Mahmoud Nabil
Negative Selection Approach to support Formal Verification and Validation of BlackBox Models' Input Constraints
Sep 03, 2022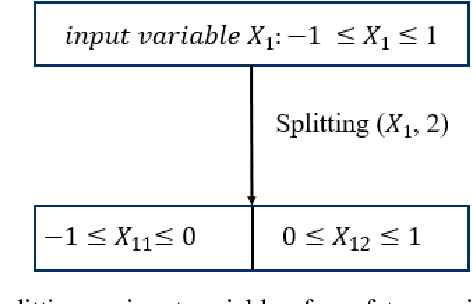
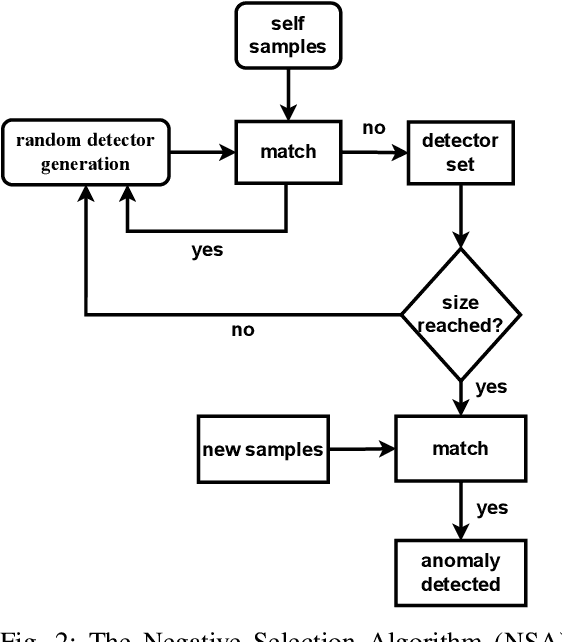
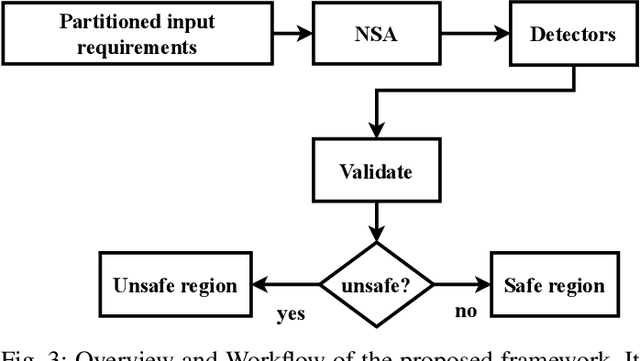
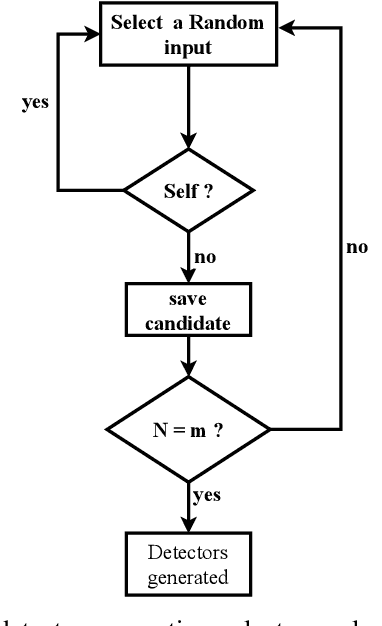
Abstract:Generating unsafe sub-requirements from a partitioned input space to support verification-guided test cases for formal verification of black-box models is a challenging problem for researchers. The size of the search space makes exhaustive search computationally impractical. This paper investigates a meta-heuristic approach to search for unsafe candidate sub-requirements in partitioned input space. We present a Negative Selection Algorithm (NSA) for identifying the candidates' unsafe regions within given safety properties. The Meta-heuristic capability of the NSA algorithm made it possible to estimate vast unsafe regions while validating a subset of these regions. We utilize a parallel execution of partitioned input space to produce safe areas. The NSA based on the prior knowledge of the safe regions is used to identify candidate unsafe region areas and the Marabou framework is then used to validate the NSA results. Our preliminary experimentation and evaluation show that the procedure finds candidate unsafe sub-requirements when validated with the Marabou framework with high precision.
Enabling Content-Centric Device-to-Device Communication in the Millimeter-Wave Band
Apr 12, 2021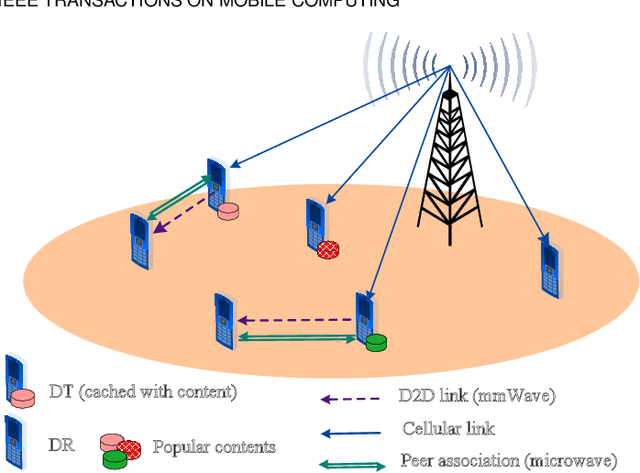
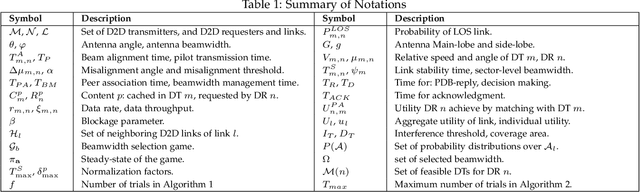
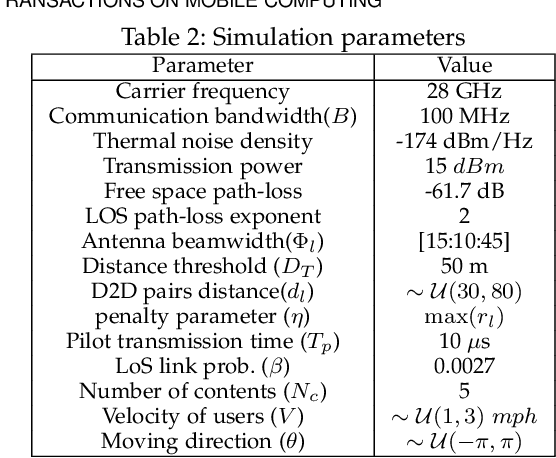
Abstract:The growth in wireless traffic and mobility of devices have congested the core network significantly. This bottleneck, along with spectrum scarcity, made the conventional cellular networks insufficient for the dissemination of large contents. In this paper, we propose a novel scheme that enables efficient initialization of CCN-based D2D networks in the mmWave band through addressing decentralized D2D peer association and antenna beamwidth selection. The proposed scheme considers mmWave characteristics such as directional communication and blockage susceptibility. We propose a heuristic peer association algorithm to associate D2D users using context information, including link stability time and content availability. The performance of the proposed scheme in terms of data throughput and transmission efficiency is evaluated through extensive simulations. Simulation results show that the proposed scheme improves network performance significantly and outperforms other methods in the literature.
Mimic Learning to Generate a Shareable Network Intrusion Detection Model
May 02, 2019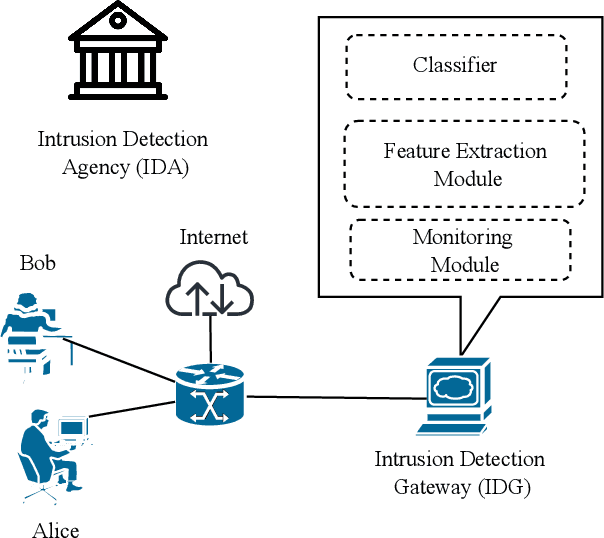
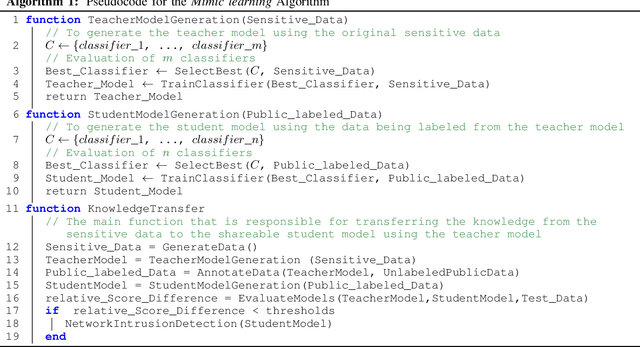
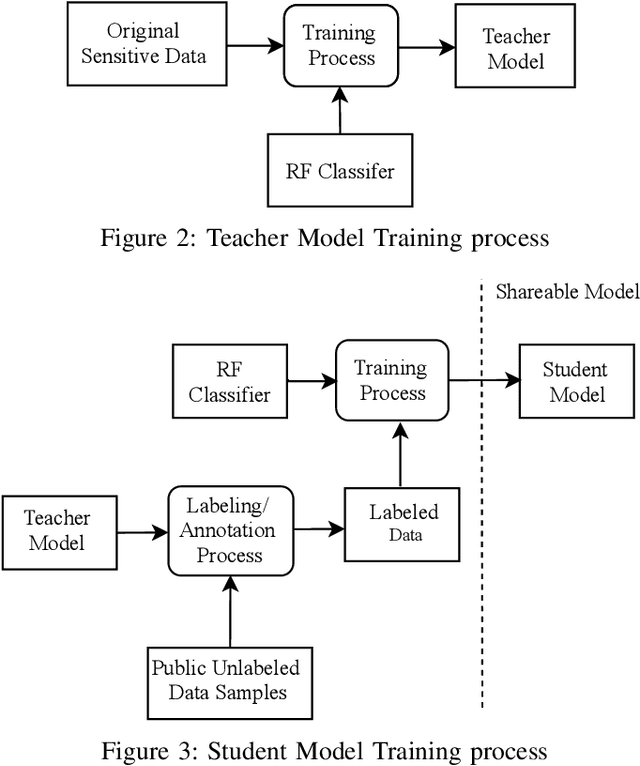
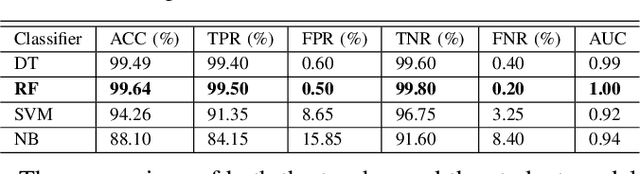
Abstract:Purveyors of malicious network attacks continue to increase the complexity and the sophistication of their techniques, and their ability to evade detection continues to improve as well. Hence, intrusion detection systems must also evolve to meet these increasingly challenging threats. Machine learning is often used to support this needed improvement. However, training a good prediction model can require a large set of labelled training data. Such datasets are difficult to obtain because privacy concerns prevent the majority of intrusion detection agencies from sharing their sensitive data. In this paper, we propose the use of mimic learning to enable the transfer of intrusion detection knowledge through a teacher model trained on private data to a student model. This student model provides a mean of publicly sharing knowledge extracted from private data without sharing the data itself. Our results confirm that the proposed scheme can produce a student intrusion detection model that mimics the teacher model without requiring access to the original dataset.
Deep Recurrent Electricity Theft Detection in AMI Networks with Random Tuning of Hyper-parameters
Sep 06, 2018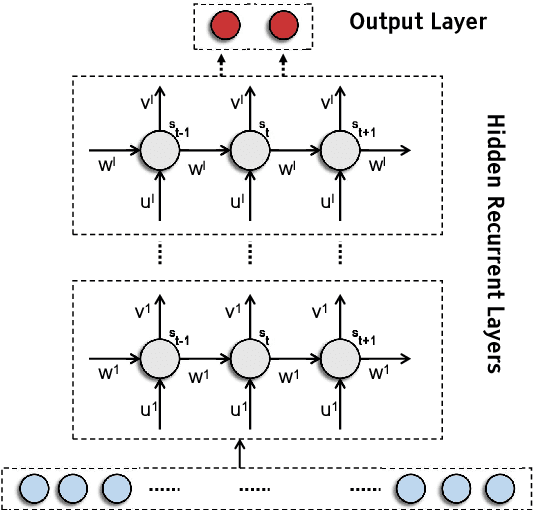
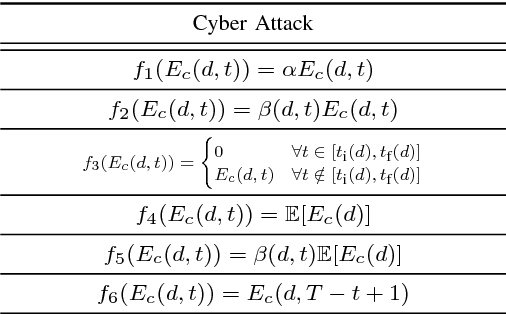
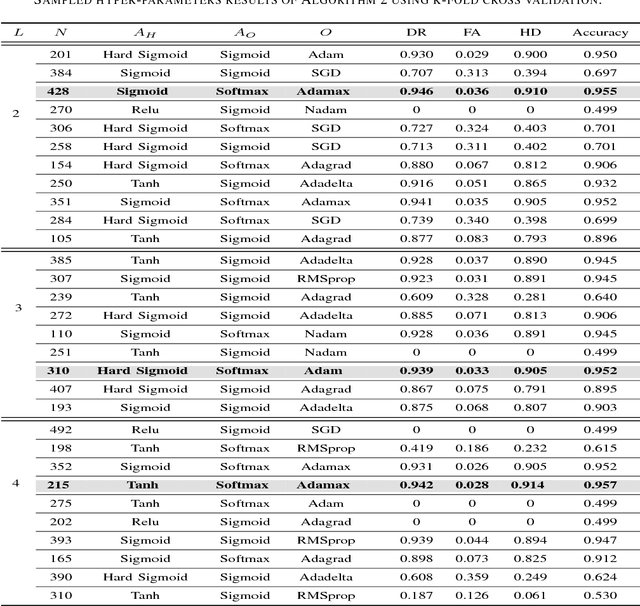
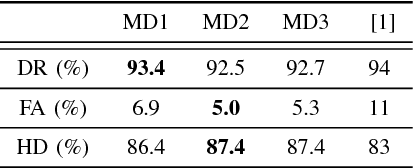
Abstract:Modern smart grids rely on advanced metering infrastructure (AMI) networks for monitoring and billing purposes. However, such an approach suffers from electricity theft cyberattacks. Different from the existing research that utilizes shallow, static, and customer-specific-based electricity theft detectors, this paper proposes a generalized deep recurrent neural network (RNN)-based electricity theft detector that can effectively thwart these cyberattacks. The proposed model exploits the time series nature of the customers' electricity consumption to implement a gated recurrent unit (GRU)-RNN, hence, improving the detection performance. In addition, the proposed RNN-based detector adopts a random search analysis in its learning stage to appropriately fine-tune its hyper-parameters. Extensive test studies are carried out to investigate the detector's performance using publicly available real data of 107,200 energy consumption days from 200 customers. Simulation results demonstrate the superior performance of the proposed detector compared with state-of-the-art electricity theft detectors.
Random Projection and Its Applications
Oct 09, 2017

Abstract:Random Projection is a foundational research topic that connects a bunch of machine learning algorithms under a similar mathematical basis. It is used to reduce the dimensionality of the dataset by projecting the data points efficiently to a smaller dimensions while preserving the original relative distance between the data points. In this paper, we are intended to explain random projection method, by explaining its mathematical background and foundation, the applications that are currently adopting it, and an overview on its current research perspective.
LABR: A Large Scale Arabic Sentiment Analysis Benchmark
May 03, 2015

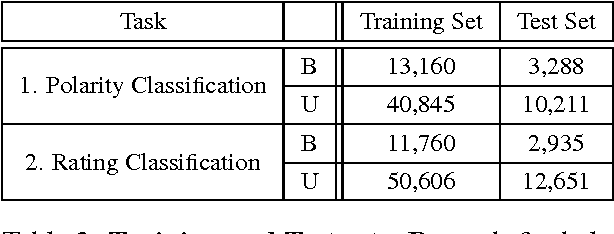

Abstract:We introduce LABR, the largest sentiment analysis dataset to-date for the Arabic language. It consists of over 63,000 book reviews, each rated on a scale of 1 to 5 stars. We investigate the properties of the dataset, and present its statistics. We explore using the dataset for two tasks: (1) sentiment polarity classification; and (2) ratings classification. Moreover, we provide standard splits of the dataset into training, validation and testing, for both polarity and ratings classification, in both balanced and unbalanced settings. We extend our previous work by performing a comprehensive analysis on the dataset. In particular, we perform an extended survey of the different classifiers typically used for the sentiment polarity classification problem. We also construct a sentiment lexicon from the dataset that contains both single and compound sentiment words and we explore its effectiveness. We make the dataset and experimental details publicly available.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge