Zhongxiang Wei
DRL-Enabled Trajectory Planing for UAV-Assisted VLC: Optimal Altitude and Reward Design
Jan 30, 2026Abstract:Recently, the integration of unmanned aerial vehicle (UAV) and visible light communication (VLC) technologies has emerged as a promising solution to offer flexible communication and efficient lighting. This letter investigates the three-dimensional trajectory planning in a UAV-assisted VLC system, where a UAV is dispatched to collect data from ground users (GUs). The core objective is to develop a trajectory planning framework that minimizes UAV flight distance, which is equivalent to maximizing the data collection efficiency. This issue is formulated as a challenging mixed-integer non-convex optimization problem. To tackle it, we first derive a closed-form optimal flight altitude under specific VLC channel gain threshold. Subsequently, we optimize the UAV horizontal trajectory by integrating a novel pheromone-driven reward mechanism with the twin delayed deep deterministic policy gradient algorithm, which enables adaptive UAV motion strategy in complex environments. Simulation results validate that the derived optimal altitude effectively reduces the flight distance by up to 35% compared to baseline methods. Additionally, the proposed reward mechanism significantly shortens the convergence steps by approximately 50%, demonstrating notable efficiency gains in the context of UAV-assisted VLC data collection.
Overcoming BS Down-Tilt for Air-Ground ISAC Coverage: Antenna Design, Beamforming and User Scheduling
Jan 18, 2026Abstract:Integrated sensing and communication holds great promise for low-altitude economy applications. However, conventional downtilted base stations primarily provide sectorized forward lobes for ground services, failing to sense air targets due to backward blind zones. In this paper, a novel antenna structure is proposed to enable air-ground beam steering, facilitating simultaneous full-space sensing and communication (S&C). Specifically, instead of inserting a reflector behind the antenna array for backlobe mitigation, an omni-steering plate is introduced to collaborate with the active array for omnidirectional beamforming. Building on this hardware innovation, sum S&C mutual information (MI) is maximized, jointly optimizing user scheduling, passive coefficients of the omni-steering plate, and beamforming of the active array. The problem is decomposed into two subproblems: one for optimizing passive coefficients via Riemannian gradient on the manifold, and the other for optimizing user scheduling and active array beamforming. Exploiting relationships among S&C MI, data decoding MMSE, and parameter estimation MMSE, the original subproblem is equivalently transformed into a sum weighted MMSE problem, rigorously established via the Lagrangian and first-order optimality conditions. Simulations show that the proposed algorithm outperforms baselines in sum-MI and MSE, while providing 360 sensing coverage. Beampattern analysis further demonstrates effective user scheduling and accurate target alignment.
A Low-Cost Multi-Band Waveform Security Framework in Resource-Constrained Communications
Feb 01, 2024Abstract:Traditional physical layer secure beamforming is achieved via precoding before signal transmission using channel state information (CSI). However, imperfect CSI will compromise the performance with imperfect beamforming and potential information leakage. In addition, multiple RF chains and antennas are needed to support the narrow beam generation, which complicates hardware implementation and is not suitable for resource-constrained Internet-of-Things (IoT) devices. Moreover, with the advancement of hardware and artificial intelligence (AI), low-cost and intelligent eavesdropping to wireless communications is becoming increasingly detrimental. In this paper, we propose a multi-carrier based multi-band waveform-defined security (WDS) framework, independent from CSI and RF chains, to defend against AI eavesdropping. Ideally, the continuous variations of sub-band structures lead to an infinite number of spectral features, which can potentially prevent brute-force eavesdropping. Sub-band spectral pattern information is efficiently constructed at legitimate users via a proposed chaotic sequence generator. A novel security metric, termed signal classification accuracy (SCA), is used to evaluate the security robustness under AI eavesdropping. Communication error probability and complexity are also investigated to show the reliability and practical capability of the proposed framework. Finally, compared to traditional secure beamforming techniques, the proposed multi-band WDS framework reduces power consumption by up to six times.
Towards Structural Sparse Precoding: Dynamic Time, Frequency, Space, and Power Multistage Resource Programming
Oct 15, 2023Abstract:In last decades, dynamic resource programming in partial resource domains has been extensively investigated for single time slot optimizations. However, with the emerging real-time media applications in fifth-generation communications, their new quality of service requirements are often measured in temporal dimension. This requires multistage optimization for full resource domain dynamic programming. Taking experience rate as a typical temporal multistage metric, we jointly optimize time, frequency, space and power domains resource for multistage optimization. To strike a good tradeoff between system performance and computational complexity, we first transform the formulated mixed integer non-linear constraints into equivalent convex second order cone constraints, by exploiting the coupling effect among the resources. Leveraging the concept of structural sparsity, the objective of max-min experience rate is given as a weighted 1-norm term associated with the precoding matrix. Finally, a low-complexity iterative algorithm is proposed for full resource domain programming, aided by another simple conic optimization for obtaining its feasible initial result. Simulation verifies that our design significantly outperform the benchmarks while maintaining a fast convergence rate, shedding light on full domain dynamic resource programming of multistage optimizations.
Toward UL-DL Rate Balancing: Joint Resource Allocation and Hybrid-Mode Multiple Access for UAV-BS Assisted Communication Systems
Nov 16, 2021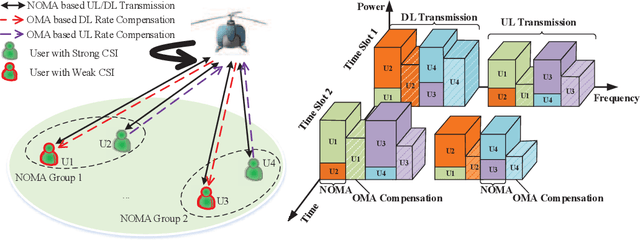
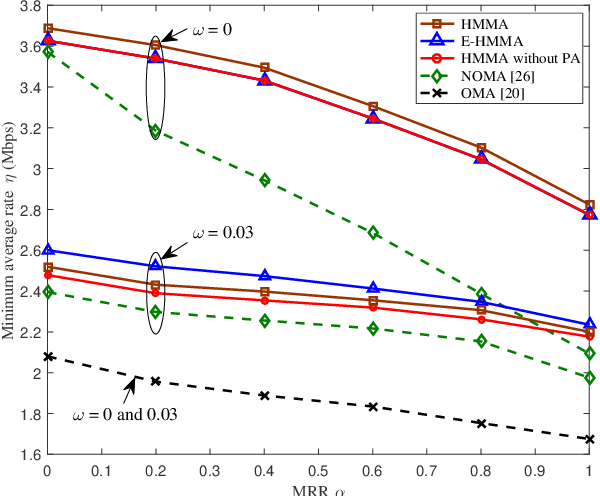

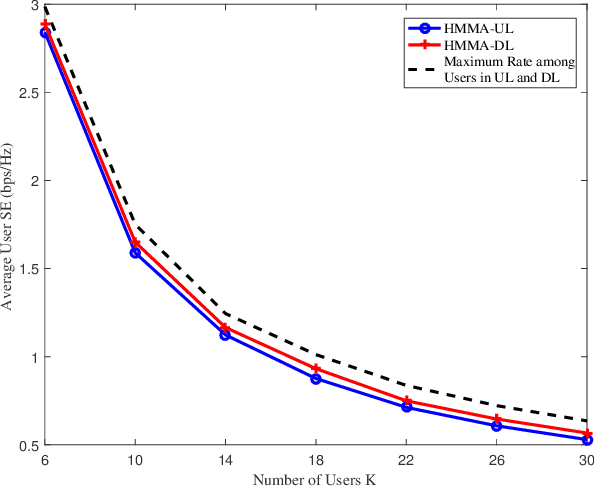
Abstract:In this paper, we investigate unmanned aerial vehicle (UAV) assisted communication systems that require quasi-balanced data rates in uplink (UL) and downlink (DL), as well as users' heterogeneous traffic. To the best of our knowledge, this is the first work to explicitly investigate joint UL-DL optimization for UAV assisted systems under heterogeneous requirements. A hybrid-mode multiple access (HMMA) scheme is proposed toward heterogeneous traffic, where non-orthogonal multiple access (NOMA) targets high average data rate, while orthogonal multiple access (OMA) aims to meet users' instantaneous rate demands by compensating for their rates. HMMA enables a higher degree of freedom in multiple access and achieves a superior minimum average rate among users than the UAV assisted NOMA or OMA schemes. Under HMMA, a joint UL-DL resource allocation algorithm is proposed with a closed-form optimal solution for UL/DL power allocation to achieve quasi-balanced average rates for UL and DL. Furthermore, considering the error propagation in successive interference cancellation (SIC) of NOMA, an enhanced-HMMA scheme is proposed, which demonstrates high robustness against SIC error and a higher minimum average rate than the HMMA scheme.
Physical Layer Anonymous Precoding: The Path to Privacy-Preserving Communications
Sep 18, 2021


Abstract:Next-generation systems aim to increase both the speed and responsiveness of wireless communications, while supporting compelling applications such as edge and cloud computing, remote-Health, vehicle-to-infrastructure communications, etc. As these applications are expected to carry confidential personal data, ensuring user privacy becomes a critical issue. In contrast to traditional security and privacy designs that aim to prevent confidential information from being eavesdropped upon by adversaries, or learned by unauthorized parties, in this paper we consider designs that mask the users' identities during communication, hence resulting in anonymous communications. In particular, we examine the recent interest in physical layer (PHY) anonymous solutions. This line of research departs from conventional higher layer anonymous authentication, encryption and routing protocols, and judiciously manipulates the signaling pattern of transmitted signals in order to mask the senders' PHY characteristics. We first discuss the concept of anonymity at the PHY, and illustrate a strategy that is able to unmask the sender's identity by analyzing his or her PHY information only, i.e., signalling patterns and the inherent fading characteristics. Subsequently, we overview the emerging area of anonymous precoding to preserve the sender's anonymity, while ensuring high receiver-side signal-to-interference-plus-noise ratio (SINR) for communication. This family of anonymous precoding designs represents a new approach to providing anonymity at the PHY, introducing a new dimension for privacy-preserving techniques.
Towards Multi-Functional 6G Wireless Networks: Integrating Sensing, Communication and Security
Jul 16, 2021



Abstract:Integrated sensing and communication (ISAC) has recently emerged as a candidate 6G technology, aiming to unify the two key operations of the future network in spectrum/energy/cost efficient way. ISAC involves communicating information to receivers and simultaneously sensing targets, while both operations use the same waveforms, the same transmitter and ultimately the same network infrastructure. Nevertheless, the inclusion of information signalling into the probing waveform for target sensing raises unique and difficult challenges from the perspective of information security. At the same time, the sensing capability incorporated in the ISAC transmission offers unique opportunities to design secure ISAC techniques. This overview paper discusses these unique challenges and opportunities for the next generation of ISAC networks. We first briefly discuss the fundamentals of waveform design for sensing and communication. Then, we detail the challenges and contradictory objectives involved in securing ISAC transmission, along with state-of-the-art approaches to address them. We then identify the new opportunity of using the sensing capability to obtain knowledge of the targets, as an enabling approach against known weaknesses of PHY security. Finally, we illustrate a low-cost secure ISAC architecture, followed by a series of open research topics. This family of sensing-aided secure ISAC techniques brings a new insight on providing information security, with an eye on robust and hardware-constrained designs tailored for low-cost ISAC devices.
Secure Dual-Functional Radar-Communication Transmission: Exploiting Interference for Resilience Against Target Eavesdropping
Jul 10, 2021



Abstract:We study security solutions for dual-functional radar communication (DFRC) systems, which detect the radar target and communicate with downlink cellular users in millimeter-wave (mmWave) wireless networks simultaneously. Uniquely for such scenarios, the radar target is regarded as a potential eavesdropper which might surveil the information sent from the base station (BS) to communication users (CUs), that is carried by the radar probing signal. Transmit waveform and receive beamforming are jointly designed to maximize the signal-to-interference-plus-noise ratio (SINR) of the radar under the security and power budget constraints. We apply a Directional Modulation (DM) approach to exploit constructive interference (CI), where the known multiuser interference (MUI) can be exploited as a source of useful signal. Moreover, to further deteriorate the eavesdropping signal at the radar target, we utilize destructive interference (DI) by pushing the received symbols at the target towards the destructive region of the signal constellation. Our numerical results verify the effectiveness of the proposed design showing a secure transmission with enhanced performance against benchmark DFRC techniques.
Secure Dual-Functional Radar-Communication System via Exploiting Known Interference in the Presence of Clutter
Jun 08, 2021


Abstract:This paper addresses the problem that designing the transmit waveform and receive beamformer aims to maximize the receive radar SINR for secure dual-functional radar-communication (DFRC) systems, where the undesired multi-user interference (MUI) is transformed to useful power. In this system, the DFRC base station (BS) serves communication users (CUs) and detects the target simultaneously, where the radar target is regarded to be malicious since it might eavesdrop the transmitted information from BS to CUs. Inspired by the constructive interference (CI) approach, the phases of received signals at CUs are rotated into the relaxed decision region, and the undesired MUI is designed to contribute in useful power. Then, the convex approximation method (SCA) is adopted to tackle the optimization problem. Finally, numerical results are given to validate the effectiveness of the proposed method, which shows that it is viable to ensure the communication data secure adopting the techniques that we propose.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge