Stefano Tomasin
Department of Information Engineering, University of Padova, Italy
Physical Layer-Based Device Fingerprinting for Wireless Security: From Theory to Practice
Jun 11, 2025Abstract:The identification of the devices from which a message is received is part of security mechanisms to ensure authentication in wireless communications. Conventional authentication approaches are cryptography-based, which, however, are usually computationally expensive and not adequate in the Internet of Things (IoT), where devices tend to be low-cost and with limited resources. This paper provides a comprehensive survey of physical layer-based device fingerprinting, which is an emerging device authentication for wireless security. In particular, this article focuses on hardware impairment-based identity authentication and channel features-based authentication. They are passive techniques that are readily applicable to legacy IoT devices. Their intrinsic hardware and channel features, algorithm design methodologies, application scenarios, and key research questions are extensively reviewed here. The remaining research challenges are discussed, and future work is suggested that can further enhance the physical layer-based device fingerprinting.
Physical Layer Authentication With Colored RIS in Visible Light Communications
Apr 18, 2025



Abstract:We study a visible light communication (VLC) system that employs a colored reconfigurable intelligent surface (CRIS) based on dichroic mirrors that reflect light at tunable frequencies. A verifier can use the CRIS to authenticate transmissions by comparing received multicolor power profiles with expected patterns. Four CRIS configuration strategies are evaluated: a deterministic cyclic pattern, static random reflectance, dynamic random reflectance, and dynamic random permutation of fixed profiles. Randomized configurations, especially dynamic ones, achieve superior authentication, enabling a novel challenge-response physical-layer authentication scheme over CRIS.
Hybrid Channel- and Coding-Based Challenge-Response Physical-Layer Authentication
Jan 29, 2025


Abstract:This letter proposes a new physical layer authentication mechanism operating at the physical layer of a communication system where the receiver has partial control of the channel conditions (e.g., using an intelligent reflecting surface). We aim to exploit both instantaneous channel state information (CSI) and a secret shared key for authentication. This is achieved by both transmitting an identifying key by wiretap coding (to conceal the key from the attacker) and checking that the instantaneous CSI corresponds to the channel configuration randomly selected by the receiver. We investigate the trade-off between the pilot signals used for CSI estimation and the coding rate (or key length) to improve the overall security of the authentication procedure.
Authentication by Location Tracking in Underwater Acoustic Networks
Oct 04, 2024



Abstract:Physical layer message authentication in underwater acoustic networks (UWANs) leverages the characteristics of the underwater acoustic channel (UWAC) as a fingerprint of the transmitting device. However, as the device moves its UWAC changes, and the authentication mechanism must track such variations. In this paper, we propose a context-based authentication mechanism operating in two steps: first, we estimate the position of the underwater device, then we predict its future position based on the previously estimated ones. To check the authenticity of the transmission, we compare the estimated and the predicted position. The location is estimated using a convolutional neural network taking as input the sample covariance matrix of the estimated UWACs. The prediction uses either a Kalman filter or a recurrent neural network (RNN). The authentication check is performed on the squared error between the predicted and estimated positions. The solution based on the Kalman filter outperforms that built on the RNN when the device moves according to a correlated Gauss-Markov mobility model, which reproduces a typical underwater motion.
Challenge-Response to Authenticate Drone Communications: A Game Theoretic Approach
Oct 01, 2024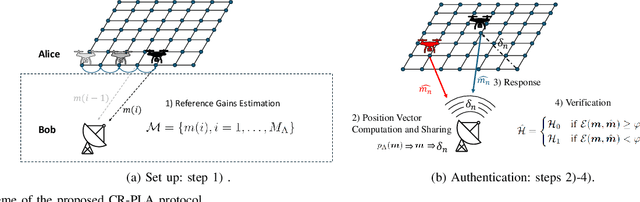
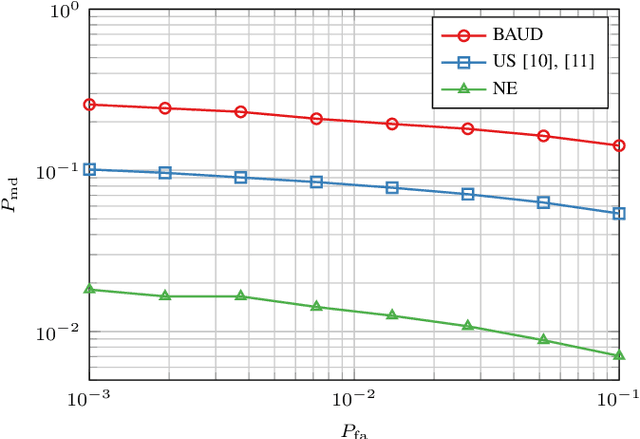
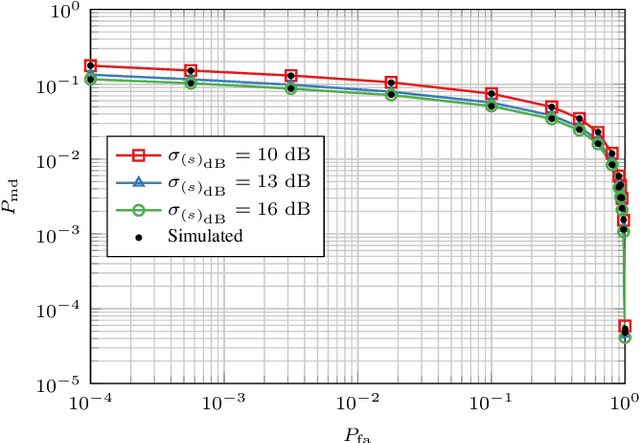
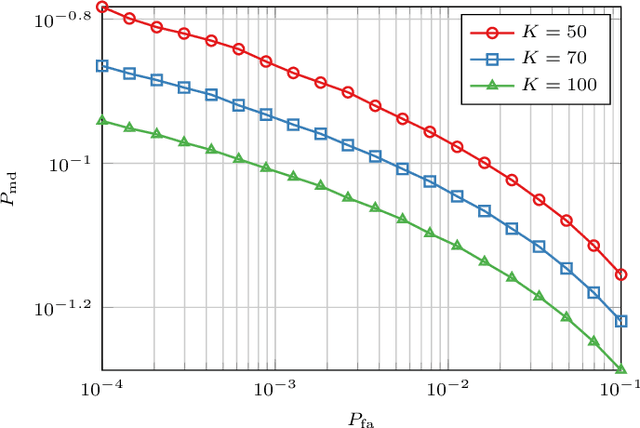
Abstract:In this paper, we propose a novel strategy for physical layer authentications based on the challenge-response concept for a transmitting drone (Alice). In a preliminary training phase, Alice moves over several positions, and Bob (either a drone or a ground device) estimates the Alice-Bob channel gains. Then Alice transmits its message from different random positions (challenge) and Bob, upon receiving the messages, authenticates the sender via a log-likelihood test on the estimated channel gains (response). In turn, the intruder Trudy selects random positions on which she transmits messages on behalf of Alice to Bob. In this paper, we design the probability mass distribution of Alice's challenge positions and the Trudy response positions by modeling the problem as a zero-sum game between Bob and Trudy, where the payoff of Trudy is the missed detection probability. Moreover, we propose three different approaches that minimize the energy spent by Alice without sacrificing security, which differ in computational complexity and resulting energy consumption. Finally, we test the proposed technique via numerical simulations, which include a realistic model of both Alice-Bob and Trudy-Bob fading channels, affected by shadowing.
Performance Limits for Signals of Opportunity-Based Navigation
Jul 23, 2024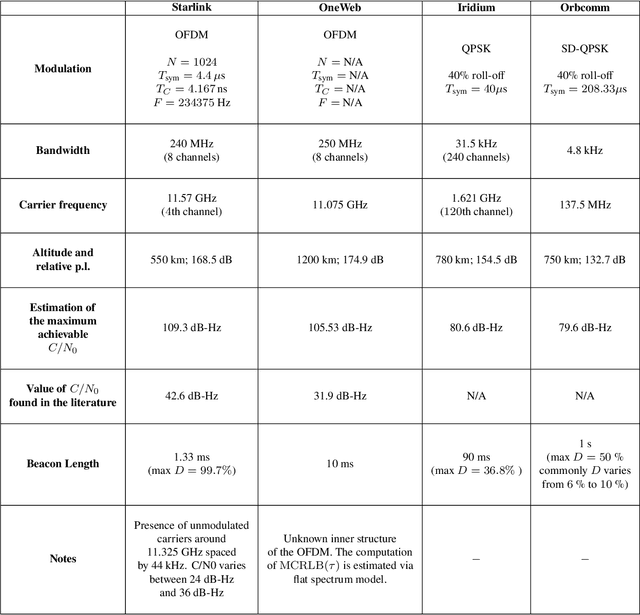
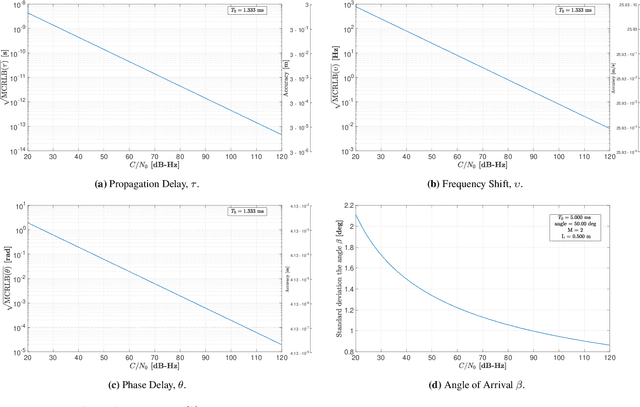
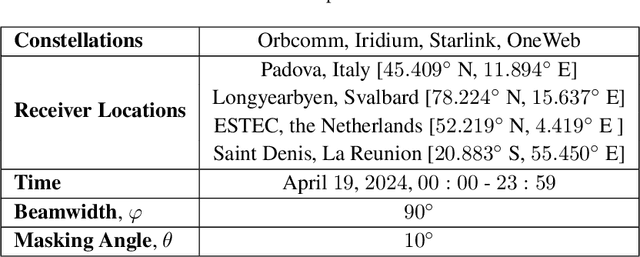
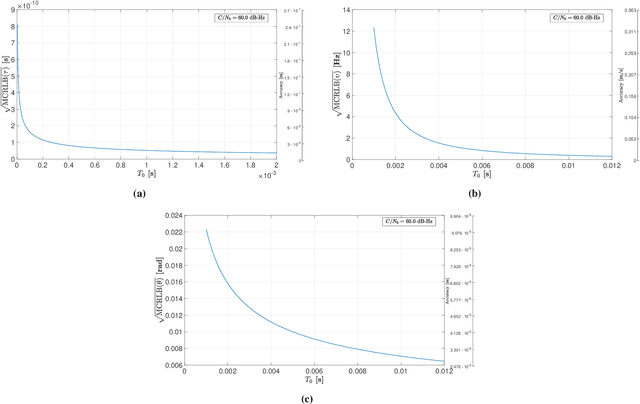
Abstract:This paper investigates the potential of non-terrestrial and terrestrial signals of opportunity (SOOP) for navigation applications. Non-terrestrial SOOP analysis employs modified Cram\`er-Rao lower bound (MCRLB) to establish a relationship between SOOP characteristics and the accuracy of ranging information. This approach evaluates hybrid navigation module performance without direct signal simulation. The MCRLB is computed for ranging accuracy, considering factors like propagation delay, frequency offset, phase offset, and angle-of-arrival (AOA), across diverse non-terrestrial SOOP candidates. Additionally, Geometric Dilution of Precision (GDOP) and low earth orbit (LEO) SOOP availability are assessed. Validation involves comparing MCRLB predictions with actual ranging measurements obtained in a realistic simulated scenario. Furthermore, a qualitative evaluation examines terrestrial SOOP, considering signal availability, accuracy attainability, and infrastructure demands.
Detecting 5G Signal Jammers Using Spectrograms with Supervised and Unsupervised Learning
May 07, 2024Abstract:Cellular networks are potential targets of jamming attacks to disrupt wireless communications. Since the fifth generation (5G) of cellular networks enables mission-critical applications, such as autonomous driving or smart manufacturing, the resulting malfunctions can cause serious damage. This paper proposes to detect broadband jammers by an online classification of spectrograms. These spectrograms are computed from a stream of in-phase and quadrature (IQ) samples of 5G radio signals. We obtain these signals experimentally and describe how to design a suitable dataset for training. Based on this data, we compare two classification methods: a supervised learning model built on a basic convolutional neural network (CNN) and an unsupervised learning model based on a convolutional autoencoder (CAE). After comparing the structure of these models, their performance is assessed in terms of accuracy and computational complexity.
One-Class Classification as GLRT for Jamming Detection in Private 5G Networks
May 07, 2024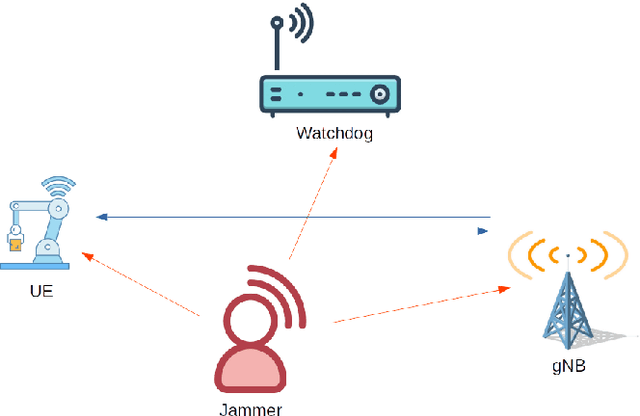
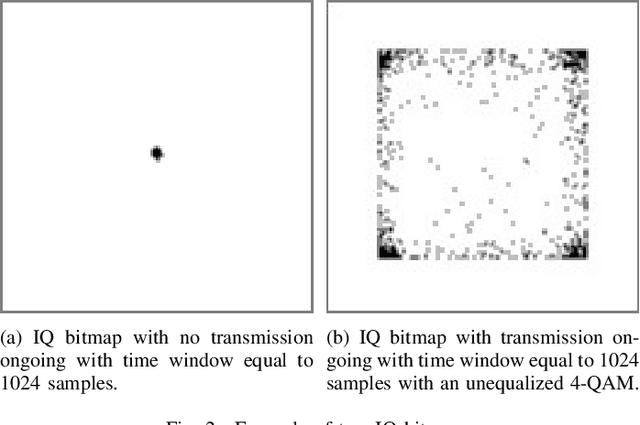
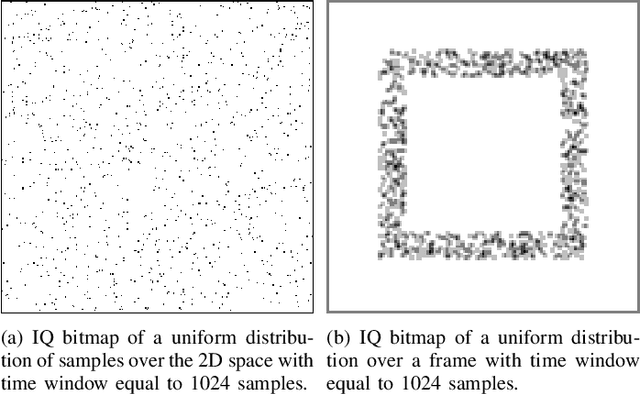
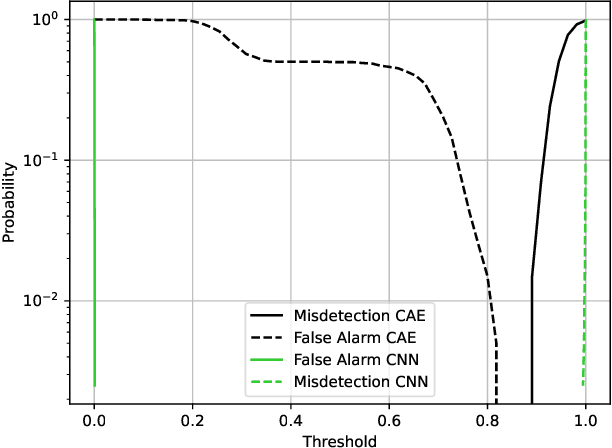
Abstract:5G mobile networks are vulnerable to jamming attacks that may jeopardize valuable applications such as industry automation. In this paper, we propose to analyze radio signals with a dedicated device to detect jamming attacks. We pursue a learning approach, with the detector being a CNN implementing a GLRT. To this end, the CNN is trained as a two-class classifier using two datasets: one of real legitimate signals and another generated artificially so that the resulting classifier implements the GLRT. The artificial dataset is generated mimicking different types of jamming signals. We evaluate the performance of this detector using experimental data obtained from a private 5G network and several jamming signals, showing the technique's effectiveness in detecting the attacks.
Detecting 5G Narrowband Jammers with CNN, k-nearest Neighbors, and Support Vector Machines
May 07, 2024Abstract:5G cellular networks are particularly vulnerable against narrowband jammers that target specific control sub-channels in the radio signal. One mitigation approach is to detect such jamming attacks with an online observation system, based on machine learning. We propose to detect jamming at the physical layer with a pre-trained machine learning model that performs binary classification. Based on data from an experimental 5G network, we study the performance of different classification models. A convolutional neural network will be compared to support vector machines and k-nearest neighbors, where the last two methods are combined with principal component analysis. The obtained results show substantial differences in terms of classification accuracy and computation time.
Energy-Based Optimization of Physical-Layer Challenge-Response Authentication with Drones
May 06, 2024



Abstract:Drones are expected to be used for many tasks in the future and require secure communication protocols. In this work, we propose a novel physical layer authentication (PLA)-based challenge-response (CR) protocol in which a drone Bob authenticates the sender (either on the ground or air) by exploiting his prior knowledge of the wireless channel statistic (fading, path loss, and shadowing). In particular, Bob will move to a set of positions in the space, and by estimating the attenuations of the received signals he will authenticate the sender. We take into account the energy consumption in the design and provide three solutions: a purely greedy solution (PG), an optimal Bellman iterative solution (BI), and a heuristic solution based on the evaluation of the standard deviation of the attenuations in the space. Finally, we demonstrate the effectiveness of our approach through numerical simulations.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge