Dayu Fan
KGRAG-SC: Knowledge Graph RAG-Assisted Semantic Communication
Sep 05, 2025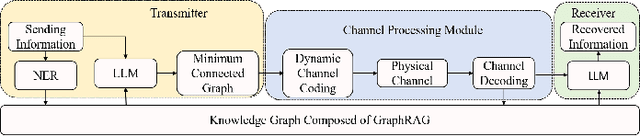
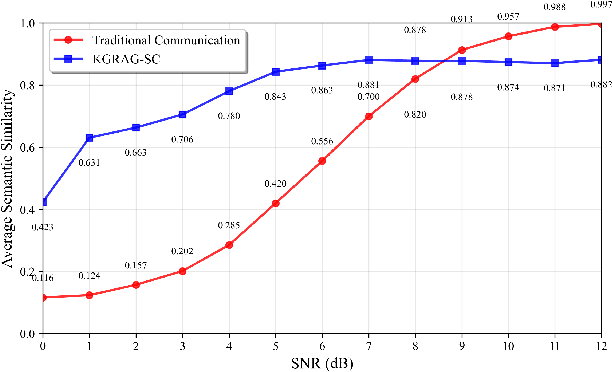
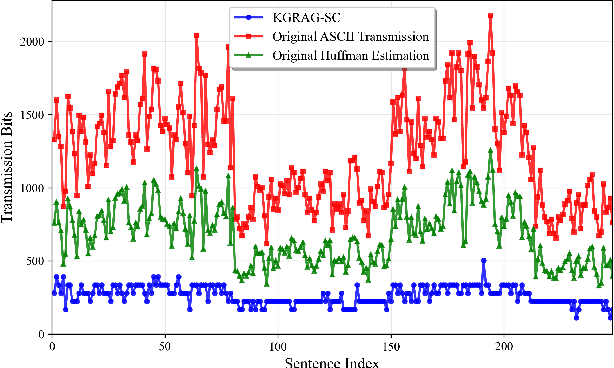
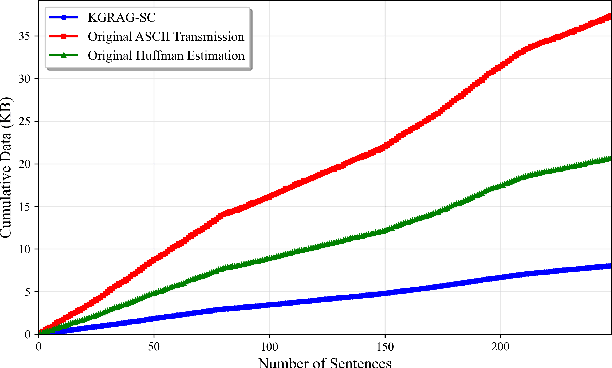
Abstract:The state-of-the-art semantic communication (SC) schemes typically rely on end-to-end deep learning frameworks that lack interpretability and struggle with robust semantic selection and reconstruction under noisy conditions. To address this issue, this paper presents KGRAG-SC, a knowledge graph-assisted SC framework that leverages retrieval-augmented generation principles. KGRAG-SC employs a multi-dimensional knowledge graph, enabling efficient semantic extraction through community-guided entity linking and GraphRAG-assisted processing. The transmitter constructs minimal connected subgraphs that capture essential semantic relationships and transmits only compact entity indices rather than full text or semantic triples. An importance-aware adaptive transmission strategy provides unequal error protection based on structural centrality metrics, prioritizing critical semantic elements under adverse channel conditions. At the receiver, large language models perform knowledge-driven text reconstruction using the shared knowledge graph as structured context, ensuring robust semantic recovery even with partial information loss. Experimental results demonstrate that KGRAG-SC achieves superior semantic fidelity in low Signal-to-Noise Ratio (SNR) conditions while significantly reducing transmission overhead compared to traditional communication methods, highlighting the effectiveness of integrating structured knowledge representation with generative language models for SC systems.
Generative Diffusion Models for Wireless Networks: Fundamental, Architecture, and State-of-the-Art
Jul 22, 2025Abstract:With the rapid development of Generative Artificial Intelligence (GAI) technology, Generative Diffusion Models (GDMs) have shown significant empowerment potential in the field of wireless networks due to advantages, such as noise resistance, training stability, controllability, and multimodal generation. Although there have been multiple studies focusing on GDMs for wireless networks, there is still a lack of comprehensive reviews on their technological evolution. Motivated by this, we systematically explore the application of GDMs in wireless networks. Firstly, starting from mathematical principles, we analyze technical advantages of GDMs and present six representative models. Furthermore, we propose the multi-layer wireless network architecture including sensing layer, transmission layer, application layer, and security plane. We also introduce the core mechanisms of GDM at each of the layers. Subsequently, we conduct a rigorous review on existing GDM-based schemes, with a focus on analyzing their innovative points, the role of GDMs, strengths, and weaknesses. Ultimately, we extract key challenges and provide potential solutions, with the aim of providing directional guidance for future research in this field.
Secure Semantic Communication With Homomorphic Encryption
Jan 17, 2025



Abstract:In recent years, Semantic Communication (SemCom), which aims to achieve efficient and reliable transmission of meaning between agents, has garnered significant attention from both academia and industry. To ensure the security of communication systems, encryption techniques are employed to safeguard confidentiality and integrity. However, traditional cryptography-based encryption algorithms encounter obstacles when applied to SemCom. Motivated by this, this paper explores the feasibility of applying homomorphic encryption to SemCom. Initially, we review the encryption algorithms utilized in mobile communication systems and analyze the challenges associated with their application to SemCom. Subsequently, we employ scale-invariant feature transform to demonstrate that semantic features can be preserved in homomorphic encrypted ciphertext. Based on this finding, we propose a task-oriented SemCom scheme secured through homomorphic encryption. We design the privacy preserved deep joint source-channel coding (JSCC) encoder and decoder, and the frequency of key updates can be adjusted according to service requirements without compromising transmission performance. Simulation results validate that, when compared to plaintext images, the proposed scheme can achieve almost the same classification accuracy performance when dealing with homomorphic ciphertext images. Furthermore, we provide potential future research directions for homomorphic encrypted SemCom.
A Survey of Secure Semantic Communications
Jan 01, 2025



Abstract:Semantic communication (SemCom) is regarded as a promising and revolutionary technology in 6G, aiming to transcend the constraints of ``Shannon's trap" by filtering out redundant information and extracting the core of effective data. Compared to traditional communication paradigms, SemCom offers several notable advantages, such as reducing the burden on data transmission, enhancing network management efficiency, and optimizing resource allocation. Numerous researchers have extensively explored SemCom from various perspectives, including network architecture, theoretical analysis, potential technologies, and future applications. However, as SemCom continues to evolve, a multitude of security and privacy concerns have arisen, posing threats to the confidentiality, integrity, and availability of SemCom systems. This paper presents a comprehensive survey of the technologies that can be utilized to secure SemCom. Firstly, we elaborate on the entire life cycle of SemCom, which includes the model training, model transfer, and semantic information transmission phases. Then, we identify the security and privacy issues that emerge during these three stages. Furthermore, we summarize the techniques available to mitigate these security and privacy threats, including data cleaning, robust learning, defensive strategies against backdoor attacks, adversarial training, differential privacy, cryptography, blockchain technology, model compression, and physical-layer security. Lastly, this paper outlines future research directions to guide researchers in related fields.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge