Matthias Hollick
Transparent and Resilient Activity Recognition via Attention-Based Distributed Radar Sensing
Jan 06, 2026Abstract:Distributed radar sensors enable robust human activity recognition. However, scaling the number of coordinated nodes introduces challenges in feature extraction from large datasets, and transparent data fusion. We propose an end-to-end framework that operates directly on raw radar data. Each radar node employs a lightweight 2D Convolutional Neural Network (CNN) to extract local features. A self-attention fusion block then models inter-node relationships and performs adaptive information fusion. Local feature extraction reduces the input dimensionality by up to 480x. This significantly lowers communication overhead and latency. The attention mechanism provides inherent interpretability by quantifying the contribution of each radar node. A hybrid supervised contrastive loss further improves feature separability, especially for fine-grained and imbalanced activity classes. Experiments on real-world distributed Ultra Wide Band (UWB) radar data demonstrate that the proposed method reduces model complexity by 70.8\%, while achieving higher average accuracy than baseline approaches. Overall, the framework enables transparent, efficient, and low-overhead distributed radar sensing.
Faulty RIS-aided Integrated Sensing and Communication: Modeling and Optimization
May 23, 2025Abstract:This work investigates a practical reconfigurable intelligent surface (RIS)-aided integrated sensing and communication (ISAC) system, where a subset of RIS elements fail to function properly and reflect incident signals randomly towards unintended directions, thereby degrading system performance. To date, no study has addressed such impairments caused by faulty RIS elements in ISAC systems. This work aims to fill the gap. First, to quantify the impact of faulty elements on ISAC performance, we derive the misspecified Cram\'er-Rao bound (MCRB) for sensing parameter estimation and signal-to-interference-and-noise ratio (SINR) for communication quality. Then, to mitigate the performance loss caused by faulty elements, we jointly design the remaining functional RIS phase shifts and transmit beamforming to minimize the MCRB, subject to the communication SINR and transmit power constraints. The resulting optimization problem is highly non-convex due to the intricate structure of the MCRB expression and constant-modulus constraint imposed on RIS. To address this, we reformulate it into a more tractable form and propose a block coordinate descent (BCD) algorithm that incorporates majorization-minimization (MM), successive convex approximation (SCA), and penalization techniques. Simulation results demonstrate that our proposed approach reduces the MCRB performance loss by 24.36% on average compared to the case where the presence of faulty elements is ignored. Furthermore, the performance gain becomes more evident as the number of faulty elements increases.
BeamSec: A Practical mmWave Physical Layer Security Scheme Against Strong Adversaries
Sep 19, 2023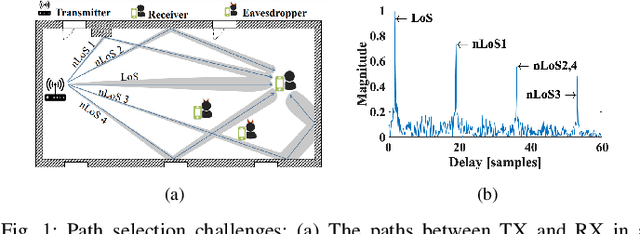
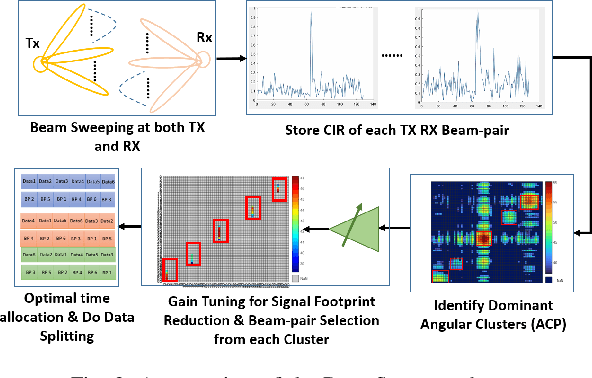
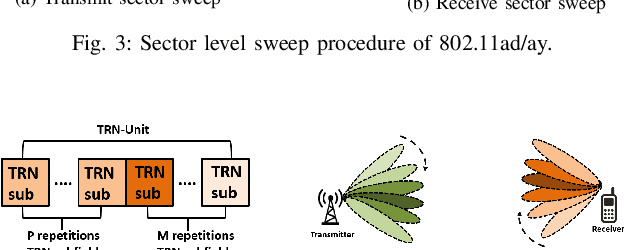
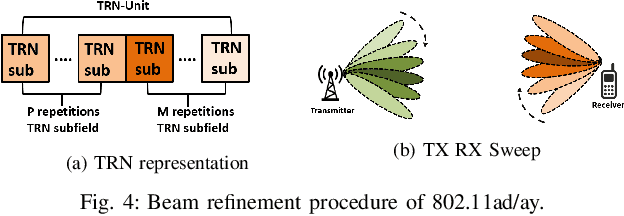
Abstract:The high directionality of millimeter-wave (mmWave) communication systems has proven effective in reducing the attack surface against eavesdropping, thus improving the physical layer security. However, even with highly directional beams, the system is still exposed to eavesdropping against adversaries located within the main lobe. In this paper, we propose \acrshort{BSec}, a solution to protect the users even from adversaries located in the main lobe. The key feature of BeamSec are: (i) Operating without the knowledge of eavesdropper's location/channel; (ii) Robustness against colluding eavesdropping attack and (iii) Standard compatibility, which we prove using experiments via our IEEE 802.11ad/ay-compatible 60 GHz phased-array testbed. Methodologically, BeamSec first identifies uncorrelated and diverse beam-pairs between the transmitter and receiver by analyzing signal characteristics available through standard-compliant procedures. Next, it encodes the information jointly over all selected beam-pairs to minimize information leakage. We study two methods for allocating transmission time among different beams, namely uniform allocation (no knowledge of the wireless channel) and optimal allocation for maximization of the secrecy rate (with partial knowledge of the wireless channel). Our experiments show that \acrshort{BSec} outperforms the benchmark schemes against single and colluding eavesdroppers and enhances the secrecy rate by 79.8% over a random paths selection benchmark.
Sequential Parametric Optimization for Rate-Splitting Precoding in Non-Orthogonal Unicast and Multicast Transmissions
Jan 25, 2022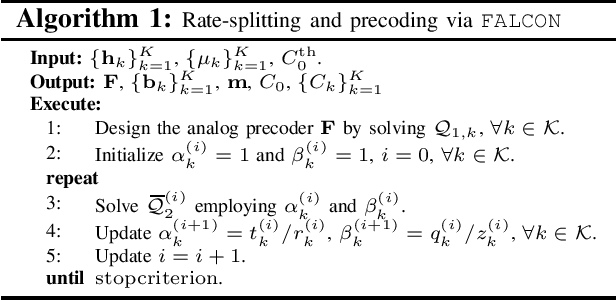
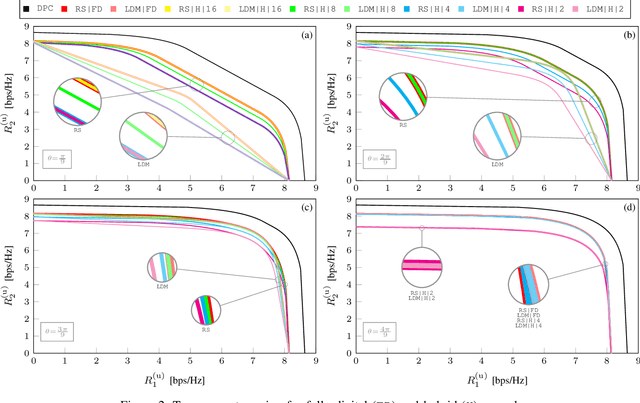
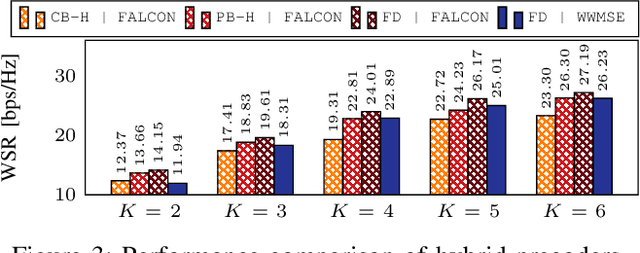
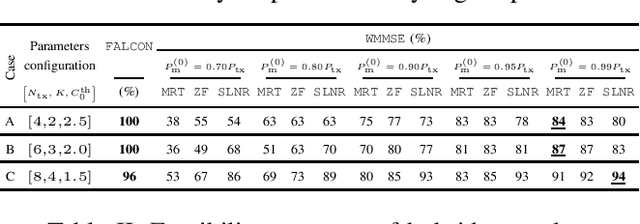
Abstract:This paper investigates rate-splitting (RS) precoding for non-orthogonal unicast and multicast (NOUM) transmissions using fully-digital and hybrid precoders. We study the nonconvex weighted sum-rate (WSR) maximization problem subject to a multicast requirement. We propose FALCON, an approach based on sequential parametric optimization, to solve the aforementioned problem. We show that FALCON converges to a local optimum without requiring judicious selection of an initial feasible point. Besides, we show through simulations that by leveraging RS, hybrid precoders can attain nearly the same performance as their fully-digital counterparts under certain specific settings.
My Armband Leaks Passwords: An EMG and IMU Based Keylogging Side-Channel Attack
Dec 04, 2021
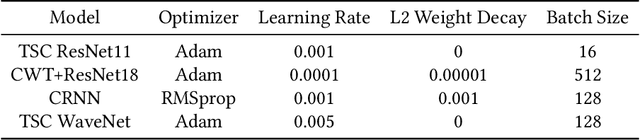

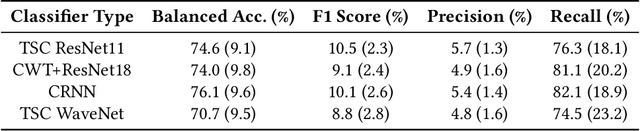
Abstract:Wearables that constantly collect various sensor data of their users increase the chances for inferences of unintentional and sensitive information such as passwords typed on a physical keyboard. We take a thorough look at the potential of using electromyographic (EMG) data, a sensor modality which is new to the market but has lately gained attention in the context of wearables for augmented reality (AR), for a keylogging side-channel attack. Our approach is based on neural networks for a between-subject attack in a realistic scenario using the Myo Armband to collect the sensor data. In our approach, the EMG data has proven to be the most prominent source of information compared to the accelerometer and gyroscope, increasing the keystroke detection performance. For our end-to-end approach on raw data, we report a mean balanced accuracy of about 76 % for the keystroke detection and a mean top-3 key accuracy of about 32 % on 52 classes for the key identification on passwords of varying strengths. We have created an extensive dataset including more than 310 000 keystrokes recorded from 37 volunteers, which is available as open access along with the source code used to create the given results.
* 24 pages, 10 figures, the source code is available at https://github.com/seemoo-lab/myo-keylogging and the dataset is available at https://doi.org/10.5281/zenodo.5594651
BEAMWAVE: Cross-Layer Beamforming and Scheduling for Superimposed Transmissions in Industrial IoT mmWave Networks
Aug 09, 2021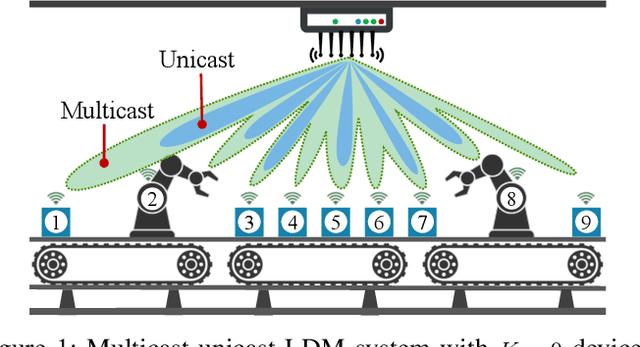
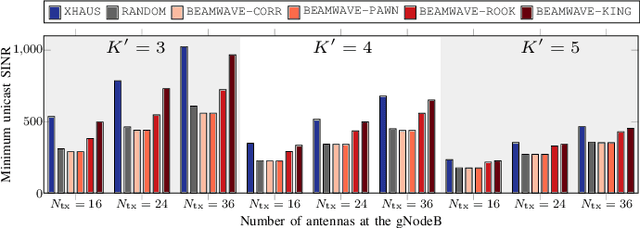
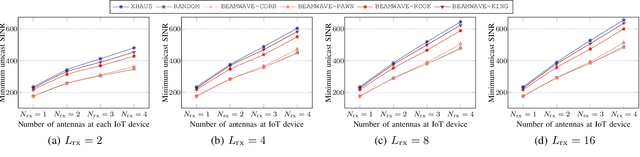

Abstract:The omnipresence of IoT devices in Industry 4.0 is expected to foster higher reliability, safety, and efficiency. However, interconnecting a large number of wireless devices without jeopardizing the system performance proves challenging. To address the requirements of future industries, we investigate the cross-layer design of beamforming and scheduling for layered-division multiplexing (LDM) systems in millimeter-wave bands. Scheduling is crucial as the devices in industrial settings are expected to proliferate rapidly. Also, highly performant beamforming is necessary to ensure scalability. By adopting LDM, multiple transmissions can be non-orthogonally superimposed. Specifically, we consider a superior-importance control multicast message required to be ubiquitous to all devices and inferior-importance private unicast messages targeting a subset of scheduled devices. Due to NP-hardness, we propose BEAMWAVE, which decomposes the problem into beamforming and scheduling. Through simulations, we show that BEAMWAVE attains near-optimality and outperforms other competing schemes.
* 8 pages. Accepted at WiOpt 2021
Perils of Zero-Interaction Security in the Internet of Things
Jan 22, 2019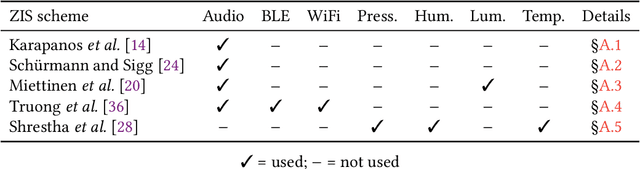
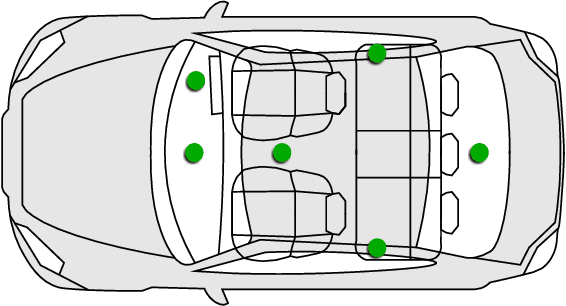
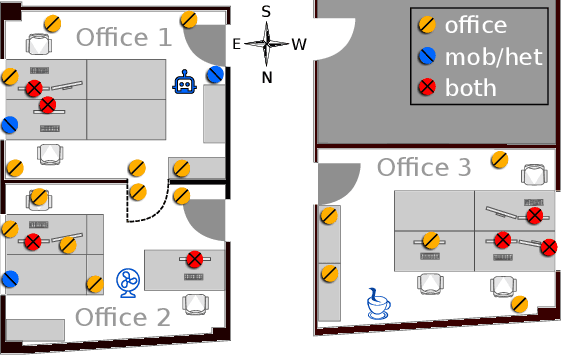
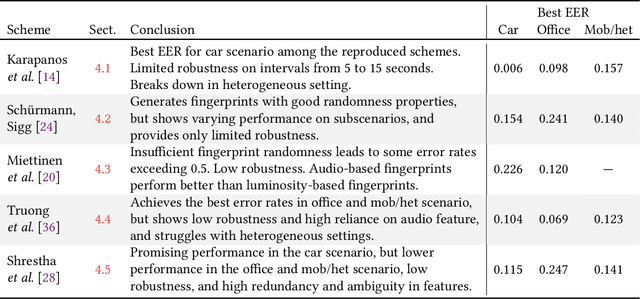
Abstract:The Internet of Things (IoT) demands authentication systems which can provide both security and usability. Recent research utilizes the rich sensing capabilities of smart devices to build security schemes operating without human interaction, such as zero-interaction pairing (ZIP) and zero-interaction authentication (ZIA). Prior work proposed a number of ZIP and ZIA schemes and reported promising results. However, those schemes were often evaluated under conditions which do not reflect realistic IoT scenarios. In addition, drawing any comparison among the existing schemes is impossible due to the lack of a common public dataset and unavailability of scheme implementations. In this paper, we address these challenges by conducting the first large-scale comparative study of ZIP and ZIA schemes, carried out under realistic conditions. We collect and release the most comprehensive dataset in the domain to date, containing over 4250 hours of audio recordings and 1 billion sensor readings from three different scenarios, and evaluate five state-of-the-art schemes based on these data. Our study reveals that the effectiveness of the existing proposals is highly dependent on the scenario they are used in. In particular, we show that these schemes are subject to error rates between 0.6% and 52.8%.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge