Mahmoud Daneshmand
Assessing Text Classification Methods for Cyberbullying Detection on Social Media Platforms
Dec 27, 2024
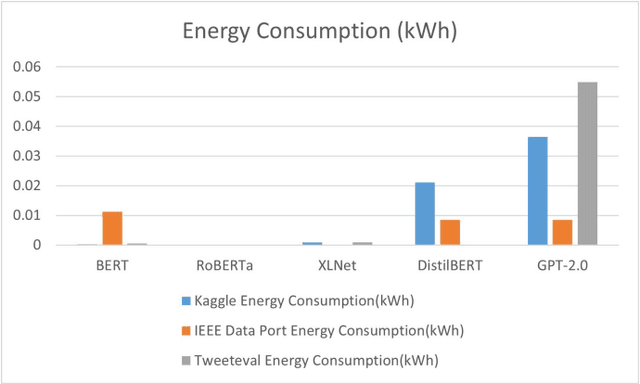
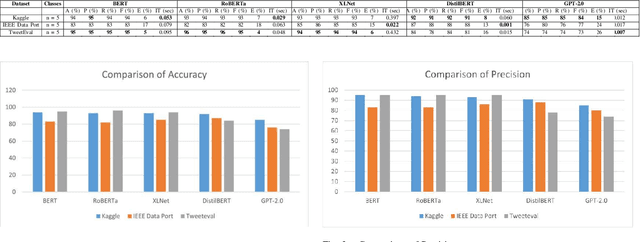
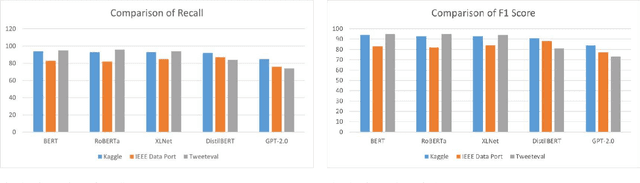
Abstract:Cyberbullying significantly contributes to mental health issues in communities by negatively impacting the psychology of victims. It is a prevalent problem on social media platforms, necessitating effective, real-time detection and monitoring systems to identify harmful messages. However, current cyberbullying detection systems face challenges related to performance, dataset quality, time efficiency, and computational costs. This research aims to conduct a comparative study by adapting and evaluating existing text classification techniques within the cyberbullying detection domain. The study specifically evaluates the effectiveness and performance of these techniques in identifying cyberbullying instances on social media platforms. It focuses on leveraging and assessing large language models, including BERT, RoBERTa, XLNet, DistilBERT, and GPT-2.0, for their suitability in this domain. The results show that BERT strikes a balance between performance, time efficiency, and computational resources: Accuracy of 95%, Precision of 95%, Recall of 95%, F1 Score of 95%, Error Rate of 5%, Inference Time of 0.053 seconds, RAM Usage of 35.28 MB, CPU/GPU Usage of 0.4%, and Energy Consumption of 0.000263 kWh. The findings demonstrate that generative AI models, while powerful, do not consistently outperform fine-tuned models on the tested benchmarks. However, state-of-the-art performance can still be achieved through strategic adaptation and fine-tuning of existing models for specific datasets and tasks.
Chatbots to ChatGPT in a Cybersecurity Space: Evolution, Vulnerabilities, Attacks, Challenges, and Future Recommendations
May 29, 2023Abstract:Chatbots shifted from rule-based to artificial intelligence techniques and gained traction in medicine, shopping, customer services, food delivery, education, and research. OpenAI developed ChatGPT blizzard on the Internet as it crossed one million users within five days of its launch. However, with the enhanced popularity, chatbots experienced cybersecurity threats and vulnerabilities. This paper discussed the relevant literature, reports, and explanatory incident attacks generated against chatbots. Our initial point is to explore the timeline of chatbots from ELIZA (an early natural language processing computer program) to GPT-4 and provide the working mechanism of ChatGPT. Subsequently, we explored the cybersecurity attacks and vulnerabilities in chatbots. Besides, we investigated the ChatGPT, specifically in the context of creating the malware code, phishing emails, undetectable zero-day attacks, and generation of macros and LOLBINs. Furthermore, the history of cyberattacks and vulnerabilities exploited by cybercriminals are discussed, particularly considering the risk and vulnerabilities in ChatGPT. Addressing these threats and vulnerabilities requires specific strategies and measures to reduce the harmful consequences. Therefore, the future directions to address the challenges were presented.
IoT-Enabled Social Relationships Meet Artificial Social Intelligence
Feb 21, 2021



Abstract:With the recent advances of the Internet of Things, and the increasing accessibility of ubiquitous computing resources and mobile devices, the prevalence of rich media contents, and the ensuing social, economic, and cultural changes, computing technology and applications have evolved quickly over the past decade. They now go beyond personal computing, facilitating collaboration and social interactions in general, causing a quick proliferation of social relationships among IoT entities. The increasing number of these relationships and their heterogeneous social features have led to computing and communication bottlenecks that prevent the IoT network from taking advantage of these relationships to improve the offered services and customize the delivered content, known as relationship explosion. On the other hand, the quick advances in artificial intelligence applications in social computing have led to the emerging of a promising research field known as Artificial Social Intelligence (ASI) that has the potential to tackle the social relationship explosion problem. This paper discusses the role of IoT in social relationships detection and management, the problem of social relationships explosion in IoT and reviews the proposed solutions using ASI, including social-oriented machine-learning and deep-learning techniques.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge