Jinyoung Lee
Text-Aware Adapter for Few-Shot Keyword Spotting
Dec 24, 2024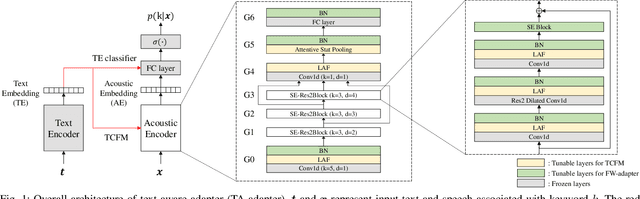
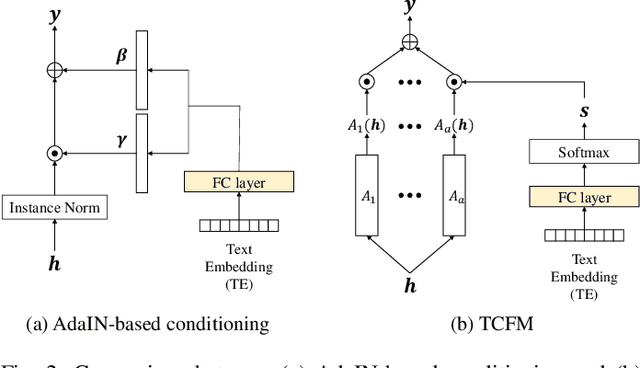
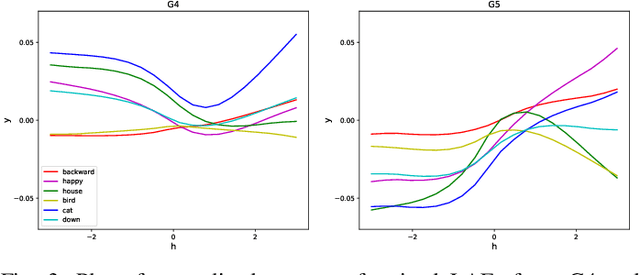
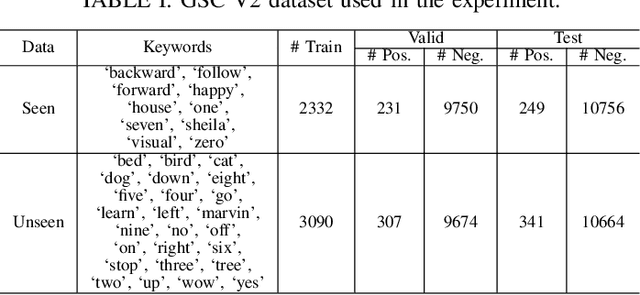
Abstract:Recent advances in flexible keyword spotting (KWS) with text enrollment allow users to personalize keywords without uttering them during enrollment. However, there is still room for improvement in target keyword performance. In this work, we propose a novel few-shot transfer learning method, called text-aware adapter (TA-adapter), designed to enhance a pre-trained flexible KWS model for specific keywords with limited speech samples. To adapt the acoustic encoder, we leverage a jointly pre-trained text encoder to generate a text embedding that acts as a representative vector for the keyword. By fine-tuning only a small portion of the network while keeping the core components' weights intact, the TA-adapter proves highly efficient for few-shot KWS, enabling a seamless return to the original pre-trained model. In our experiments, the TA-adapter demonstrated significant performance improvements across 35 distinct keywords from the Google Speech Commands V2 dataset, with only a 0.14% increase in the total number of parameters.
Multi-User Cooperation for Covert Communication Under Quasi-Static Fading
Apr 10, 2023Abstract:This work studies a covert communication scheme for an uplink multi-user scenario in which some users are opportunistically selected to help a covert user. In particular, the selected users emit interfering signals via an orthogonal resource dedicated to the covert user together with signals for their own communications using orthogonal resources allocated to the selected users, which helps the covert user hide the presence of the covert communication. For the covert communication scheme, we carry out extensive analysis and find system parameters in closed forms. The analytic derivation for the system parameters allow one to find the optimal combination of system parameters by performing a simple one-dimensional search. In addition, the analytic results elucidate relations among the system parameters. In particular, it will be proved that the optimal strategy for the non-covert users is an on-off scheme with equal transmit power. The theoretical results derived in this work are confirmed by comparing them with numerical results obtained with exhaustive searches. Finally, we demonstrate that the results of work can be utilized in versatile ways by demonstrating a design of covert communication with energy efficiency into account.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge