Fabrizio Ruggeri
CNR IMATI, Milano
A Noise Resilient Approach for Robust Hurst Exponent Estimation
Oct 06, 2025Abstract:Understanding signal behavior across scales is vital in areas such as natural phenomena analysis and financial modeling. A key property is self-similarity, quantified by the Hurst exponent (H), which reveals long-term dependencies. Wavelet-based methods are effective for estimating H due to their multi-scale analysis capability, but additive noise in real-world measurements often degrades accuracy. We propose Noise-Controlled ALPHEE (NC-ALPHEE), an enhancement of the Average Level-Pairwise Hurst Exponent Estimator (ALPHEE), incorporating noise mitigation and generating multiple level-pairwise estimates from signal energy pairs. A neural network (NN) combines these estimates, replacing traditional averaging. This adaptive learning maintains ALPHEE's behavior in noise-free cases while improving performance in noisy conditions. Extensive simulations show that in noise-free data, NC-ALPHEE matches ALPHEE's accuracy using both averaging and NN-based methods. Under noise, however, traditional averaging deteriorates and requires impractical level restrictions, while NC-ALPHEE consistently outperforms existing techniques without such constraints. NC-ALPHEE offers a robust, adaptive approach for H estimation, significantly enhancing the reliability of wavelet-based methods in noisy environments.
Generative Bayesian Computation for Maximum Expected Utility
Aug 28, 2024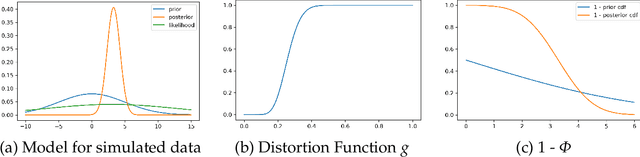
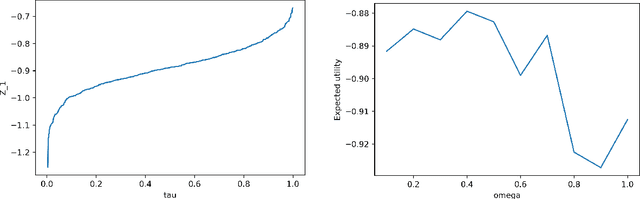
Abstract:Generative Bayesian Computation (GBC) methods are developed to provide an efficient computational solution for maximum expected utility (MEU). We propose a density-free generative method based on quantiles that naturally calculates expected utility as a marginal of quantiles. Our approach uses a deep quantile neural estimator to directly estimate distributional utilities. Generative methods assume only the ability to simulate from the model and parameters and as such are likelihood-free. A large training dataset is generated from parameters and output together with a base distribution. Our method a number of computational advantages primarily being density-free with an efficient estimator of expected utility. A link with the dual theory of expected utility and risk taking is also discussed. To illustrate our methodology, we solve an optimal portfolio allocation problem with Bayesian learning and a power utility (a.k.a. fractional Kelly criterion). Finally, we conclude with directions for future research.
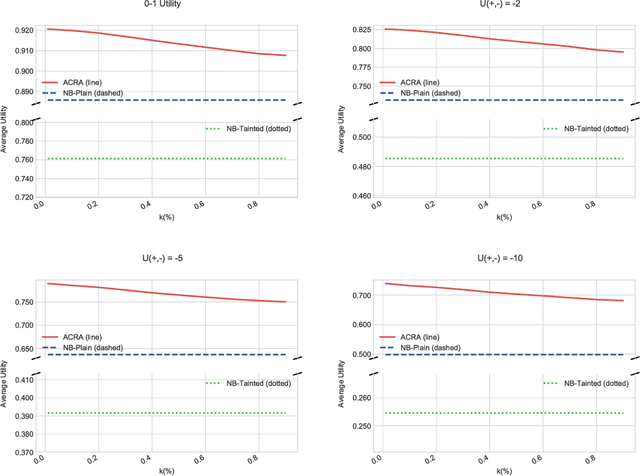
Protecting Classifiers From Attacks. A Bayesian Approach
Apr 18, 2020



Abstract:Classification problems in security settings are usually modeled as confrontations in which an adversary tries to fool a classifier manipulating the covariates of instances to obtain a benefit. Most approaches to such problems have focused on game-theoretic ideas with strong underlying common knowledge assumptions, which are not realistic in the security realm. We provide an alternative Bayesian framework that accounts for the lack of precise knowledge about the attacker's behavior using adversarial risk analysis. A key ingredient required by our framework is the ability to sample from the distribution of originating instances given the possibly attacked observed one. We propose a sampling procedure based on approximate Bayesian computation, in which we simulate the attacker's problem taking into account our uncertainty about his elements. For large scale problems, we propose an alternative, scalable approach that could be used when dealing with differentiable classifiers. Within it, we move the computational load to the training phase, simulating attacks from an adversary, adapting the framework to obtain a classifier robustified against attacks.
Adversarial classification: An adversarial risk analysis approach
Jun 26, 2018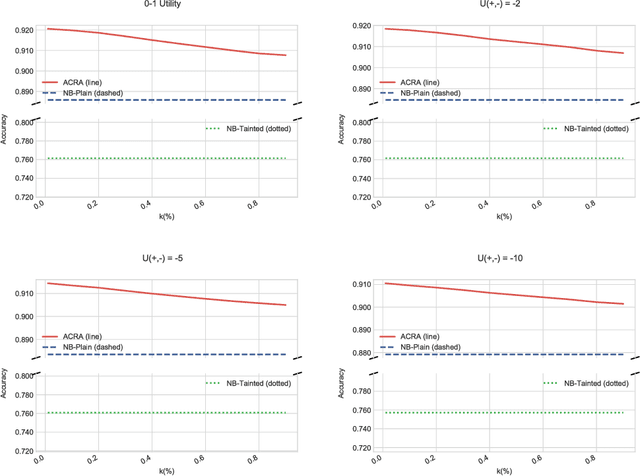
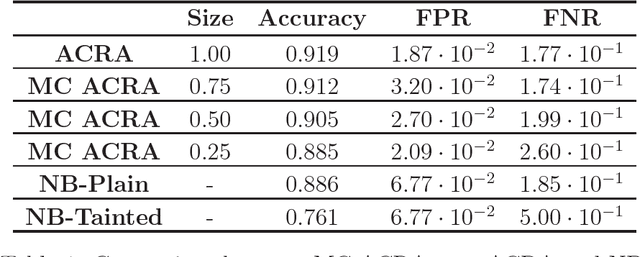

Abstract:Classification problems in security settings are usually contemplated as confrontations in which one or more adversaries try to fool a classifier to obtain a benefit. Most approaches to such adversarial classification problems have focused on game theoretical ideas with strong underlying common knowledge assumptions, which are actually not realistic in security domains. We provide an alternative framework to such problem based on adversarial risk analysis, which we illustrate with several examples. Computational and implementation issues are discussed.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge