Alexander Ivanov
Michael Pokorny
Humanity's Last Exam
Jan 24, 2025Abstract:Benchmarks are important tools for tracking the rapid advancements in large language model (LLM) capabilities. However, benchmarks are not keeping pace in difficulty: LLMs now achieve over 90\% accuracy on popular benchmarks like MMLU, limiting informed measurement of state-of-the-art LLM capabilities. In response, we introduce Humanity's Last Exam (HLE), a multi-modal benchmark at the frontier of human knowledge, designed to be the final closed-ended academic benchmark of its kind with broad subject coverage. HLE consists of 3,000 questions across dozens of subjects, including mathematics, humanities, and the natural sciences. HLE is developed globally by subject-matter experts and consists of multiple-choice and short-answer questions suitable for automated grading. Each question has a known solution that is unambiguous and easily verifiable, but cannot be quickly answered via internet retrieval. State-of-the-art LLMs demonstrate low accuracy and calibration on HLE, highlighting a significant gap between current LLM capabilities and the expert human frontier on closed-ended academic questions. To inform research and policymaking upon a clear understanding of model capabilities, we publicly release HLE at https://lastexam.ai.
A collection of the data coding means and event coding means multiplexed over the 100BASE-T1 PMA sublayer, over a 10BASE-T/Te MAU-like entity, over a 10BASE-T1S PMA-like entity, and over the 10BASE-T1L PMA sublayer
Mar 27, 2023Abstract:This collection bundles the following memos dedicated to Fast-speed (100 Mb/s) and Original-speed (10 Mb/s) Ethernet protocols, including upgradeable from Manchester (ME/DME) into Like-a-Manchester (LaM) encoding schemes: [1] "Data Coding Means and Event Coding Means Multiplexed Over the 100BASE-T1 PMA Sublayer" (extends the IEEE 802.3bw protocol, uses a non-LaM encoding, present at pp. 1-4); [2] "Data Coding Means and Event Coding Means Multiplexed Over a 10BASE-T/Te MAU-like Entity" (IEEE 802.3i/az, LaM-based, pp. 5-8); [3] "Data Coding Means and Event Coding Means Multiplexed Over a 10BASE-T1S PMA-like Entity" (IEEE 802.3cg's Clause 147, LaM-based, pp. 9-12); and [4] "Data Coding Means and Event Coding Means Multiplexed Over the 10BASE-T1L PMA Sublayer" (IEEE 802.3cg's Clause 146, non-LaM, pp. 13-16).
A collection of the data coding means and event coding means multiplexed over the 1000BASE-T1, 10GBASE-T, 10GBASE-KR, MultiGBASE-T1, 25G/40GBASE-T, 2.5G/5GBASE-T, 100GBASE-R, 10G/25G-EPON, and 10GPASS-XR microframes
Feb 27, 2023Abstract:This collection bundles the following memos dedicated to Ethernet protocols featuring a very long binary transport word (microframe): [1] "Data Coding Means and Event Coding Means Multiplexed Over the 1000BASE-T1 PCS Payload" (extends the IEEE 802.3bp protocol, present at pp. 1-4 in the bundle); [2] "Data Coding Means and Event Coding Means Multiplexed Over the 10GBASE-T PCS Payload" (IEEE 802.3an, pp. 5-8); [3] "Data Coding Means and Event Coding Means Multiplexed Over the 10GBASE-KR PCS Payload" (IEEE 802.3ap, pp. 9-12); [4] "Data Coding Means and Event Coding Means Multiplexed Over the MultiGBASE-T1 PCS Payload" (IEEE 802.3ch, pp. 13-16); [5] "Data Coding Means and Event Coding Means Multiplexed Over the 25G/40GBASE-T FEC Input" (IEEE 802.3bq, pp. 17-20); [6] "Data Coding Means and Event Coding Means Multiplexed Over the 2.5G/5GBASE-T FEC Input" (IEEE 802.3bz, pp. 21-24); [7] "Data Coding Means and Event Coding Means Multiplexed Over the 100GBASE-R FEC Inputs" (IEEE 802.3bj, pp. 25-28); [8] "Data Coding Means and Event Coding Means Multiplexed Over the 10G/25G-EPON FEC Inputs" (IEEE 802.3av/ca, pp. 29-32); and [9] "Data Coding Means and Event Coding Means Multiplexed Over the 10GPASS-XR FEC Inputs" (IEEE 802.3bn, pp. 33-36).
Manifold Hypothesis in Data Analysis: Double Geometrically-Probabilistic Approach to Manifold Dimension Estimation
Jul 08, 2021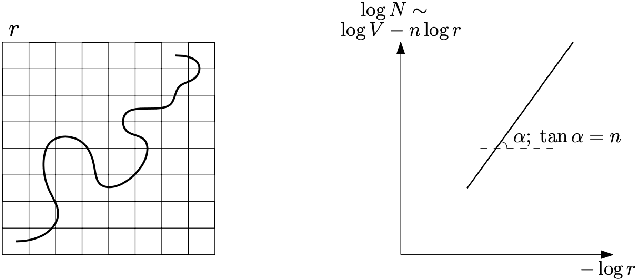
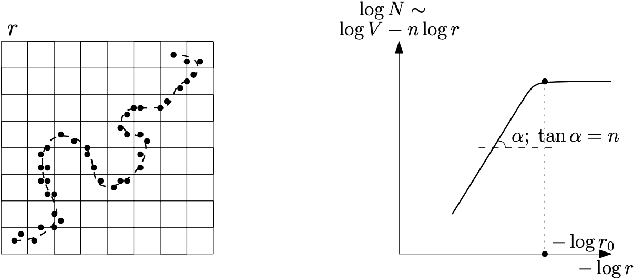

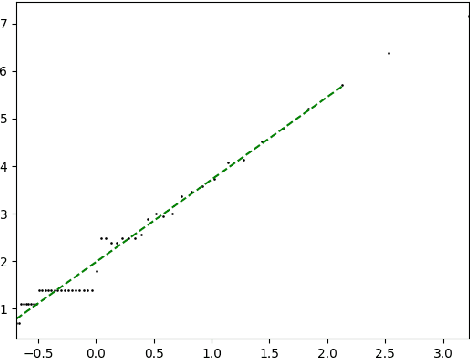
Abstract:Manifold hypothesis states that data points in high-dimensional space actually lie in close vicinity of a manifold of much lower dimension. In many cases this hypothesis was empirically verified and used to enhance unsupervised and semi-supervised learning. Here we present new approach to manifold hypothesis checking and underlying manifold dimension estimation. In order to do it we use two very different methods simultaneously - one geometric, another probabilistic - and check whether they give the same result. Our geometrical method is a modification for sparse data of a well-known box-counting algorithm for Minkowski dimension calculation. The probabilistic method is new. Although it exploits standard nearest neighborhood distance, it is different from methods which were previously used in such situations. This method is robust, fast and includes special preliminary data transformation. Experiments on real datasets show that the suggested approach based on two methods combination is powerful and effective.
Secure Minimum Time Planning Under Environmental Uncertainty: an Extended Treatment
Mar 06, 2018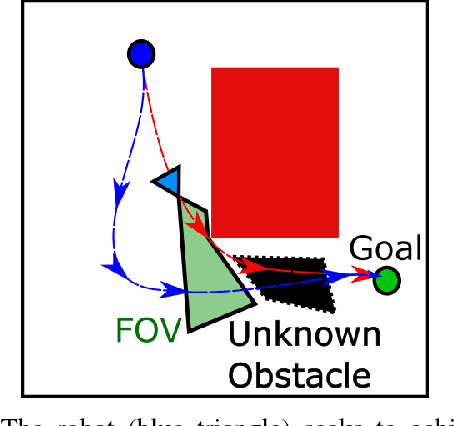
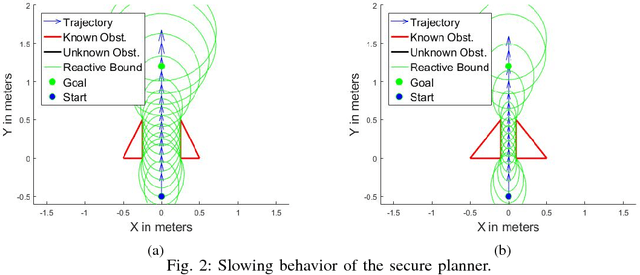
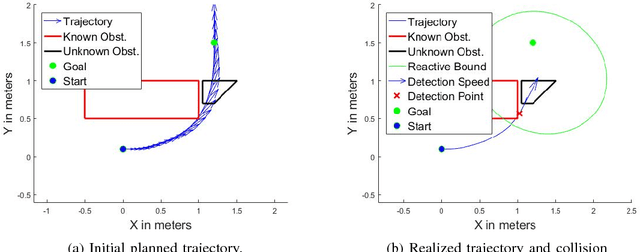
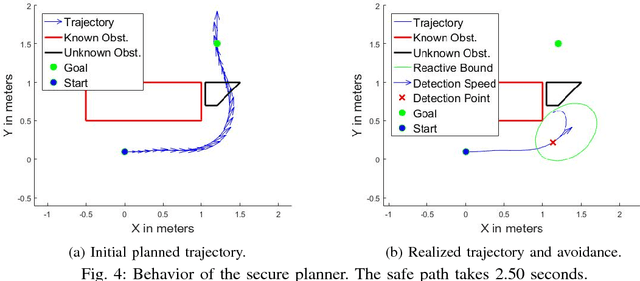
Abstract:Cyber Physical Systems (CPS) are becoming ubiquitous and affect the physical world, yet security is seldom at the forefront of their design. This is especially true of robotic control algorithms which seldom consider the effect of a cyber attack on mission objectives and success. This work presents a secure optimal control algorithm in the face of a cyber attack on a robot's knowledge of the environment. This work focuses on cyber attack, but the results generalize to incomplete or outdated information of an environment. This work fuses ideas from robust control, optimal control, and sensor based planning to provide a generalization of stopping distance in 3D. The planner is implemented in simulation and its properties are analyzed.
Evaluating 35 Methods to Generate Structural Connectomes Using Pairwise Classification
Jun 19, 2017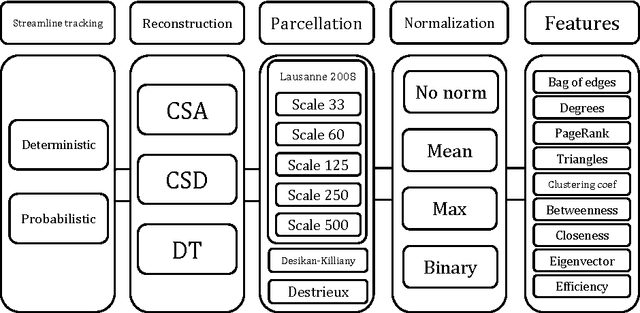
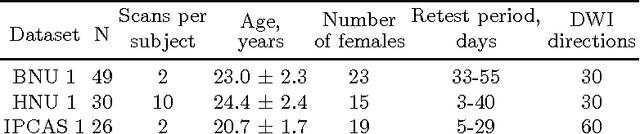

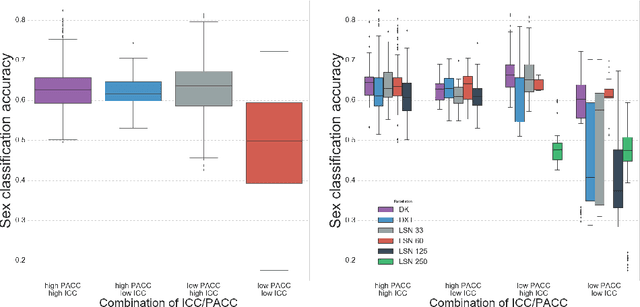
Abstract:There is no consensus on how to construct structural brain networks from diffusion MRI. How variations in pre-processing steps affect network reliability and its ability to distinguish subjects remains opaque. In this work, we address this issue by comparing 35 structural connectome-building pipelines. We vary diffusion reconstruction models, tractography algorithms and parcellations. Next, we classify structural connectome pairs as either belonging to the same individual or not. Connectome weights and eight topological derivative measures form our feature set. For experiments, we use three test-retest datasets from the Consortium for Reliability and Reproducibility (CoRR) comprised of a total of 105 individuals. We also compare pairwise classification results to a commonly used parametric test-retest measure, Intraclass Correlation Coefficient (ICC).
An Extended Consideration of Joint Exploration and Tracking: JET
May 18, 2017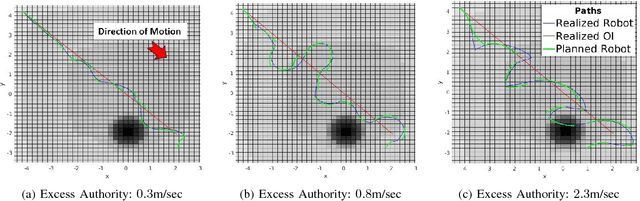
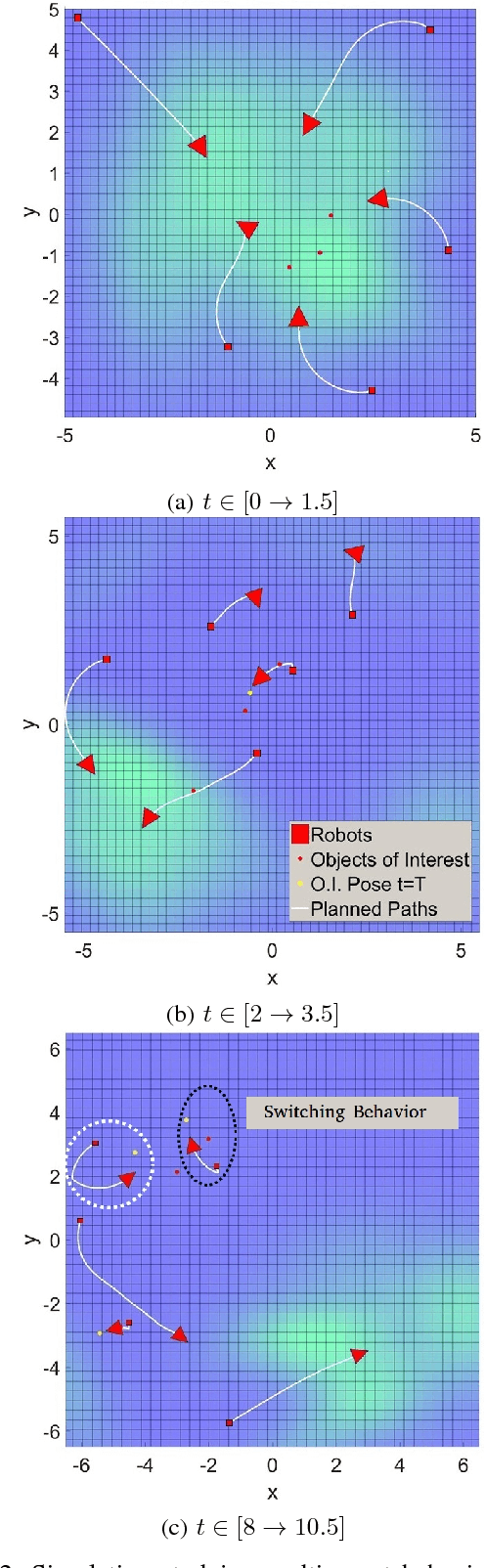
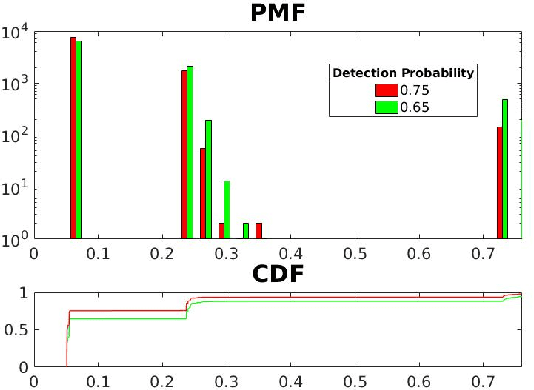
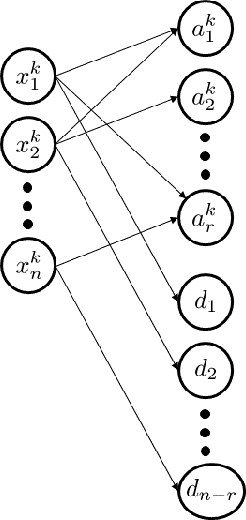
Abstract:Autonomous exploration and multi-object tracking by a team of agents have traditionally been considered as two separate, yet related, problems which are usually solved in two phases: an exploration phase then a tracking phase. The exploration problem is usually viewed through an information theoretic framework where a robotic agent attempts to gather as much information about the environment or an Object of Interest (OI). Conversely, the tracking problem attempts to maintain precise location information about an OI over time. This work proposes a single framework which enables the multi-robot multi-object problem to be solved simultaneously. A hierarchical architecture is used to coordinate robotic agents in the tracking of multiple OIs while simultaneously allowing the task to remain computationally efficient. The primary contributions of this work are a probabilistic constraint on the tracked OIs' covariances guarantees tracking performance throughout the entire mission. The automatic discovery of new OIs, a seamless transition to guaranteed tracking of discovered OIs, and the automatic balancing of exploration with the requirements of tracking.
An Extended Treatment of Uncertainty Constrained robotic Exploration: An Integrated Exploration Planner
Apr 28, 2017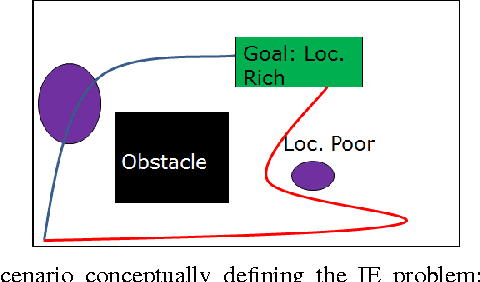
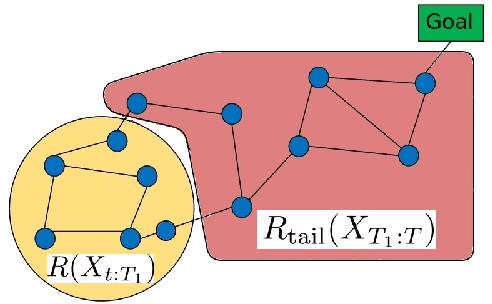
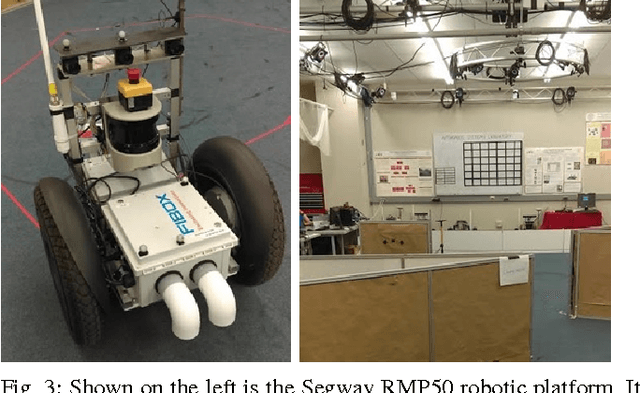
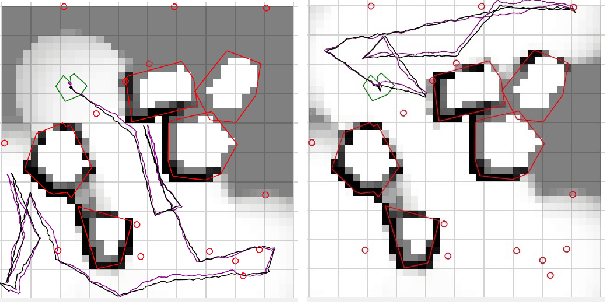
Abstract:Efficient robotic exploration of unknown, sensor limited, global-information-deficient environments poses unique challenges to path planning algorithms. In these difficult environments, no deterministic guarantees on path completion and mission success can be made in general. Integrated Exploration (IE), which strives to combine localization and exploration, must be solved in order to create an autonomous robotic system capable of long term operation in new and challenging environments. This paper formulates a probabilistic framework which allows the creation of exploration algorithms providing probabilistic guarantees of success. A novel connection is made between the Hamiltonian Path Problem and exploration. The Guaranteed Probabilistic Information Explorer (G-PIE) is developed for the IE problem, providing a probabilistic guarantee on path completion, and asymptotic optimality of exploration. A receding horizon formulation, dubbed RH-PIE, is presented which addresses the exponential complexity present in G-PIE. Finally, RH-PIE planner is verified via autonomous, hardware-in-the-loop experiments.
Structural Connectome Validation Using Pairwise Classification
Jan 30, 2017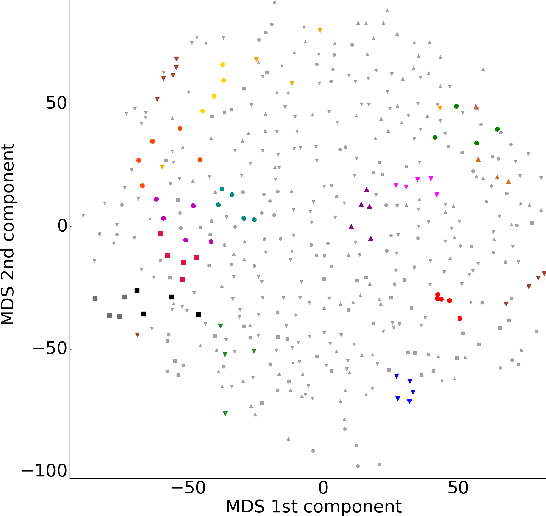
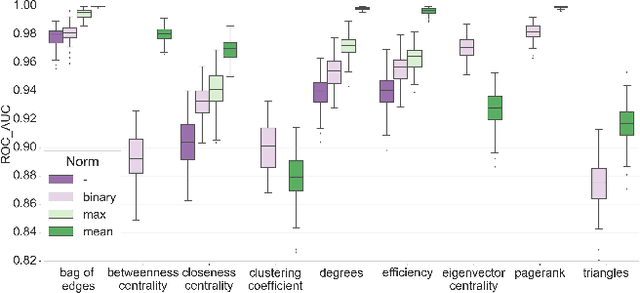
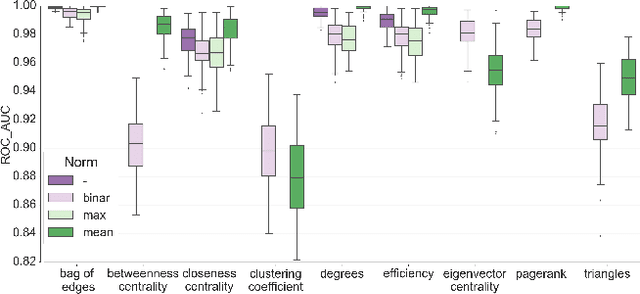
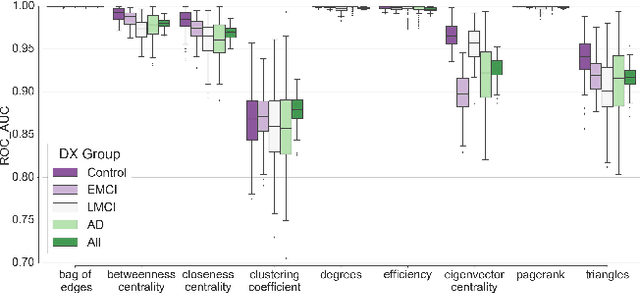
Abstract:In this work, we study the extent to which structural connectomes and topological derivative measures are unique to individual changes within human brains. To do so, we classify structural connectome pairs from two large longitudinal datasets as either belonging to the same individual or not. Our data is comprised of 227 individuals from the Alzheimer's Disease Neuroimaging Initiative (ADNI) and 226 from the Parkinson's Progression Markers Initiative (PPMI). We achieve 0.99 area under the ROC curve score for features which represent either weights or network structure of the connectomes (node degrees, PageRank and local efficiency). Our approach may be useful for eliminating noisy features as a preprocessing step in brain aging studies and early diagnosis classification problems.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge