Gourab Ghatak
Weighted K-Harmonic Means Clustering: Convergence Analysis and Applications to Wireless Communications
Dec 18, 2025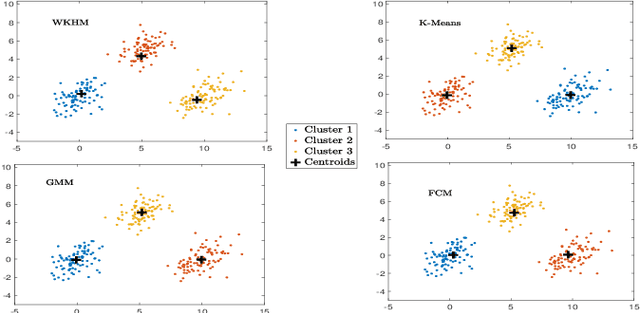
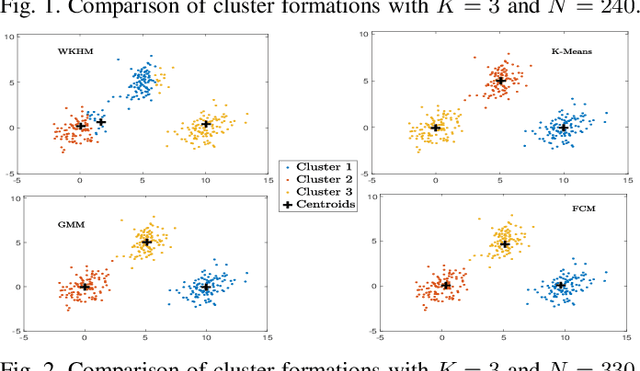
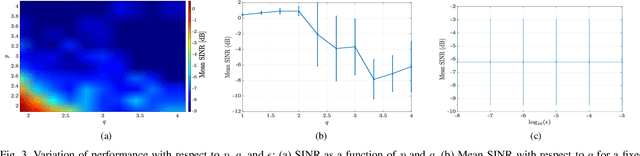
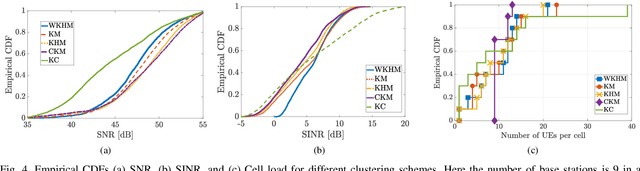
Abstract:We propose the \emph{weighted K-harmonic means} (WKHM) clustering algorithm, a regularized variant of K-harmonic means designed to ensure numerical stability while enabling soft assignments through inverse-distance weighting. Unlike classical K-means and constrained K-means, WKHM admits a direct interpretation in wireless networks: its weights are exactly equivalent to fractional user association based on received signal strength. We establish rigorous convergence guarantees under both deterministic and stochastic settings, addressing key technical challenges arising from non-convexity and random initialization. Specifically, we prove monotone descent to a local minimum under fixed initialization, convergence in probability under Binomial Point Process (BPP) initialization, and almost sure convergence under mild decay conditions. These results provide the first stochastic convergence guarantees for harmonic-mean-based clustering. Finally, through extensive simulations with diverse user distributions, we show that WKHM achieves a superior tradeoff between minimum signal strength and load fairness compared to classical and modern clustering baselines, making it a principled tool for joint radio node placement and user association in wireless networks.
Spatially Correlated Blockage Aware Placement of RIS in IIoT Networks
Aug 23, 2025Abstract:We study the impact of deploying reconfigurable intelligent surfaces (RISs) in mitigating coverage gaps and enhancing transmission reliability in an industrial internet of things (IIoT) network. First, we consider a single blockage scenario and characterize the correlation between blocking events of the base station (BS)-user and the RIS-user links and study its impact on the probability of establishing a viable reflected link. Then, by considering multiple blockages, we derive the distribution of the signal to noise ratio (SNR) as a function of data size, blockage density, the number of RISs, and the deployment area. We analyze the impact of normalized blockage radius and identify the threshold beyond which the assumption of independent blockages deviates from the ground truth of correlated blocking. Finally, we compare the outage performance of this RIS-assisted system with that operated with network- controlled relays, and demonstrate that while the relays provide a higher reliability beyond a certain blockage threshold, increasing the number of RISs may help mitigate this effect. These insights offer valuable design guidelines for deploying RIS-aided IIoT networks in dense blockage environments.
Distribution Bounds on the Conditional ROC in a Poisson Field of Interferers and Clutters
May 27, 2025Abstract:We present a novel analytical framework to characterize the distribution of the conditional receiver operating characteristic (ROC) in radar systems operating within a realization of a Poisson field of interferers and clutters. While conventional stochastic geometry based studies focus on the distribution of signal to interference and noise ratio (SINR), they fail to capture the statistical variations in detection and false-alarm performance across different network realizations. By leveraging higher-order versions of the Campbell-Mecke theorem and tools from stochastic geometry, we derive closed-form expressions for the mean and variance of the conditional false-alarm probability, and provide tight upper bounds using Cantelli's inequality. Additionally, we present a beta distribution approximation to capture the meta-distribution of the noise and interference power, enabling fine-grained performance evaluation. The results are extended to analyze the conditional detection probability, albeit with simpler bounds. Our approach reveals a new approach to radar design and robust ROC selection, including percentile-level guarantees, which are essential for emerging high-reliability applications. The insights derived here advocate for designing radar detection thresholds and signal processing algorithms based not merely on mean false-alarm or detection probabilities, but on tail behavior and percentile guarantees.
Variance-Optimal Arm Selection: Regret Minimization and Best Arm Identification
May 17, 2025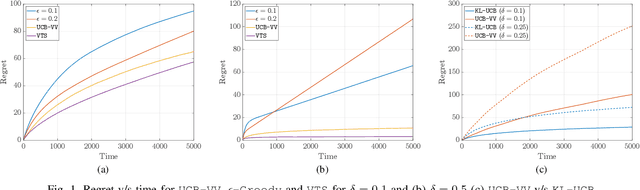
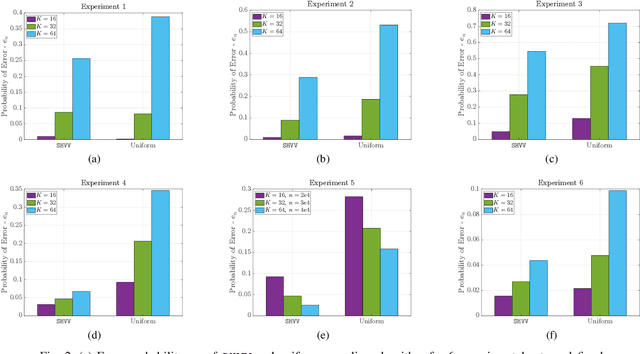
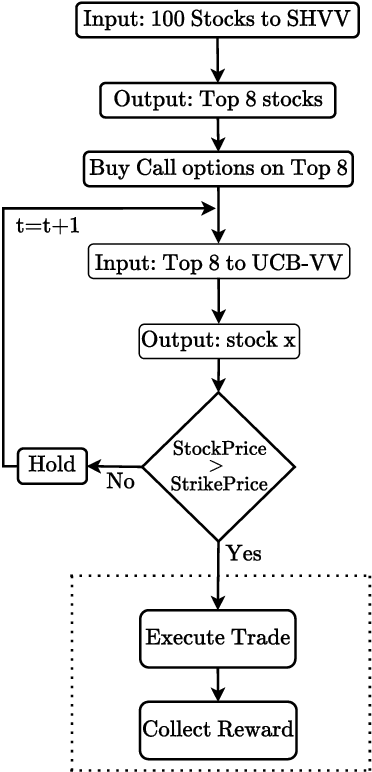
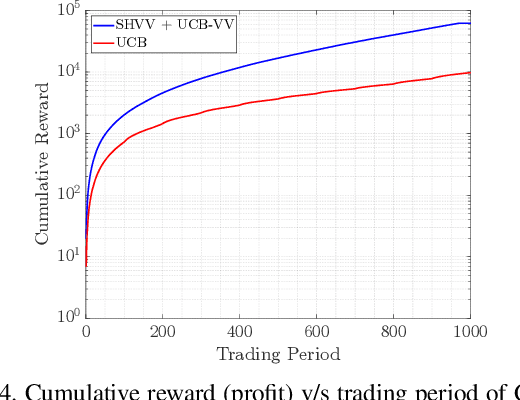
Abstract:This paper focuses on selecting the arm with the highest variance from a set of $K$ independent arms. Specifically, we focus on two settings: (i) regret setting, that penalizes the number of pulls of suboptimal arms in terms of variance, and (ii) fixed-budget \ac{BAI} setting, that evaluates the ability of an algorithm to determine the arm with the highest variance after a fixed number of pulls. We develop a novel online algorithm called \texttt{UCB-VV} for the regret setting and show that its upper bound on regret for bounded rewards evolves as $\mathcal{O}\left(\log{n}\right)$ where $n$ is the horizon. By deriving the lower bound on the regret, we show that \texttt{UCB-VV} is order optimal. For the fixed budget \ac{BAI} setting and propose the \texttt{SHVV} algorithm. We show that the upper bound of the error probability of \texttt{SHVV} evolves as $\exp\left(-\frac{n}{\log(K) H}\right)$, where $H$ represents the complexity of the problem, and this rate matches the corresponding lower bound. We extend the framework from bounded distributions to sub-Gaussian distributions using a novel concentration inequality on the sample variance. Leveraging the same, we derive a concentration inequality for the empirical Sharpe ratio (SR) for sub-Gaussian distributions, which was previously unknown in the literature. Empirical simulations show that \texttt{UCB-VV} consistently outperforms \texttt{$\epsilon$-greedy} across different sub-optimality gaps though it is surpassed by \texttt{VTS}, which exhibits the lowest regret, albeit lacking in theoretical guarantees. We also illustrate the superior performance of \texttt{SHVV}, for a fixed budget setting under 6 different setups against uniform sampling. Finally, we conduct a case study to empirically evaluate the performance of the \texttt{UCB-VV} and \texttt{SHVV} in call option trading on $100$ stocks generated using \ac{GBM}.
UAV-Based Cell-Free Massive MIMO: Joint Placement and Power Optimization under Fronthaul Capacity Limitations
Feb 07, 2025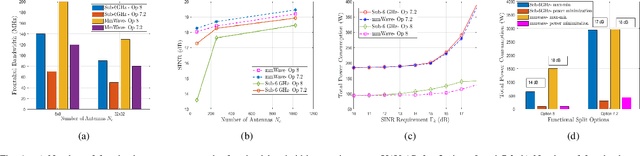
Abstract:We consider a cell-free massive multiple-input multiple-output (mMIMO) network, where unmanned aerial vehicles (UAVs) equipped with multiple antennas serve as distributed UAV-access points (UAV-APs). These UAV-APs provide seamless coverage by jointly serving user equipments (UEs) with out predefined cell boundaries. However, high-capacity wireless networks face significant challenges due to fronthaul limitations in UAV-assisted architectures. This letter proposes a novel UAV-based cell-free mMIMO framework that leverages distributed UAV-APs to serve UEs while addressing the capacity constraints of wireless fronthaul links. We evaluate functional split Options 7.2 and 8 for the fronthaul links, aiming to maximize the minimum signal-to-interference-plus-noise ratio (SINR) among the UEs and minimize the power consumption by optimizing the transmit powers of UAV-APs and selectively activating them. Our analysis compares sub-6 GHz and millimeter wave (mmWave) bands for the fronthaul, showing that mmWave achieves superior SINR with lower power consumption, particularly under Option 8. Additionally, we determine the minimum fronthaul bandwidth required to activate a single UAV-AP under different split options.
An Algorithm for Fixed Budget Best Arm Identification with Combinatorial Exploration
Feb 03, 2025



Abstract:We consider the best arm identification (BAI) problem in the $K-$armed bandit framework with a modification - the agent is allowed to play a subset of arms at each time slot instead of one arm. Consequently, the agent observes the sample average of the rewards of the arms that constitute the probed subset. Several trade-offs arise here - e.g., sampling a larger number of arms together results in a wider view of the environment, while sampling fewer arms enhances the information about individual reward distributions. Furthermore, grouping a large number of suboptimal arms together albeit reduces the variance of the reward of the group, it may enhance the group mean to make it close to that containing the optimal arm. To solve this problem, we propose an algorithm that constructs $\log_2 K$ groups and performs a likelihood ratio test to detect the presence of the best arm in each of these groups. Then a Hamming decoding procedure determines the unique best arm. We derive an upper bound for the error probability of the proposed algorithm based on a new hardness parameter $H_4$. Finally, we demonstrate cases under which it outperforms the state-of-the-art algorithms for the single play case.
Fine Grained Analysis and Optimization of Large Scale Automotive Radar Networks
Nov 30, 2024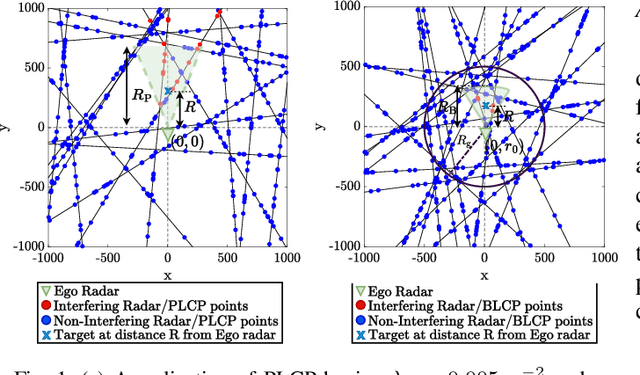
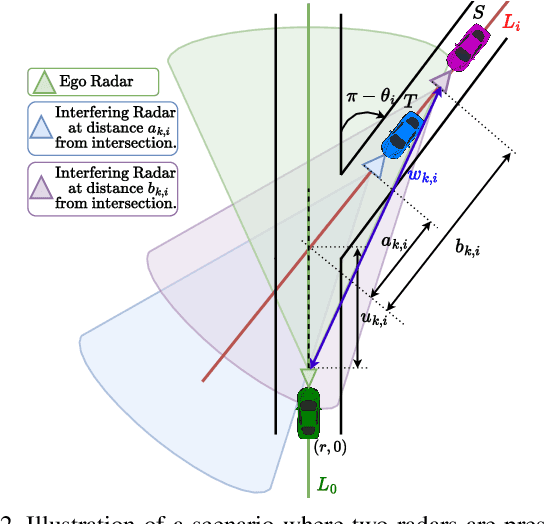
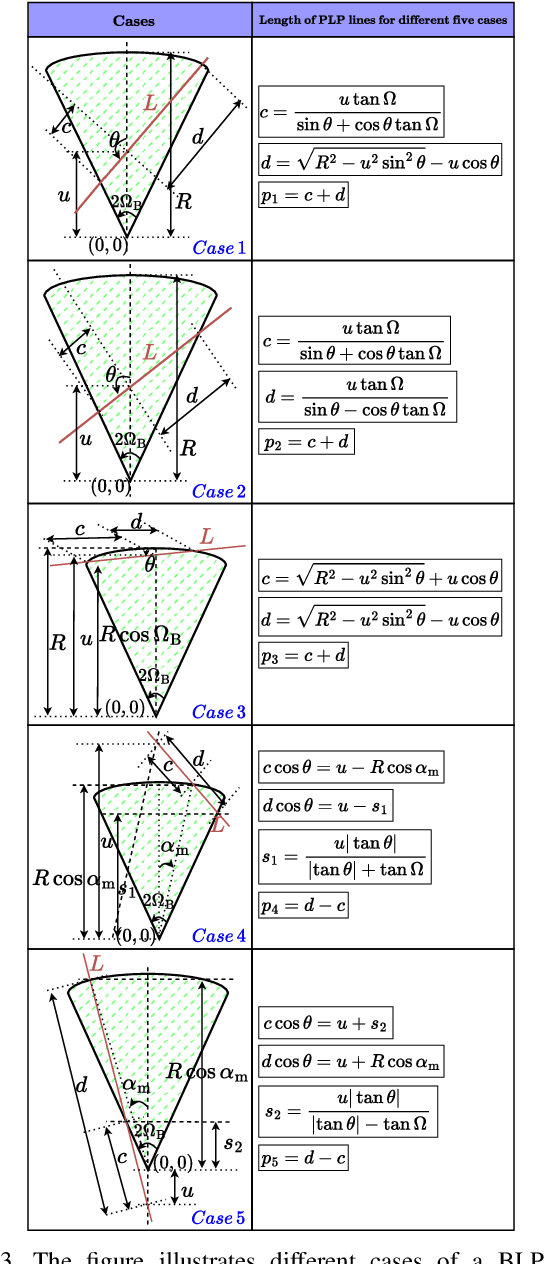
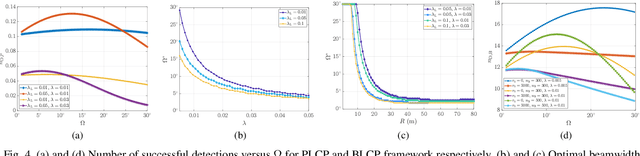
Abstract:Advanced driver assistance systems (ADAS) enabled by automotive radars have significantly enhanced vehicle safety and driver experience. However, the extensive use of radars in dense road conditions introduces mutual interference, which degrades detection accuracy and reliability. Traditional interference models are limited to simple highway scenarios and cannot characterize the performance of automotive radars in dense urban environments. In our prior work, we employed stochastic geometry (SG) to develop two automotive radar network models: the Poisson line Cox process (PLCP) for dense city centers and smaller urban zones and the binomial line Cox process (BLCP) to encompass both urban cores and suburban areas. In this work, we introduce the meta-distribution (MD) framework upon these two models to distinguish the sources of variability in radar detection metrics. Additionally, we optimize the radar beamwidth and transmission probability to maximize the number of successful detections of a radar node in the network. Further, we employ a computationally efficient Chebyshev-Markov (CM) bound method for reconstructing MDs, achieving higher accuracy than the conventional Gil-Pelaez theorem. Using the framework, we analyze the specific impacts of beamwidth, detection range, and interference on radar detection performance and offer practical insights for developing adaptive radar systems tailored to diverse traffic and environmental conditions.
Impact of Device Caching and Handovers on the Performance of 3D UAV Networks with Blockages
Sep 30, 2024



Abstract:We investigate an urban network characterized by blockages, where unmanned aerial vehicles (UAVs) offer ad-hoc coverage to mobile users with distinct service rate requirements. The UAV-BSs are modeled using a two-dimensional (2-D) marked-poisson point process (MPPP), where the marks represent the altitude of each UAV-base station (UAV-BS). Initially, we model the network blockages and analyze the association probabilities of line-of-sight (LoS) and non-line-of-sight (NLoS) UAV-BSs using stochastic geometry. Subsequently, we derive the bth moment of the conditional success probability (CSP) and employ a meta distribution (MD)-based analytical framework of signal-to-interference noise ratio (SINR) taking into account the blockage distribution in the network. Furthermore, we proposea cache-based handover management strategy that dynamically selects the cell search time and delays the received signal strength (RSS)-based base station (BS) associations. This strategy aims to minimize unnecessary handovers (HOs) experienced by users by leveraging caching capabilities at user equipment (UE). We evaluate the HO rate and average throughput experienced by users ensuring their service rate requirements are met. We demonstrate that LoS associations decrease as the network density increases due to the substantial increase of NLoS UAV-BSs in the network. Additionally, we show that the presence of blockages does not necessarily have a negative impact on network reliability
Optimizing Sharpe Ratio: Risk-Adjusted Decision-Making in Multi-Armed Bandits
May 28, 2024


Abstract:Sharpe Ratio (SR) is a critical parameter in characterizing financial time series as it jointly considers the reward and the volatility of any stock/portfolio through its variance. Deriving online algorithms for optimizing the SR is particularly challenging since even offline policies experience constant regret with respect to the best expert Even-Dar et al (2006). Thus, instead of optimizing the usual definition of SR, we optimize regularized square SR (RSSR). We consider two settings for the RSSR, Regret Minimization (RM) and Best Arm Identification (BAI). In this regard, we propose a novel multi-armed bandit (MAB) algorithm for RM called UCB-RSSR for RSSR maximization. We derive a path-dependent concentration bound for the estimate of the RSSR. Based on that, we derive the regret guarantees of UCB-RSSR and show that it evolves as O(log n) for the two-armed bandit case played for a horizon n. We also consider a fixed budget setting for well-known BAI algorithms, i.e., sequential halving and successive rejects, and propose SHVV, SHSR, and SuRSR algorithms. We derive the upper bound for the error probability of all proposed BAI algorithms. We demonstrate that UCB-RSSR outperforms the only other known SR optimizing bandit algorithm, U-UCB Cassel et al (2023). We also establish its efficacy with respect to other benchmarks derived from the GRA-UCB and MVTS algorithms. We further demonstrate the performance of proposed BAI algorithms for multiple different setups. Our research highlights that our proposed algorithms will find extensive applications in risk-aware portfolio management problems. Consequently, our research highlights that our proposed algorithms will find extensive applications in risk-aware portfolio management problems.
Impact of Urban Street Geometry on the Detection Probability of Automotive Radars
Dec 09, 2023

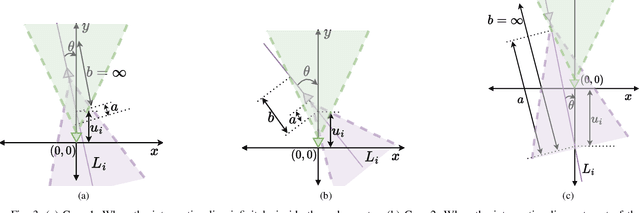
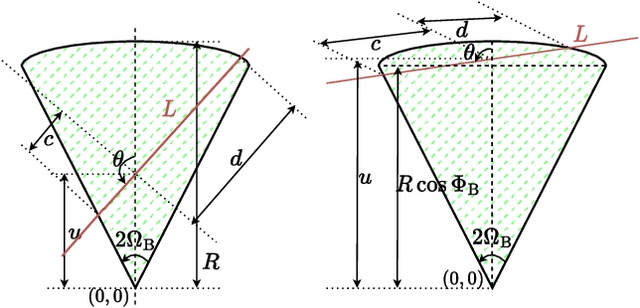
Abstract:Prior works have analyzed the performance of millimeter wave automotive radars in the presence of diverse clutter and interference scenarios using stochastic geometry tools instead of more time-consuming measurement studies or system-level simulations. In these works, the distributions of radars or discrete clutter scatterers were modeled as Poisson point processes in the Euclidean space. However, since most automotive radars are likely to be mounted on vehicles and road infrastructure, road geometries are an important factor that must be considered. Instead of considering each road geometry as an individual case for study, in this work, we model each case as a specific instance of an underlying Poisson line process and further model the distribution of vehicles on the road as a Poisson point process - forming a Poisson line Cox process. Then, through the use of stochastic geometry tools, we estimate the average number of interfering radars for specific road and vehicular densities and the effect of radar parameters such as noise and beamwidth on the radar detection metrics. The numerical results are validated with Monte Carlo simulations.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge