Hamidreza Jafarnejadsani
Multi-Robot Coordination with Adversarial Perception
Apr 12, 2025Abstract:This paper investigates the resilience of perception-based multi-robot coordination with wireless communication to online adversarial perception. A systematic study of this problem is essential for many safety-critical robotic applications that rely on the measurements from learned perception modules. We consider a (small) team of quadrotor robots that rely only on an Inertial Measurement Unit (IMU) and the visual data measurements obtained from a learned multi-task perception module (e.g., object detection) for downstream tasks, including relative localization and coordination. We focus on a class of adversarial perception attacks that cause misclassification, mislocalization, and latency. We propose that the effects of adversarial misclassification and mislocalization can be modeled as sporadic (intermittent) and spurious measurement data for the downstream tasks. To address this, we present a framework for resilience analysis of multi-robot coordination with adversarial measurements. The framework integrates data from Visual-Inertial Odometry (VIO) and the learned perception model for robust relative localization and state estimation in the presence of adversarially sporadic and spurious measurements. The framework allows for quantifying the degradation in system observability and stability in relation to the success rate of adversarial perception. Finally, experimental results on a multi-robot platform demonstrate the real-world applicability of our methodology for resource-constrained robotic platforms.
Distributed Detection of Adversarial Attacks for Resilient Cooperation of Multi-Robot Systems with Intermittent Communication
Oct 06, 2024Abstract:This paper concerns the consensus and formation of a network of mobile autonomous agents in adversarial settings where a group of malicious (compromised) agents are subject to deception attacks. In addition, the communication network is arbitrarily time-varying and subject to intermittent connections, possibly imposed by denial-of-service (DoS) attacks. We provide explicit bounds for network connectivity in an integral sense, enabling the characterization of the system's resilience to specific classes of adversarial attacks. We also show that under the condition of connectivity in an integral sense uniformly in time, the system is finite-gain $\mathcal{L}_{p}$ stable and uniformly exponentially fast consensus and formation are achievable, provided malicious agents are detected and isolated from the network. We present a distributed and reconfigurable framework with theoretical guarantees for detecting malicious agents, allowing for the resilient cooperation of the remaining cooperative agents. Simulation studies are provided to illustrate the theoretical findings.
Learning When to Use Adaptive Adversarial Image Perturbations against Autonomous Vehicles
Dec 28, 2022Abstract:The deep neural network (DNN) models for object detection using camera images are widely adopted in autonomous vehicles. However, DNN models are shown to be susceptible to adversarial image perturbations. In the existing methods of generating the adversarial image perturbations, optimizations take each incoming image frame as the decision variable to generate an image perturbation. Therefore, given a new image, the typically computationally-expensive optimization needs to start over as there is no learning between the independent optimizations. Very few approaches have been developed for attacking online image streams while considering the underlying physical dynamics of autonomous vehicles, their mission, and the environment. We propose a multi-level stochastic optimization framework that monitors an attacker's capability of generating the adversarial perturbations. Based on this capability level, a binary decision attack/not attack is introduced to enhance the effectiveness of the attacker. We evaluate our proposed multi-level image attack framework using simulations for vision-guided autonomous vehicles and actual tests with a small indoor drone in an office environment. The results show our method's capability to generate the image attack in real-time while monitoring when the attacker is proficient given state estimates.
Multi-level Adaptation for Automatic Landing with Engine Failure under Turbulent Weather
Sep 09, 2022
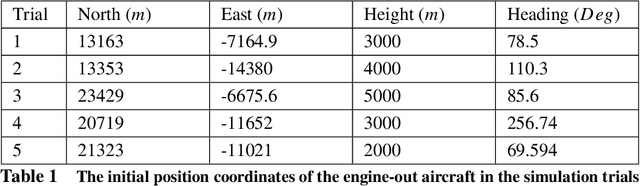
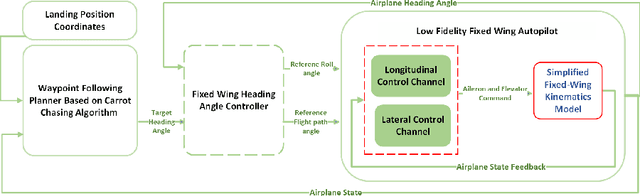
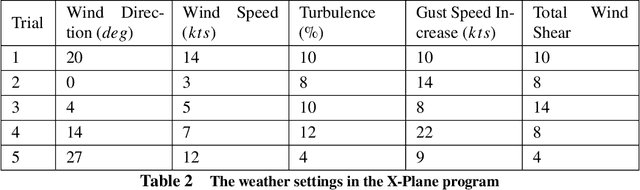
Abstract:This paper addresses efficient feasibility evaluation of possible emergency landing sites, online navigation, and path following for automatic landing under engine-out failure subject to turbulent weather. The proposed Multi-level Adaptive Safety Control framework enables unmanned aerial vehicles (UAVs) under large uncertainties to perform safety maneuvers traditionally reserved for human pilots with sufficient experience. In this framework, a simplified flight model is first used for time-efficient feasibility evaluation of a set of landing sites and trajectory generation. Then, an online path following controller is employed to track the selected landing trajectory. We used a high-fidelity simulation environment for a fixed-wing aircraft to test and validate the proposed approach under various weather uncertainties. For the case of emergency landing due to engine failure under severe weather conditions, the simulation results show that the proposed automatic landing framework is robust to uncertainties and adaptable at different landing stages while being computationally inexpensive for planning and tracking tasks.
A Modular Continuum Manipulator for Aerial Manipulation and Perching
Jun 13, 2022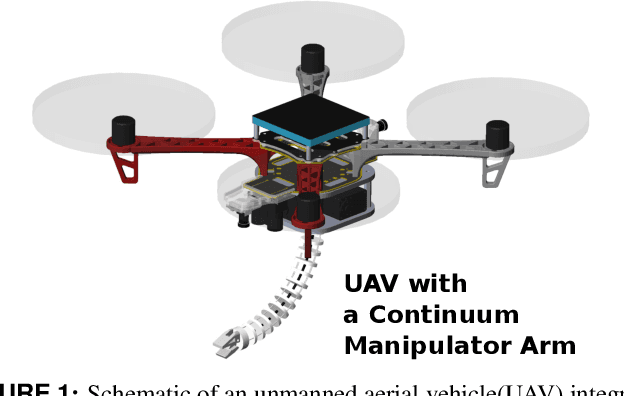
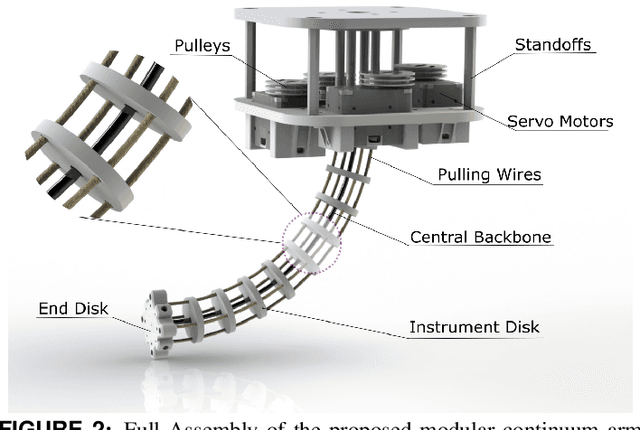
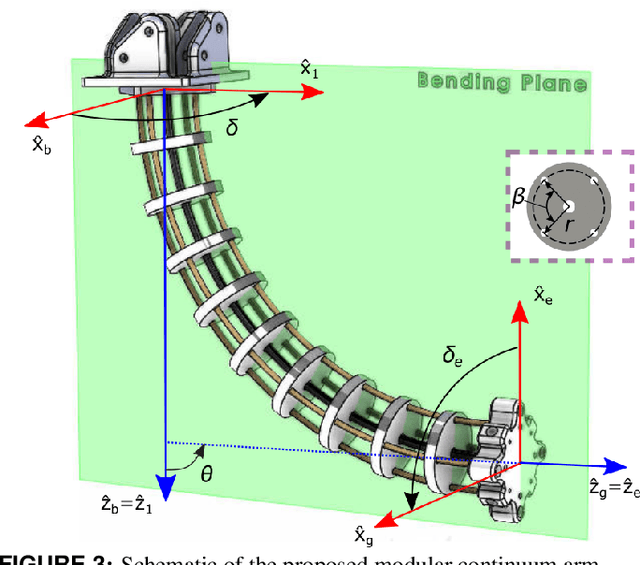
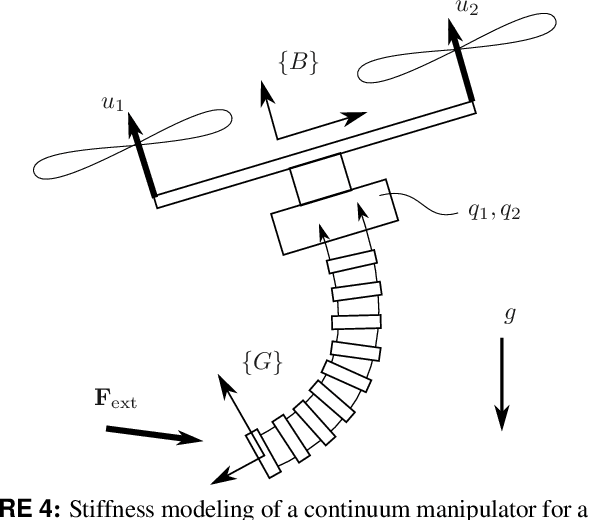
Abstract:Most aerial manipulators use serial rigid-link designs, which results in large forces when initiating contacts during manipulation and could cause flight stability difficulty. This limitation could potentially be improved by the compliance of continuum manipulators. To achieve this goal, we present the novel design of a compact, lightweight, and modular cable-driven continuum manipulator for aerial drones. We then derive a complete modeling framework for its kinematics, statics, and stiffness (compliance). The framework is essential for integrating the manipulator to aerial drones. Finally, we report preliminary experimental validations of the hardware prototype, providing insights on its manipulation feasibility. Future work includes the integration and test of the proposed continuum manipulator with aerial drones.
Detection of Stealthy Adversaries for Networked Unmanned Aerial Vehicles
Feb 19, 2022



Abstract:A network of unmanned aerial vehicles (UAVs) provides distributed coverage, reconfigurability, and maneuverability in performing complex cooperative tasks. However, it relies on wireless communications that can be susceptible to cyber adversaries and intrusions, disrupting the entire network's operation. This paper develops model-based centralized and decentralized observer techniques for detecting a class of stealthy intrusions, namely zero-dynamics and covert attacks, on networked UAVs in formation control settings. The centralized observer that runs in a control center leverages switching in the UAVs' communication topology for attack detection, and the decentralized observers, implemented onboard each UAV in the network, use the model of networked UAVs and locally available measurements. Experimental results are provided to show the effectiveness of the proposed detection schemes in different case studies.
Learning Image Attacks toward Vision Guided Autonomous Vehicles
May 17, 2021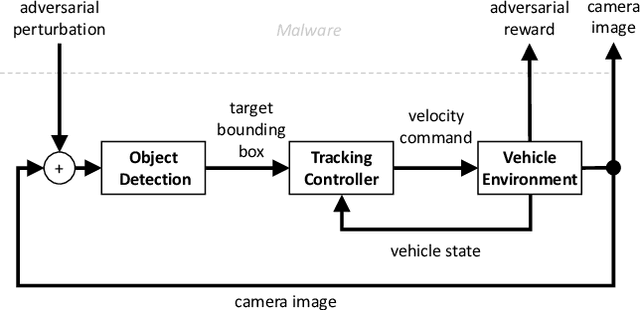
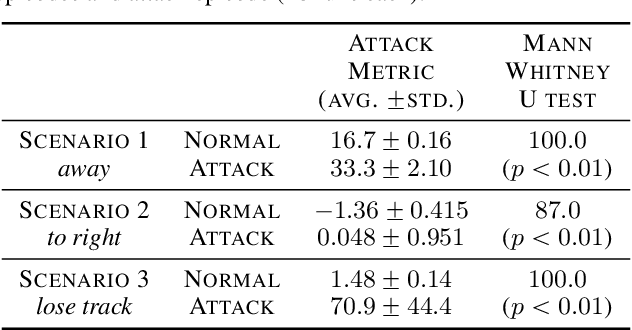
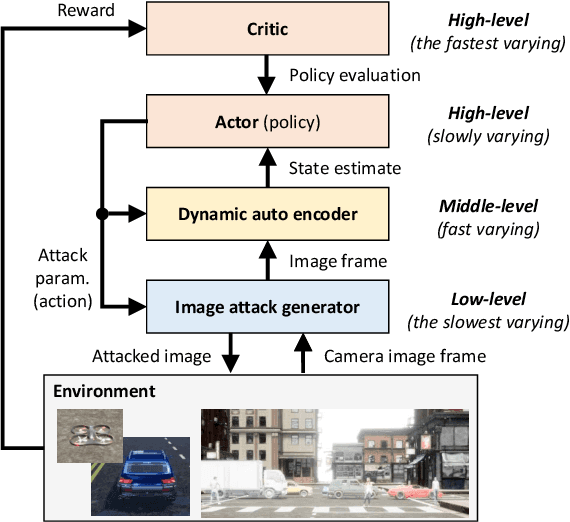

Abstract:While adversarial neural networks have been shown successful for static image attacks, very few approaches have been developed for attacking online image streams while taking into account the underlying physical dynamics of autonomous vehicles, their mission, and environment. This paper presents an online adversarial machine learning framework that can effectively misguide autonomous vehicles' missions. In the existing image attack methods devised toward autonomous vehicles, optimization steps are repeated for every image frame. This framework removes the need for fully converged optimization at every frame to realize image attacks in real-time. Using reinforcement learning, a generative neural network is trained over a set of image frames to obtain an attack policy that is more robust to dynamic and uncertain environments. A state estimator is introduced for processing image streams to reduce the attack policy's sensitivity to physical variables such as unknown position and velocity. A simulation study is provided to validate the results.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge