Rohit Arora
Data-driven Multistage Distributionally Robust Linear Optimization with Nested Distance
Jul 23, 2024



Abstract:We study multistage distributionally robust linear optimization, where the uncertainty set is defined as a ball of distribution centered at a scenario tree using the nested distance. The resulting minimax problem is notoriously difficult to solve due to its inherent non-convexity. In this paper, we demonstrate that, under mild conditions, the robust risk evaluation of a given policy can be expressed in an equivalent recursive form. Furthermore, assuming stagewise independence, we derive equivalent dynamic programming reformulations to find an optimal robust policy that is time-consistent and well-defined on unseen sample paths. Our reformulations reconcile two modeling frameworks: the multistage-static formulation (with nested distance) and the multistage-dynamic formulation (with one-period Wasserstein distance). Moreover, we identify tractable cases when the value functions can be computed efficiently using convex optimization techniques.
Detection of Doctored Speech: Towards an End-to-End Parametric Learn-able Filter Approach
Jun 27, 2022



Abstract:The Automatic Speaker Verification systems have potential in biometrics applications for logical control access and authentication. A lot of things happen to be at stake if the ASV system is compromised. The preliminary work presents a comparative analysis of the wavelet and MFCC-based state-of-the-art spoof detection techniques developed in these papers, respectively (Novoselov et al., 2016) (Alam et al., 2016a). The results on ASVspoof 2015 justify our inclination towards wavelet-based features instead of MFCC features. The experiments on the ASVspoof 2019 database show the lack of credibility of the traditional handcrafted features and give us more reason to progress towards using end-to-end deep neural networks and more recent techniques. We use Sincnet architecture as our baseline. We get E2E deep learning models, which we call WSTnet and CWTnet, respectively, by replacing the Sinc layer with the Wavelet Scattering and Continuous wavelet transform layers. The fusion model achieved 62% and 17% relative improvement over traditional handcrafted models and our Sincnet baseline when evaluated on the modern spoofing attacks in ASVspoof 2019. The final scale distribution and the number of scales used in CWTnet are far from optimal for the task at hand. So to solve this problem, we replaced the CWT layer with a Wavelet Deconvolution(WD) (Khan and Yener, 2018) layer in our CWTnet architecture. This layer calculates the Discrete-Continuous Wavelet Transform similar to the CWTnet but also optimizes the scale parameter using back-propagation. The WDnet model achieved 26% and 7% relative improvement over CWTnet and Sincnet models respectively when evaluated over ASVspoof 2019 dataset. This shows that more generalized features are extracted as compared to the features extracted by CWTnet as only the most important and relevant frequency regions are focused upon.
Impact of Channel Variation on One-Class Learning for Spoof Detection
Oct 09, 2021
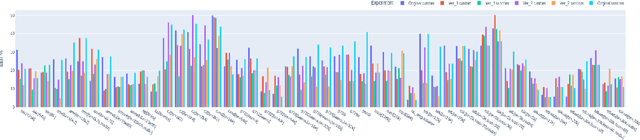
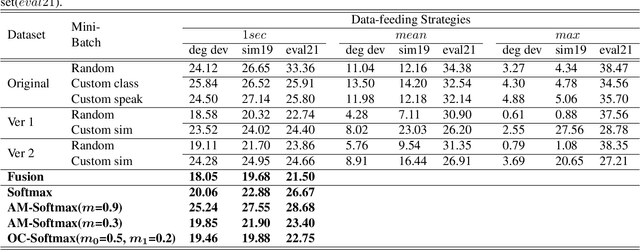
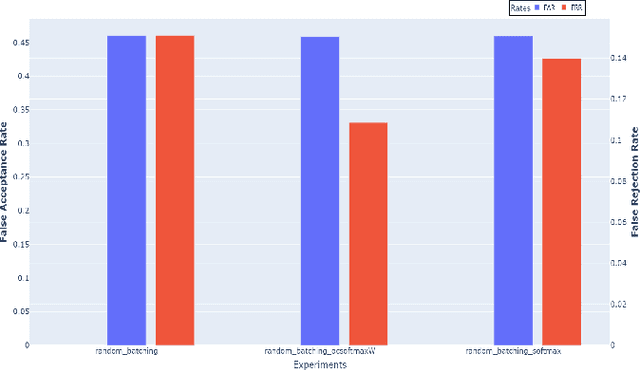
Abstract:The value of Spoofing detection in increasing the reliability of the ASV system is unparalleled. In reality, however, the performance of countermeasure systems (CMs) degrades significantly due to channel variation. Multi-conditional training(MCT) is a well-established technique to handle such scenarios. However, "which data-feeding strategy is optimal for MCT?" is not known in the case of spoof detection. In this paper, various codec simulations were used to modify ASVspoof 2019 dataset, and assessments were done using data-feeding and mini-batching strategies to help address this question. Our experiments aim to test the efficacy of the various margin-based losses for training Resnet based models with LFCC front-end feature extractor to correctly classify the spoofed and bonafide samples degraded using codec simulations. Contrastingly to most of the works that focus mainly on architectures, this study highlights the relevance of the deemed-of-low-importance process of data-feeding and mini-batching to raise awareness of the need to refine it for better performance.
Search-based Path Planning for a High Dimensional Manipulator in Cluttered Environments Using Optimization-based Primitives
Jul 06, 2021



Abstract:In this work we tackle the path planning problem for a 21-dimensional snake robot-like manipulator, navigating a cluttered gas turbine for the purposes of inspection. Heuristic search based approaches are effective planning strategies for common manipulation domains. However, their performance on high dimensional systems is heavily reliant on the effectiveness of the action space and the heuristics chosen. The complex nature of our system, reachability constraints, and highly cluttered turbine environment renders naive choices of action spaces and heuristics ineffective. To this extent we have developed i) a methodology for dynamically generating actions based on online optimization that help the robot navigate narrow spaces, ii) a technique for lazily generating these computationally expensive optimization actions to effectively utilize resources, and iii) heuristics that reason about the homotopy classes induced by the blades of the turbine in the robot workspace and a Multi-Heuristic framework which guides the search along the relevant classes. The impact of our contributions is presented through an experimental study in simulation, where the 21 DOF manipulator navigates towards regions of inspection within a turbine.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge