Francesco Ardizzon
Physical Layer-Based Device Fingerprinting for Wireless Security: From Theory to Practice
Jun 11, 2025Abstract:The identification of the devices from which a message is received is part of security mechanisms to ensure authentication in wireless communications. Conventional authentication approaches are cryptography-based, which, however, are usually computationally expensive and not adequate in the Internet of Things (IoT), where devices tend to be low-cost and with limited resources. This paper provides a comprehensive survey of physical layer-based device fingerprinting, which is an emerging device authentication for wireless security. In particular, this article focuses on hardware impairment-based identity authentication and channel features-based authentication. They are passive techniques that are readily applicable to legacy IoT devices. Their intrinsic hardware and channel features, algorithm design methodologies, application scenarios, and key research questions are extensively reviewed here. The remaining research challenges are discussed, and future work is suggested that can further enhance the physical layer-based device fingerprinting.
Crystal Oscillators in OSNMA-Enabled Receivers: An Implementation View for Automotive Applications
Jan 25, 2025Abstract:To ensure the authenticity of navigation data, Galileo Open Service navigation message authentication (OSNMA) requires loose synchronization between the receiver clock and the system time. This means that during the period between clock calibrations, the receiver clock error needs to be smaller than a pre-defined threshold, currently up to 165s for OSNMA. On the other hand, relying on the PVT solution to steer the receiver clock or correct its bias may not be possible since this would depend on the very same signals we intend to authenticate. This work aims to investigate the causes of the frequency accuracy loss leading to clock errors and to build a model that, from the datasheet of a real-time clock (RTC) device, allows to bound the error clock during a certain period. The model's main contributors are temperature changes, long-term aging, and offset at calibration, but it includes other factors. We then apply the model to several RTCs from different manufacturers and bound the maximum error for certain periods, with a focus on the two-year between-calibration period expected for the smart tachograph, an automotive application that will integrate OSNMA.
Authentication by Location Tracking in Underwater Acoustic Networks
Oct 04, 2024



Abstract:Physical layer message authentication in underwater acoustic networks (UWANs) leverages the characteristics of the underwater acoustic channel (UWAC) as a fingerprint of the transmitting device. However, as the device moves its UWAC changes, and the authentication mechanism must track such variations. In this paper, we propose a context-based authentication mechanism operating in two steps: first, we estimate the position of the underwater device, then we predict its future position based on the previously estimated ones. To check the authenticity of the transmission, we compare the estimated and the predicted position. The location is estimated using a convolutional neural network taking as input the sample covariance matrix of the estimated UWACs. The prediction uses either a Kalman filter or a recurrent neural network (RNN). The authentication check is performed on the squared error between the predicted and estimated positions. The solution based on the Kalman filter outperforms that built on the RNN when the device moves according to a correlated Gauss-Markov mobility model, which reproduces a typical underwater motion.
Challenge-Response to Authenticate Drone Communications: A Game Theoretic Approach
Oct 01, 2024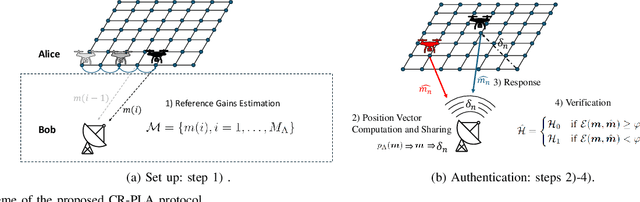
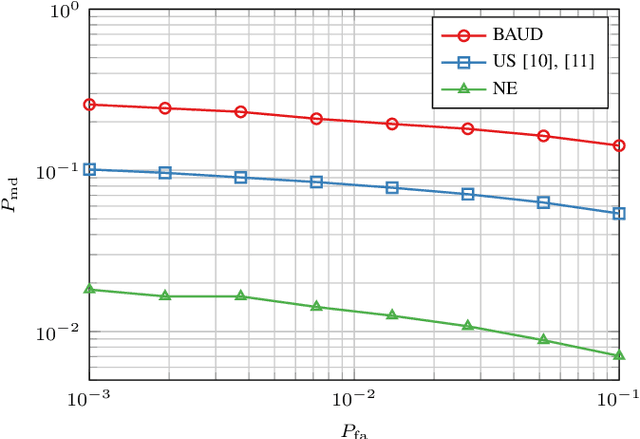
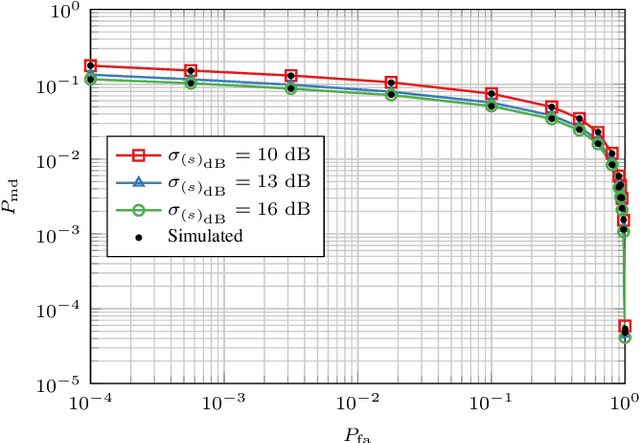
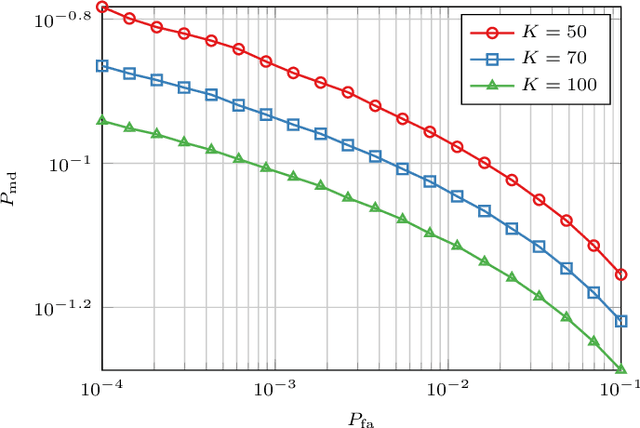
Abstract:In this paper, we propose a novel strategy for physical layer authentications based on the challenge-response concept for a transmitting drone (Alice). In a preliminary training phase, Alice moves over several positions, and Bob (either a drone or a ground device) estimates the Alice-Bob channel gains. Then Alice transmits its message from different random positions (challenge) and Bob, upon receiving the messages, authenticates the sender via a log-likelihood test on the estimated channel gains (response). In turn, the intruder Trudy selects random positions on which she transmits messages on behalf of Alice to Bob. In this paper, we design the probability mass distribution of Alice's challenge positions and the Trudy response positions by modeling the problem as a zero-sum game between Bob and Trudy, where the payoff of Trudy is the missed detection probability. Moreover, we propose three different approaches that minimize the energy spent by Alice without sacrificing security, which differ in computational complexity and resulting energy consumption. Finally, we test the proposed technique via numerical simulations, which include a realistic model of both Alice-Bob and Trudy-Bob fading channels, affected by shadowing.
Performance Limits for Signals of Opportunity-Based Navigation
Jul 23, 2024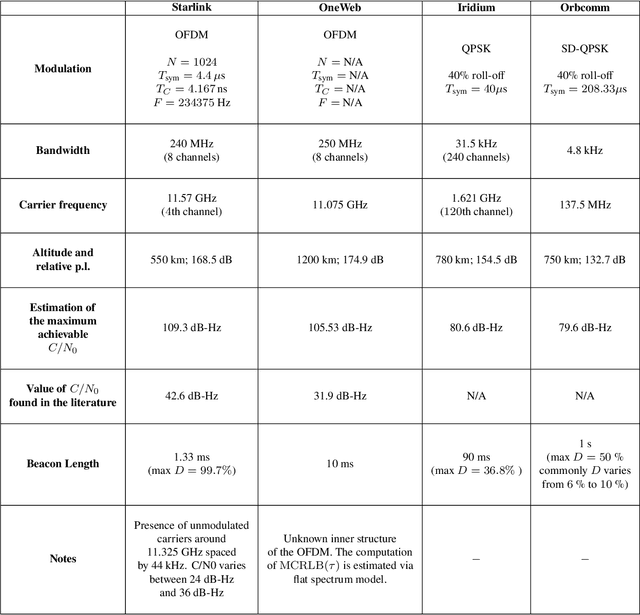
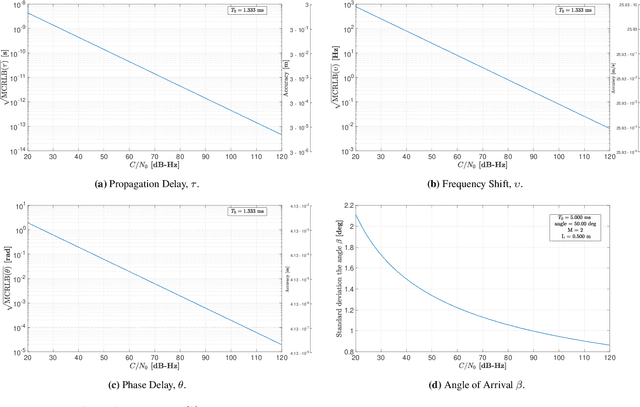
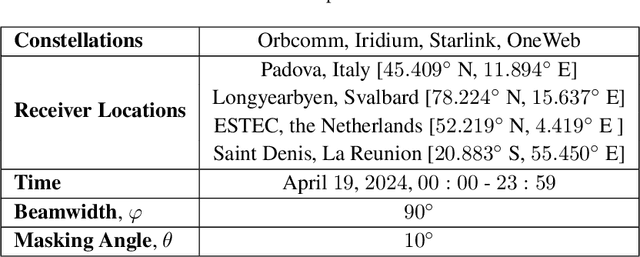
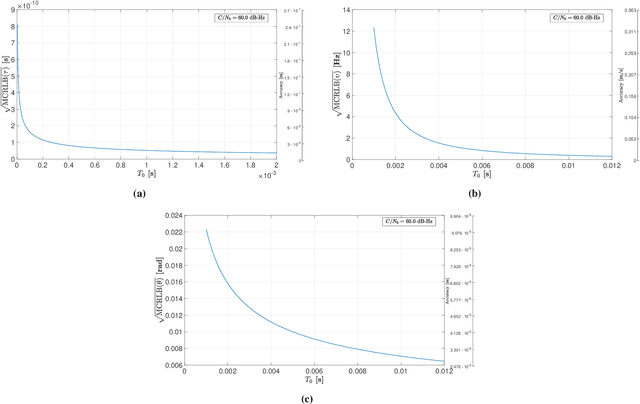
Abstract:This paper investigates the potential of non-terrestrial and terrestrial signals of opportunity (SOOP) for navigation applications. Non-terrestrial SOOP analysis employs modified Cram\`er-Rao lower bound (MCRLB) to establish a relationship between SOOP characteristics and the accuracy of ranging information. This approach evaluates hybrid navigation module performance without direct signal simulation. The MCRLB is computed for ranging accuracy, considering factors like propagation delay, frequency offset, phase offset, and angle-of-arrival (AOA), across diverse non-terrestrial SOOP candidates. Additionally, Geometric Dilution of Precision (GDOP) and low earth orbit (LEO) SOOP availability are assessed. Validation involves comparing MCRLB predictions with actual ranging measurements obtained in a realistic simulated scenario. Furthermore, a qualitative evaluation examines terrestrial SOOP, considering signal availability, accuracy attainability, and infrastructure demands.
One-Class Classification as GLRT for Jamming Detection in Private 5G Networks
May 07, 2024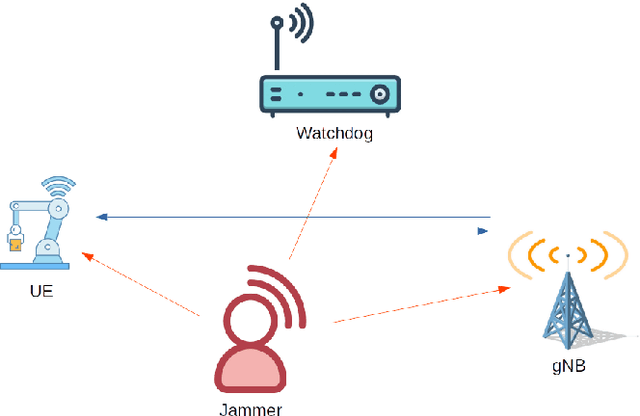
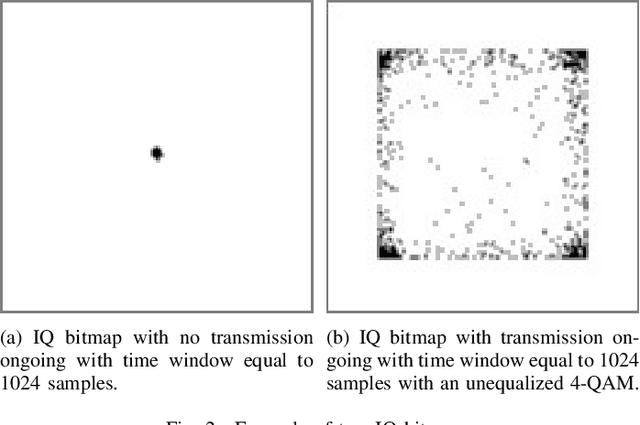
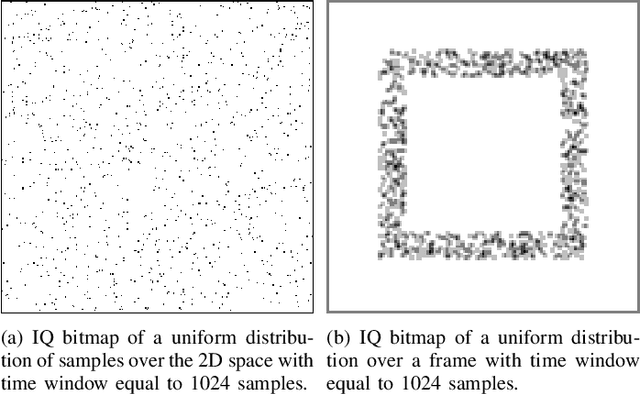
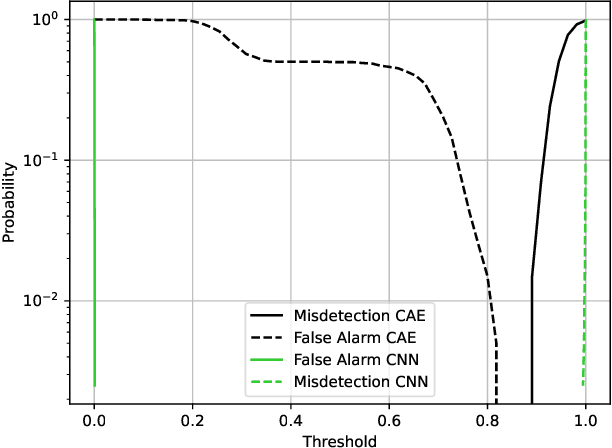
Abstract:5G mobile networks are vulnerable to jamming attacks that may jeopardize valuable applications such as industry automation. In this paper, we propose to analyze radio signals with a dedicated device to detect jamming attacks. We pursue a learning approach, with the detector being a CNN implementing a GLRT. To this end, the CNN is trained as a two-class classifier using two datasets: one of real legitimate signals and another generated artificially so that the resulting classifier implements the GLRT. The artificial dataset is generated mimicking different types of jamming signals. We evaluate the performance of this detector using experimental data obtained from a private 5G network and several jamming signals, showing the technique's effectiveness in detecting the attacks.
Energy-Based Optimization of Physical-Layer Challenge-Response Authentication with Drones
May 06, 2024



Abstract:Drones are expected to be used for many tasks in the future and require secure communication protocols. In this work, we propose a novel physical layer authentication (PLA)-based challenge-response (CR) protocol in which a drone Bob authenticates the sender (either on the ground or air) by exploiting his prior knowledge of the wireless channel statistic (fading, path loss, and shadowing). In particular, Bob will move to a set of positions in the space, and by estimating the attenuations of the received signals he will authenticate the sender. We take into account the energy consumption in the design and provide three solutions: a purely greedy solution (PG), an optimal Bellman iterative solution (BI), and a heuristic solution based on the evaluation of the standard deviation of the attenuations in the space. Finally, we demonstrate the effectiveness of our approach through numerical simulations.
Secret-Key-Agreement Advantage Distillation With Quantization Correction
Apr 20, 2023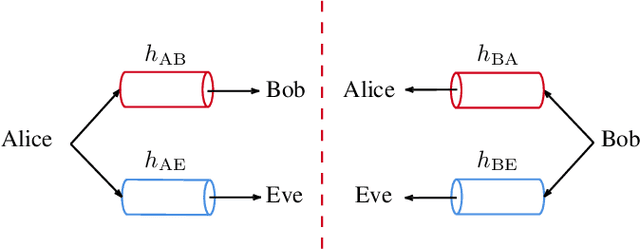
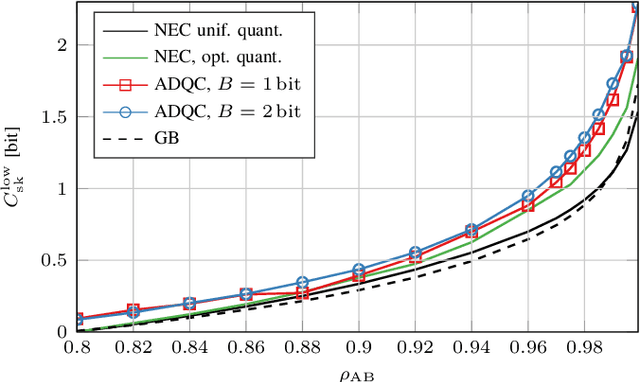
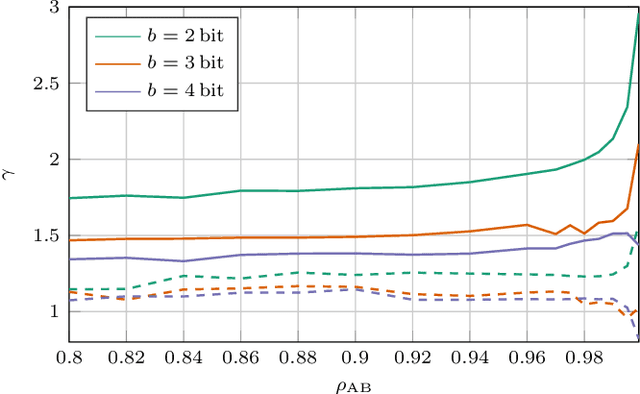
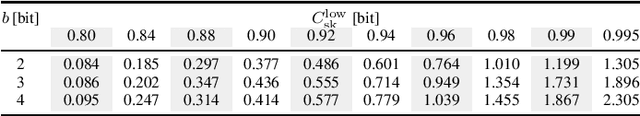
Abstract:We propose a novel advantage distillation strategy for physical layer-based secret-key-agreement (SKA). We consider a scenario where Alice and Bob aim at extracting a common bit sequence, which should remain secret to Eve, by quantizing a random number obtained from measurements at their communication channel. We propose an asymmetric advantage distillation protocol with two novel features: i) Alice quantizes her measurement and sends partial information on it over an authenticated public side channel, and ii) Bob quantizes his measurement by exploiting the partial information. The partial information on the position of the measurement in the quantization interval and its sharing allows Bob to obtain a quantized value closer to that of Alice. Both strategies increase the lower bound of the secret key rate.
On the Limits of Cross-Authentication Checks for GNSS Signals
Apr 06, 2023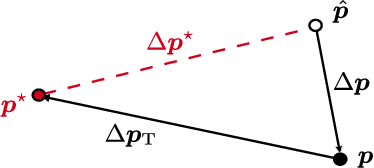
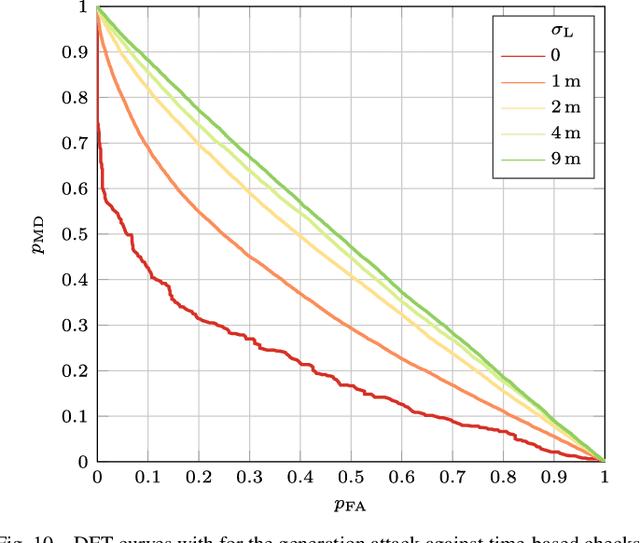
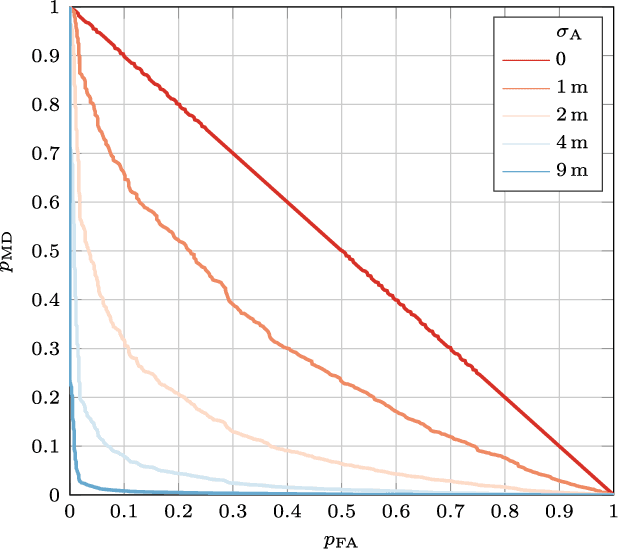
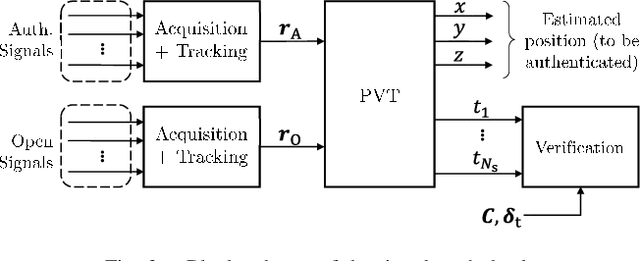
Abstract:Global navigation satellite systems (GNSSs) are implementing security mechanisms: examples are Galileo open service navigation message authentication (OS-NMA) and GPS chips-message robust authentication (CHIMERA). Each of these mechanisms operates in a single band. However, nowadays, even commercial GNSS receivers typically compute the position, velocity, and time (PVT) solution using multiple constellations and signals from multiple bands at once, significantly improving both accuracy and availability. Hence, cross-authentication checks have been proposed, based on the PVT obtained from the mixture of authenticated and non-authenticated signals. In this paper, first, we formalize the models for the cross-authentication checks. Next, we describe, for each check, a spoofing attack to generate a fake signal leading the victim to a target PVT without notice. We analytically relate the degrees of the freedom of the attacker in manipulating the victim's solution to both the employed security checks and the number of open signals that can be tampered with by the attacker. We test the performance of the considered attack strategies on an experimental dataset. Lastly, we show the limits of the PVT-based GNSS cross-authentication checks, where both authenticated and non-authenticated signals are used.
On the Optimal Spoofing Attack and Countermeasure in Satellite Navigation Systems
Feb 03, 2023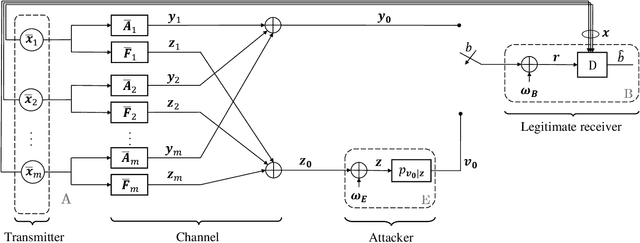
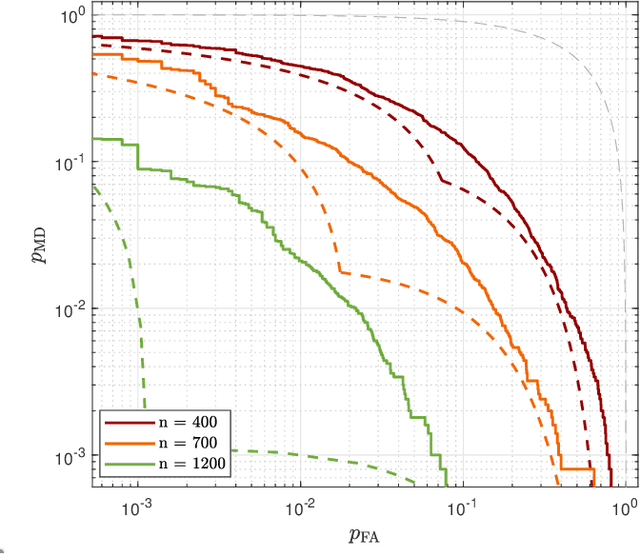
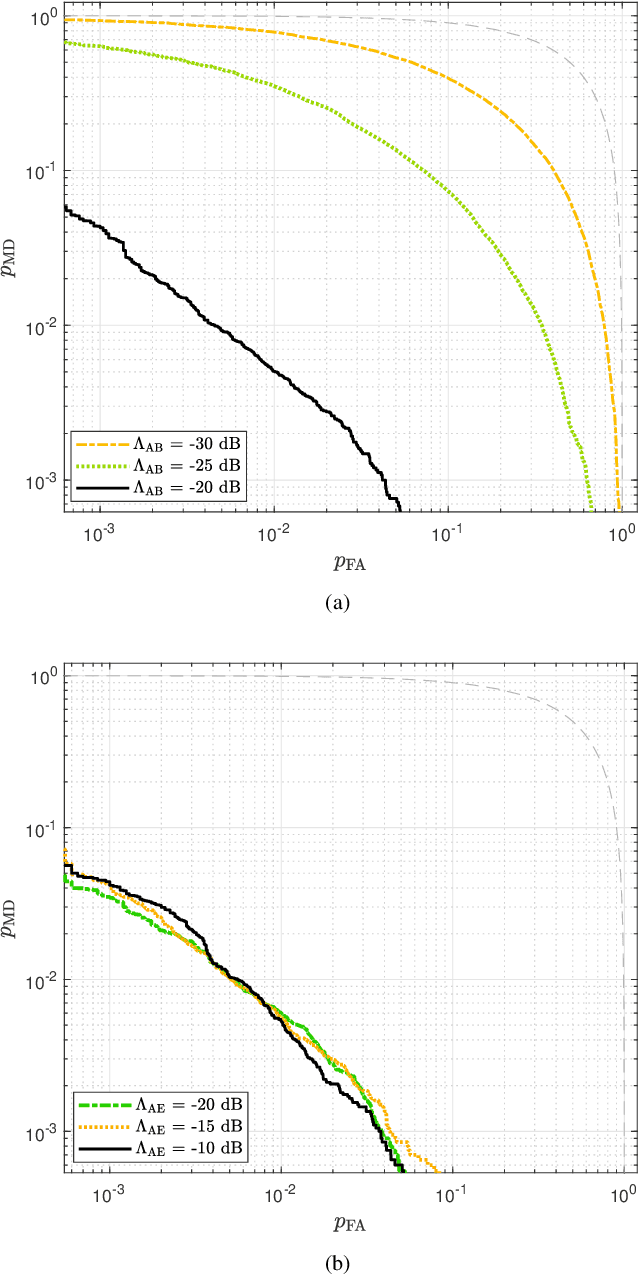
Abstract:The threat of signal spoofing attacks against GNSS has grown in recent years and has motivated the study of anti-spoofing techniques. However, defense methods have been designed only against specific attacks. This paper introduces a general model of the spoofing attack framework in GNSS, from which optimal attack and defense strategies are derived. We consider a scenario with a legitimate receiver (Bob) testing if the received signals come from multiple legitimate space vehicles (Alice) or from an attack device (Eve). We first derive the optimal attack strategy against a Gaussian transmission from Alice, by minimizing an outer bound on the achievable error probability region of the spoofing detection test. Then, framing the spoofing and its detection as an adversarial game, we show that the Gaussian transmission and the corresponding optimal attack constitute a Nash equilibrium. Lastly, we consider the case of practical modulation schemes for Alice and derive the generalized likelihood ratio test. Numerical results validate the analytical derivations and show that the bound on the achievable error region is representative of the actual performance.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge