Laura Alzola Kirschgens
Volatile memory forensics for the Robot Operating System
Dec 22, 2018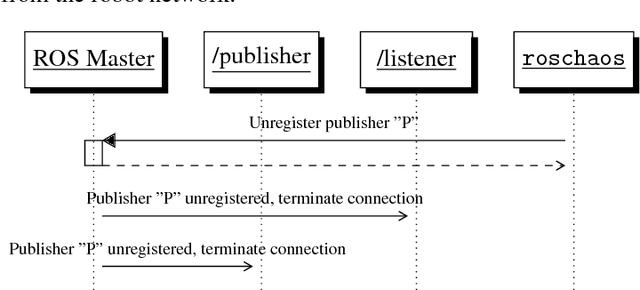
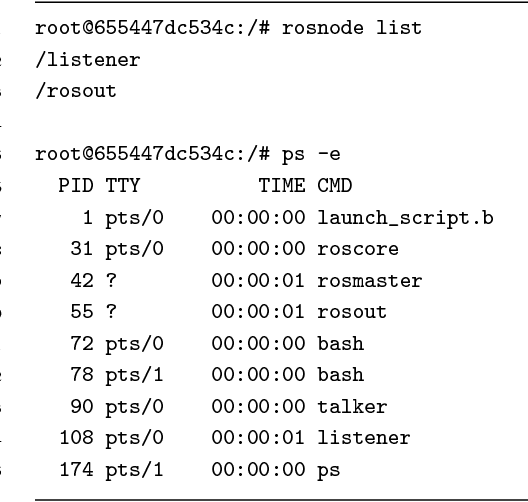
Abstract:The increasing impact of robotics on industry and on society will unavoidably lead to the involvement of robots in incidents and mishaps. In such cases, forensic analyses are key techniques to provide useful evidence on what happened, and try to prevent future incidents. This article discusses volatile memory forensics for the Robot Operating System (ROS). The authors start by providing a general overview of forensic techniques in robotics and then present a robotics-specific Volatility plugin named linux_rosnode, packaged within the ros_volatility project and aimed to extract evidence from robot's volatile memory. They demonstrate how this plugin can be used to detect a specific attack pattern on ROS, where a publisher node is unregistered externally, leading to denial of service and disruption of robotic behaviors. Step-by-step, common practices are introduced for performing forensic analysis and several techniques to capture memory are described. The authors finalize by introducing some future remarks while providing references to reproduce their work.
Aztarna, a footprinting tool for robots
Dec 22, 2018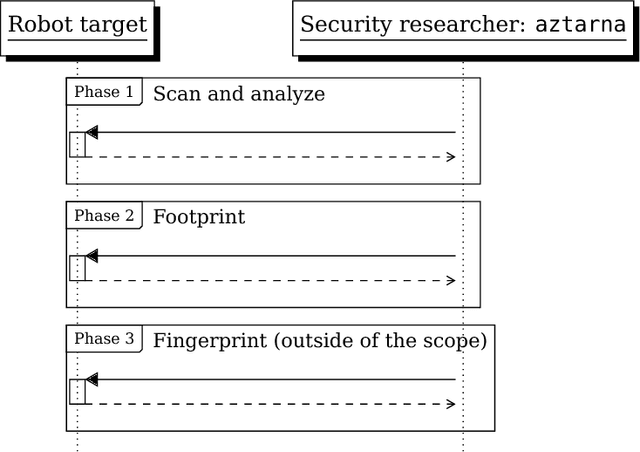
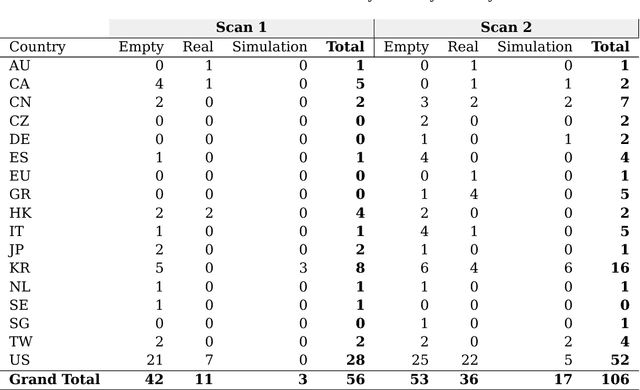
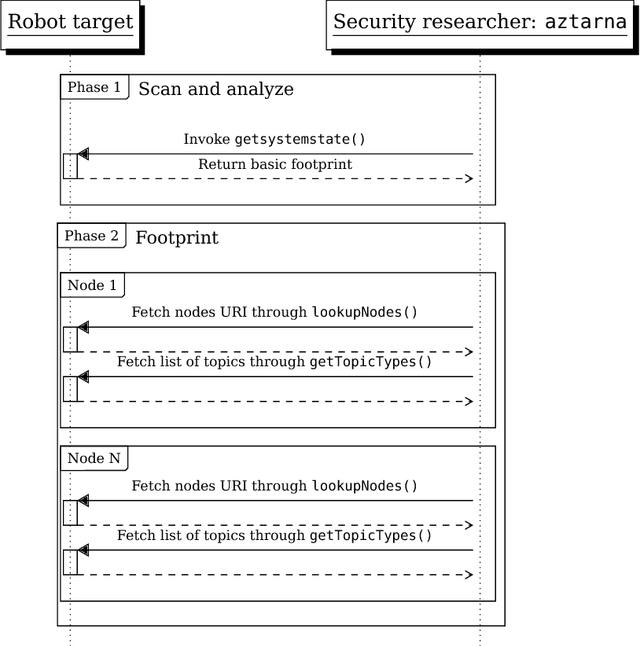
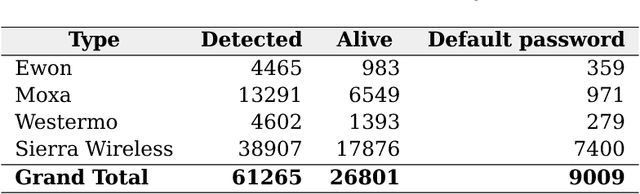
Abstract:Industry 4.0 is changing the commonly held assumption that robots are to be deployed in closed and isolated networks. When analyzed from a security point of view, the global picture is disheartening: robotics industry has not seriously allocated effort to follow good security practices in the robots produced. Instead, most manufacturers keep forwarding the problem to the end-users of these machines. As learned in previous technological revolutions, such as at the dawn of PCs or smartphones, action needs to be taken in time to avoid disastrous consequences. In an attempt to provide the robotics and security communities with the right tools to perform assessments, in this paper we present aztarna, a footprinting tool for robotics. We discuss how such tool can facilitate the process of identifying vestiges of different robots, while maintaining an extensible structure aimed for future fingerprinting extensions. With this contribution, we aim to raise awareness and interest of the robotics community, robot manufacturers and robot end-users on the need of starting global actions to embrace security. We open source the tool and disclose preliminary results that demonstrate the current insecurity landscape in industry. We argue that the robotic ecosystem is in need of generating a robot security community, conscious about good practices and empowered by the right tools.
Robotics CTF , a playground for robot hacking
Oct 01, 2018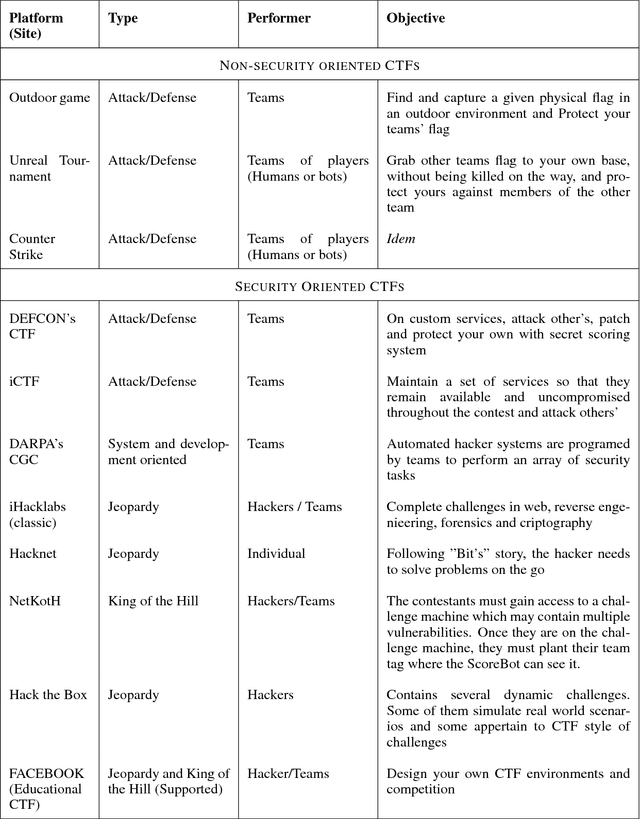
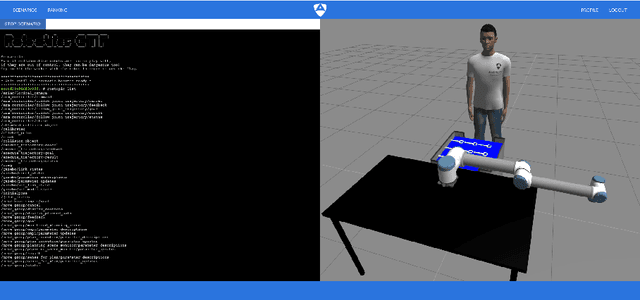
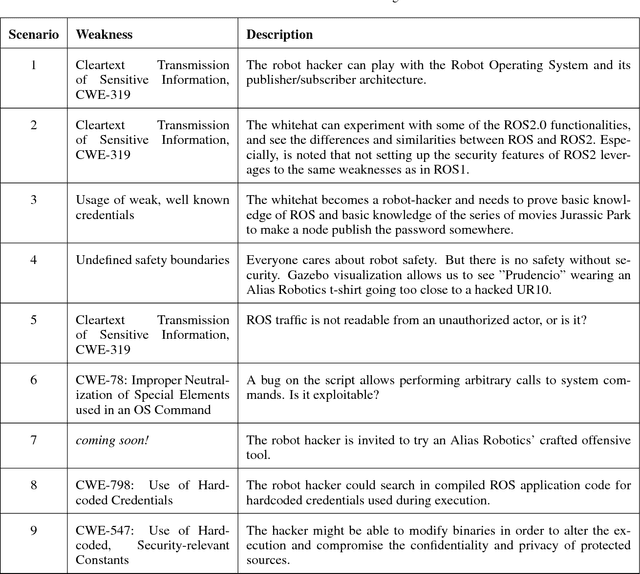
Abstract:Robots state of insecurity is onstage. There is an emerging concern about major robot vulnerabilities and their adverse consequences. However, there is still a considerable gap between robotics and cybersecurity domains. For the purpose of filling that gap, the present technical report presents the Robotics CTF (RCTF), an online playground to challenge robot security from any browser. We describe the architecture of the RCTF and provide 9 scenarios where hackers can challenge the security of different robotic setups. Our work empowers security researchers to a) reproduce virtual robotic scenarios locally and b) change the networking setup to mimic real robot targets. We advocate for hacker powered security in robotics and contribute by open sourcing our scenarios.
Time Synchronization in modular collaborative robots
Sep 19, 2018
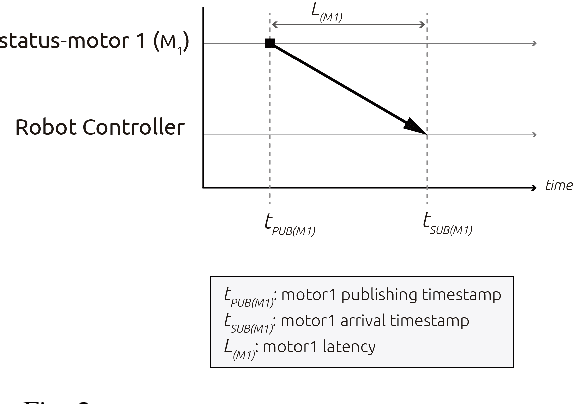
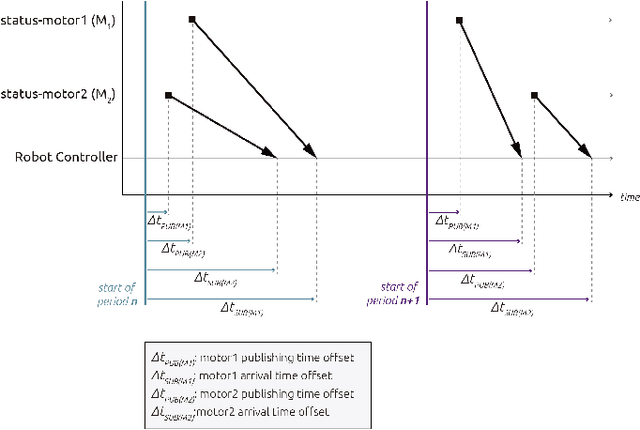
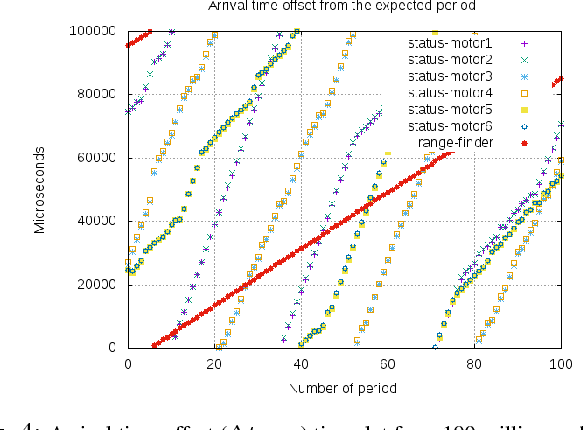
Abstract:A new generation of robot systems which are modular, flexible and safe for human-robot interaction are needed. Existing cobots seem to meet only the later and require a modular approach to improve their reconfigurability and interoperability. We propose a new sub-class of cobots named M-cobots which tackle these problems. In particular, we discuss the relevance of synchronization for these systems, analyze it and demonstrate how with a properly configured M-cobot, we are able to obtain a) distributed sub-microsecond clock synchronization accuracy among modules, b) timestamping accuracy of ROS 2.0 messages under 100 microseconds and c) millisecond-level end-to-end communication latencies, even when disturbed with networking overloads of up to 90% of the network capacity.
Towards an open standard for assessing the severity of robot security vulnerabilities, the Robot Vulnerability Scoring System
Jul 26, 2018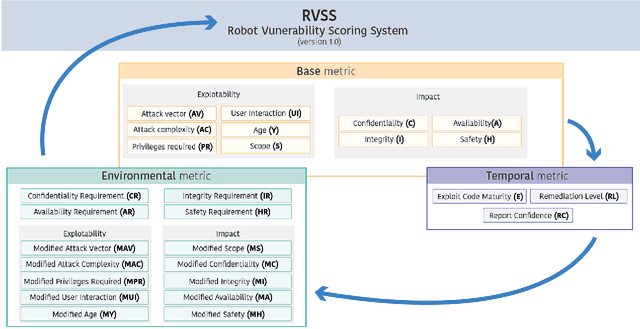
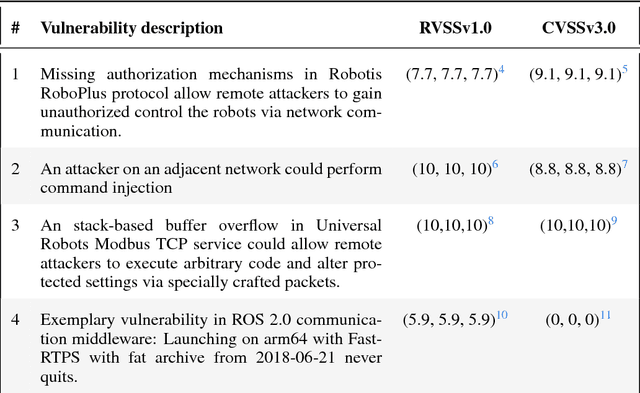
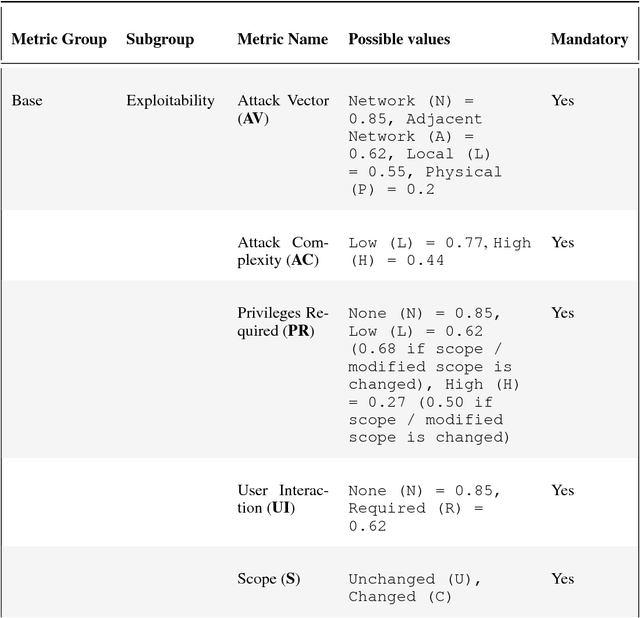
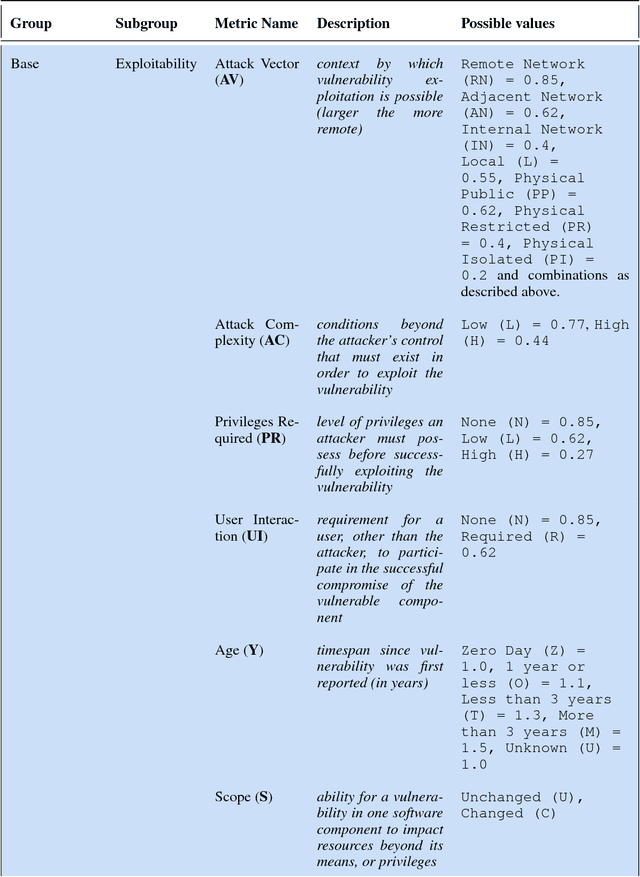
Abstract:Robots are typically not created with security as a main concern. Contrasting to typical IT systems, cyberphysical systems rely on security to handle safety aspects. In light of the former, classic scoring methods such as the Common Vulnerability Scoring System (CVSS) are not able to accurately capture the severity of robot vulnerabilities. The present research work focuses upon creating an open and free to access Robot Vulnerability Scoring System (RVSS) that considers major relevant issues in robotics including a) robot safety aspects, b) assessment of downstream implications of a given vulnerability, c) library and third-party scoring assessments and d) environmental variables, such as time since vulnerability disclosure or exposure on the web. Finally, an experimental evaluation of RVSS with contrast to CVSS is provided and discussed with focus on the robotics security landscape.
Robot hazards: from safety to security
Jun 11, 2018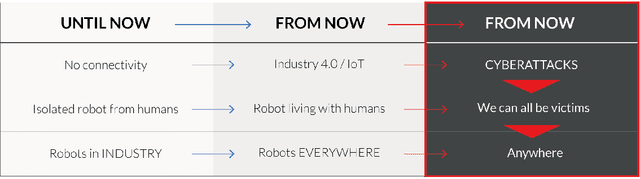
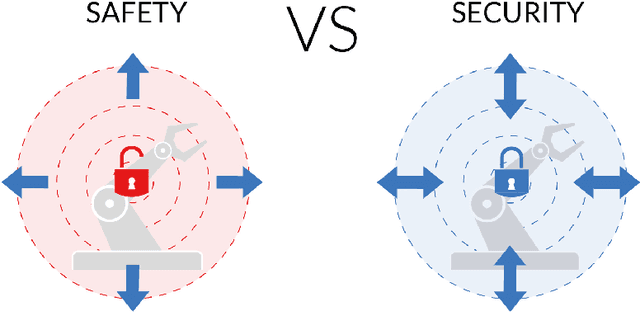
Abstract:Robotics landscape is experiencing big changes. Robots are spreading and will soon be everywhere. Systems traditionally employed in industry are being replaced by collaborative robots, while more and more professional and consumer robots are introduced in people's daily activities. Robots are increasingly intertwined with other facets of IT and envisioned to get much more autonomy, interacting physically with humans. We claim that, following Personal Computers (PCs) and smartphones, robots are the next technological revolution and yet, robot security is being ignored by manufacturers. The present paper aims to alert about the need of dealing not only with safety but with robot security from the very beginning of the forthcoming technological era. We provide herein a document that reviews robot hazards and analyzes the consequences of not facing these issues. We advocate strongly for a security-first approach as a must to be implemented now.
Introducing the Robot Security Framework (RSF), a standardized methodology to perform security assessments in robotics
Jun 11, 2018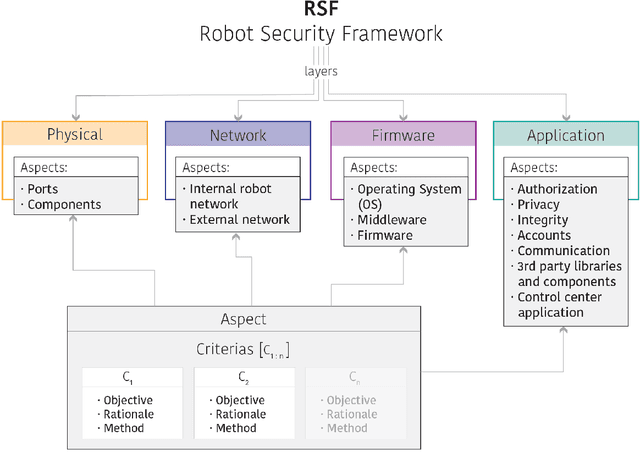
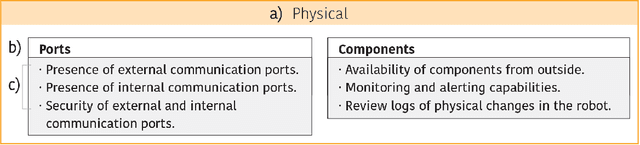
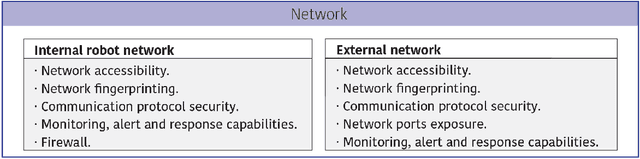
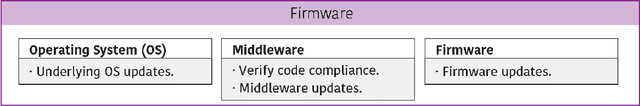
Abstract:Robots have gained relevance in society, increasingly performing critical tasks. Nonetheless, robot security is being underestimated. Robotics security is a complex landscape, which often requires a cross-disciplinar perspective to which classical security lags behind. To address this issue, we present the Robot Security Framework (RSF), a methodology to perform systematic security assessments in robots. We propose, adapt and develop specific terminology and provide guidelines to enable a holistic security assessment following four main layers (Physical, Network, Firmware and Application). We argue that modern robotics should regard as equally relevant internal and external communication security. Finally, we advocate against "security by obscurity". We conclude that the field of security in robotics deserves further research efforts.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge