Rongke Liu
A Unified NOMA Framework in Beam-Hopping Satellite Communication Systems
Jan 17, 2024



Abstract:This paper investigates the application of a unified non-orthogonal multiple access framework in beam hopping (U-NOMA-BH) based satellite communication systems. More specifically, the proposed U-NOMA-BH framework can be applied to code-domain NOMA based BH (CD-NOMA-BH) and power-domain NOMA based BH (PD-NOMA-BH) systems. To satisfy dynamic-uneven traffic demands, we formulate the optimization problem to minimize the square of discrete difference by jointly optimizing power allocation, carrier assignment and beam scheduling. The non-convexity of the objective function and the constraint condition is solved through Dinkelbach's transform and variable relaxation. As a further development, the closed-from and asymptotic expressions of outage probability are derived for CD/PD-NOMA-BH systems. Based on approximated results, the diversity orders of a pair of users are obtained in detail. In addition, the system throughput of U-NOMA-BH is discussed in delay-limited transmission mode. Numerical results verify that: i) The gap between traffic requests of CD/PD-NOMA-BH systems appears to be more closely compared with orthogonal multiple access based BH (OMA-BH); ii) The CD-NOMA-BH system is capable of providing the enhanced traffic request and capacity provision; and iii) The outage behaviors of CD/PD-NOMA-BH are better than that of OMA-BH.
Unstoppable Attack: Label-Only Model Inversion via Conditional Diffusion Model
Jul 18, 2023Abstract:Model inversion attacks (MIAs) are aimed at recovering private data from a target model's training set, which poses a threat to the privacy of deep learning models. MIAs primarily focus on the white-box scenario where the attacker has full access to the structure and parameters of the target model. However, practical applications are black-box, it is not easy for adversaries to obtain model-related parameters, and various models only output predicted labels. Existing black-box MIAs primarily focused on designing the optimization strategy, and the generative model is only migrated from the GAN used in white-box MIA. Our research is the pioneering study of feasible attack models in label-only black-box scenarios, to the best of our knowledge. In this paper, we develop a novel method of MIA using the conditional diffusion model to recover the precise sample of the target without any extra optimization, as long as the target model outputs the label. Two primary techniques are introduced to execute the attack. Firstly, select an auxiliary dataset that is relevant to the target model task, and the labels predicted by the target model are used as conditions to guide the training process. Secondly, target labels and random standard normally distributed noise are input into the trained conditional diffusion model, generating target samples with pre-defined guidance strength. We then filter out the most robust and representative samples. Furthermore, we propose for the first time to use Learned Perceptual Image Patch Similarity (LPIPS) as one of the evaluation metrics for MIA, with systematic quantitative and qualitative evaluation in terms of attack accuracy, realism, and similarity. Experimental results show that this method can generate similar and accurate data to the target without optimization and outperforms generators of previous approaches in the label-only scenario.
Flexible Hybrid Beamforming for Spectrally Efficient 6G Joint Radar-Communications
Nov 15, 2022



Abstract:Joint radar-communications (JRC) benefits from multi-functionality of radar and communication operations using same hardware and radio frequency (RF) spectrum resources. Thus JRC systems possess very high potential to be employed into the sixth generation (6G) standards. This paper designs a flexible beamformer for multiple-input multiple output (MIMO) JRC with maximized spectral efficiency (SE). Hybrid beamforming is implemented which constitutes lesser number of RF chains than number of transmitter antennas. We jointly express JRC rate with communication and radar entities including a weighting factor which depicts the dominance of one operation over the other. The joint-SE based proposed method optimally selects the number of RF chains with flexible hynrid beamforming design. Furthermore, when the communication operation takes place the proposed method takes into account the interference occurring from the radar operation and vice-versa. Fractional programming based selection procedure is used for flexible beamforming and optimal number of RF chains while considering interference of each operation. Simulation results are presented and compared with different baselines to show effectiveness of the proposed flexible hybrid beamforming method.
On Lattice-Code based Multiple Access: Uplink Architecture and Algorithms
Oct 03, 2022
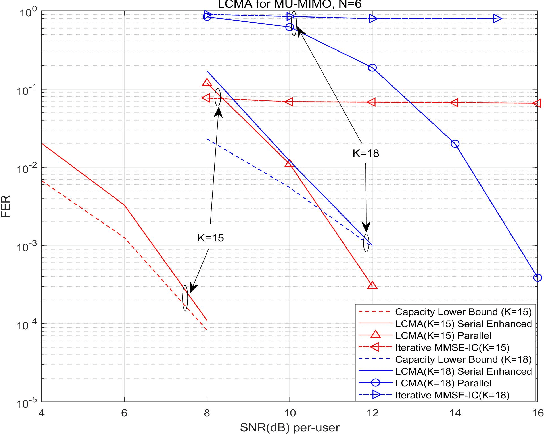

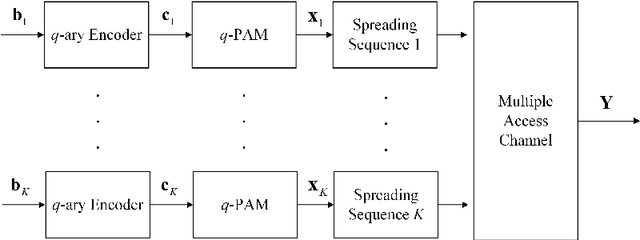
Abstract:This paper studies a lattice-code based multiple-access (LCMA) framework, and develops a package of processing techniques that are essential to its practical implementation. In the uplink, $K$ users encode their messages with the same ring coded modulation of $2^{m}$-PAM signaling. With it, the integer sum of multiple codewords belongs to the $n$-dimension lattice of the base code. Such property enables efficient \textit{algebraic binning} for computing linear combinations of $K$ users' messages. For the receiver, we devise two new algorithms, based on linear physical-layer network coding and linear filtering, to calculate the symbol-wise a posteriori probabilities (APPs) w.r.t. the $K$ streams of linear codeword combinations. The resultant APP streams are forwarded to the $q$-ary belief-propagation decoders, which parallelly compute $K$ streams of linear message combinations. Finally, by multiplying the inverse of the coefficient matrix, all users' messages are recovered. Even with single-stage parallel processing, LCMA is shown to support a remarkably larger number of users and exhibits improved frame error rate (FER) relative to existing NOMA systems such as IDMA and SCMA. Further, we propose a new multi-stage LCMA receiver relying on \emph{generalized matrix inversion}. With it, a near-capacity performance is demonstrated for a wide range of system loads. Numerical results demonstrate that the number of users that LCMA can support is no less than 350\% of the length of the spreading sequence or number of receive antennas. Since LCMA relaxes receiver iteration, off-the-shelf channel codes in standards can be directly utilized, avoiding the compatibility and convergence issue of channel code and detector in IDMA and SCMA.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge