Laura Crosara
Hybrid Channel- and Coding-Based Challenge-Response Physical-Layer Authentication
Jan 29, 2025


Abstract:This letter proposes a new physical layer authentication mechanism operating at the physical layer of a communication system where the receiver has partial control of the channel conditions (e.g., using an intelligent reflecting surface). We aim to exploit both instantaneous channel state information (CSI) and a secret shared key for authentication. This is achieved by both transmitting an identifying key by wiretap coding (to conceal the key from the attacker) and checking that the instantaneous CSI corresponds to the channel configuration randomly selected by the receiver. We investigate the trade-off between the pilot signals used for CSI estimation and the coding rate (or key length) to improve the overall security of the authentication procedure.
Performance Limits for Signals of Opportunity-Based Navigation
Jul 23, 2024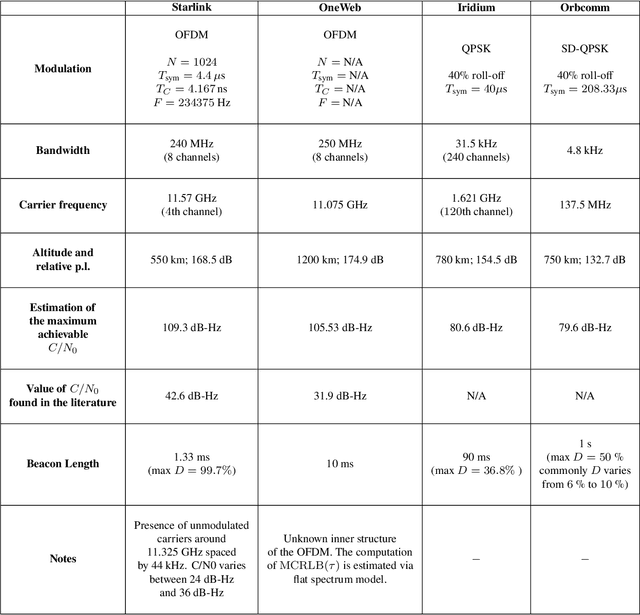
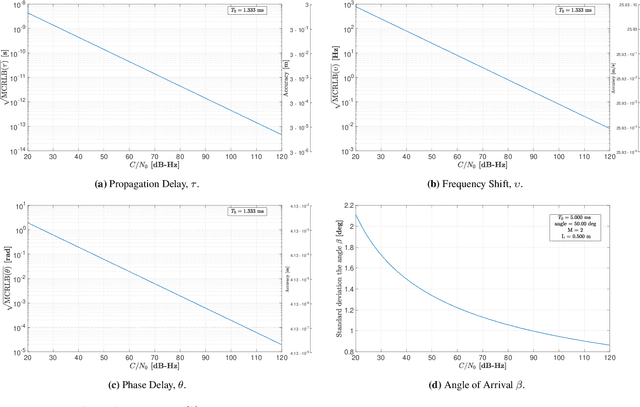
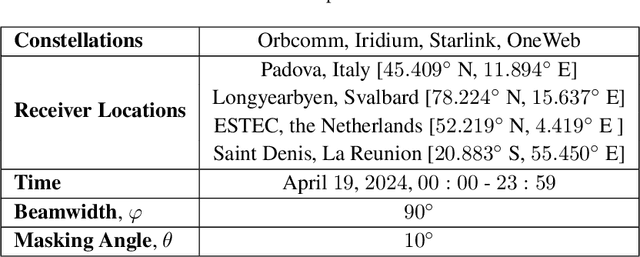
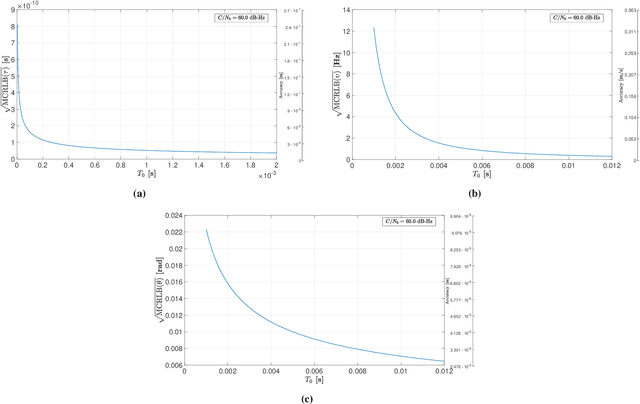
Abstract:This paper investigates the potential of non-terrestrial and terrestrial signals of opportunity (SOOP) for navigation applications. Non-terrestrial SOOP analysis employs modified Cram\`er-Rao lower bound (MCRLB) to establish a relationship between SOOP characteristics and the accuracy of ranging information. This approach evaluates hybrid navigation module performance without direct signal simulation. The MCRLB is computed for ranging accuracy, considering factors like propagation delay, frequency offset, phase offset, and angle-of-arrival (AOA), across diverse non-terrestrial SOOP candidates. Additionally, Geometric Dilution of Precision (GDOP) and low earth orbit (LEO) SOOP availability are assessed. Validation involves comparing MCRLB predictions with actual ranging measurements obtained in a realistic simulated scenario. Furthermore, a qualitative evaluation examines terrestrial SOOP, considering signal availability, accuracy attainability, and infrastructure demands.
On the Limits of Cross-Authentication Checks for GNSS Signals
Apr 06, 2023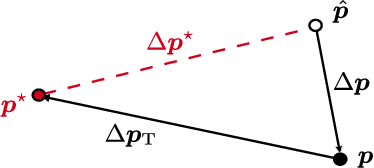
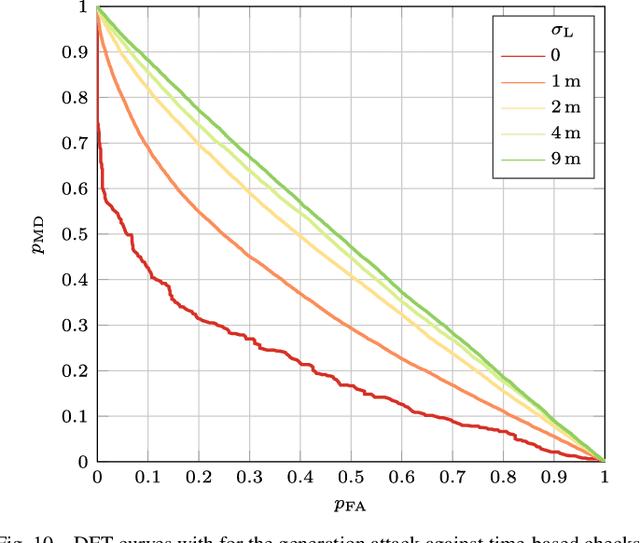
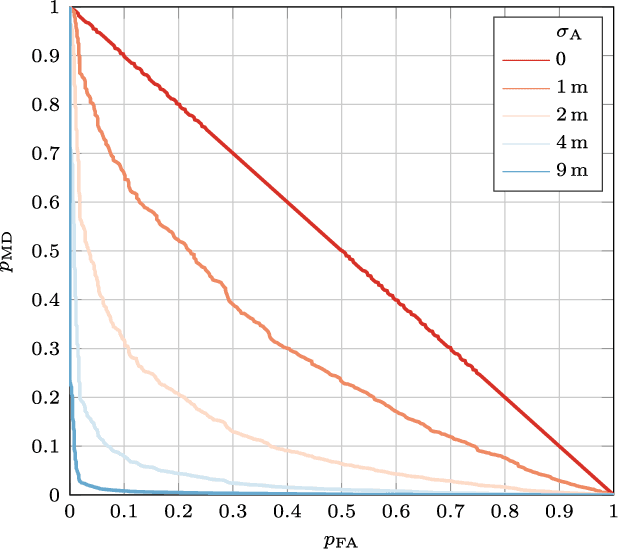
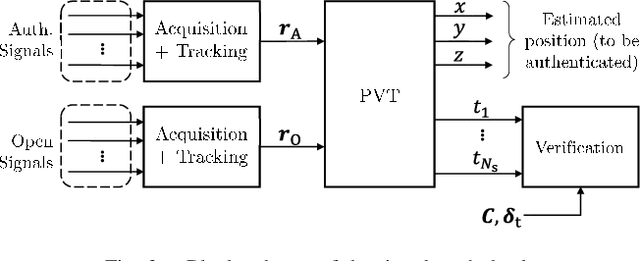
Abstract:Global navigation satellite systems (GNSSs) are implementing security mechanisms: examples are Galileo open service navigation message authentication (OS-NMA) and GPS chips-message robust authentication (CHIMERA). Each of these mechanisms operates in a single band. However, nowadays, even commercial GNSS receivers typically compute the position, velocity, and time (PVT) solution using multiple constellations and signals from multiple bands at once, significantly improving both accuracy and availability. Hence, cross-authentication checks have been proposed, based on the PVT obtained from the mixture of authenticated and non-authenticated signals. In this paper, first, we formalize the models for the cross-authentication checks. Next, we describe, for each check, a spoofing attack to generate a fake signal leading the victim to a target PVT without notice. We analytically relate the degrees of the freedom of the attacker in manipulating the victim's solution to both the employed security checks and the number of open signals that can be tampered with by the attacker. We test the performance of the considered attack strategies on an experimental dataset. Lastly, we show the limits of the PVT-based GNSS cross-authentication checks, where both authenticated and non-authenticated signals are used.
On the Optimal Spoofing Attack and Countermeasure in Satellite Navigation Systems
Feb 03, 2023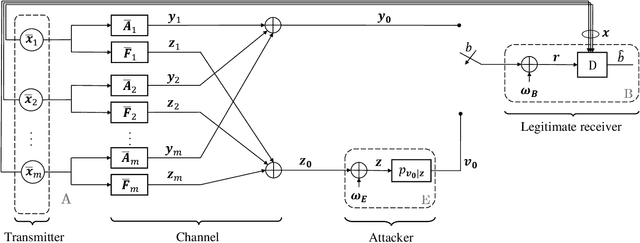
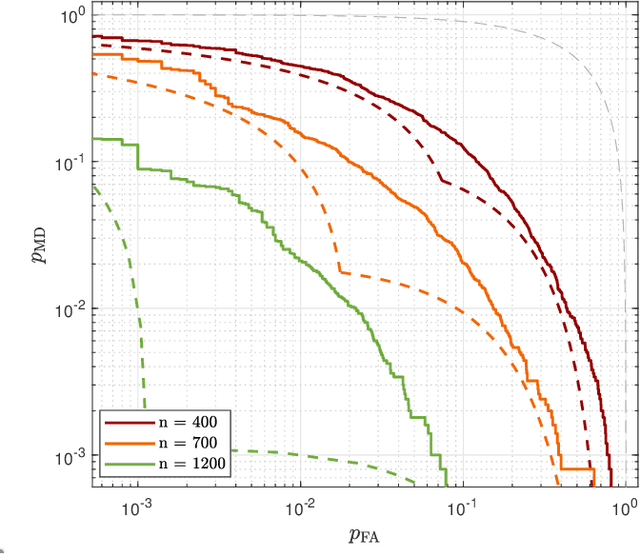
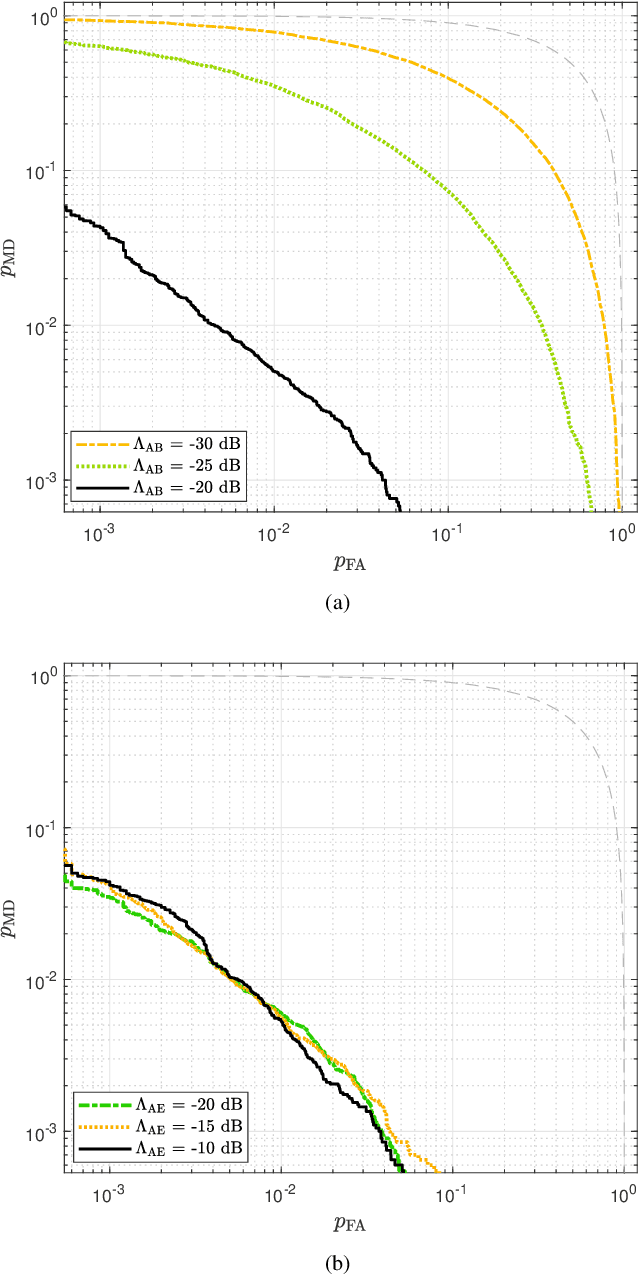
Abstract:The threat of signal spoofing attacks against GNSS has grown in recent years and has motivated the study of anti-spoofing techniques. However, defense methods have been designed only against specific attacks. This paper introduces a general model of the spoofing attack framework in GNSS, from which optimal attack and defense strategies are derived. We consider a scenario with a legitimate receiver (Bob) testing if the received signals come from multiple legitimate space vehicles (Alice) or from an attack device (Eve). We first derive the optimal attack strategy against a Gaussian transmission from Alice, by minimizing an outer bound on the achievable error probability region of the spoofing detection test. Then, framing the spoofing and its detection as an adversarial game, we show that the Gaussian transmission and the corresponding optimal attack constitute a Nash equilibrium. Lastly, we consider the case of practical modulation schemes for Alice and derive the generalized likelihood ratio test. Numerical results validate the analytical derivations and show that the bound on the achievable error region is representative of the actual performance.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge