Federico Corò
DATAMUt: Deterministic Algorithms for Time-Delay Attack Detection in Multi-Hop UAV Networks
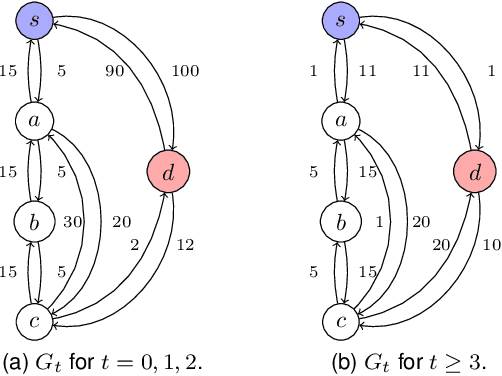
May 12, 2025Abstract:Unmanned Aerial Vehicles (UAVs), also known as drones, have gained popularity in various fields such as agriculture, emergency response, and search and rescue operations. UAV networks are susceptible to several security threats, such as wormhole, jamming, spoofing, and false data injection. Time Delay Attack (TDA) is a unique attack in which malicious UAVs intentionally delay packet forwarding, posing significant threats, especially in time-sensitive applications. It is challenging to distinguish malicious delay from benign network delay due to the dynamic nature of UAV networks, intermittent wireless connectivity, or the Store-Carry-Forward (SCF) mechanism during multi-hop communication. Some existing works propose machine learning-based centralized approaches to detect TDA, which are computationally intensive and have large message overheads. This paper proposes a novel approach DATAMUt, where the temporal dynamics of the network are represented by a weighted time-window graph (TWiG), and then two deterministic polynomial-time algorithms are presented to detect TDA when UAVs have global and local network knowledge. Simulation studies show that the proposed algorithms have reduced message overhead by a factor of five and twelve in global and local knowledge, respectively, compared to existing approaches. Additionally, our approaches achieve approximately 860 and 1050 times less execution time in global and local knowledge, respectively, outperforming the existing methods.
A Novel Multi-Layer Framework for BVLoS Drone Operation: A Preliminary Study
Jan 14, 2023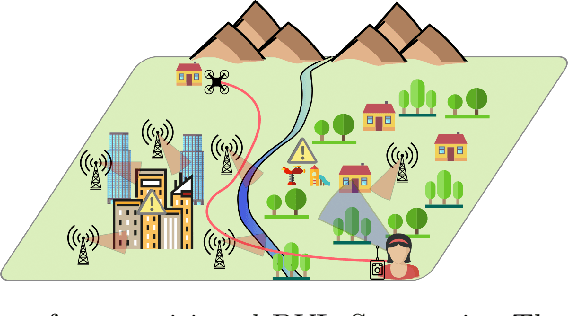
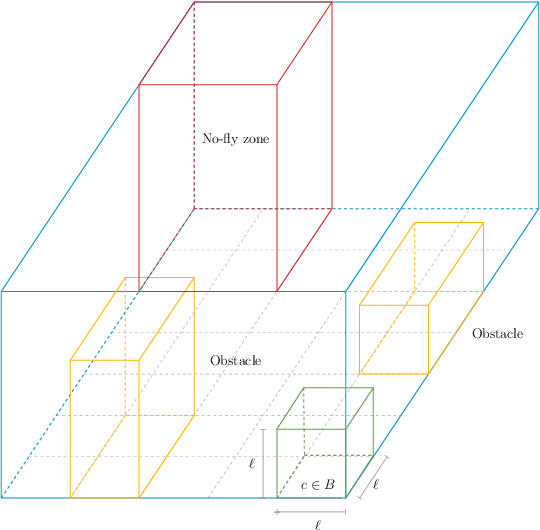
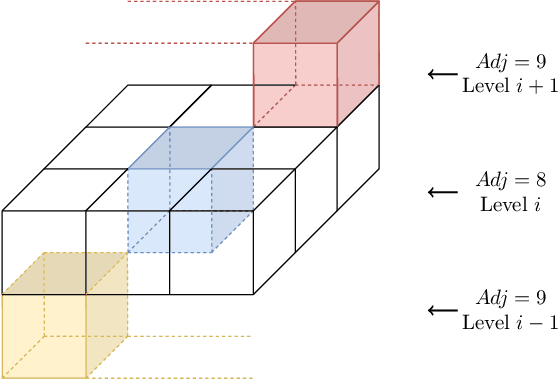
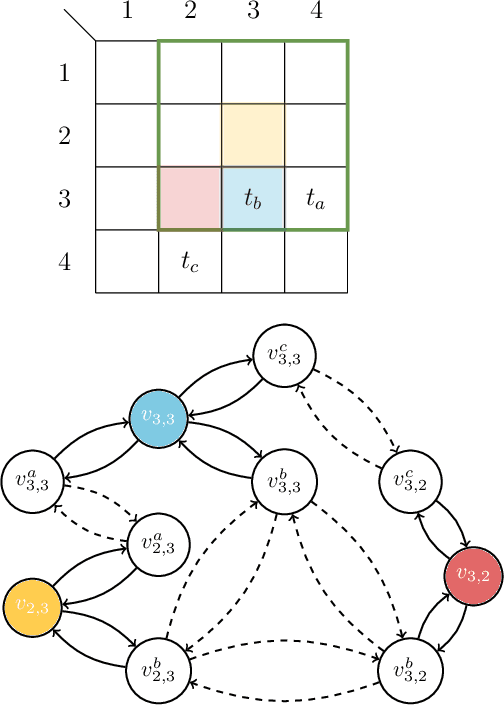
Abstract:Drones have become increasingly popular in a variety of fields, including agriculture, emergency response, and package delivery. However, most drone operations are currently limited to within Visual Line of Sight (vlos) due to safety concerns. Flying drones Beyond Visual Line of Sight (bvlos) presents new challenges and opportunities, but also requires new technologies and regulatory frameworks, not yet implemented, to ensure that the drone is constantly under the control of a remote operator. In this preliminary study, we assume to remotely control the drone using the available ground cellular network infrastructure. We propose to plan bvlos drone operations using a novel multi-layer framework that includes many layers of constraints that closely resemble real-world scenarios and challenges. These layers include information such as the potential ground risk in the event of a drone failure, the available ground cellular network infrastructure, and the presence of ground obstacles. From the multi-layer framework, a graph is constructed whose edges are weighted with a dependability score that takes into account the information of the multi-layer framework. Then, the planning of bvlos drone missions is equivalent to solving the Maximum Path Dependability Problem on the constructed graph, which turns out to be solvable by applying Dijkstra's algorithm.
Securing Federated Learning against Overwhelming Collusive Attackers
Sep 28, 2022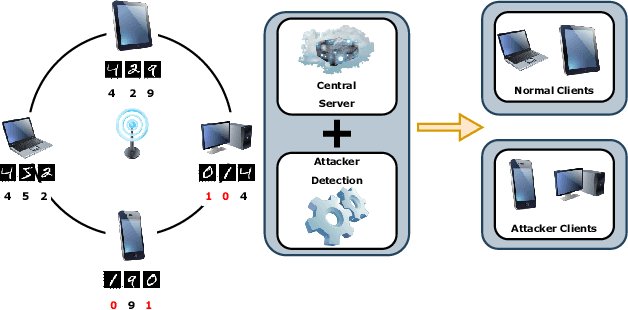
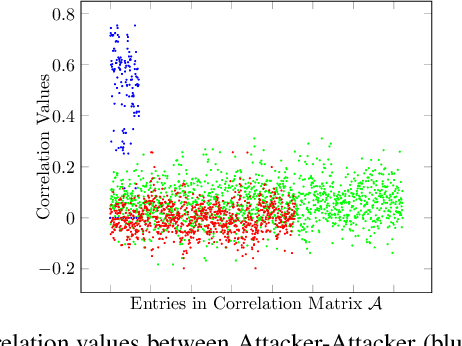
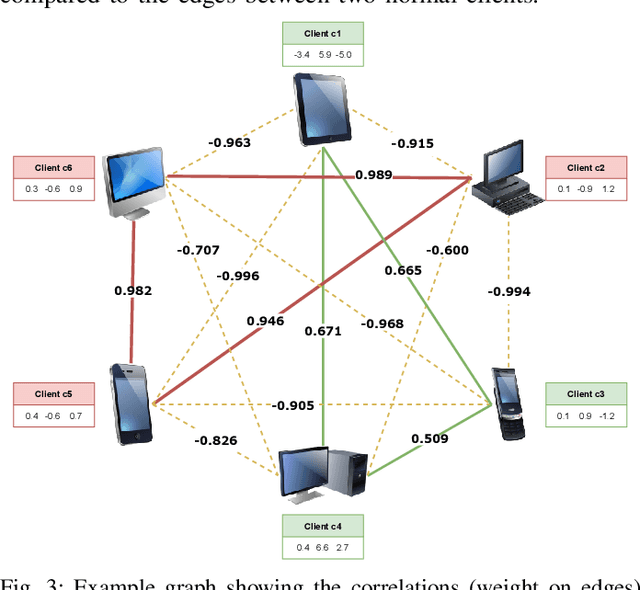
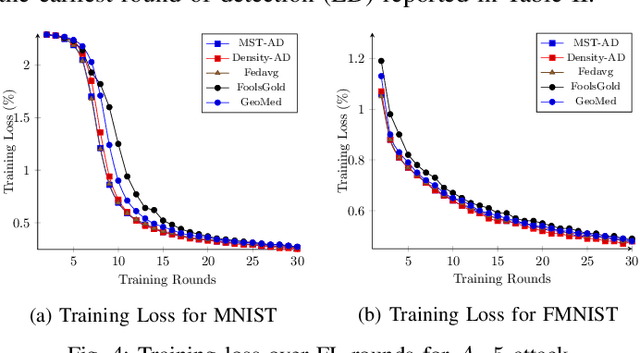
Abstract:In the era of a data-driven society with the ubiquity of Internet of Things (IoT) devices storing large amounts of data localized at different places, distributed learning has gained a lot of traction, however, assuming independent and identically distributed data (iid) across the devices. While relaxing this assumption that anyway does not hold in reality due to the heterogeneous nature of devices, federated learning (FL) has emerged as a privacy-preserving solution to train a collaborative model over non-iid data distributed across a massive number of devices. However, the appearance of malicious devices (attackers), who intend to corrupt the FL model, is inevitable due to unrestricted participation. In this work, we aim to identify such attackers and mitigate their impact on the model, essentially under a setting of bidirectional label flipping attacks with collusion. We propose two graph theoretic algorithms, based on Minimum Spanning Tree and k-Densest graph, by leveraging correlations between local models. Our FL model can nullify the influence of attackers even when they are up to 70% of all the clients whereas prior works could not afford more than 50% of clients as attackers. The effectiveness of our algorithms is ascertained through experiments on two benchmark datasets, namely MNIST and Fashion-MNIST, with overwhelming attackers. We establish the superiority of our algorithms over the existing ones using accuracy, attack success rate, and early detection round.
Multi-Depot Multi-Trip Vehicle Routing with Total Completion Time Minimization
Jul 13, 2022



Abstract:Unmanned aerial vehicles (UAVs) are aircraft whose flights can be fully autonomous without any provision for human intervention. One of the most useful and promising domains where UAVs can be employed is natural disaster management. In this paper, we focus on an emergency scenario and propose the use of a fleet of UAVs that help rescue teams to individuate people needing help inside an affected area. We model this situation as an original graph theoretical problem called Multi-Depot Multi-Trip Vehicle Routing Problem with Total Completion Times minimization (MDMT-VRP-TCT); we go through some problems already studied in the literature that appear somehow similar to it and highlight the differences, propose a mathematical formulation for our problem as a MILP, design a matheuristic framework to quickly solve large instances, and experimentally test its performance. Beyond the proposed application, our solution works in any case in which a multi-depot multi-trip vehicle routing problem must be solved.
Energy-Constrained Delivery of Goods with Drones Under Varying Wind Conditions
Dec 17, 2020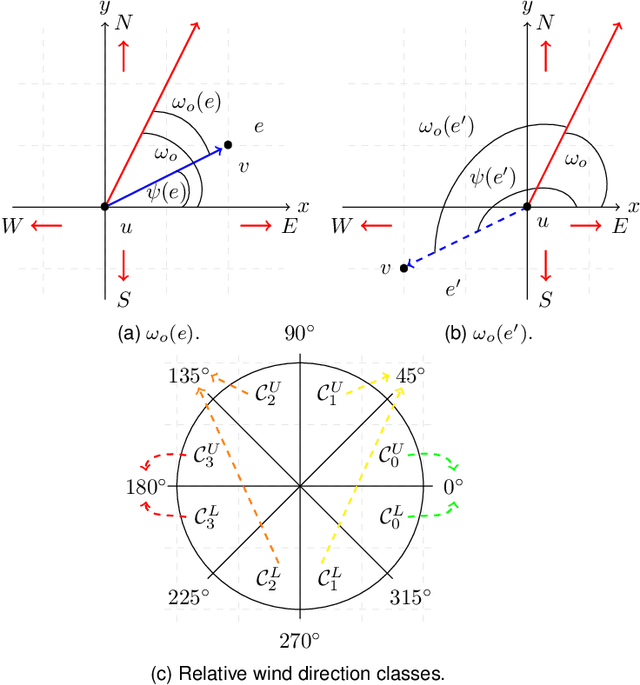
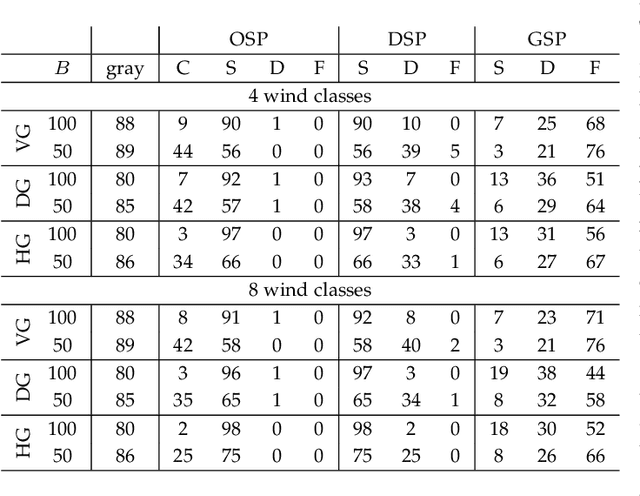
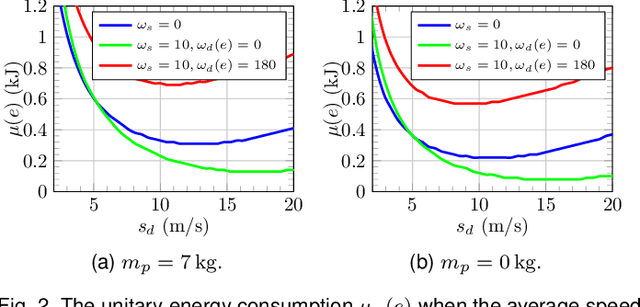
Abstract:In this paper, we study the feasibility of sending drones to deliver goods from a depot to a customer by solving what we call the Mission-Feasibility Problem (MFP). Due to payload constraints, the drone can serve only one customer at a time. To this end, we propose a novel framework based on time-dependent cost graphs to properly model the MFP and tackle the delivery dynamics. When the drone moves in the delivery area, the global wind may change thereby affecting the drone's energy consumption, which in turn can increase or decrease. This issue is addressed by designing three algorithms, namely: (i) compute the route of minimum energy once, at the beginning of the mission, (ii) dynamically reconsider the most convenient trip towards the destination, and (iii) dynamically select only the best local choice. We evaluate the performance of our algorithms on both synthetic and real-world data. The changes in the drone's energy consumption are reflected by changes in the cost of the edges of the graphs. The algorithms receive the new costs every time the drone flies over a new vertex, and they have no full knowledge in advance of the weights. We compare them in terms of the percentage of missions that are completed with success (the drone delivers the goods and comes back to the depot), with delivered (the drone delivers the goods but cannot come back to the depot), and with failure (the drone neither delivers the goods nor comes back to the depot).
* typo author's name
Optimal Routing Schedules for Robots Operating in Aisle-Structures
Sep 15, 2019



Abstract:In this paper, we consider the Constant-cost Orienteering Problem (COP) where a robot, constrained by a limited travel budget, aims at selecting a path with the largest reward in an aisle-graph. The aisle-graph consists of a set of loosely connected rows where the robot can change lane only at either end, but not in the middle. Even when considering this special type of graphs, the orienteering problem is known to be NP-hard. We optimally solve in polynomial time two special cases, COP-FR where the robot can only traverse full rows, and COP-SC where the robot can access the rows only from one side. To solve the general COP, we then apply our special case algorithms as well as a new heuristic that suitably combines them. Despite its light computational complexity and being confined into a very limited class of paths, the optimal solutions for COP-FR turn out to be competitive even for COP in both real and synthetic scenarios. Furthermore, our new heuristic for the general case outperforms state-of-art algorithms, especially for input with highly unbalanced rewards.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge