Volatile memory forensics for the Robot Operating System
Paper and Code
Dec 22, 2018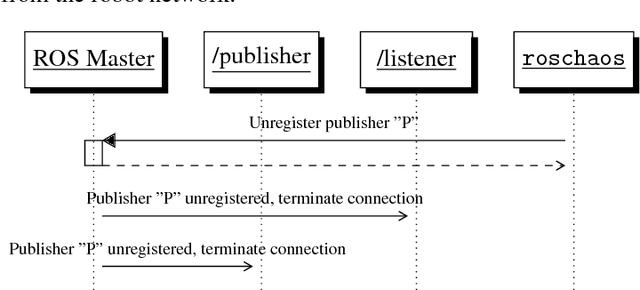
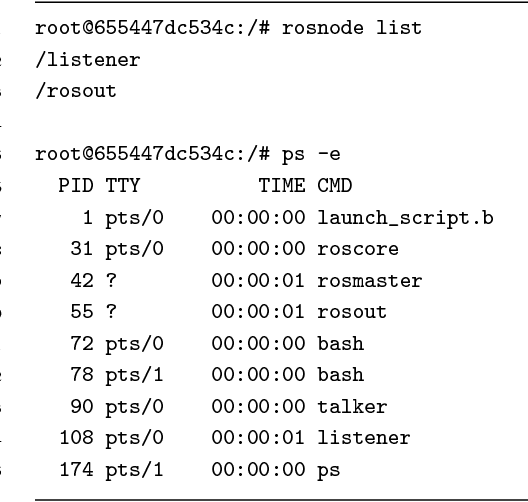
The increasing impact of robotics on industry and on society will unavoidably lead to the involvement of robots in incidents and mishaps. In such cases, forensic analyses are key techniques to provide useful evidence on what happened, and try to prevent future incidents. This article discusses volatile memory forensics for the Robot Operating System (ROS). The authors start by providing a general overview of forensic techniques in robotics and then present a robotics-specific Volatility plugin named linux_rosnode, packaged within the ros_volatility project and aimed to extract evidence from robot's volatile memory. They demonstrate how this plugin can be used to detect a specific attack pattern on ROS, where a publisher node is unregistered externally, leading to denial of service and disruption of robotic behaviors. Step-by-step, common practices are introduced for performing forensic analysis and several techniques to capture memory are described. The authors finalize by introducing some future remarks while providing references to reproduce their work.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge