Valentina E. Balas
Fault Tolerance of Neural Networks in Adversarial Settings
Oct 30, 2019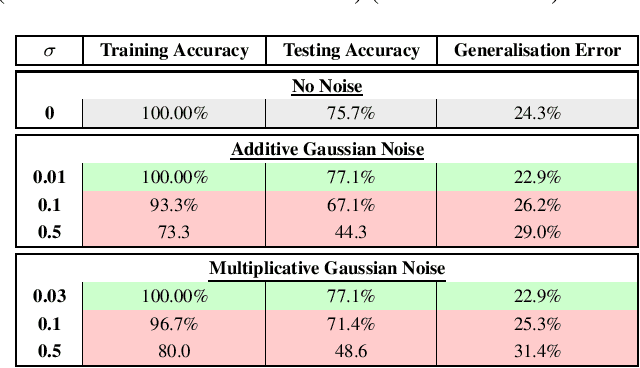
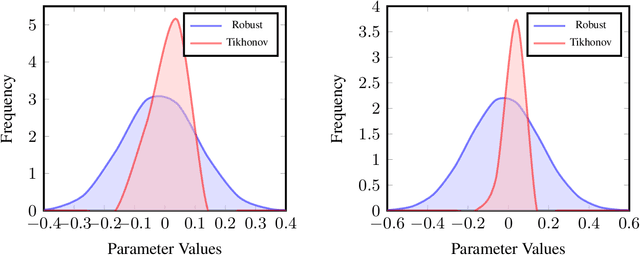
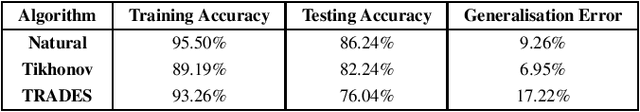
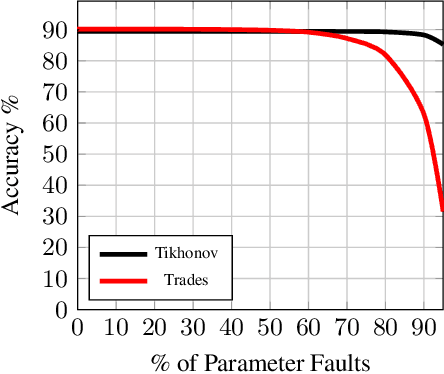
Abstract:Artificial Intelligence systems require a through assessment of different pillars of trust, namely, fairness, interpretability, data and model privacy, reliability (safety) and robustness against against adversarial attacks. While these research problems have been extensively studied in isolation, an understanding of the trade-off between different pillars of trust is lacking. To this extent, the trade-off between fault tolerance, privacy and adversarial robustness is evaluated for the specific case of Deep Neural Networks, by considering two adversarial settings under a security and a privacy threat model. Specifically, this work studies the impact of the fault tolerance of the Neural Network on training the model by adding noise to the input (Adversarial Robustness) and noise to the gradients (Differential Privacy). While training models with noise to inputs, gradients or weights enhances fault tolerance, it is observed that adversarial robustness and fault tolerance are at odds with each other. On the other hand, ($\epsilon,\delta$)-Differentially Private models enhance the fault tolerance, measured using generalisation error, theoretically has an upper bound of $e^{\epsilon} - 1 + \delta$. This novel study of the trade-off between different elements of trust is pivotal for training a model which satisfies the requirements for different pillars of trust simultaneously.
Adversarial Fault Tolerant Training for Deep Neural Networks
Jul 09, 2019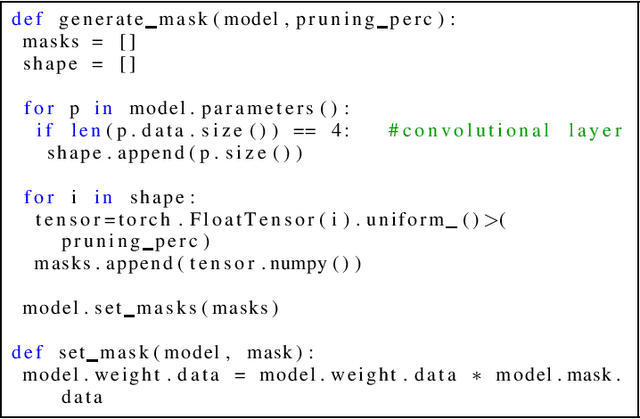
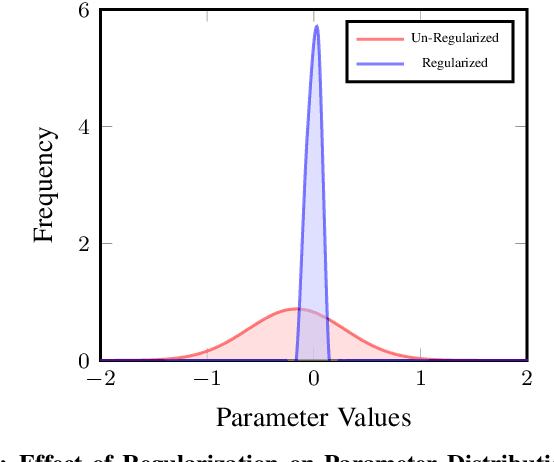
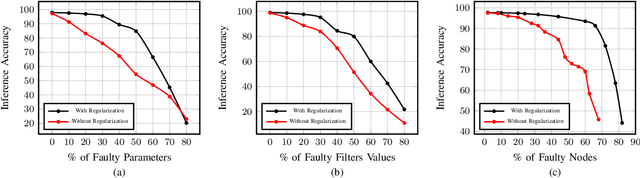
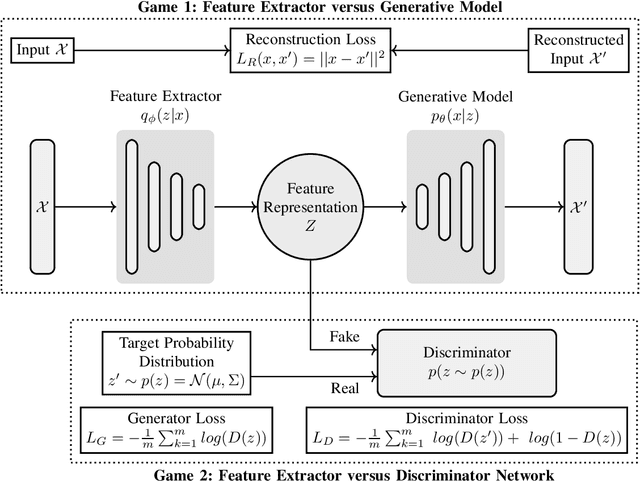
Abstract:Deep Learning Accelerators are prone to faults which manifest in the form of errors in Neural Networks. Fault Tolerance in Neural Networks is crucial in real-time safety critical applications requiring computation for long durations. Neural Networks with high regularisation exhibit superior fault tolerance, however, at the cost of classification accuracy. In the view of difference in functionality, a Neural Network is modelled as two separate networks, i.e, the Feature Extractor with unsupervised learning objective and the Classifier with a supervised learning objective. Traditional approaches of training the entire network using a single supervised learning objective is insufficient to achieve the objectives of the individual components optimally. In this work, a novel multi-criteria objective function, combining unsupervised training of the Feature Extractor followed by supervised tuning with Classifier Network is proposed. The unsupervised training solves two games simultaneously in the presence of adversary neural networks with conflicting objectives to the Feature Extractor. The first game minimises the loss in reconstructing the input image for indistinguishability given the features from the Extractor, in the presence of a generative decoder. The second game solves a minimax constraint optimisation for distributional smoothening of feature space to match a prior distribution, in the presence of a Discriminator network. The resultant strongly regularised Feature Extractor is combined with the Classifier Network for supervised fine-tuning. The proposed Adversarial Fault Tolerant Neural Network Training is scalable to large networks and is independent of the architecture. The evaluation on benchmarking datasets: FashionMNIST and CIFAR10, indicates that the resultant networks have high accuracy with superior tolerance to stuck at "0" faults compared to widely used regularisers.
Stealing Neural Networks via Timing Side Channels
Dec 31, 2018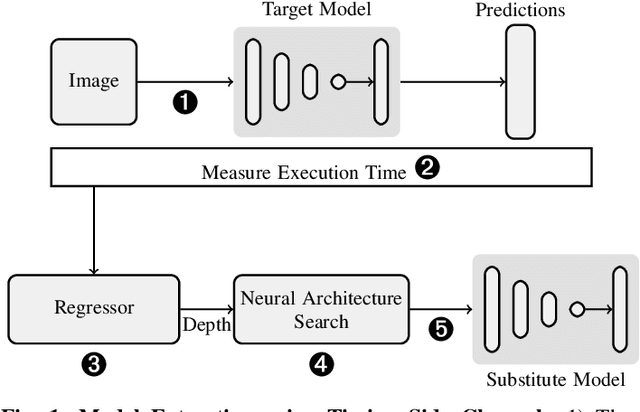
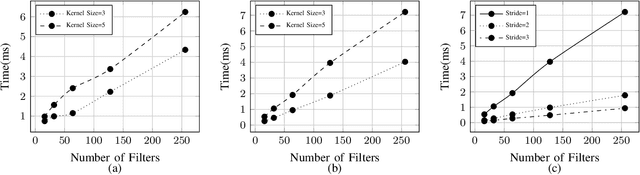
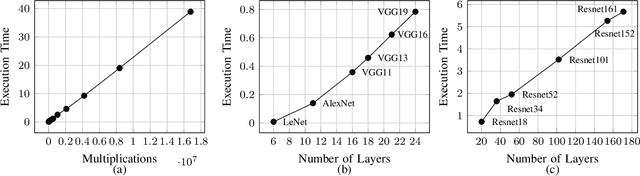
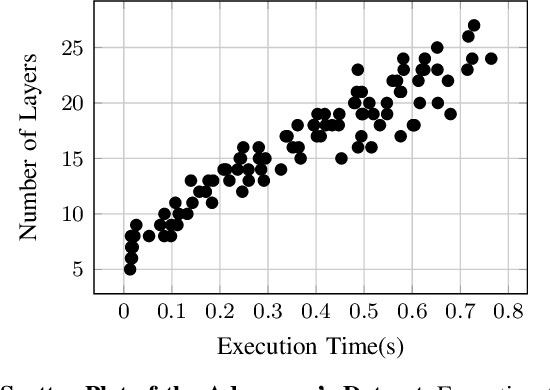
Abstract:Deep learning is gaining importance in many applications and Cloud infrastructures are being advocated for this computational paradigm. However, there is a security issue which is yet to be addressed. An adversary can extract the neural network architecture for commercial gain. Given the architecture, an adversary can further infer the regularization hyperparameter, input data and generate effective transferable adversarial examples to evade classifiers. We observe that neural networks are vulnerable to timing side channel attacks as the total execution time of the network is dependent on the network depth due to the sequential computation of the layers. In this paper, black box neural network extraction attack by exploiting the timing side channels to infer the depth of the network has been proposed. The proposed approach is independent of the neural network architecture and scalable. Reconstructing substitute architectures with similar functionality as the target model is a search problem. The depth inferred from exploiting the timing side channel reduces the search space. Further, reinforcement learning with knowledge distillation is used to efficiently search for the optimal substitute architecture in the complex yet reduced search space. We evaluate our attack on VGG architectures on CIFAR10 dataset and reconstruct substitute models with test accuracy close to the target models.
The Biometric Menagerie - A Fuzzy and Inconsistent Concept
Sep 27, 2012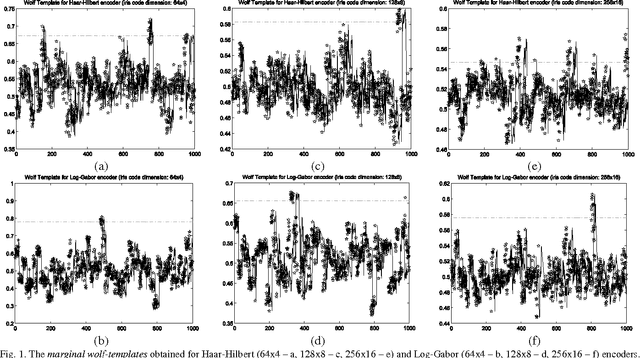
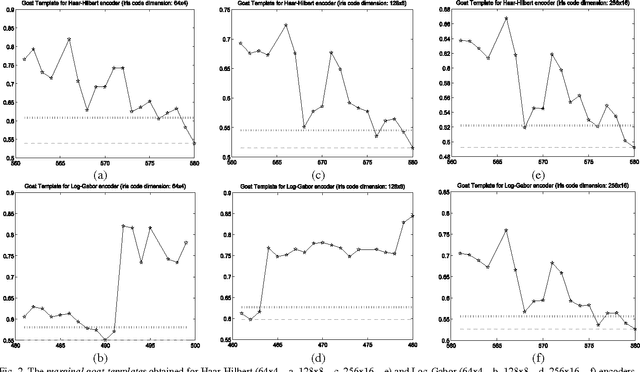
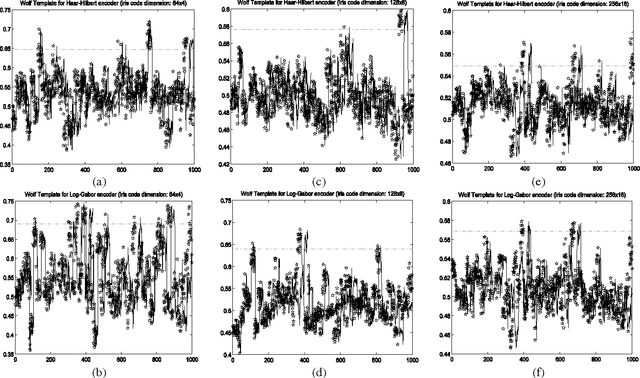
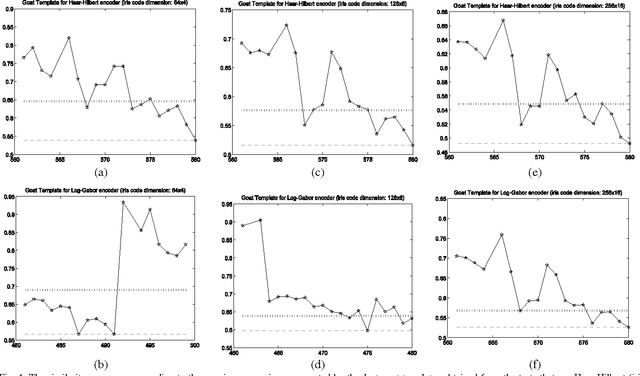
Abstract:This paper proves that in iris recognition, the concepts of sheep, goats, lambs and wolves - as proposed by Doddington and Yager in the so-called Biometric Menagerie, are at most fuzzy and at least not quite well defined. They depend not only on the users or on their biometric templates, but also on the parameters that calibrate the iris recognition system. This paper shows that, in the case of iris recognition, the extensions of these concepts have very unsharp and unstable (non-stationary) boundaries. The membership of a user to these categories is more often expressed as a degree (as a fuzzy value) rather than as a crisp value. Moreover, they are defined by fuzzy Sugeno rules instead of classical (crisp) definitions. For these reasons, we said that the Biometric Menagerie proposed by Doddington and Yager could be at most a fuzzy concept of biometry, but even this status is conditioned by improving its definition. All of these facts are confirmed experimentally in a series of 12 exhaustive iris recognition tests undertaken for University of Bath Iris Image Database while using three different iris code dimensions (256x16, 128x8 and 64x4), two different iris texture encoders (Log-Gabor and Haar-Hilbert) and two different types of safety models.
Combined Haar-Hilbert and Log-Gabor Based Iris Encoders
Feb 08, 2012



Abstract:This chapter shows that combining Haar-Hilbert and Log-Gabor improves iris recognition performance leading to a less ambiguous biometric decision landscape in which the overlap between the experimental intra- and interclass score distributions diminishes or even vanishes. Haar-Hilbert, Log-Gabor and combined Haar-Hilbert and Log-Gabor encoders are tested here both for single and dual iris approach. The experimental results confirm that the best performance is obtained for the dual iris approach when the iris code is generated using the combined Haar-Hilbert and Log-Gabor encoder, and when the matching score fuses the information from both Haar-Hilbert and Log-Gabor channels of the combined encoder.
Exploratory simulation of an Intelligent Iris Verifier Distributed System
Jun 18, 2011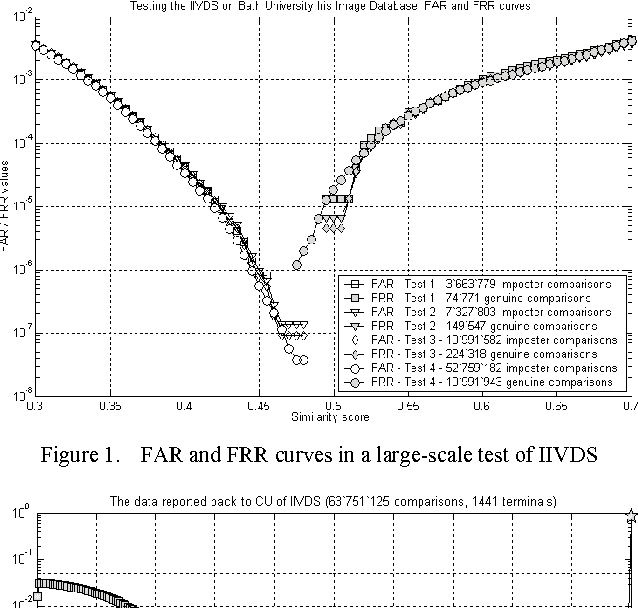
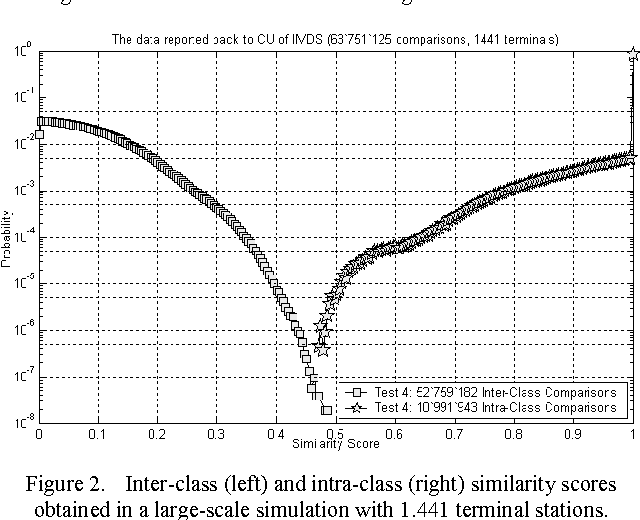
Abstract:This paper discusses some topics related to the latest trends in the field of evolutionary approaches to iris recognition. It presents the results of an exploratory experimental simulation whose goal was to analyze the possibility of establishing an Interchange Protocol for Digital Identities evolved in different geographic locations interconnected through and into an Intelligent Iris Verifier Distributed System (IIVDS) based on multi-enrollment. Finding a logically consistent model for the Interchange Protocol is the key factor in designing the future large-scale iris biometric networks. Therefore, the logical model of such a protocol is also investigated here. All tests are made on Bath Iris Database and prove that outstanding power of discrimination between the intra- and the inter-class comparisons can be achieved by an IIVDS, even when practicing 52.759.182 inter-class and 10.991.943 intra-class comparisons. Still, the test results confirm that inconsistent enrollment can change the logic of recognition from a fuzzified 2-valent consistent logic of biometric certitudes to a fuzzified 3-valent inconsistent possibilistic logic of biometric beliefs justified through experimentally determined probabilities, or to a fuzzified 8-valent logic which is almost consistent as a biometric theory - this quality being counterbalanced by an absolutely reasonable loss in the user comfort level.
* 4 pages, 2 figures, latest version: http://fmi.spiruharet.ro/bodorin/
From Cognitive Binary Logic to Cognitive Intelligent Agents
Jun 18, 2011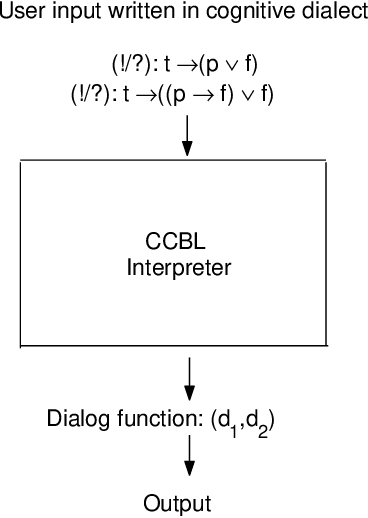
Abstract:The relation between self awareness and intelligence is an open problem these days. Despite the fact that self awarness is usually related to Emotional Intelligence, this is not the case here. The problem described in this paper is how to model an agent which knows (Cognitive) Binary Logic and which is also able to pass (without any mistake) a certain family of Turing Tests designed to verify its knowledge and its discourse about the modal states of truth corresponding to well-formed formulae within the language of Propositional Binary Logic.
* 3 figures, 4 pages, latest version: http://fmi.spiruharet.ro/bodorin/
Comparing Haar-Hilbert and Log-Gabor Based Iris Encoders on Bath Iris Image Database
Jun 12, 2011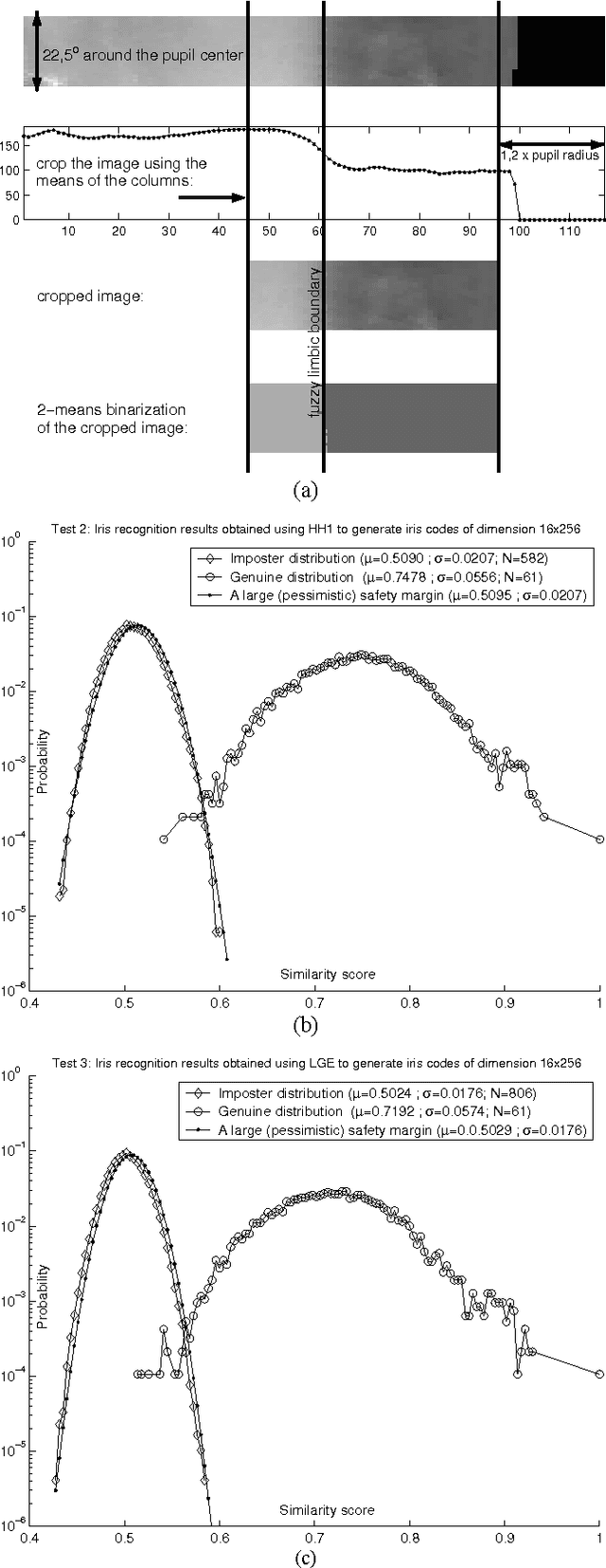
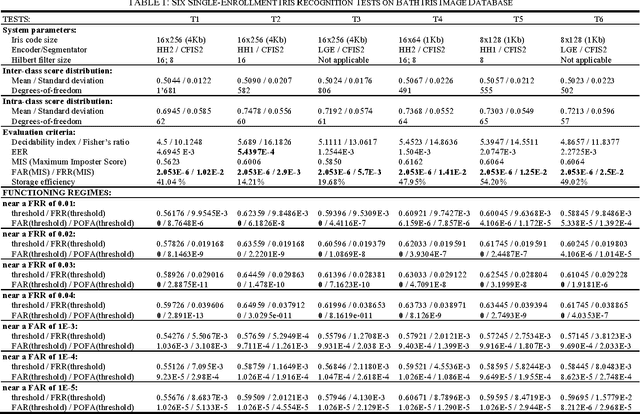
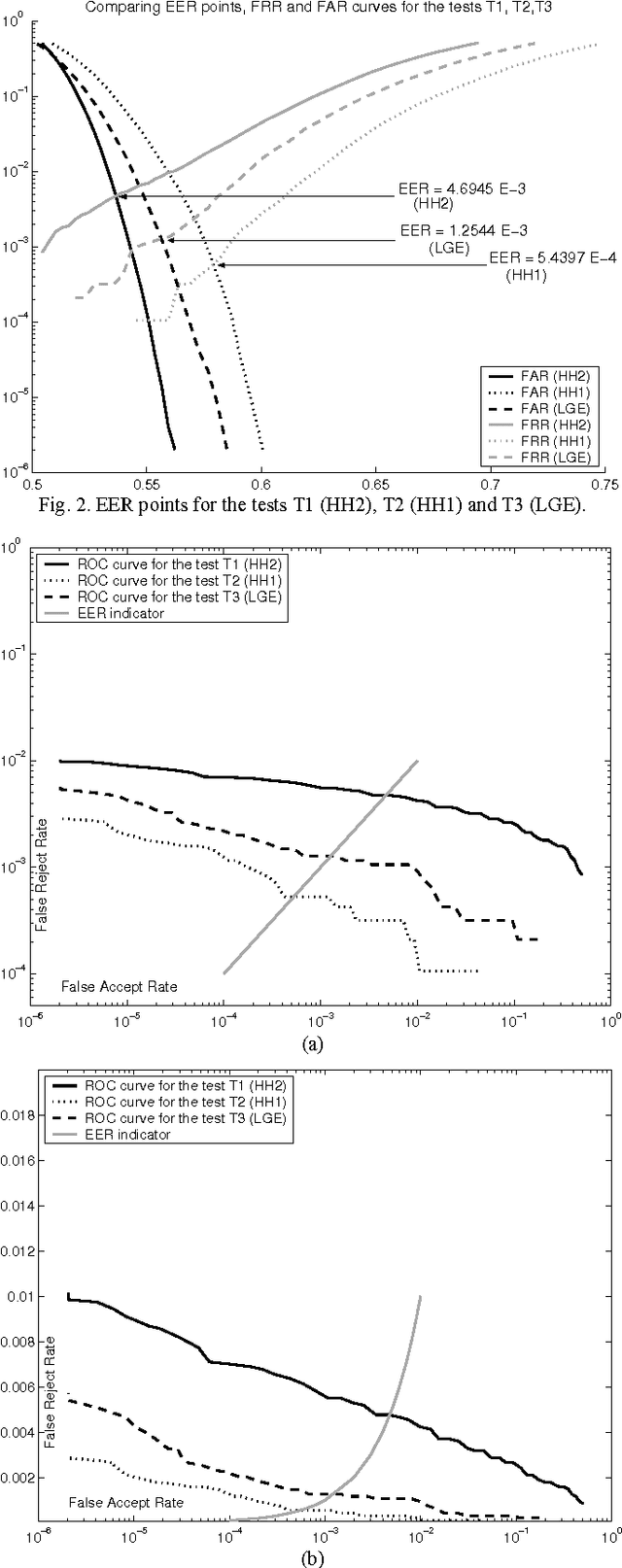
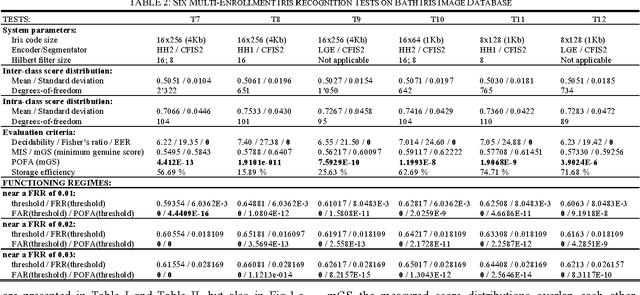
Abstract:This papers introduces a new family of iris encoders which use 2-dimensional Haar Wavelet Transform for noise attenuation, and Hilbert Transform to encode the iris texture. In order to prove the usefulness of the newly proposed iris encoding approach, the recognition results obtained by using these new encoders are compared to those obtained using the classical Log- Gabor iris encoder. Twelve tests involving single/multienrollment and conducted on Bath Iris Image Database are presented here. One of these tests achieves an Equal Error Rate comparable to the lowest value reported so far for this database. New Matlab tools for iris image processing are also released together with this paper: a second version of the Circular Fuzzy Iris Segmentator (CFIS2), a fast Log-Gabor encoder and two Haar-Hilbert based encoders.
* 6 pages, 4 figures, latest version: http://fmi.spiruharet.ro/bodorin/
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge