Si-Hyeon Lee
Robust Beamforming and Time Allocation for Time-Division Cell-Free Near-Field ISAC
Jan 19, 2026Abstract:In this paper, we propose a time-division near-field integrated sensing and communication (ISAC) framework for cell-free multiple-input multiple-output (MIMO), where sensing and downlink communication are separated in time. During the sensing phase, user locations are estimated and used to construct location-aware channels, which are then exploited in the subsequent communication phase. By explicitly modeling the coupling between sensing-induced localization errors and channel-estimation errors, we capture the tradeoff between sensing accuracy and communication throughput. Based on this model, we jointly optimize the time-allocation ratio, sensing covariance matrix, and robust downlink beamforming under imperfect channel state information (CSI). The resulting non-convex problem is addressed via a semidefinite programming (SDP)-based reformulation within an alternating-optimization framework. To further reduce computational complexity, we also propose two low-complexity suboptimal designs: an error-ignorant scheme and a maximum ratio transmission (MRT)-based scheme. Simulation results show that the proposed scheme significantly improves localization accuracy over far-field and monostatic setups, thereby reducing channel estimation errors and ultimately enhancing the achievable rate. Moreover, the error-ignorant scheme performs well under stringent sensing requirements, whereas the MRT-based scheme remains robust over a wide range of sensing requirements by adapting the time-allocation ratio, albeit with some beamforming loss.
Provably Near-Optimal Federated Ensemble Distillation with Negligible Overhead
Feb 10, 2025



Abstract:Federated ensemble distillation addresses client heterogeneity by generating pseudo-labels for an unlabeled server dataset based on client predictions and training the server model using the pseudo-labeled dataset. The unlabeled server dataset can either be pre-existing or generated through a data-free approach. The effectiveness of this approach critically depends on the method of assigning weights to client predictions when creating pseudo-labels, especially in highly heterogeneous settings. Inspired by theoretical results from GANs, we propose a provably near-optimal weighting method that leverages client discriminators trained with a server-distributed generator and local datasets. Our experiments on various image classification tasks demonstrate that the proposed method significantly outperforms baselines. Furthermore, we show that the additional communication cost, client-side privacy leakage, and client-side computational overhead introduced by our method are negligible, both in scenarios with and without a pre-existing server dataset.
Exactly Minimax-Optimal Locally Differentially Private Sampling
Oct 30, 2024Abstract:The sampling problem under local differential privacy has recently been studied with potential applications to generative models, but a fundamental analysis of its privacy-utility trade-off (PUT) remains incomplete. In this work, we define the fundamental PUT of private sampling in the minimax sense, using the f-divergence between original and sampling distributions as the utility measure. We characterize the exact PUT for both finite and continuous data spaces under some mild conditions on the data distributions, and propose sampling mechanisms that are universally optimal for all f-divergences. Our numerical experiments demonstrate the superiority of our mechanisms over baselines, in terms of theoretical utilities for finite data space and of empirical utilities for continuous data space.
Trajectory Optimization for Cellular-Enabled UAV with Connectivity and Battery Constraints
Jul 30, 2023Abstract:In this paper, we address the problem of path planning for a cellular-enabled UAV with connectivity and battery constraints. The UAV's mission is to deliver a payload from an initial point to a final point, while maintaining connectivity with a BS and adhering to the battery constraint. The UAV's battery can be replaced by a fully charged battery at a charging station, which takes some time. Our key contribution lies in proposing an algorithm that efficiently computes an optimal path that minimizes the mission completion time, solvable in polynomial time. We achieve this by transforming the problem into an equivalent two-level shortest path finding problem over weighted graphs and leveraging graph theoretic approaches to solve it. In more detail, we first find an optimal path and speed to travel between each pair of charging stations without replacing the battery, and then find the optimal order of visiting charging stations. To demonstrate the effectiveness of our approach, we compare it with previously proposed algorithms and show that our algorithm outperforms those in terms of both computational complexity and performance.
Multi-User Cooperation for Covert Communication Under Quasi-Static Fading
Apr 10, 2023Abstract:This work studies a covert communication scheme for an uplink multi-user scenario in which some users are opportunistically selected to help a covert user. In particular, the selected users emit interfering signals via an orthogonal resource dedicated to the covert user together with signals for their own communications using orthogonal resources allocated to the selected users, which helps the covert user hide the presence of the covert communication. For the covert communication scheme, we carry out extensive analysis and find system parameters in closed forms. The analytic derivation for the system parameters allow one to find the optimal combination of system parameters by performing a simple one-dimensional search. In addition, the analytic results elucidate relations among the system parameters. In particular, it will be proved that the optimal strategy for the non-covert users is an on-off scheme with equal transmit power. The theoretical results derived in this work are confirmed by comparing them with numerical results obtained with exhaustive searches. Finally, we demonstrate that the results of work can be utilized in versatile ways by demonstrating a design of covert communication with energy efficiency into account.
Anti-Jamming Games for Multi-User Multi-Band Networks
Nov 11, 2021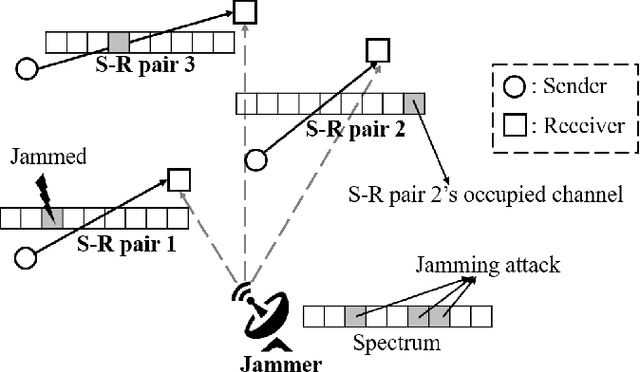
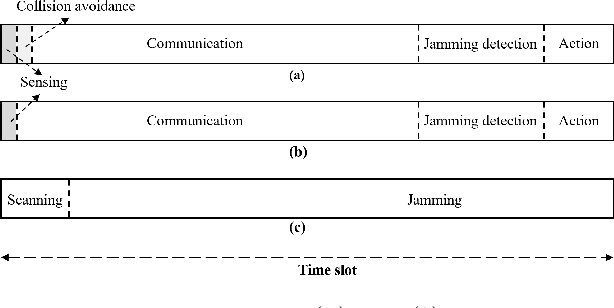
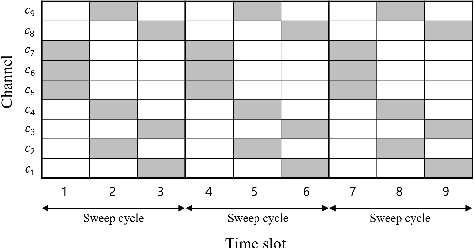
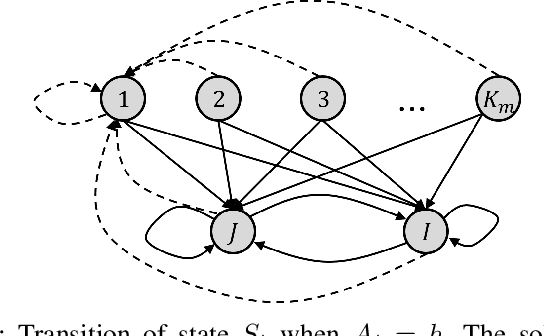
Abstract:For multi-user multi-band networks, a zero-sum game between the users and the jammer is considered. In the formulation of the game, the rewards of the users are modeled with various parameters including communication rate, hopping cost, and jamming loss. It is analytically shown that for any symmetric collision avoidance protocol, a staying-threshold frequency hopping and a sweeping attack establish an equilibrium. We also propose two kinds of collision avoidance protocols to ensure that at most one user communicates in a band, and provide various numerical results that show the effect of the reward parameters and collision avoidance protocols on the optimal threshold of the staying-threshold frequency hopping and the expected rewards of the users.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge