Mattia Piana
Physical Layer-Based Device Fingerprinting for Wireless Security: From Theory to Practice
Jun 11, 2025Abstract:The identification of the devices from which a message is received is part of security mechanisms to ensure authentication in wireless communications. Conventional authentication approaches are cryptography-based, which, however, are usually computationally expensive and not adequate in the Internet of Things (IoT), where devices tend to be low-cost and with limited resources. This paper provides a comprehensive survey of physical layer-based device fingerprinting, which is an emerging device authentication for wireless security. In particular, this article focuses on hardware impairment-based identity authentication and channel features-based authentication. They are passive techniques that are readily applicable to legacy IoT devices. Their intrinsic hardware and channel features, algorithm design methodologies, application scenarios, and key research questions are extensively reviewed here. The remaining research challenges are discussed, and future work is suggested that can further enhance the physical layer-based device fingerprinting.
Challenge-Response to Authenticate Drone Communications: A Game Theoretic Approach
Oct 01, 2024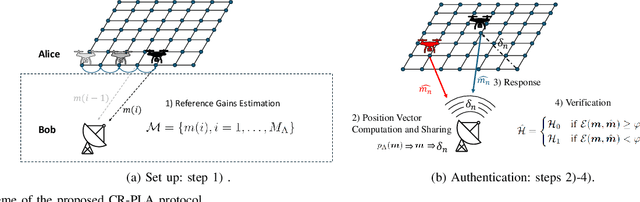
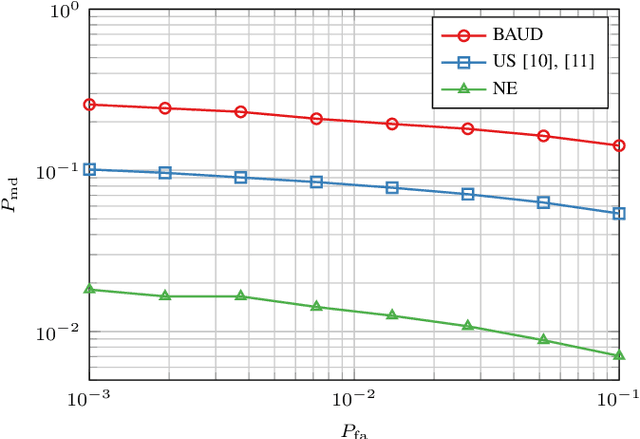
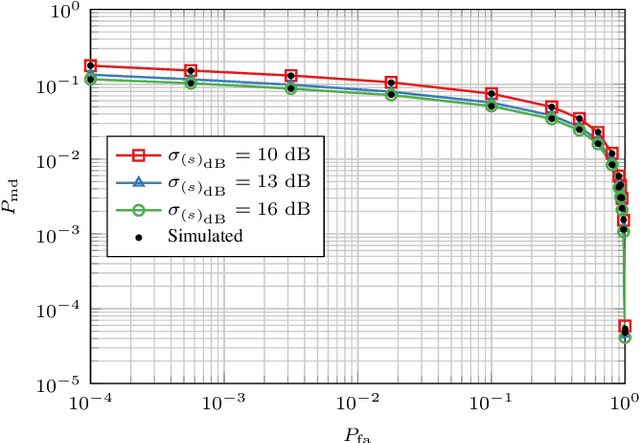
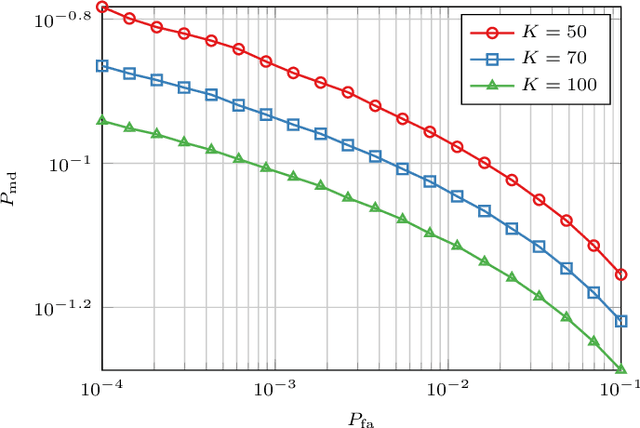
Abstract:In this paper, we propose a novel strategy for physical layer authentications based on the challenge-response concept for a transmitting drone (Alice). In a preliminary training phase, Alice moves over several positions, and Bob (either a drone or a ground device) estimates the Alice-Bob channel gains. Then Alice transmits its message from different random positions (challenge) and Bob, upon receiving the messages, authenticates the sender via a log-likelihood test on the estimated channel gains (response). In turn, the intruder Trudy selects random positions on which she transmits messages on behalf of Alice to Bob. In this paper, we design the probability mass distribution of Alice's challenge positions and the Trudy response positions by modeling the problem as a zero-sum game between Bob and Trudy, where the payoff of Trudy is the missed detection probability. Moreover, we propose three different approaches that minimize the energy spent by Alice without sacrificing security, which differ in computational complexity and resulting energy consumption. Finally, we test the proposed technique via numerical simulations, which include a realistic model of both Alice-Bob and Trudy-Bob fading channels, affected by shadowing.
Energy-Based Optimization of Physical-Layer Challenge-Response Authentication with Drones
May 06, 2024



Abstract:Drones are expected to be used for many tasks in the future and require secure communication protocols. In this work, we propose a novel physical layer authentication (PLA)-based challenge-response (CR) protocol in which a drone Bob authenticates the sender (either on the ground or air) by exploiting his prior knowledge of the wireless channel statistic (fading, path loss, and shadowing). In particular, Bob will move to a set of positions in the space, and by estimating the attenuations of the received signals he will authenticate the sender. We take into account the energy consumption in the design and provide three solutions: a purely greedy solution (PG), an optimal Bellman iterative solution (BI), and a heuristic solution based on the evaluation of the standard deviation of the attenuations in the space. Finally, we demonstrate the effectiveness of our approach through numerical simulations.
User Localization with HRIS and Backscatter Modulation for Next-Generation Networks
Mar 01, 2024



Abstract:Hybrid reflective intelligent surfaces (HRISs) can support localization in sixth-generation (6G) networks thanks to their ability to generate narrow beams and at the same time receive and process locally the impinging signals. In this paper, we propose a novel protocol for user localization in a network with an HRIS. The protocol includes two steps. In the first step, the HRIS operates in full absorption mode and the user equipment (UE) transmits a signal that is locally processed at the HRIS to estimate the angle of arrival (AoA). In the second step, the base station transmits a downlink reference signal to the UE, and the HRIS superimposes a message by a backscatter modulation. The message contains information on the previously estimated AoA. Lastly, the UE, knowing the position of the HRIS, estimates the time of flight (ToF) from the signal of the second step and demodulates the information on the AoA to obtain an estimate of its location. Numerical results confirm the effectiveness of the proposed solution, also in comparison with the Cram\'er Rao lower bound on the estimated quantities.nd on the estimated quantities.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge