Katharina Krombholz
"Why do so?" -- A Practical Perspective on Machine Learning Security
Jul 11, 2022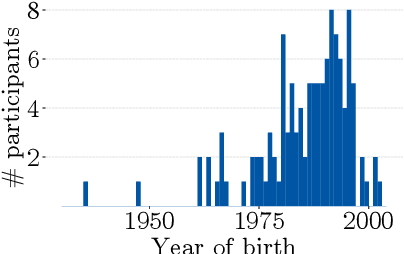
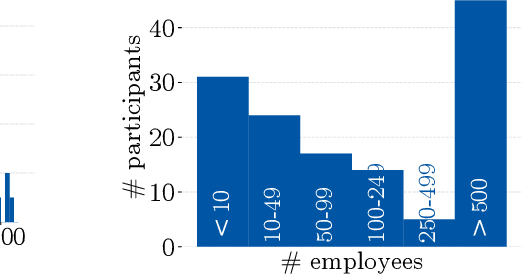
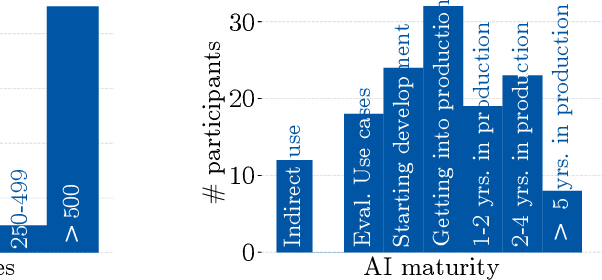
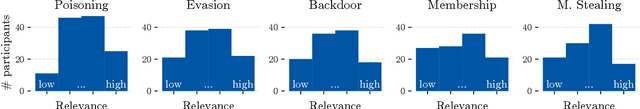
Abstract:Despite the large body of academic work on machine learning security, little is known about the occurrence of attacks on machine learning systems in the wild. In this paper, we report on a quantitative study with 139 industrial practitioners. We analyze attack occurrence and concern and evaluate statistical hypotheses on factors influencing threat perception and exposure. Our results shed light on real-world attacks on deployed machine learning. On the organizational level, while we find no predictors for threat exposure in our sample, the amount of implement defenses depends on exposure to threats or expected likelihood to become a target. We also provide a detailed analysis of practitioners' replies on the relevance of individual machine learning attacks, unveiling complex concerns like unreliable decision making, business information leakage, and bias introduction into models. Finally, we find that on the individual level, prior knowledge about machine learning security influences threat perception. Our work paves the way for more research about adversarial machine learning in practice, but yields also insights for regulation and auditing.
Mental Models of Adversarial Machine Learning
May 08, 2021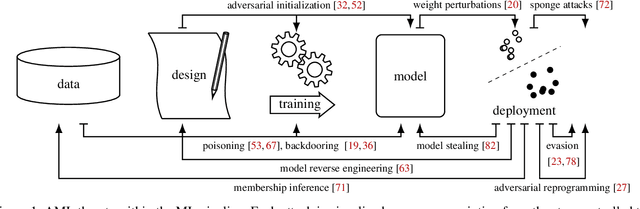
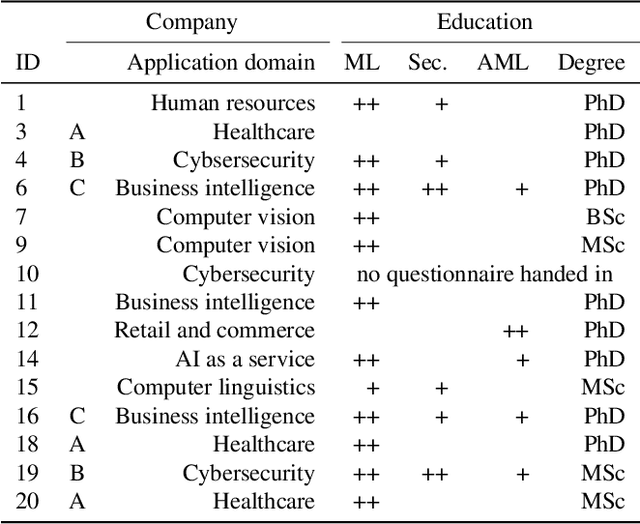
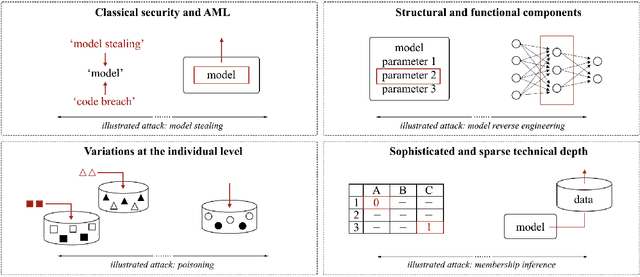
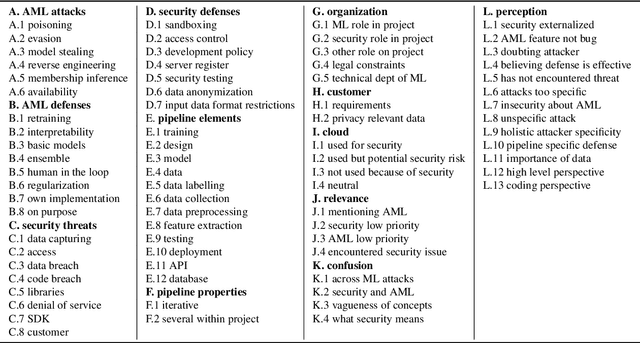
Abstract:Although machine learning (ML) is widely used in practice, little is known about practitioners' actual understanding of potential security challenges. In this work, we close this substantial gap in the literature and contribute a qualitative study focusing on developers' mental models of the ML pipeline and potentially vulnerable components. Studying mental models has helped in other security fields to discover root causes or improve risk communication. Our study reveals four characteristic ranges in mental models of industrial practitioners. The first range concerns the intertwined relationship of adversarial machine learning (AML) and classical security. The second range describes structural and functional components. The third range expresses individual variations of mental models, which are neither explained by the application nor by the educational background of the corresponding subjects. The fourth range corresponds to the varying levels of technical depth, which are however not determined by our subjects' level of knowledge. Our characteristic ranges have implications for the integration of AML into corporate workflows, security enhancing tools for practitioners, and creating appropriate regulatory frameworks for AML.
WhiteNet: Phishing Website Detection by Visual Whitelists
Sep 01, 2019



Abstract:Phishing websites aiming at stealing users' information by claiming fake identities and impersonating visual profiles belonging to trustworthy websites are still a major threat for today's Internet thread. Therefore, detecting visual similarity to a set of whitelisted legitimate websites was often used in phishing detection literature. Despite numerous previous efforts, these methods are either evaluated on datasets with severe limitations or assume a close copy of the targeted legitimate webpages, which makes them easy to be bypassed. This paper contributes WhiteNet, a new similarity-based phishing detection framework, i.e., a triplet network with three shared Convolutional Neural Networks (CNNs). We furthermore present WhitePhish, an improved dataset to evaluate WhiteNet and other frameworks in an ecologically valid manner. WhiteNet learns profiles for websites in order to detect zero-day phishing websites and achieves an area of 0.9879 under the ROC curve of legitimate versus phishing binary classification which outperforms re-implemented state-of-the-art methods. WhitePhish is an extended dataset based on an in-depth analysis of whitelist sources and dataset characteristics.
Shape Evasion: Preventing Body Shape Inference of Multi-Stage Approaches
May 27, 2019



Abstract:Modern approaches to pose and body shape estimation have recently achieved strong performance even under challenging real-world conditions. Even from a single image of a clothed person, a realistic looking body shape can be inferred that captures a users' weight group and body shape type well. This opens up a whole spectrum of applications -- in particular in fashion -- where virtual try-on and recommendation systems can make use of these new and automatized cues. However, a realistic depiction of the undressed body is regarded highly private and therefore might not be consented by most people. Hence, we ask if the automatic extraction of such information can be effectively evaded. While adversarial perturbations have been shown to be effective for manipulating the output of machine learning models -- in particular, end-to-end deep learning approaches -- state of the art shape estimation methods are composed of multiple stages. We perform the first investigation of different strategies that can be used to effectively manipulate the automatic shape estimation while preserving the overall appearance of the original image.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge