Bin Qiu
Joint Topology and Power Optimization for Multi-UAV Collaborative Secure Communication
Apr 23, 2025Abstract:In this paper, we investigate an unmanned aerial vehicle (UAV)-enabled secure communication scenario that a cluster of UAVs performs a virtual non-uniform linear array (NULA) to communicate with a base station (BS) in the presence of eavesdroppers (Eves). Our goal is to design the UAV topology, trajectory, and precoding to maximize the system channel capacity. To this end, we convert the original problem into equivalent two-stage problems. Specifically, we first try to maximize the channel gain by meticulously designing the UAV topology. We then study the joint optimization of the trajectory and precoding for total transmit power minimization while satisfying the constraints on providing quality of service (QoS) assurance to the BS, the leakage tolerance to Eves, the per-UAV transmit power, the initial/final locations, and the cylindrical no-fly zones. For the UAV topology design, we prove that the topology follows the Fekete-point distribution. The design of trajectory and precoding is formulated as a non-convex optimization problem which is generally intractable. Subsequently, the non-convex constraints are converted into convex terms, and a double-loop search algorithm is proposed to solve the transmit power minimization problem. Introduce random rotation offsets so as to perform a dynamic stochastic channel to enhance the security. Numerical results demonstrate the superiority of the proposed method in promoting capacity.
Multi-Beam Symbol-Level Secure Communication for Hybrid Near- and Far-Field Communications
Jul 23, 2024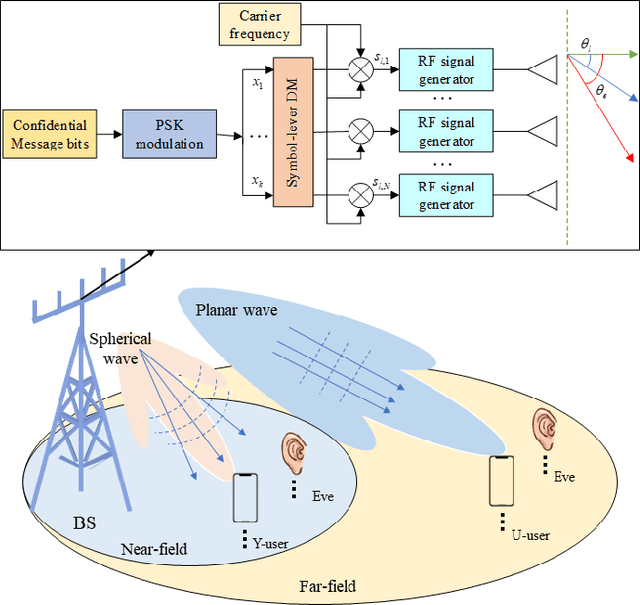
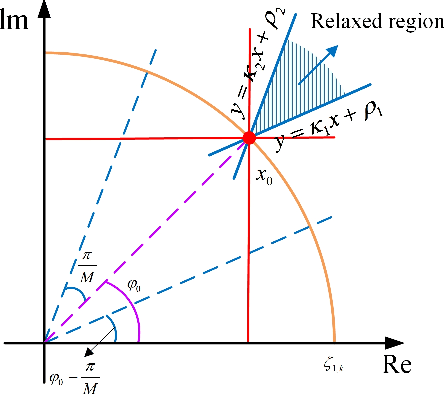
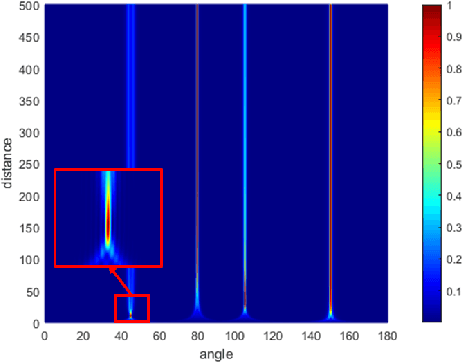
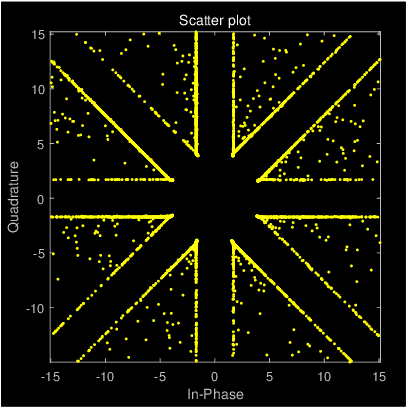
Abstract:This paper introduces a multi-beam secure communication scheme for mixed near-field and far-field (hNF) scenarios, primarily designed to address the challenges faced by sixth-generation (6G) networks in simultaneously managing near-field and far-field communications. This method significantly reduces the signal quality at eavesdroppers(Eves) while ensuring high-quality reception for legitimate users, effectively enhancing communication security. At the transmitter, this study employs multi-beam symbol-level directional modulation to ensure secure and reliable transmission in a mixed eavesdropping environment. Given the uncertainty about eavesdropper information, the transmission beamforming vectors are specially designed to meet specific symbol-level constraints, thereby ensuring effective reception for legitimate users. Experimental and simulation results demonstrate the effectiveness of our approach in improving secrecy performance, reducing transmission power, and enhancing energy efficiency, offering a practical solution to the security challenges faced by future wireless networks.
Robust Multi-Beam Secure mmWave Wireless Communication for Hybrid Wiretapping Systems
Jul 19, 2024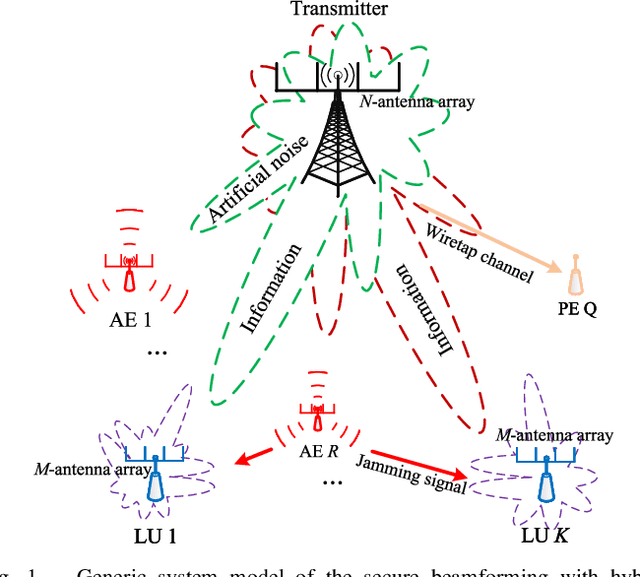
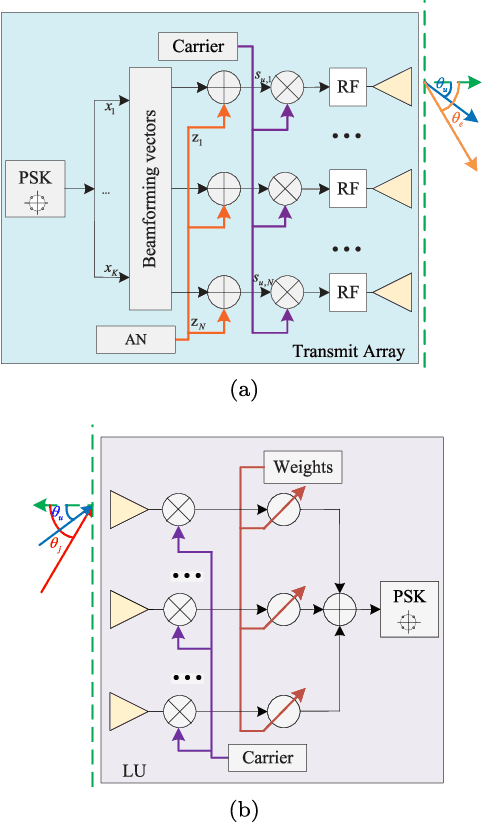
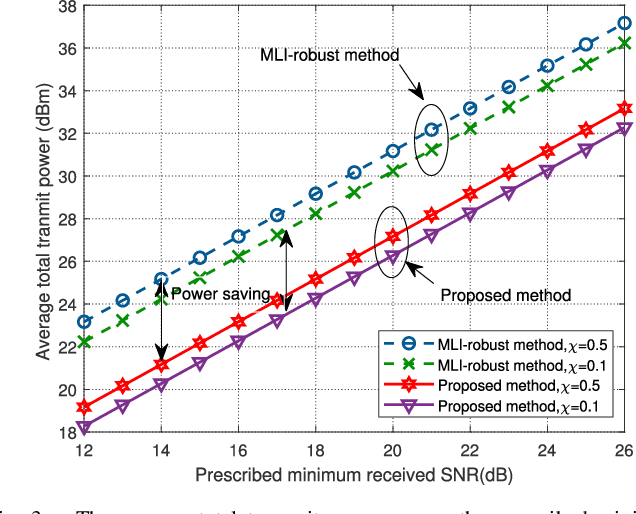
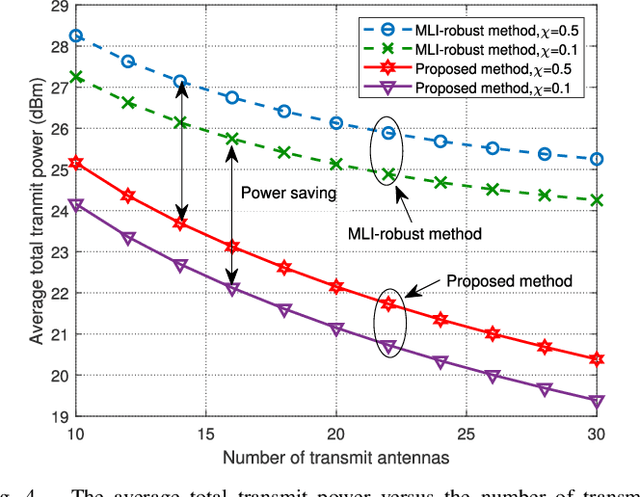
Abstract:In this paper, we consider the physical layer (PHY) security problem for hybrid wiretapping wireless systems in millimeter wave transmission, where active eavesdroppers (AEs) and passive eavesdroppers (PEs) coexist to intercept the confidential messages and emit jamming signals. To achieve secure and reliable transmission, we propose an artificial noise (AN)-aided robust multi-beam array transceiver scheme. Leveraging beamforming, we aim to minimize transmit power by jointly designing the information and AN beamforming, while satisfying valid reception for legitimate users (LUs), per-antenna power constraints for transmitter, as well as all interception power constraints for eavesdroppers (Eves). In particular, the interception power formulation is taken into account for protecting the information against hybrid Eves with imperfect AE channel state information (CSI) and no PE CSI. In light of the intractability of the problem, we reformulate the considered problem by replacing non-convex constraints with tractable forms. Afterwards, a two-stage algorithm is developed to obtain the optimal solution. Additionally, we design the received beamforming weights by means of minimum variance distortionless response, such that the jamming caused by AEs can be effectively suppressed. Simulation results demonstrate the superiority of our proposed scheme in terms of energy efficiency and security.
Joint Information and Jamming Beamforming for Securing IoT Networks With Rate-Splitting
Jul 19, 2024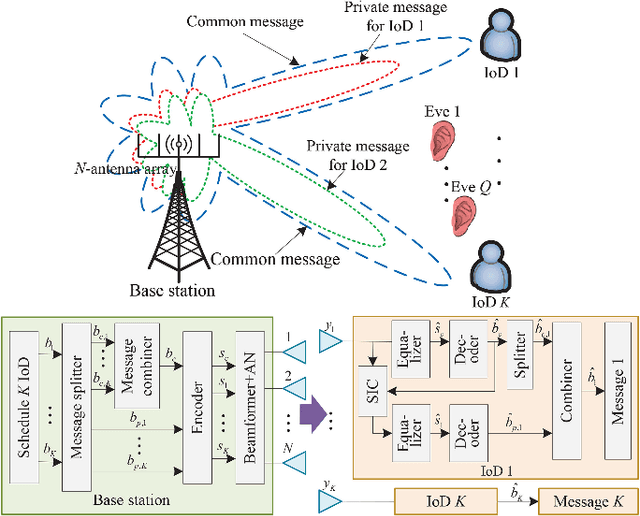
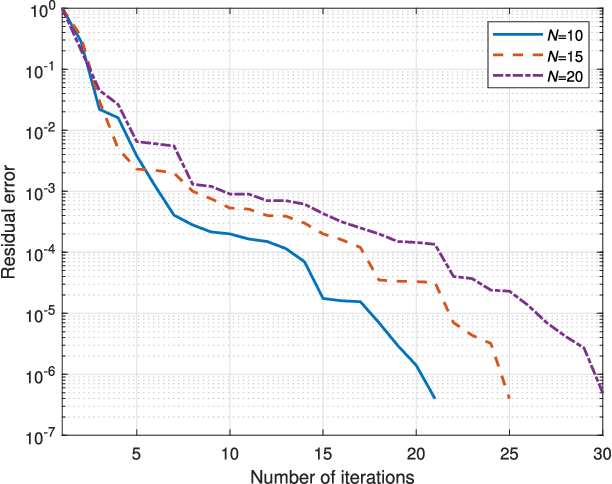
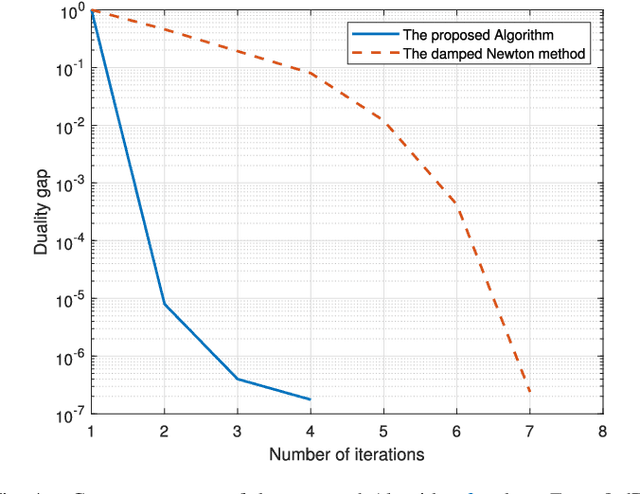
Abstract:The goal of this paper is to address the physical layer (PHY) security problem for multi-user multi-input single-output (MU-MISO) Internet of Things (IoT) systems in the presence of passive eavesdroppers (Eves). To this end, we propose an artificial noise (AN)-aided rate-splitting (RS)-based secure beamforming scheme. Our design considers the dual use of common messages and places the research emphasis on hiding the private messages for secure communication. In particular, leveraging AN-aided RS-based beamforming, we aim to maximize the focused secrecy sum-rate (F-SSR) by jointly designing transmit information and AN beamforming while satisfying the desired received constraints for the private messages at IoT devices (IoDs), and per-antenna transmit power constraint at base station. Then, we proposed a two-stage algorithm to iteratively find the optimal solution. By transforming non-convex terms into linear terms, we first reformulate the original problem as a convex program. Next, we recast the optimization problem to an unconstrained problem to obtain the global optimal solutions. Utilizing the duality framework, we further develop an efficient algorithm based on a barrier interior point method to solve the reformulated problem. Simulation results validate the superior performance of our proposed schemes.
Decomposed and Distributed Directional Modulation for Secure Wireless Communication
Jul 18, 2024Abstract:Directional modulation and artificial noise (AN)-based methods have been widely employed to achieve physical-layer security (PLS). However, these approaches can only achieve angle-dependent secure transmission. This paper presents an AN-aided decomposed and distributed directional modulation (D3M) scheme for secure wireless communications, which takes advantage of the spatial signatures to achieve an extra range-dimension security apart from the angles. Leveraging decomposed and distributed structure, each of modulated signal is represented by mutually orthogonal in-phase and quadrature branches, which are transmitted by two distributed transmitters to enhance PLS. In particular, we first aim to minimize transmit message power by integrated design of the transmit beamformers, subject to prescribed received signal-to-noise ratio (SNR) for the legitimate user (LU) and no inter-branch interference. This guarantees reliable and accurate transmission for the LU with the minimum transmit message power. Considering the leakage power on the sidelobes, AN is superimposed on the messages to try to mask the confidential information transmission. Simulation results demonstrate the security enhancement of our proposed D3M system.
Background-aware Classification Activation Map for Weakly Supervised Object Localization
Dec 29, 2021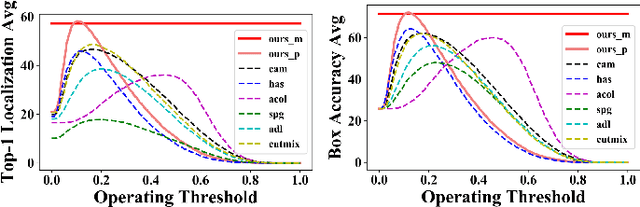
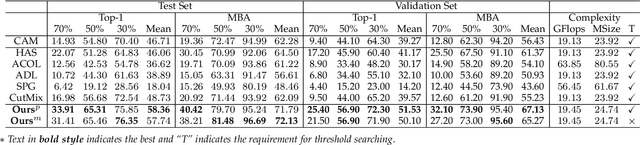
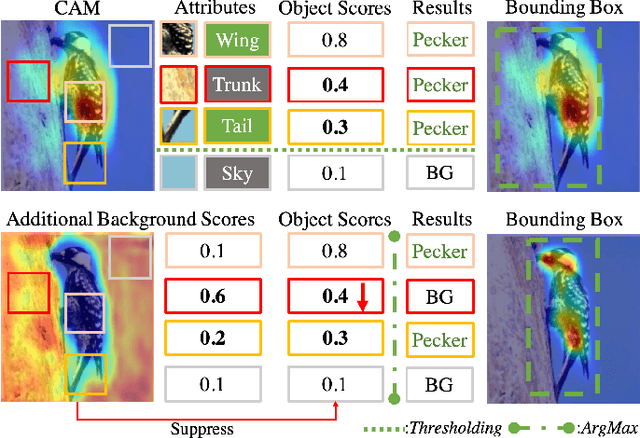
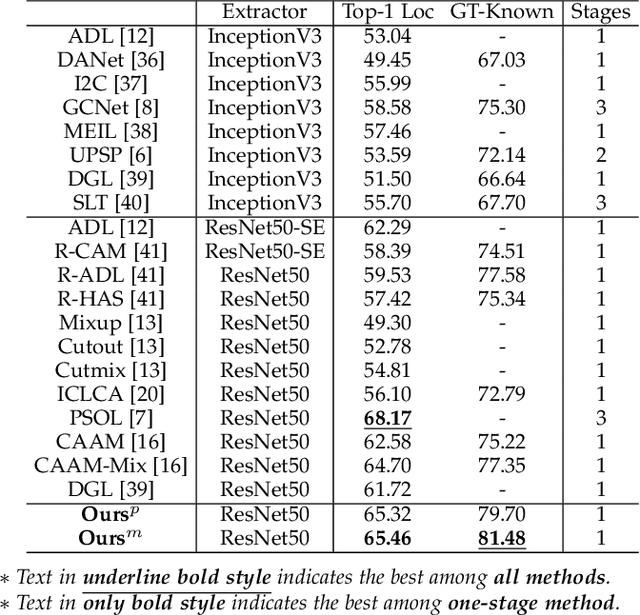
Abstract:Weakly supervised object localization (WSOL) relaxes the requirement of dense annotations for object localization by using image-level classification masks to supervise its learning process. However, current WSOL methods suffer from excessive activation of background locations and need post-processing to obtain the localization mask. This paper attributes these issues to the unawareness of background cues, and propose the background-aware classification activation map (B-CAM) to simultaneously learn localization scores of both object and background with only image-level labels. In our B-CAM, two image-level features, aggregated by pixel-level features of potential background and object locations, are used to purify the object feature from the object-related background and to represent the feature of the pure-background sample, respectively. Then based on these two features, both the object classifier and the background classifier are learned to determine the binary object localization mask. Our B-CAM can be trained in end-to-end manner based on a proposed stagger classification loss, which not only improves the objects localization but also suppresses the background activation. Experiments show that our B-CAM outperforms one-stage WSOL methods on the CUB-200, OpenImages and VOC2012 datasets.
Detection and Attention: Diagnosing Pulmonary Lung Cancer from CT by Imitating Physicians
Dec 14, 2017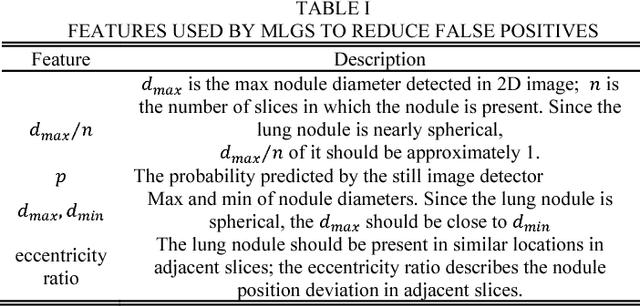
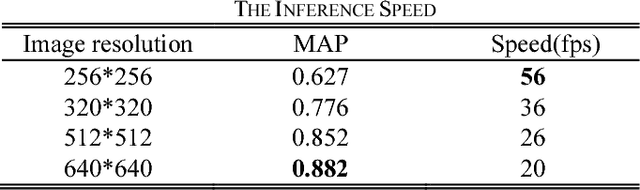
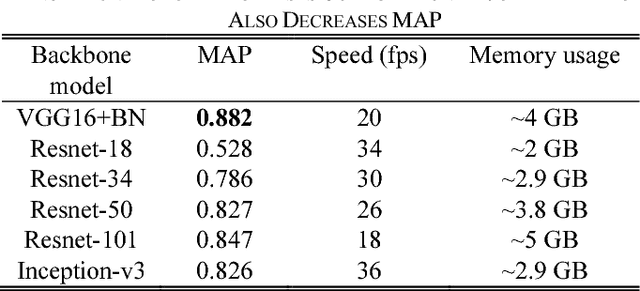
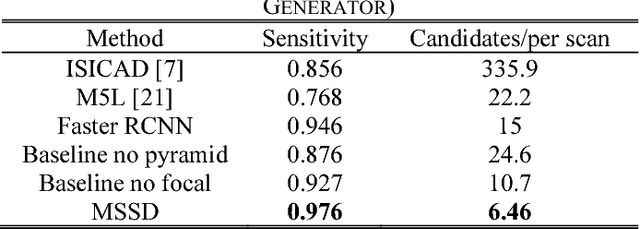
Abstract:This paper proposes a novel and efficient method to build a Computer-Aided Diagnoses (CAD) system for lung nodule detection based on Computed Tomography (CT). This task was treated as an Object Detection on Video (VID) problem by imitating how a radiologist reads CT scans. A lung nodule detector was trained to automatically learn nodule features from still images to detect lung nodule candidates with both high recall and accuracy. Unlike previous work which used 3-dimensional information around the nodule to reduce false positives, we propose two simple but efficient methods, Multi-slice propagation (MSP) and Motionless-guide suppression (MLGS), which analyze sequence information of CT scans to reduce false negatives and suppress false positives. We evaluated our method in open-source LUNA16 dataset which contains 888 CT scans, and obtained state-of-the-art result (Free-Response Receiver Operating Characteristic score of 0.892) with detection speed (end to end within 20 seconds per patient on a single NVidia GTX 1080) much higher than existing methods.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge