Waqas Aman
Effective Capacity Analysis of Joint Near and Far-Field Communication in 6G URLLC Networks
Nov 11, 2025Abstract:The emergence of 6G networks enables simultaneous near-field and far-field communications through extremely large antenna arrays and high carrier frequencies. While these regimes enhance spatial multiplexing and link capacity, their coexistence poses new challenges in ensuring quality-of-service (QoS) guarantees for delay-sensitive applications. This paper presents an effective capacity (EC) analysis framework that jointly models near- and far-field communication regimes under distance estimation uncertainty. The user location is modeled as a random variable spanning both propagation regions, and tractable closed-form expression for the EC is derived to quantify delay performance. Numerical results illustrate the impact of estimation variance, QoS exponent, far-field boundary and near-field boundary (Fraunhofer distance) on EC performance.
Benchmarking Online Object Trackers for Underwater Robot Position Locking Applications
Feb 23, 2025



Abstract:Autonomously controlling the position of Remotely Operated underwater Vehicles (ROVs) is of crucial importance for a wide range of underwater engineering applications, such as in the inspection and maintenance of underwater industrial structures. Consequently, studying vision-based underwater robot navigation and control has recently gained increasing attention to counter the numerous challenges faced in underwater conditions, such as lighting variability, turbidity, camera image distortions (due to bubbles), and ROV positional disturbances (due to underwater currents). In this paper, we propose (to the best of our knowledge) a first rigorous unified benchmarking of more than seven Machine Learning (ML)-based one-shot object tracking algorithms for vision-based position locking of ROV platforms. We propose a position-locking system that processes images of an object of interest in front of which the ROV must be kept stable. Then, our proposed system uses the output result of different object tracking algorithms to automatically correct the position of the ROV against external disturbances. We conducted numerous real-world experiments using a BlueROV2 platform within an indoor pool and provided clear demonstrations of the strengths and weaknesses of each tracking approach. Finally, to help alleviate the scarcity of underwater ROV data, we release our acquired data base as open-source with the hope of benefiting future research.
Performance Analysis of Underwater Acoustic Channel Amid Jamming by Random Jammers
May 05, 2024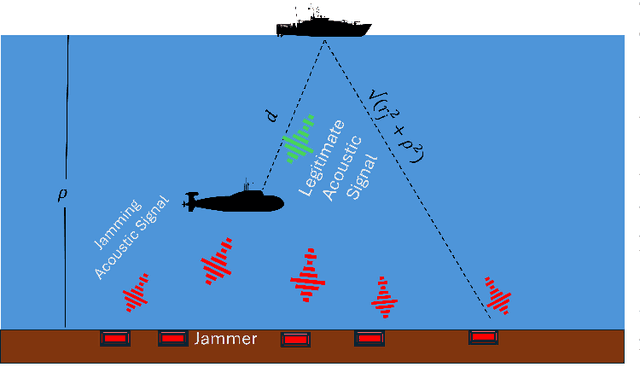
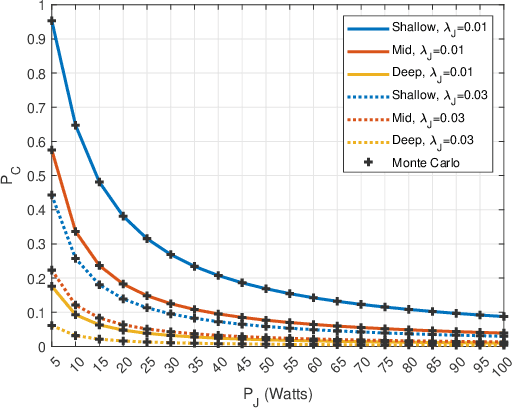
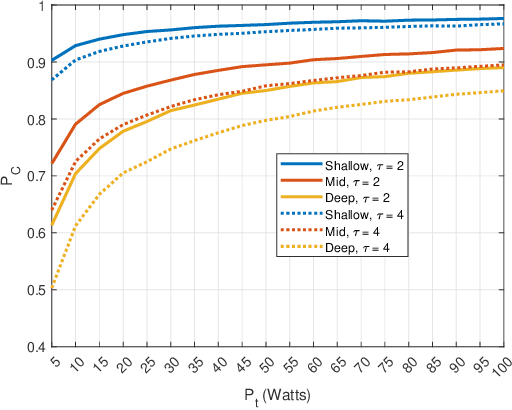
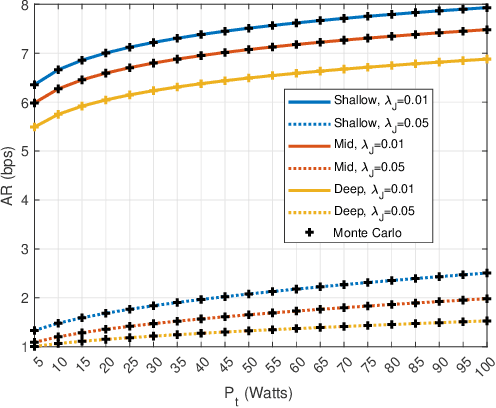
Abstract:Underwater communication networks are increasingly popularized by various important maritime applications. However, this also leads to an increased threat landscape. This letter presents the first study that considers jamming attacks by random jammers present in the surroundings of legitimate transceivers in underwater acoustic communication systems. We investigate the impact of jamming attacks on various performance parameters of the legitimate underwater acoustic communication link. In particular, we investigate the legitimate link using stochastic geometry for important performance parameters, namely coverage probability, average rate, and energy efficiency of the link between two legitimate nodes, i.e., underwater and surface nodes. We then derive and present tractable expressions for these performance parameters. Finally, we performed a Monte Carlo simulation to validate our analysis. We plot the performance metrics against the transmit power, and jamming power for different intensities of the jammers in shallow, mid, and deep water scenarios. Results reveal that on average, jamming in deep water has a relatively high impact on the performance of legitimate link than in shallow water.
On the Potential of Re-configurable Intelligent Surface (RIS)-assisted Physical Layer Authentication (PLA)
May 02, 2024Abstract:Re-configurable Intelligent Surfaces (RIS) technology is increasingly becoming a potential component for next-generation wireless networks, offering enhanced performance in terms of throughput, spectral, and energy efficiency. However, the broadcast nature of RIS-assisted wireless communication makes it vulnerable to malicious attacks at the physical layer. At the same time, physical layer authentication is gaining popularity as a solution to secure wireless networks, thwarting different attacks such as cloning, spoofing, and impersonation by using the random features of the physical layer. In this paper, we investigate RIS-assisted wireless communication systems to unlock the potential of using RIS for physical layer authentication (PLA). In particular, we exploit two distinct features of the physical layer: pathloss and channel impulse response (CIR) for PLA in RIS-assisted wireless communication. We construct hypothesis tests for the estimated features and derive closed-form error expressions. Further, we consider the critical error, i.e., missed detection, as our objective function to minimize by optimizing the phase shift of the RIS pannel. We compare the performance of our proposed mechanisms with PLA schemes using the same features but with no RIS. Furthermore, we thoroughly evaluate our proposed schemes using performance metrics such as the probability of false alarm (PFA), the probability of missed detection (PMD), and the receiver operating characteristic (ROC) curves. The results demonstrate a clear positive impact of RIS on PLA, as it effectively reduces PMD values to zero when determining the optimal phase shift.
Hybrid PLS-ML Authentication Scheme for V2I Communication Networks
Aug 28, 2023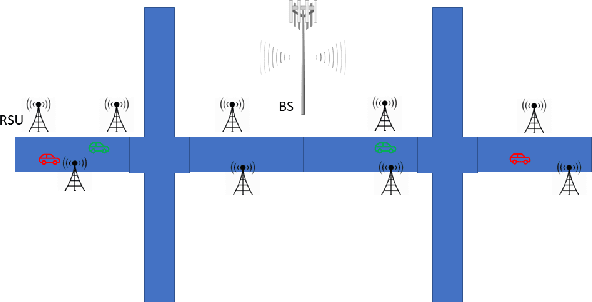
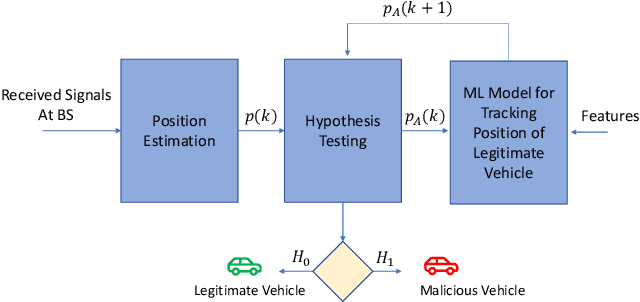
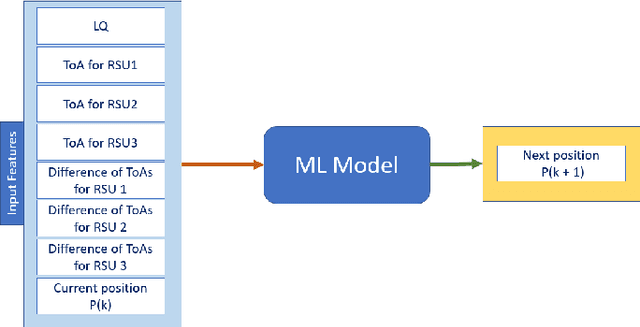
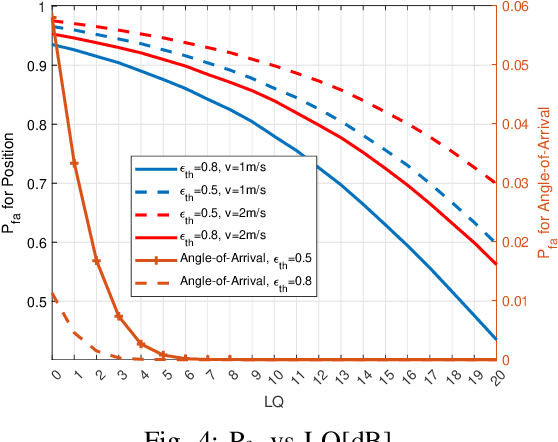
Abstract:Vehicular communication networks are rapidly emerging as vehicles become smarter. However, these networks are increasingly susceptible to various attacks. The situation is exacerbated by the rise in automated vehicles complicates, emphasizing the need for security and authentication measures to ensure safe and effective traffic management. In this paper, we propose a novel hybrid physical layer security (PLS)-machine learning (ML) authentication scheme by exploiting the position of the transmitter vehicle as a device fingerprint. We use a time-of-arrival (ToA) based localization mechanism where the ToA is estimated at roadside units (RSUs), and the coordinates of the transmitter vehicle are extracted at the base station (BS).Furthermore, to track the mobility of the moving legitimate vehicle, we use ML model trained on several system parameters. We try two ML models for this purpose, i.e., support vector regression and decision tree. To evaluate our scheme, we conduct binary hypothesis testing on the estimated positions with the help of the ground truths provided by the ML model, which classifies the transmitter node as legitimate or malicious. Moreover, we consider the probability of false alarm and the probability of missed detection as performance metrics resulting from the binary hypothesis testing, and mean absolute error (MAE), mean square error (MSE), and coefficient of determination $\text{R}^2$ to further evaluate the ML models. We also compare our scheme with a baseline scheme that exploits the angle of arrival at RSUs for authentication. We observe that our proposed position-based mechanism outperforms the baseline scheme significantly in terms of missed detections.
Pathloss-based non-Line-of-Sight Identification in an Indoor Environment: An Experimental Study
Jul 29, 2023

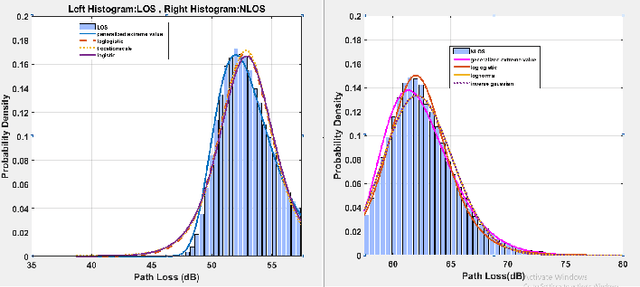
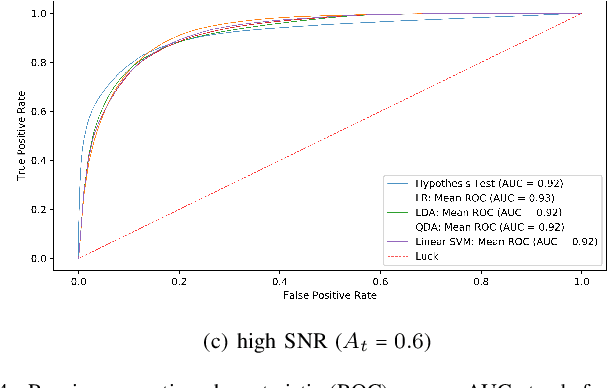
Abstract:This paper reports the findings of an experimental study on the problem of line-of-sight (LOS)/non-line-of-sight (NLOS) classification in an indoor environment. Specifically, we deploy a pair of NI 2901 USRP software-defined radios (SDR) in a large hall. The transmit SDR emits an unmodulated tone of frequency 10 KHz, on a center frequency of 2.4 GHz, using three different signal-to-noise ratios (SNR). The receive SDR constructs a dataset of pathloss measurements from the received signal as it moves across 15 equi-spaced positions on a 1D grid (for both LOS and NLOS scenarios). We utilize our custom dataset to estimate the pathloss parameters (i.e., pathloss exponent) using the least-squares method, and later, utilize the parameterized pathloss model to construct a binary hypothesis test for NLOS identification. Further, noting that the pathloss measurements slightly deviate from Gaussian distribution, we feed our custom dataset to four machine learning (ML) algorithms, i.e., linear support vector machine (SVM) and radial basis function SVM (RBF-SVM), linear discriminant analysis (LDA), quadratic discriminant analysis (QDA), and logistic regression (LR). It turns out that the performance of the ML algorithms is only slightly superior to the Neyman-Pearson-based binary hypothesis test (BHT). That is, the RBF-SVM classifier (the best performing ML classifier) and the BHT achieve a maximum accuracy of 88.24% and 87.46% for low SNR, 83.91% and 81.21% for medium SNR, and 87.38% and 86.65% for high SNR.
Expanding Boundaries: Cross-Media Routing for Seamless Underwater and Aerial Communication
Jul 24, 2023



Abstract:The colossal evolution of wireless communication technologies over the past few years has driven increased interest in its integration in a variety of less-explored environments, such as the underwater medium. In this magazine paper, we present a comprehensive discussion on a novel concept of routing protocol known as cross-media routing, incorporating the marine and aerial interfaces. In this regard, we discuss the limitation of single-media routing and advocate the need for cross-media routing along with the current status of research development in this direction. To this end, we also propose a novel cross-media routing protocol known as bubble routing for autonomous marine systems where different sets of AUVs, USVs, and airborne nodes are considered for the routing problem. We evaluate the performance of the proposed routing protocol by using the two key performance metrics, i.e., packet delivery ratio (PDR) and end-to-end delay. Moreover, we delve into the challenges encountered in cross-media routing, unveiling exciting opportunities for future research and innovation. As wireless communication expands its horizons to encompass the underwater and aerial domains, understanding and addressing these challenges will pave the way for enhanced cross-media communication and exploration.
Location-based Physical Layer Authentication in Underwater Acoustic Communication Networks
Mar 12, 2023Abstract:Research in underwater communication is rapidly becoming attractive due to its various modern applications. An efficient mechanism to secure such communication is via physical layer security. In this paper, we propose a novel physical layer authentication (PLA) mechanism in underwater acoustic communication networks where we exploit the position/location of the transmitter nodes to achieve authentication. We perform transmitter position estimation from the received signals at reference nodes deployed at fixed positions in a predefined underwater region. We use time of arrival (ToA) estimation and derive the distribution of inherent uncertainty in the estimation. Next, we perform binary hypothesis testing on the estimated position to decide whether the transmitter node is legitimate or malicious. We then provide closed-form expressions of false alarm rate and missed detection rate resulted from binary hypothesis testing. We validate our proposal via simulation results, which demonstrate errors' behavior against the link quality, malicious node location, and receiver operating characteristic (ROC) curves. We also compare our results with the performance of previously proposed fingerprint mechanisms for PLA in underwater acoustic communication networks, for which we show a clear advantage of using the position as a fingerprint in PLA.
On the Downlink Coverage Performance of RIS-Assisted THz Networks
Feb 05, 2023

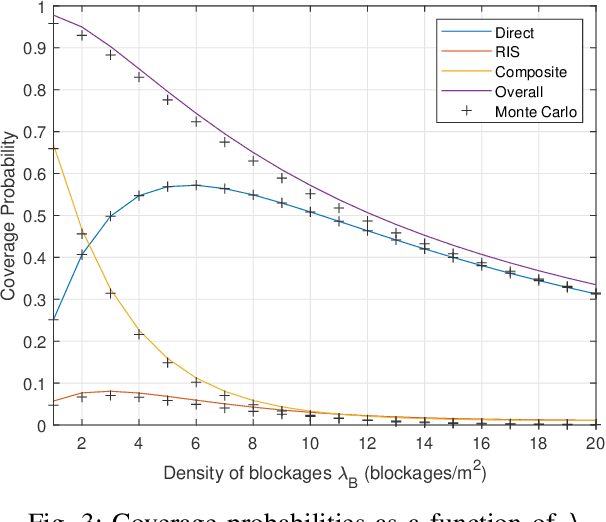

Abstract:This letter provides a stochastic geometry (SG)-based coverage probability (CP) analysis of an indoor terahertz (THz) downlink assisted by a single reconfigurable intelligent surface (RIS) panel. Specifically, multiple access points (AP) deployed on the ceiling of a hall (each equipped with multiple antennas) need to serve multiple user equipment (UE) nodes. Due to presence of blockages, a typical UE may either get served via a direct link, the RIS, or both links (the composite link). The locations of the APs and blockages are modelled as a Poisson point process (PPP) and SG framework is utilized to compute the CP, at a reference UE for all the three scenarios. Monte-Carlo simulation results validate our theoretical analysis.
Transfer learning for non-intrusive load monitoring and appliance identification in a smart home
Jan 08, 2023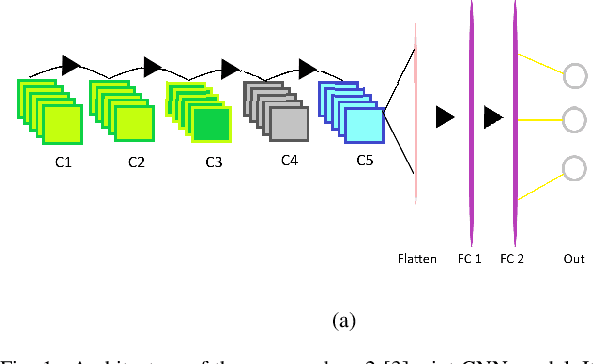

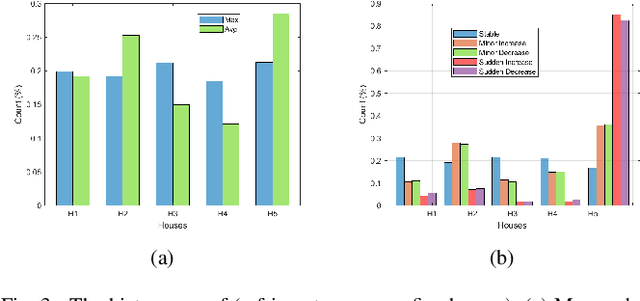

Abstract:Non-intrusive load monitoring (NILM) or energy disaggregation is an inverse problem whereby the goal is to extract the load profiles of individual appliances, given an aggregate load profile of the mains of a home. NILM could help identify the power usage patterns of individual appliances in a home, and thus, could help realize novel energy conservation schemes for smart homes. In this backdrop, this work proposes a novel deep-learning approach to solve the NILM problem and a few related problems as follows. 1) We build upon the reputed seq2-point convolutional neural network (CNN) model to come up with the proposed seq2-[3]-point CNN model to solve the (home) NILM problem and site-NILM problem (basically, NILM at a smaller scale). 2) We solve the related problem of appliance identification by building upon the state-of-the-art (pre-trained) 2D-CNN models, i.e., AlexNet, ResNet-18, and DenseNet-121, which are trained upon two custom datasets that consist of Wavelets and short-time Fourier transform (STFT)-based 2D electrical signatures of the appliances. 3) Finally, we do some basic qualitative inference about an individual appliance's health by comparing the power consumption of the same appliance across multiple homes. Low-frequency REDD dataset is used to train and test the proposed deep learning models for all problems, except site-NILM where REFIT dataset has been used. As for the results, we achieve a maximum accuracy of 94.6\% for home-NILM, 81\% for site-NILM, and 88.9\% for appliance identification (with Resnet-based model).
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge