Libang Zhang
Smoothness Really Matters: A Simple yet Effective Approach for Unsupervised Graph Domain Adaptation
Dec 16, 2024



Abstract:Unsupervised Graph Domain Adaptation (UGDA) seeks to bridge distribution shifts between domains by transferring knowledge from labeled source graphs to given unlabeled target graphs. Existing UGDA methods primarily focus on aligning features in the latent space learned by graph neural networks (GNNs) across domains, often overlooking structural shifts, resulting in limited effectiveness when addressing structurally complex transfer scenarios. Given the sensitivity of GNNs to local structural features, even slight discrepancies between source and target graphs could lead to significant shifts in node embeddings, thereby reducing the effectiveness of knowledge transfer. To address this issue, we introduce a novel approach for UGDA called Target-Domain Structural Smoothing (TDSS). TDSS is a simple and effective method designed to perform structural smoothing directly on the target graph, thereby mitigating structural distribution shifts and ensuring the consistency of node representations. Specifically, by integrating smoothing techniques with neighborhood sampling, TDSS maintains the structural coherence of the target graph while mitigating the risk of over-smoothing. Our theoretical analysis shows that TDSS effectively reduces target risk by improving model smoothness. Empirical results on three real-world datasets demonstrate that TDSS outperforms recent state-of-the-art baselines, achieving significant improvements across six transfer scenarios. The code is available in https://github.com/cwei01/TDSS.
SCNet: A Neural Network for Automated Side-Channel Attack
Aug 02, 2020
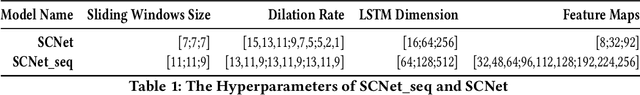
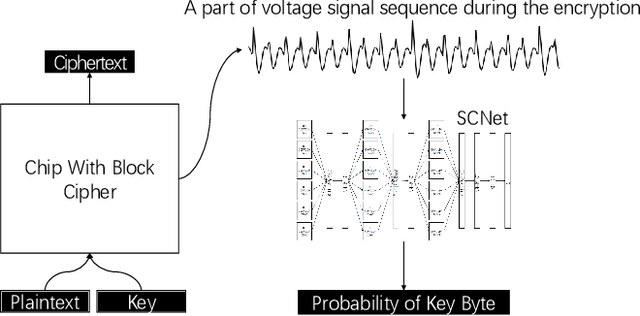
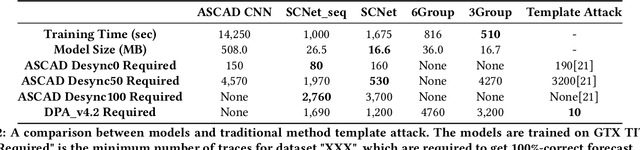
Abstract:The side-channel attack is an attack method based on the information gained about implementations of computer systems, rather than weaknesses in algorithms. Information about system characteristics such as power consumption, electromagnetic leaks and sound can be exploited by the side-channel attack to compromise the system. Much research effort has been directed towards this field. However, such an attack still requires strong skills, thus can only be performed effectively by experts. Here, we propose SCNet, which automatically performs side-channel attacks. And we also design this network combining with side-channel domain knowledge and different deep learning model to improve the performance and better to explain the result. The results show that our model achieves good performance with fewer parameters. The proposed model is a useful tool for automatically testing the robustness of computer systems.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge