Liangmin Wang
Sherman
Chu-ko-nu: A Reliable, Efficient, and Anonymously Authentication-Enabled Realization for Multi-Round Secure Aggregation in Federated Learning
Feb 23, 2024Abstract:Secure aggregation enables federated learning (FL) to perform collaborative training of clients from local gradient updates without exposing raw data. However, existing secure aggregation schemes inevitably perform an expensive fresh setup per round because each client needs to establish fresh input-independent secrets over different rounds. The latest research, Flamingo (S&P 2023), designed a share-transfer-based reusable secret key to support the server continuously performing multiple rounds of aggregation. Nevertheless, the share transfer mechanism it proposed can only be achieved with P probability, which has limited reliability. To tackle the aforementioned problems, we propose a more reliable and anonymously authenticated scheme called Chu-ko-nu for multi-round secure aggregation. Specifically, in terms of share transfer, Chu-ko-nu breaks the probability P barrier by supplementing a redistribution process of secret key components (the sum of all components is the secret key), thus ensuring the reusability of the secret key. Based on this reusable secret key, Chu-ko-nu can efficiently perform consecutive aggregation in the following rounds. Furthermore, considering the client identity authentication and privacy protection issue most approaches ignore, Chu-ko-nu introduces a zero-knowledge proof-based authentication mechanism. It can support clients anonymously participating in FL training and enables the server to authenticate clients effectively in the presence of various attacks. Rigorous security proofs and extensive experiments demonstrated that Chu-ko-nu can provide reliable and anonymously authenticated aggregation for FL with low aggregation costs, at least a 21.02% reduction compared to the state-of-the-art schemes.
Physical Layer Security Assisted Computation Offloading in Intelligently Connected Vehicle Networks
Mar 25, 2022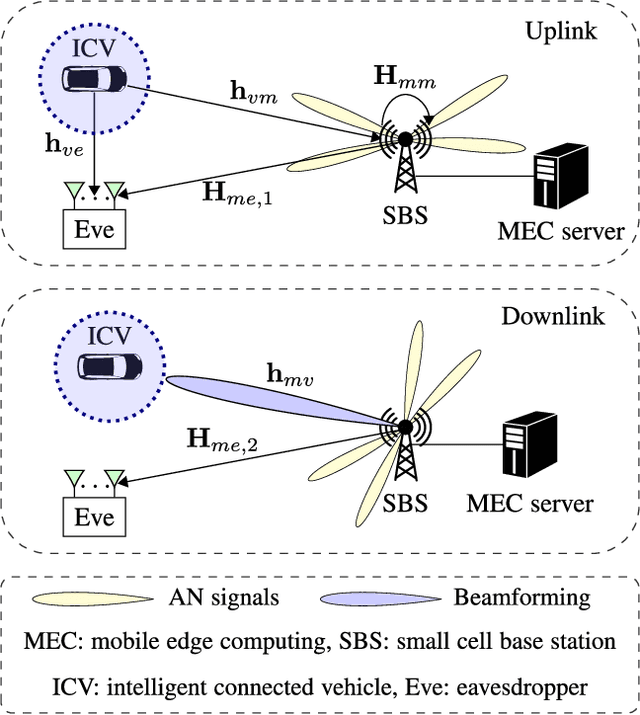
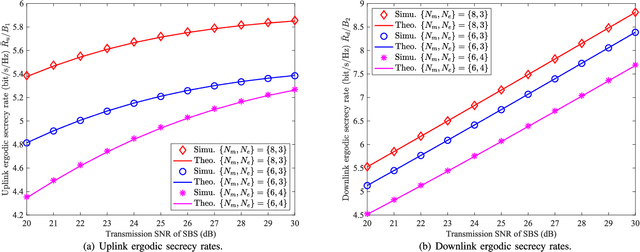
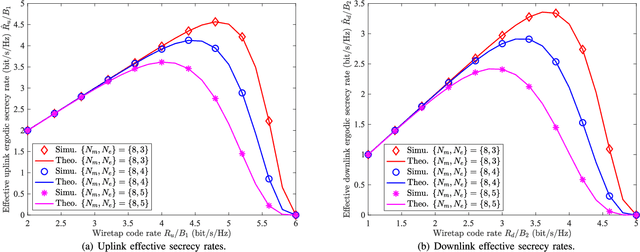
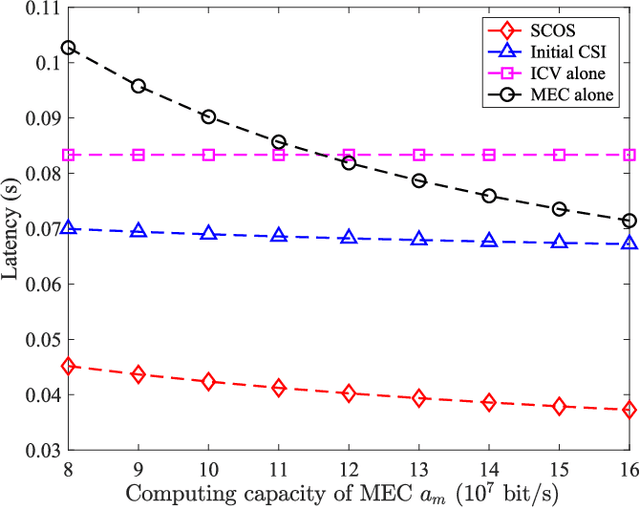
Abstract:In this paper, we propose a secure computation offloading scheme (SCOS) in intelligently connected vehicle (ICV) networks, aiming to minimize overall latency of computing via offloading part of computational tasks to nearby servers in small cell base stations (SBSs), while securing the information delivered during offloading and feedback phases via physical layer security. Existing computation offloading schemes usually neglected time-varying characteristics of channels and their corresponding secrecy rates, resulting in an inappropriate task partition ratio and a large secrecy outage probability. To address these issues, we utilize an ergodic secrecy rate to determine how many tasks are offloaded to the edge, where ergodic secrecy rate represents the average secrecy rate over all realizations in a time-varying wireless channel. Adaptive wiretap code rates are proposed with a secrecy outage constraint to match time-varying wireless channels. In addition, the proposed secure beamforming and artificial noise (AN) schemes can improve the ergodic secrecy rates of uplink and downlink channels even without eavesdropper channel state information (CSI). Numerical results demonstrate that the proposed schemes have a shorter system delay than the strategies neglecting time-varying characteristics.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge