Tien Ngoc Ha
Radio Maps for Beam Alignment in mmWave Communications with Location Uncertainty
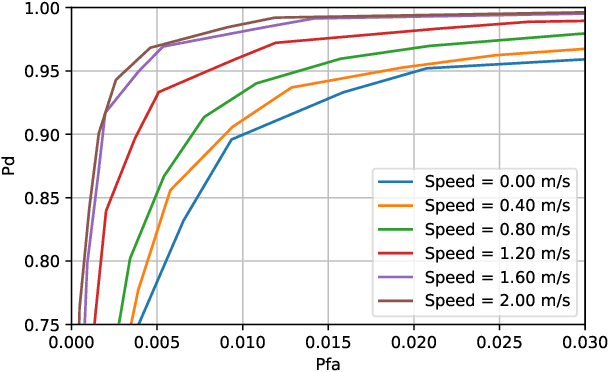
Feb 25, 2024Abstract:Next generation communication systems require accurate beam alignment to counteract the impairments that characterize propagation in high-frequency bands. The overhead of the pilot sequences required to select the best beam pair is prohibitive when codebooks contain a large number of beams, as is the case in practice. To remedy this issue, some schemes exploit information about the user location to predict the best beam pair. However, these schemes (i) involve no measurements whatsoever, which generally results in a highly suboptimal predicted beam, and (ii) are not robust to localization errors. To address these limitations, this paper builds upon the notion of radio map to develop two algorithms that attain a balance between the quality of the obtained beam pair and measurement overhead. The proposed algorithms predict the received power corresponding to each pair and measure just the Q pairs with highest prediction. While the first algorithm targets simplicity, the second one relies on a Bayesian approach to endow the prediction process with robustness to localization error. The performance of both algorithms is shown to widely outperform existing methods using ray-tracing data.
Spoofing Detection in the Physical Layer with Graph Neural Networks
Jan 16, 2024Abstract:In a spoofing attack, a malicious actor impersonates a legitimate user to access or manipulate data without authorization. The vulnerability of cryptographic security mechanisms to compromised user credentials motivates spoofing attack detection in the physical layer, which traditionally relied on channel features, such as the received signal strength (RSS) measured by spatially distributed receivers or access points. However, existing methods cannot effectively cope with the dynamic nature of channels, which change over time as a result of user mobility and other factors. To address this limitation, this work builds upon the intuition that the temporal pattern of changes in RSS features can be used to detect the presence of concurrent transmissions from multiple (possibly changing) locations, which in turn indicates the existence of an attack. Since a localization-based approach would require costly data collection and would suffer from low spatial resolution due to multipath, the proposed algorithm employs a deep neural network to construct a graph embedding of a sequence of RSS features that reflects changes in the propagation conditions. A graph neural network then classifies these embeddings to detect spoofing attacks. The effectiveness and robustness of the proposed scheme are corroborated by experiments with real-data.
Theoretical Analysis of the Radio Map Estimation Problem
Nov 07, 2023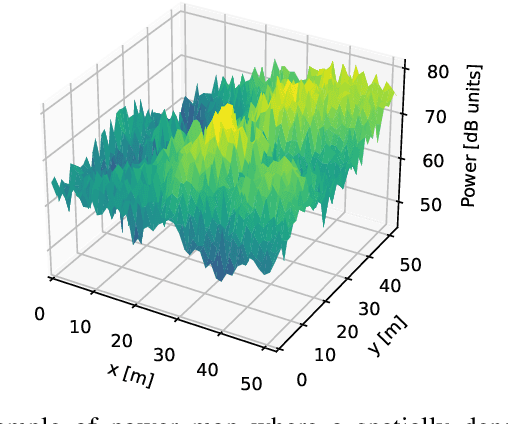

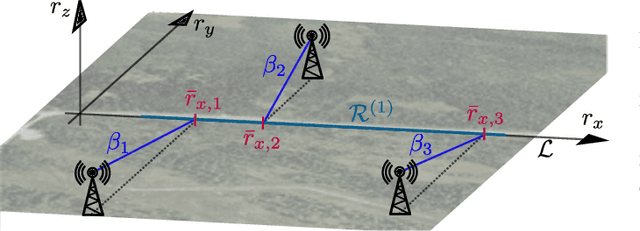
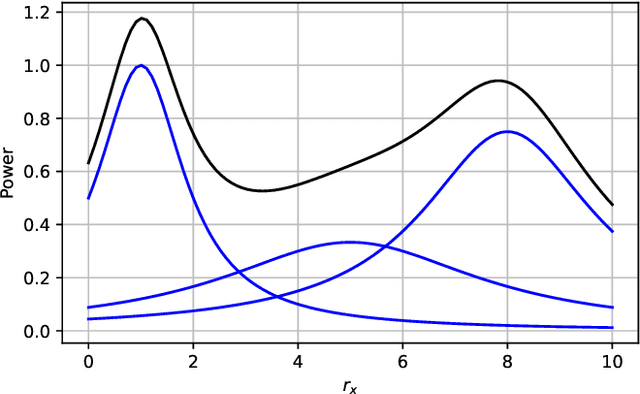
Abstract:Radio map estimation (RME) constructs representations providing radio frequency metrics, such as the received signal strength, at every location of a geographic area using a set of measurements collected at multiple positions. The resulting radio maps find a wide range of applications in wireless communications, including prediction of coverage holes, network planning, resource allocation, and path planning for mobile robots. Although a vast number of estimators have been proposed, the theoretical understanding of the RME problem has not been pursued. The present work aims at filling this gap along two directions. First, the complexity of the function space of radio maps is quantified by means of lower and upper bounds on their spatial variability, which offers valuable insight into the required spatial distribution of measurements and estimators that can be used. Second, the reconstruction error for power maps in free space is upper bounded for three simple spatial interpolators, namely zeroth-order, first-order, and sinc interpolators. In view of these bounds, the proximity coefficient, which is an increasing function of the transmitted power and a decreasing function of the distance from the transmitters to the mapped region, is proposed to quantify the complexity of the RME problem. Simple numerical experiments assess the tightness of the obtained bounds and reveal the practical trade-offs associated with the considered interpolators.
Spoofing Attack Detection in the Physical Layer with Robustness to User Movement
Oct 17, 2023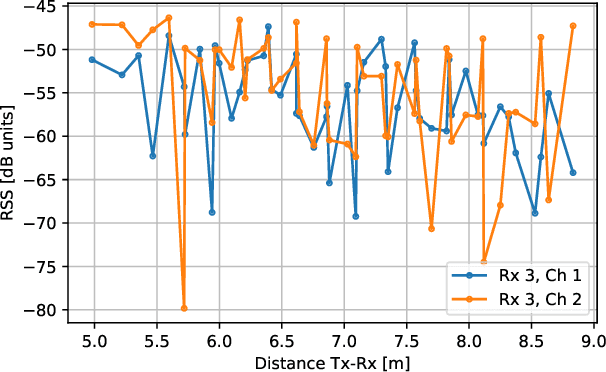
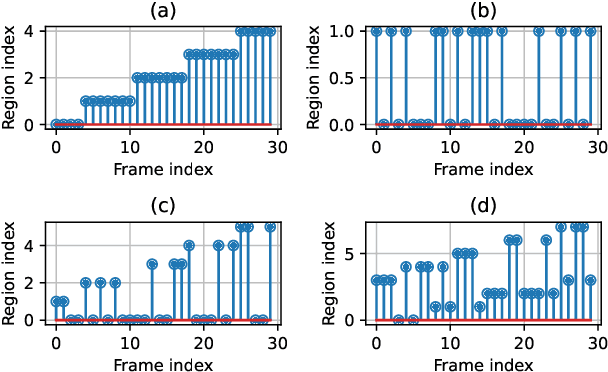
Abstract:In a spoofing attack, an attacker impersonates a legitimate user to access or modify data belonging to the latter. Typical approaches for spoofing detection in the physical layer declare an attack when a change is observed in certain channel features, such as the received signal strength (RSS) measured by spatially distributed receivers. However, since channels change over time, for example due to user movement, such approaches are impractical. To sidestep this limitation, this paper proposes a scheme that combines the decisions of a position-change detector based on a deep neural network to distinguish spoofing from movement. Building upon community detection on graphs, the sequence of received frames is partitioned into subsequences to detect concurrent transmissions from distinct locations. The scheme can be easily deployed in practice since it just involves collecting a small dataset of measurements at a few tens of locations that need not even be computed or recorded. The scheme is evaluated on real data collected for this purpose.
Radio Map Estimation in the Real-World: Empirical Validation and Analysis
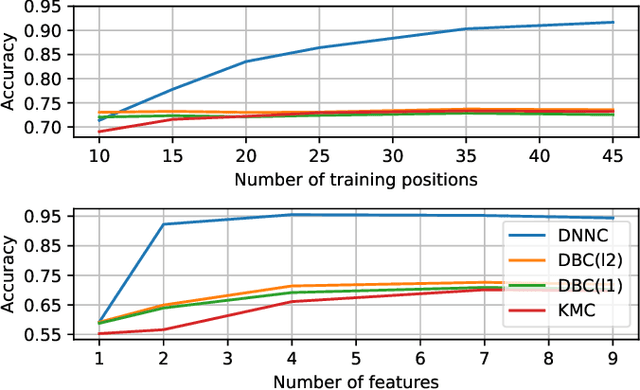
Oct 17, 2023Abstract:Radio maps quantify received signal strength or other magnitudes of the radio frequency environment at every point of a geographical region. These maps play a vital role in a large number of applications such as wireless network planning, spectrum management, and optimization of communication systems. However, empirical validation of the large number of existing radio map estimators is highly limited. To fill this gap, a large data set of measurements has been collected with an autonomous unmanned aerial vehicle (UAV) and a representative subset of these estimators were evaluated on this data. The performance-complexity trade-off and the impact of fast fading are extensively investigated. Although sophisticated estimators based on deep neural networks (DNNs) exhibit the best performance, they are seen to require large volumes of training data to offer a substantial advantage relative to more traditional schemes. A novel algorithm that blends both kinds of estimators is seen to enjoy the benefits of both, thereby suggesting the potential of exploring this research direction further.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge