Mahtab Mirmohseni
UAV-Mounted IRS (UMI) in the Presence of Hovering Fluctuations: 3D Pattern Characterization and Performance Analysis
Apr 23, 2025



Abstract:This paper investigates unmanned aerial vehicle (UAV)-mounted intelligent reflecting surfaces (IRS) to leverage the benefits of this technology for future communication networks, such as 6G. Key advantages include enhanced spectral and energy efficiency, expanded network coverage, and flexible deployment. One of the main challenges in employing UAV-mounted IRS (UMI) technology is the random fluctuations of hovering UAVs. Focusing on this challenge, this paper explores the capabilities of UMI with passive/active elements affected by UAV fluctuations in both horizontal and vertical angles, considering the three-dimensional (3D) radiation pattern of the IRS. The relationship between UAV fluctuations and IRS pattern is investigated by taking into account the random angular vibrations of UAVs. A tractable and closed-form distribution function for the IRS pattern is derived, using linear approximation and by dividing it into several sectors. In addition, closed-form expressions for outage probability (OP) are obtained using central limit theorem (CLT) and Gamma approximation. The theoretical expressions are validated through Monte Carlo simulations. The findings indicate that the random fluctuations of hovering UAVs have a notable impact on the performance of UMI systems. To avoid link interruptions due to UAV instability, IRS should utilize fewer elements, even though this leads to a decrease in directivity. As a result, unlike terrestrial IRS, incorporating more elements into aerial IRS systems does not necessarily improve performance due to the fluctuations in UAV. Numerical results show that the OP can be minimized by selecting the optimal number of IRS elements and using active elements.
On Stochastic Performance Analysis of Secure Integrated Sensing and Communication Networks
Apr 13, 2025Abstract:This paper analyzes the stochastic security performance of a multiple-input multiple-output (MIMO) integrated sensing and communication (ISAC) system in a downlink scenario. A base station (BS) transmits a multi-functional signal to simultaneously communicate with a user, sense a target angular location, and counteract eavesdropping threats. The system includes a passive single-antenna communication eavesdropper and a multi-antenna sensing eavesdropper attempting to infer the target location. The BS-user and BS-eavesdroppers channels follow Rayleigh fading, while the target azimuth angle is uniformly distributed. To evaluate the performance, we derive exact expressions for the secrecy ergodic rate and the ergodic Cramer-Rao lower bound (CRB) for target localization at both the BS and the sensing eavesdropper. This involves computing the probability density functions (PDFs) of the signal-to-noise ratio (SNR) and CRB, leveraging the central limit theorem for tractability. Numerical results validate our findings.
PLS-Assisted Offloading for Edge Computing-Enabled Post-Quantum Security in Resource-Constrained Devices
Apr 13, 2025


Abstract:With the advent of post-quantum cryptography (PQC) standards, it has become imperative for resource-constrained devices (RCDs) in the Internet of Things (IoT) to adopt these quantum-resistant protocols. However, the high computational overhead and the large key sizes associated with PQC make direct deployment on such devices impractical. To address this challenge, we propose an edge computing-enabled PQC framework that leverages a physical-layer security (PLS)-assisted offloading strategy, allowing devices to either offload intensive cryptographic tasks to a post-quantum edge server (PQES) or perform them locally. Furthermore, to ensure data confidentiality within the edge domain, our framework integrates two PLS techniques: offloading RCDs employ wiretap coding to secure data transmission, while non-offloading RCDs serve as friendly jammers by broadcasting artificial noise to disrupt potential eavesdroppers. Accordingly, we co-design the computation offloading and PLS strategy by jointly optimizing the device transmit power, PQES computation resource allocation, and offloading decisions to minimize overall latency under resource constraints. Numerical results demonstrate significant latency reductions compared to baseline schemes, confirming the scalability and efficiency of our approach for secure PQC operations in IoT networks.
Hybrid Channel- and Coding-Based Challenge-Response Physical-Layer Authentication
Jan 29, 2025


Abstract:This letter proposes a new physical layer authentication mechanism operating at the physical layer of a communication system where the receiver has partial control of the channel conditions (e.g., using an intelligent reflecting surface). We aim to exploit both instantaneous channel state information (CSI) and a secret shared key for authentication. This is achieved by both transmitting an identifying key by wiretap coding (to conceal the key from the attacker) and checking that the instantaneous CSI corresponds to the channel configuration randomly selected by the receiver. We investigate the trade-off between the pilot signals used for CSI estimation and the coding rate (or key length) to improve the overall security of the authentication procedure.
RIS-Assisted D2D Communication in the Presence of Interference: Outage Performance Analysis and DNN-Based Prediction
Oct 09, 2024Abstract:This paper analyses the performance of reconfigurable intelligent surface (RIS)-assisted device-to-device (D2D) communication systems, focusing on addressing co-channel interference, a prevalent issue due to the frequency reuse of sidelink in the underlay in-band D2D communications. In contrast to previous studies that either neglect interference or consider it only at the user, our research investigates a performance analysis in terms of outage probability (OP) for RIS-assisted D2D communication systems considering the presence of interference at both the user and the RIS. More specifically, we introduce a novel integral-form expression for an exact analysis of OP. Additionally, we present a new accurate approximation expression for OP, using the gamma distributions to approximate the fading of both desired and interference links, thereby yielding a closed-form expression. Nevertheless, both derived expressions, i.e., the exact integral-form and the approximate closed-form, contain special functions, such as Meijer's G-function and the parabolic cylinder function, which complicate real-time OP analysis. To circumvent this, we employ a deep neural network (DNN) for real-time OP prediction, trained with data generated by the exact expression. Moreover, we present a tight upper bound that quantifies the impact of interference on achievable diversity order and coding gain. We validate the derived expressions through Monte Carlo simulations. Our analysis reveals that while interference does not affect the system's diversity order, it significantly degrades the performance by reducing the coding gain. The results further demonstrate that increasing the number of RIS's reflecting elements is an effective strategy to mitigate the adverse effects of the interference on the system performance.
A Physical Layer Security Framework for Integrated Sensing and Semantic Communication Systems
Oct 08, 2024


Abstract:In this paper, we address a physical layer security (PLS) framework for the integrated sensing and semantic communication (ISASC) system, where a multi-antenna dual-function semantic base station serves multiple single-antenna semantic communication users (SCUs) and monitors a malicious sensing target (MST), in the presence of a single-antenna eavesdropper (EVE), with both the MST and EVE aiming to wiretap information from the SCUs' signals. To enhance PLS, we employ joint artificial noise (AN) and dedicated sensing signal (DSS) in addition to wiretap coding. To evaluate the sensing accuracy, we derive the Cramer-Rao bound (CRB) as a function of the communication, sensing, and AN beamforming (BF) vectors. Subsequently, to assess the PLS level of the ISASC system, we determine a closed-form expression for the semantic secrecy rate (SSR). To achieve an optimal trade-off region between these two competing objectives, we formulate a multi-objective optimization problem for the joint design of the BF vectors. We apply semi-definite programming, Gaussian randomization method, and golden-section search techniques to address this problem. Simulation results demonstrate that the proposed scheme outperforms baseline schemes, achieving a superior trade-off between SSR and CRB.
Optical ISAC: Fundamental Performance Limits and Transceiver Design
Aug 22, 2024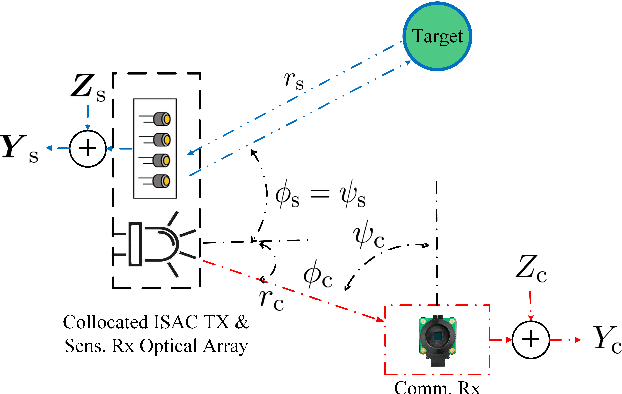
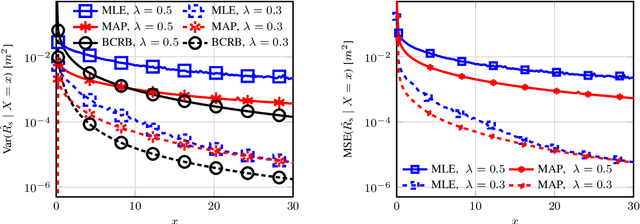
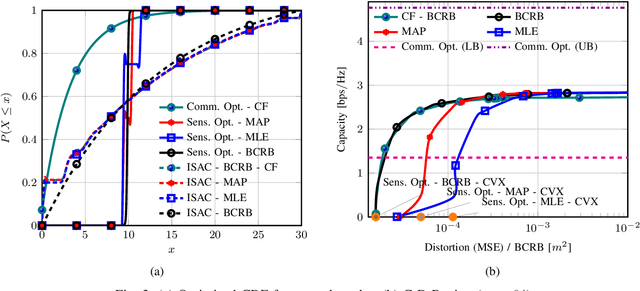
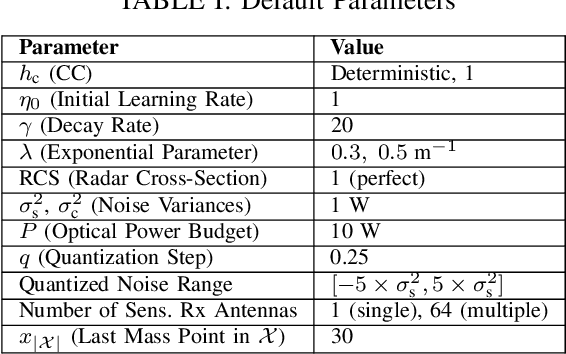
Abstract:This paper characterizes the optimal capacity-distortion (C-D) tradeoff in an optical point-to-point (P2P) system with single-input single-output for communication and single-input multiple-output for sensing (SISO-COM and SIMO-SEN) within an integrated sensing and communication (ISAC) framework. We consider the optimal rate-distortion (R-D) region and explore several inner (IB) and outer (OB) bounds. We introduce practical, asymptotically optimal maximum a posteriori (MAP) and maximum likelihood estimators (MLE) for target distance, addressing nonlinear measurement-to-state relationships and non-conjugate priors. As the number of sensing antennas increases, these estimators converge to the Bayesian Cram\'er-Rao bound (BCRB). We also establish that the achievable rate-CRB (AR-CRB) serves as an OB for the optimal C-D region, valid for both unbiased estimators and asymptotically large numbers of receive antennas. To clarify that the input distribution determines the tradeoff across the Pareto boundary of the C-D region, we propose two algorithms: \textit{i}) an iterative Blahut-Arimoto algorithm (BAA)-type method, and \textit{ii}) a memory-efficient closed-form (CF) approach. The CF approach includes a CF optimal distribution for high optical signal-to-noise ratio (O-SNR) conditions. Additionally, we adapt and refine the Deterministic-Random Tradeoff (DRT) to this optical ISAC context.
A Novel Stochastic Model for IRS-Assisted Communication Systems Based on the Sum-Product of Nakagami-$m$ Random Variables
Jan 18, 2024



Abstract:This paper presents exact formulas for the probability distribution function (PDF) and moment generating function (MGF) of the sum-product of statistically independent but not necessarily identically distributed (i.n.i.d.) Nakagami-$m$ random variables (RVs) in terms of Meijer's G-function. Additionally, exact series representations are also derived for the sum of double-Nakagami RVs, providing useful insights on the trade-off between accuracy and computational cost. Simple asymptotic analytical expressions are provided to gain further insight into the derived formula, and the achievable diversity order is obtained. The suggested statistical properties are proved to be a highly useful tool for modeling parallel cascaded Nakagami-$m$ fading channels. The application of these new results is illustrated by deriving exact expressions and simple tight upper bounds for the outage probability (OP) and average symbol error rate (ASER) of several binary and multilevel modulation signals in intelligent reflecting surfaces (IRSs)-assisted communication systems operating over Nakagami-$m$ fading channels. It is demonstrated that the new asymptotic expression is highly accurate and can be extended to encompass a wider range of scenarios. To validate the theoretical frameworks and formulations, Monte-Carlo simulation results are presented. Additionally, supplementary simulations are provided to compare the derived results with two common types of approximations available in the literature, namely the central limit theorem (CLT) and gamma distribution.
Outage Tradeoff Analysis in a Downlink Integrated Sensing and Communication Network
May 24, 2023

Abstract:This paper aims to analyze the stochastic performance of a multiple input multiple output (MIMO) integrated sensing and communication (ISAC) system in a downlink scenario, where a base station (BS) transmits a dual-functional radar-communication (DFRC) signal matrix, serving the purpose of transmitting communication data to the user while simultaneously sensing the angular location of a target. The channel between the BS and the user is modeled as a random channel with Rayleigh fading distribution, and the azimuth angle of the target is assumed to follow a uniform distribution. We use a maximum ratio transmission (MRT) beamformer to share resource between sensing and communication (S \& C) and observe the trade-off between them. We derive the approximate probability density function (PDF) of the signal-to-noise ratio (SNR) for both the user and the target. Subsequently, leveraging the obtained PDF, we derive the expressions for the user's rate outage probability (OP), as well as the OP for the Cramer-Rao lower bound (CRLB) of the angle of arrival (AOA). In our numerical results, we demonstrate the trade-off between S \& C, confirmed with simulations.
IRS-User Association in IRS-Aided MISO Wireless Networks: Convex Optimization and Machine Learning Approaches
Oct 29, 2022



Abstract:This paper concentrates on the problem of associating an intelligent reflecting surface (IRS) to multiple users in a multiple-input single-output (MISO) downlink wireless communication network. The main objective of the paper is to maximize the sum-rate of all users by solving the joint optimization problem of the IRS-user association, IRS reflection, and BS beamforming, formulated as a non-convex mixed-integer optimization problem. The variable separation and relaxation are used to transform the problem into three convex sub-problems, which are alternatively solved through the convex optimization (CO) method. The major drawback of the proposed CO-based algorithm is high computational complexity. Thus, we make use of machine learning (ML) to tackle this problem. To this end, first, we convert the optimization problem into a regression problem. Then, we solve it with feed-forward neural networks (FNNs), trained by CO-based generated data. Simulation results show that the proposed ML-based algorithm has a performance equivalent to the CO-based algorithm, but with less computation complexity due to its offline training procedure.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge