Ahmed Abdelhadi
Fast and Robust LRSD-based SAR/ISAR Imaging and Decomposition
Dec 11, 2025Abstract:The earlier works in the context of low-rank-sparse-decomposition (LRSD)-driven stationary synthetic aperture radar (SAR) imaging have shown significant improvement in the reconstruction-decomposition process. Neither of the proposed frameworks, however, can achieve satisfactory performance when facing a platform residual phase error (PRPE) arising from the instability of airborne platforms. More importantly, in spite of the significance of real-time processing requirements in remote sensing applications, these prior works have only focused on enhancing the quality of the formed image, not reducing the computational burden. To address these two concerns, this article presents a fast and unified joint SAR imaging framework where the dominant sparse objects and low-rank features of the image background are decomposed and enhanced through a robust LRSD. In particular, our unified algorithm circumvents the tedious task of computing the inverse of large matrices for image formation and takes advantage of the recent advances in constrained quadratic programming to handle the unimodular constraint imposed due to the PRPE. Furthermore, we extend our approach to ISAR autofocusing and imaging. Specifically, due to the intrinsic sparsity of ISAR images, the LRSD framework is essentially tasked with the recovery of a sparse image. Several experiments based on synthetic and real data are presented to validate the superiority of the proposed method in terms of imaging quality and computational cost compared to the state-of-the-art methods.
Orthogonal Time Frequency Space for Integrated Sensing and Communication: A Survey
Feb 15, 2024
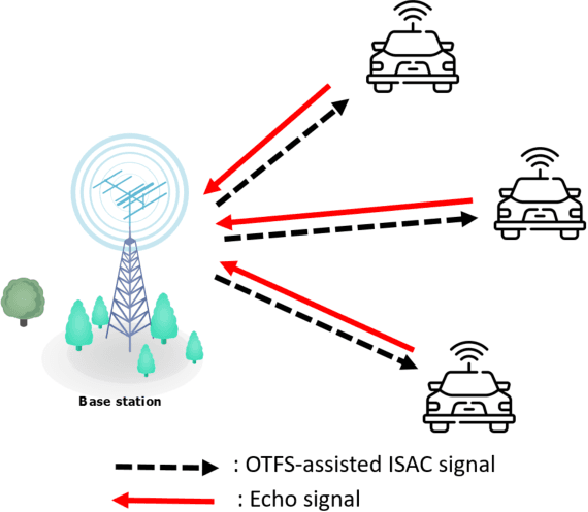

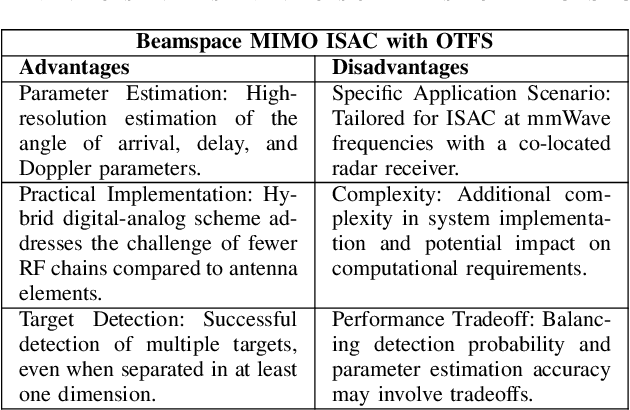
Abstract:Sixth-generation (6G) wireless communication systems, as stated in the European 6G flagship project Hexa-X, are anticipated to feature the integration of intelligence, communication, sensing, positioning, and computation. An important aspect of this integration is integrated sensing and communication (ISAC), in which the same waveform is used for both systems both sensing and communication, to address the challenge of spectrum scarcity. Recently, the orthogonal time frequency space (OTFS) waveform has been proposed to address OFDM's limitations due to the high Doppler spread in some future wireless communication systems. In this paper, we review existing OTFS waveforms for ISAC systems and provide some insights into future research. Firstly, we introduce the basic principles and a system model of OTFS and provide a foundational understanding of this innovative technology's core concepts and architecture. Subsequently, we present an overview of OTFS-based ISAC system frameworks. We provide a comprehensive review of recent research developments and the current state of the art in the field of OTFS-assisted ISAC systems to gain a thorough understanding of the current landscape and advancements. Furthermore, we perform a thorough comparison between OTFS-enabled ISAC operations and traditional OFDM, highlighting the distinctive advantages of OTFS, especially in high Doppler spread scenarios. Subsequently, we address the primary challenges facing OTFS-based ISAC systems, identifying potential limitations and drawbacks. Then, finally, we suggest future research directions, aiming to inspire further innovation in the 6G wireless communication landscape.
Large-Scale Rate-Splitting Multiple Access in Uplink UAV Networks: Effective Secrecy Throughput Maximization Under Limited Feedback Channel
Sep 26, 2022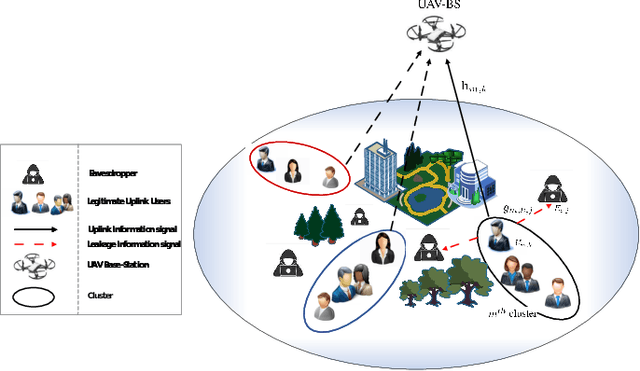
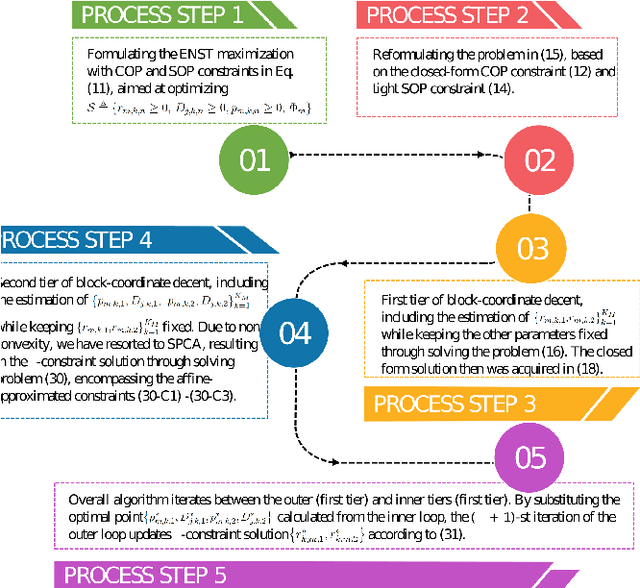
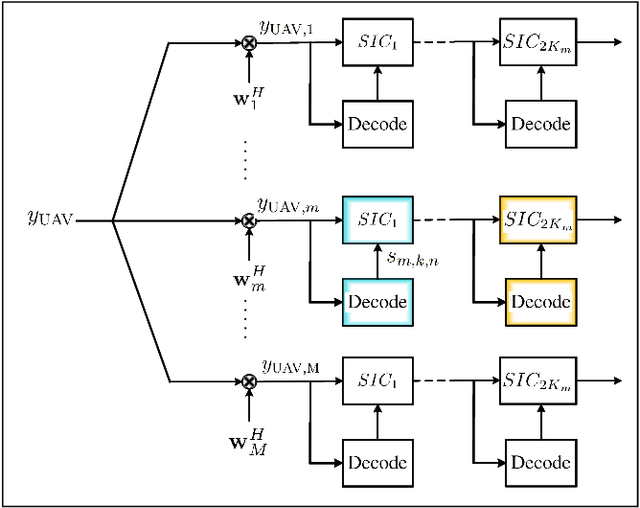
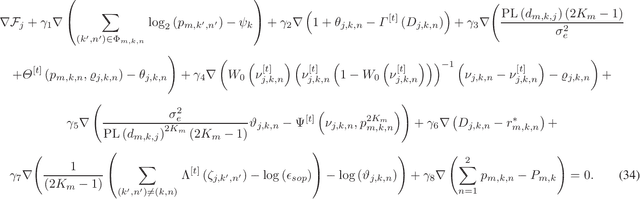
Abstract:UAVs are capable of improving the performance of next generation wireless systems. Specifically, UAVs can be exploited as aerial base-stations (UAV-BS) for supporting legitimate ground users in remote uncovered areas or in environments temporarily requiring high capacity. However, their communication performance is prone to both channel estimation errors and potential eavesdropping. Hence, we investigate the effective secrecy throughput of the UAV-aided uplink, in which rate-splitting multiple access (RSMA) is employed by each legitimate user for secure transmission under the scenario of massive access. To maximize the effective network secrecy throughput in the uplink, the transmission rate vs. power allocation relationship is formulated as a max-min optimization problem, relying on realistic imperfect CSI of both the legitimate users and of the potential eavesdroppers (Eves). We then propose a novel transformation of the associated probabilistic constraints for decoupling the variables, so that our design problem can be solved by alternatively activating the related block coordinate decent programming. In the model considered, each user transmits a superposition of two messages to a UAV-BS, each having different transmit power and the UAV-BS uses a SIC technique to decode the received messages. Given the non-convexity of the problem, it is decoupled into a pair of sub-problems. In particular, we derive a closed form expression for the optimal rate-splitting fraction of each user. Then, given the optimal rate-splitting fraction of each user, the \epsilon-constrainted transmit power of each user is calculated by harnessing SPCA programming.
Mixture GAN For Modulation Classification Resiliency Against Adversarial Attacks
May 29, 2022
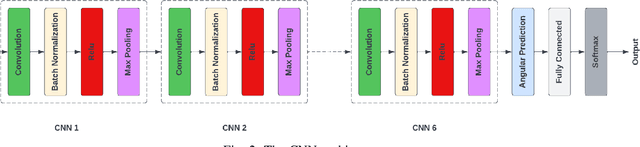
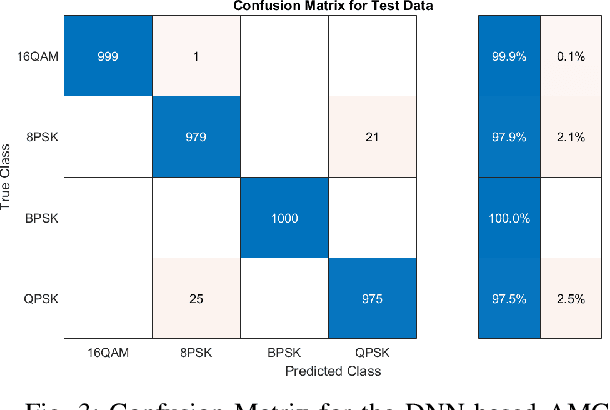

Abstract:Automatic modulation classification (AMC) using the Deep Neural Network (DNN) approach outperforms the traditional classification techniques, even in the presence of challenging wireless channel environments. However, the adversarial attacks cause the loss of accuracy for the DNN-based AMC by injecting a well-designed perturbation to the wireless channels. In this paper, we propose a novel generative adversarial network (GAN)-based countermeasure approach to safeguard the DNN-based AMC systems against adversarial attack examples. GAN-based aims to eliminate the adversarial attack examples before feeding to the DNN-based classifier. Specifically, we have shown the resiliency of our proposed defense GAN against the Fast-Gradient Sign method (FGSM) algorithm as one of the most potent kinds of attack algorithms to craft the perturbed signals. The existing defense-GAN has been designed for image classification and does not work in our case where the above-mentioned communication system is considered. Thus, our proposed countermeasure approach deploys GANs with a mixture of generators to overcome the mode collapsing problem in a typical GAN facing radio signal classification problem. Simulation results show the effectiveness of our proposed defense GAN so that it could enhance the accuracy of the DNN-based AMC under adversarial attacks to 81%, approximately.
A New Dimensionality Reduction Method Based on Hensel's Compression for Privacy Protection in Federated Learning
May 01, 2022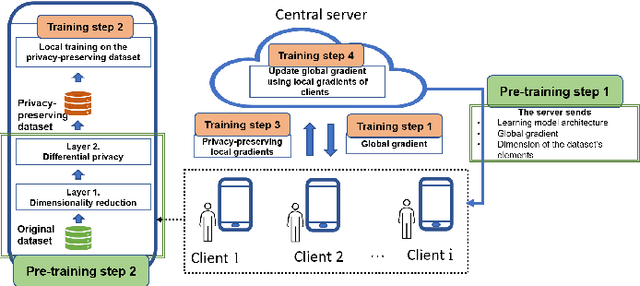
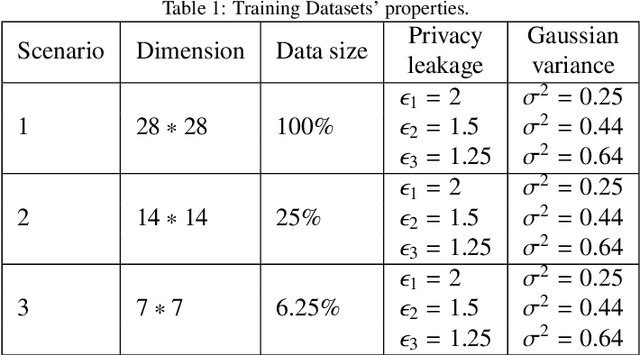
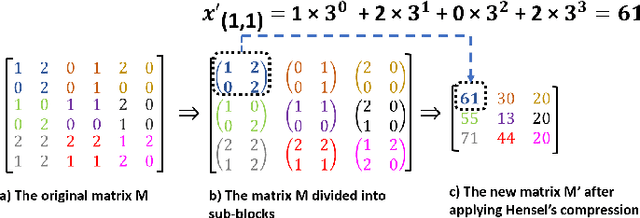
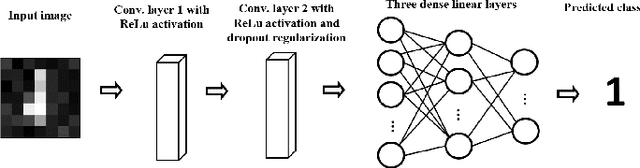
Abstract:Differential privacy (DP) is considered a de-facto standard for protecting users' privacy in data analysis, machine, and deep learning. Existing DP-based privacy-preserving training approaches consist of adding noise to the clients' gradients before sharing them with the server. However, implementing DP on the gradient is not efficient as the privacy leakage increases by increasing the synchronization training epochs due to the composition theorem. Recently researchers were able to recover images used in the training dataset using Generative Regression Neural Network (GRNN) even when the gradient was protected by DP. In this paper, we propose two layers of privacy protection approach to overcome the limitations of the existing DP-based approaches. The first layer reduces the dimension of the training dataset based on Hensel's Lemma. We are the first to use Hensel's Lemma for reducing the dimension (i.e., compress) of a dataset. The new dimensionality reduction method allows reducing the dimension of a dataset without losing information since Hensel's Lemma guarantees uniqueness. The second layer applies DP to the compressed dataset generated by the first layer. The proposed approach overcomes the problem of privacy leakage due to composition by applying DP only once before the training; clients train their local model on the privacy-preserving dataset generated by the second layer. Experimental results show that the proposed approach ensures strong privacy protection while achieving good accuracy. The new dimensionality reduction method achieves an accuracy of 97%, with only 25 % of the original data size.
Secrecy Rate Maximization for Hardware Impaired Untrusted Relaying Network with Deep Learning
Jan 07, 2021



Abstract:This paper investigates the physical layer security design of an untrusted relaying network where the source node coexists with a multi-antenna eavesdropper (Eve). While the communication relies on untrustworthy relay nodes to increase reliability, we aim to protect the confidentiality of information against combined eavesdropping attacks performed by both untrusted relay nodes and Eve. Taking into account the hardware impairments, and power budget constraints, this paper presents a novel approach to jointly optimize relay beamformer and transmit powers aimed at maximizing average secrecy rate (ASR). The resultant optimization problem is non-convex, and a suboptimal solution is obtained through the sequential parametric convex approximation (SPCA) method. In order to prevent any failure due to infeasibility, we propose an iterative initialization algorithm to find the feasible initial point of the original problem. To satisfy low-latency as one of the main key performance indicators (KPI) required in beyond 5G (B5G) communications, a computationally efficient data-driven approach is developed exploiting a deep learning model to improve the ASR while the computational burden is significantly reduced. Simulation results assess the effect of different system parameters on the ASR performance as well as the effectiveness of the proposed deep learning solution in large-scale cases.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge