Marwa Qaraqe
Secure Pinching Antenna-aided ISAC
Jul 17, 2025Abstract:In this letter, a pinching antenna (PA)-aided scheme for establishing a secure integrated sensing and communication system (ISAC) is investigated. The underlying system comprises a dual-functional radar communication (DFRC) base station (BS) linked to multiple waveguides to serve several downlink users while sensing a set of malicious targets in a given area. The PA-aided BS aims at preserving communication confidentiality with the legitimate users while being able to detect malicious targets. One objective of the proposed scheme is to optimize the PA locations, based on which an optimal design of the legitimate signal beamforming and artificial noise covariance matrices is provided to maximize the network's sensing performance, subject to secrecy and total power constraints. We demonstrate the efficacy of the proposed scheme through numerical examples and compare that against a traditional DFRC ISAC system with a uniform linear array of half-wavelength-spaced antennas. We show that the proposed scheme outperforms the baseline PA-aided scheme with equidistant PAs by $3$ dB in terms of illumination power, while it can provide gains of up to $30$ dB of the same metric against a traditional ISAC system with half-wavelength-space uniform linear arrays.
On the Secrecy-Sensing Optimization of RIS-assisted Full-Duplex Integrated Sensing and Communication Network
Apr 29, 2025Abstract:Integrated sensing and communication (ISAC) has recently emerged as a viable technique for establishing sensing and communication using the same resources. Nonetheless, the operation of ISAC networks is often challenged by the absence of a direct link between the sensing node and the targets, and by the risk of disclosing confidential data to malicious targets when using the same signal for both tasks. In this paper, a robust reconfigurable intelligent surface (RIS)-aided scheme for securing a full-duplex (FD) ISAC network is proposed. The considered network consists of uplink and downlink users served in FD through a multi-antenna dual-functional radar communication base station (BS), which employs co-located multi-antenna communication-radar arrays to detect multiple malicious targets while preserving communication secrecy in their presence. Additionally, the BS utilizes an optimized artificial noise (AN) that serves to disrupt the malicious targets' reception and increase the sensing power. By optimally designing the RIS phase shifts, transmit beamforming, AN covariance, and uplink users' transmit power and combining vectors using an alternating optimization-based algorithm, the network's sensing performance is maximized under secrecy and total power constraints. Numerical results present the proposed scheme's efficacy, particularly when a direct link between the BS and the various nodes/targets is absent.
Coordinated Half-Duplex/Full-Duplex Cooperative Rate-Splitting Multiple Access in Multi-Cell Networks
Sep 02, 2024Abstract:This paper explores downlink Cooperative Rate-Splitting Multiple Access (C-RSMA) in a multi-cell wireless network with the assistance of Joint-Transmission Coordinated Multipoint (JT-CoMP). In this network, each cell consists of a base station (BS) equipped with multiple antennas, one or more cell-center users (CCU), and multiple cell-edge users (CEU) located at the edge of the cells. Through JT-CoMP, all the BSs collaborate to simultaneously transmit the data to all the users including the CCUs and CEUs. To enhance the signal quality for the CEUs, CCUs relay the common stream to the CEUs by operating in either half-duplex (HD) or full-duplex (FD) decode-and-forward (DF) relaying mode. In this setup, we aim to jointly optimize the beamforming vectors at the BS, the allocation of common stream rates, the transmit power at relaying users, i.e., CCUs, and the time slot fraction, aiming to maximize the minimum achievable data rate. However, the formulated optimization problem is non-convex and is challenging to solve directly. To address this challenge, we employ change-of-variables, first-order Taylor approximations, and a low-complexity algorithm based on Successive Convex Approximation (SCA). We demonstrate through simulation results the efficacy of the proposed scheme, in terms of average achievable data rate, and we compare its performance to that of four baseline schemes, including HD/FD cooperative non-orthogonal multiple access (C-NOMA), NOMA, and RSMA without user cooperation. The results show that the proposed FD C-RSMA can achieve 25% over FD C-NOMA and the proposed HD C-RSMA can achieve 19% over HD C-NOMA respectively, when the BS transmit power is 20 dBm.
Enhancing Trust and Security in the Vehicular Metaverse: A Reputation-Based Mechanism for Participants with Moral Hazard
May 23, 2024



Abstract:In this paper, we tackle the issue of moral hazard within the realm of the vehicular Metaverse. A pivotal facilitator of the vehicular Metaverse is the effective orchestration of its market elements, primarily comprised of sensing internet of things (SIoT) devices. These SIoT devices play a critical role by furnishing the virtual service provider (VSP) with real-time sensing data, allowing for the faithful replication of the physical environment within the virtual realm. However, SIoT devices with intentional misbehavior can identify a loophole in the system post-payment and proceeds to deliver falsified content, which cause the whole vehicular Metaverse to collapse. To combat this significant problem, we propose an incentive mechanism centered around a reputation-based strategy. Specifically, the concept involves maintaining reputation scores for participants based on their interactions with the VSP. These scores are derived from feedback received by the VSP from Metaverse users regarding the content delivered by the VSP and are managed using a subjective logic model. Nevertheless, to prevent ``good" SIoT devices with false positive ratings to leave the Metaverse market, we build a vanishing-like system of previous ratings so that the VSP can make informed decisions based on the most recent and accurate data available. Finally, we validate our proposed model through extensive simulations. Our primary results show that our mechanism can efficiently prevent malicious devices from starting their poisoning attacks. At the same time, trustworthy SIoT devices that had a previous miss-classification are not banned from the market.
Performance Analysis of Underwater Acoustic Channel Amid Jamming by Random Jammers
May 05, 2024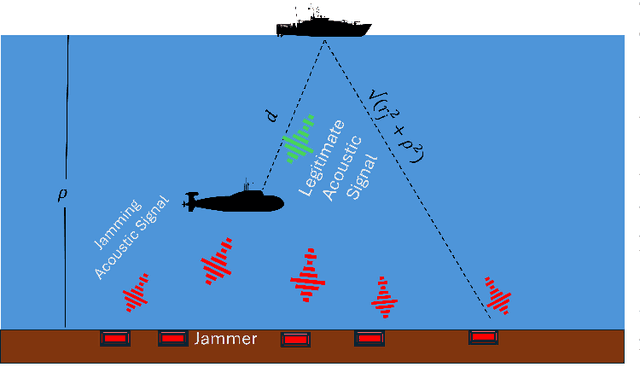
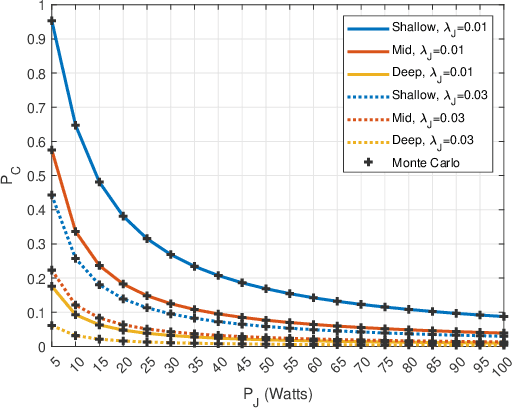
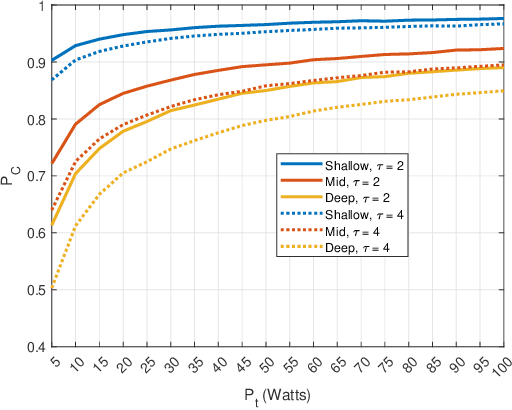
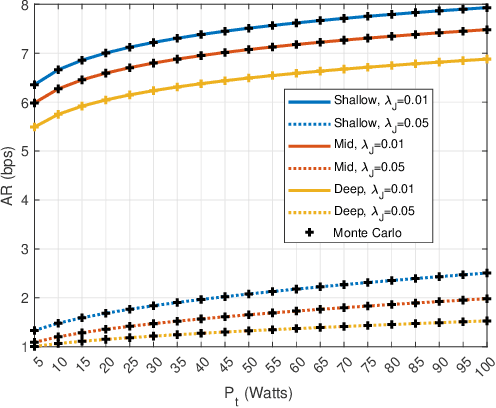
Abstract:Underwater communication networks are increasingly popularized by various important maritime applications. However, this also leads to an increased threat landscape. This letter presents the first study that considers jamming attacks by random jammers present in the surroundings of legitimate transceivers in underwater acoustic communication systems. We investigate the impact of jamming attacks on various performance parameters of the legitimate underwater acoustic communication link. In particular, we investigate the legitimate link using stochastic geometry for important performance parameters, namely coverage probability, average rate, and energy efficiency of the link between two legitimate nodes, i.e., underwater and surface nodes. We then derive and present tractable expressions for these performance parameters. Finally, we performed a Monte Carlo simulation to validate our analysis. We plot the performance metrics against the transmit power, and jamming power for different intensities of the jammers in shallow, mid, and deep water scenarios. Results reveal that on average, jamming in deep water has a relatively high impact on the performance of legitimate link than in shallow water.
On the Secrecy Enhancement of an Integrated Ground-Aerial Network with a Hybrid FSO/THz Feeder Link
Mar 24, 2024Abstract:High altitude platforms (HAPs)-aided terrestrial-aerial communication technology based on free-space optical (FSO) and Terahertz (THz) feeder links has been attracting notable interest recently due to its great potential in reaching a higher data rate and connectivity. Nonetheless, the presence of harsh vertical propagation environments and potential aerial eavesdroppers are two of the main challenges limiting the reliability and security of such a technology. In this work, a secrecy-enhancing scheme for HAP-aided ground-aerial communication is proposed. The considered network consists of HAP-assisted communication between a ground station and a legitimate user under the threat of an aerial and ground eavesdropper. Thus, the proposed scheme leverages (i) HAP diversity by exploiting the presence of multiple flying HAPs and (ii) the use of a hybrid FSO/THz transmission scheme to offer better resilience against eavesdropping attacks. An analytical secrecy outage probability (SOP) expression is derived for the scheme in consideration. Results manifest the notable gain in security of the proposed scheme with respect to both (i) the single-HAP and (ii) THz feeder-based benchmark ones, where the proposed scheme's SOP is decreased by four orders of magnitude using $4$ HAPs with respect to the first benchmark scheme, while a $5$-dB secrecy gain is manifested with respect to the second benchmark one.
A BFF-Based Attention Mechanism for Trajectory Estimation in mmWave MIMO Communications
Jan 23, 2024



Abstract:This paper explores a novel Neural Network (NN) architecture suitable for Beamformed Fingerprint (BFF) localization in a millimeter-wave (mmWave) multiple-input multiple-output (MIMO) outdoor system. The mmWave frequency bands have attracted significant attention due to their precise timing measurements, making them appealing for applications demanding accurate device localization and trajectory estimation. The proposed NN architecture captures BFF sequences originating from various user paths, and through the application of learning mechanisms, subsequently estimates these trajectories. Specifically, we propose a method for trajectory estimation, employing a transformer network (TN) that relies on attention mechanisms. This TN-based approach estimates wireless device trajectories using BFF sequences recorded within a mmWave MIMO outdoor system. To validate the efficacy of our proposed approach, numerical experiments are conducted using a comprehensive dataset of radio measurements in an outdoor setting, complemented with ray tracing to simulate wireless signal propagation at 28 GHz. The results illustrate that the TN-based trajectory estimator outperforms other methods from the existing literature and possesses the ability to generalize effectively to new trajectories outside the training dataset.
Expanding Boundaries: Cross-Media Routing for Seamless Underwater and Aerial Communication
Jul 24, 2023



Abstract:The colossal evolution of wireless communication technologies over the past few years has driven increased interest in its integration in a variety of less-explored environments, such as the underwater medium. In this magazine paper, we present a comprehensive discussion on a novel concept of routing protocol known as cross-media routing, incorporating the marine and aerial interfaces. In this regard, we discuss the limitation of single-media routing and advocate the need for cross-media routing along with the current status of research development in this direction. To this end, we also propose a novel cross-media routing protocol known as bubble routing for autonomous marine systems where different sets of AUVs, USVs, and airborne nodes are considered for the routing problem. We evaluate the performance of the proposed routing protocol by using the two key performance metrics, i.e., packet delivery ratio (PDR) and end-to-end delay. Moreover, we delve into the challenges encountered in cross-media routing, unveiling exciting opportunities for future research and innovation. As wireless communication expands its horizons to encompass the underwater and aerial domains, understanding and addressing these challenges will pave the way for enhanced cross-media communication and exploration.
Location-based Physical Layer Authentication in Underwater Acoustic Communication Networks
Mar 12, 2023Abstract:Research in underwater communication is rapidly becoming attractive due to its various modern applications. An efficient mechanism to secure such communication is via physical layer security. In this paper, we propose a novel physical layer authentication (PLA) mechanism in underwater acoustic communication networks where we exploit the position/location of the transmitter nodes to achieve authentication. We perform transmitter position estimation from the received signals at reference nodes deployed at fixed positions in a predefined underwater region. We use time of arrival (ToA) estimation and derive the distribution of inherent uncertainty in the estimation. Next, we perform binary hypothesis testing on the estimated position to decide whether the transmitter node is legitimate or malicious. We then provide closed-form expressions of false alarm rate and missed detection rate resulted from binary hypothesis testing. We validate our proposal via simulation results, which demonstrate errors' behavior against the link quality, malicious node location, and receiver operating characteristic (ROC) curves. We also compare our results with the performance of previously proposed fingerprint mechanisms for PLA in underwater acoustic communication networks, for which we show a clear advantage of using the position as a fingerprint in PLA.
Full-Duplex Magnetic Induction Communication: Opportunities and Challenges
Dec 17, 2022



Abstract:The demand for high data rates is rapidly increasing as the interest in Magnetic Induction (MI) communication-based underwater applications grow. However, the data rate in MI is limited by the use of low operational frequency in generating a quasi-static magnetic field. In this paper, we propose the use of full-duplex (FD) MI communication to efficiently utilize the available bandwidth and instantly double the data rate. We propose a two-dimensional transceiver architecture to achieve full-duplex communication by exploiting the directional nature of magnetic fields. We further evaluate the proposed end-to-end FD MI communication against self-interference (SI), its impact on communication distance, and robustness in view of orientation sensitivity. Finally, we conclude by discussing typical challenges in the realization of FD MI communication and highlight a few potential future research directions.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge