in the so-called GRU-Splitted model. Moreover, linear interpolation is used to generate the action proposals with precise start and end times. Finally, to rank the generated proposals appropriately, we use a Learn to Rank (LTR) approach. We evaluated the performance of the proposed method on Thumos14 dataset. Results show the superiority of the performance of the proposed method compared to state-of-the-art. Especially in the mean Average Precision (mAP) metric at Intersection over Union (IoU) 0.7, we get 27.52% which is 5.12% better than that of state-of-the-art methods.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge