Min Tao
Minimizing L1 over L2 norms on the gradient
Jan 04, 2021
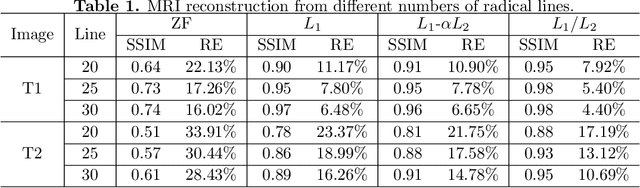
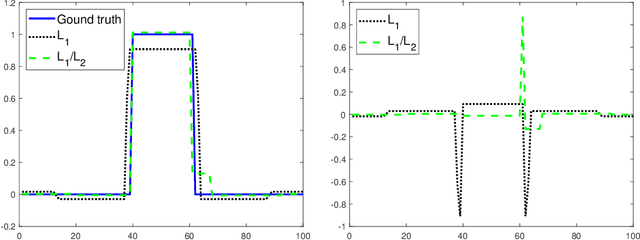
Abstract:In this paper, we study the L1/L2 minimization on the gradient for imaging applications. Several recent works have demonstrated that L1/L2 is better than the L1 norm when approximating the L0 norm to promote sparsity. Consequently, we postulate that applying L1/L2 on the gradient is better than the classic total variation (the L1 norm on the gradient) to enforce the sparsity of the image gradient. To verify our hypothesis, we consider a constrained formulation to reveal empirical evidence on the superiority of L1/L2 over L1 when recovering piecewise constant signals from low-frequency measurements. Numerically, we design a specific splitting scheme, under which we can prove the subsequential convergence for the alternating direction method of multipliers (ADMM). Experimentally, we demonstrate visible improvements of L1/L2 over L1 and other nonconvex regularizations for image recovery from low-frequency measurements and two medical applications of MRI and CT reconstruction. All the numerical results show the efficiency of our proposed approach.
Limited-angle CT reconstruction via the L1/L2 minimization
May 31, 2020
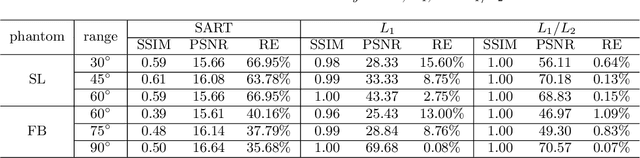

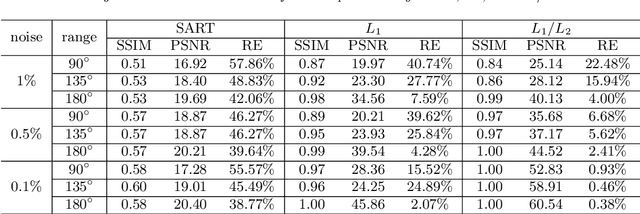
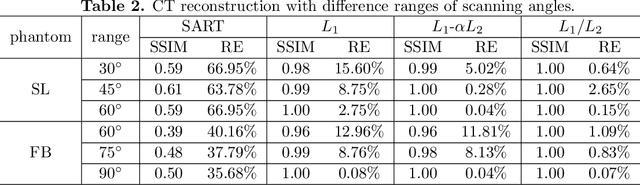
Abstract:In this paper, we consider minimizing the L1/L2 term on the gradient for a limit-angle scanning problem in computed tomography (CT) reconstruction. We design a splitting framework for both constrained and unconstrained optimization models. In addition, we can incorporate a box constraint that is reasonable for imaging applications. Numerical schemes are based on the alternating direction method of multipliers (ADMM), and we provide the convergence analysis of all the proposed algorithms (constrained/unconstrained and with/without the box constraint). Experimental results demonstrate the efficiency of our proposed approaches, showing significant improvements over the state-of-the-art methods in the limit-angle CT reconstruction. Specifically worth noticing is an exact recovery of the Shepp-Logan phantom from noiseless projection data with 30 scanning angle.
Unorganized Malicious Attacks Detection
Feb 18, 2018

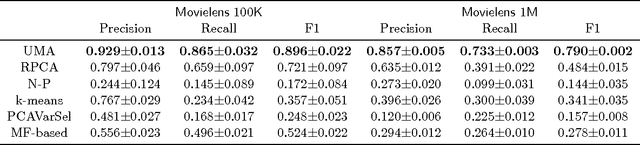

Abstract:Recommender system has attracted much attention during the past decade. Many attack detection algorithms have been developed for better recommendations, mostly focusing on shilling attacks, where an attack organizer produces a large number of user profiles by the same strategy to promote or demote an item. This work considers a different attack style: unorganized malicious attacks, where attackers individually utilize a small number of user profiles to attack different items without any organizer. This attack style occurs in many real applications, yet relevant study remains open. We first formulate the unorganized malicious attacks detection as a matrix completion problem, and propose the Unorganized Malicious Attacks detection (UMA) approach, a proximal alternating splitting augmented Lagrangian method. We verify, both theoretically and empirically, the effectiveness of our proposed approach.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge