Stefano Bistarelli
An Interleaving Semantics of the Timed Concurrent Language for Argumentation to Model Debates and Dialogue Games
Jun 13, 2023



Abstract:Time is a crucial factor in modelling dynamic behaviours of intelligent agents: activities have a determined temporal duration in a real-world environment, and previous actions influence agents' behaviour. In this paper, we propose a language for modelling concurrent interaction between agents that also allows the specification of temporal intervals in which particular actions occur. Such a language exploits a timed version of Abstract Argumentation Frameworks to realise a shared memory used by the agents to communicate and reason on the acceptability of their beliefs with respect to a given time interval. An interleaving model on a single processor is used for basic computation steps, with maximum parallelism for time elapsing. Following this approach, only one of the enabled agents is executed at each moment. To demonstrate the capabilities of language, we also show how it can be used to model interactions such as debates and dialogue games taking place between intelligent agents. Lastly, we present an implementation of the language that can be accessed via a web interface. Under consideration in Theory and Practice of Logic Programming (TPLP).
Block Argumentation
Jan 18, 2019Abstract:We contemplate a higher-level bipolar abstract argumentation for non-elementary arguments such as: X argues against Ys sincerity with the fact that Y has presented his argument to draw a conclusion C, by omitting other facts which would not have validated C. Argumentation involving such arguments requires us to potentially consider an argument as a coherent block of argumentation, i.e. an argument may itself be an argumentation. In this work, we formulate block argumentation as a specific instance of Dung-style bipolar abstract argumentation with the dual nature of arguments. We consider internal consistency of an argument(ation) under a set of constraints, of graphical (syntactic) and of semantic nature, and formulate acceptability semantics in relation to them. We discover that classical acceptability semantics do not in general hold good with the constraints. In particular, acceptability of unattacked arguments is not always warranted. Further, there may not be a unique minimal member in complete semantics, thus sceptic (grounded) semantics may not be its subset. To retain set-theoretically minimal semantics as a subset of complete semantics, we define semi-grounded semantics. Through comparisons, we show how the concept of block argumentation may further generalise structured argumentation.
A Preliminary Report on Probabilistic Attack Normal Form for Constellation Semantics
Sep 24, 2018
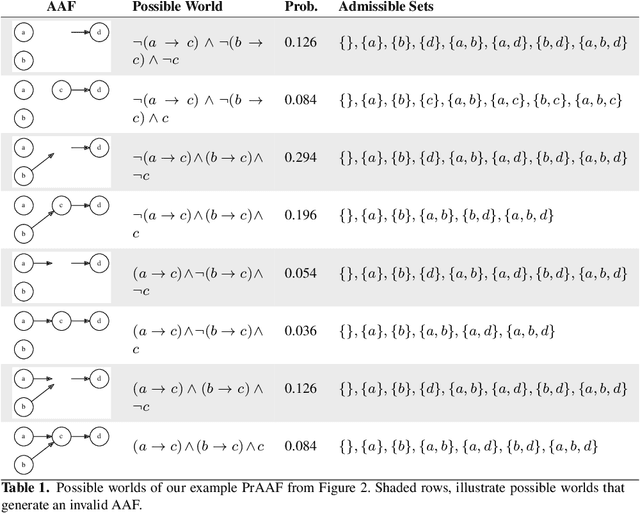
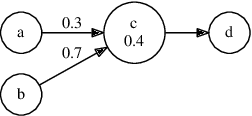
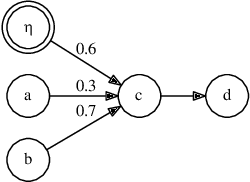
Abstract:After Dung's founding work in Abstract Argumentation Frameworks there has been a growing interest in extending the Dung's semantics in order to describe more complex or real life situations. Several of these approaches take the direction of weighted or probabilistic extensions. One of the most prominent probabilistic approaches is that of constellation Probabilistic Abstract Argumentation Frameworks from Li~et~al. In this paper, we present a normal form for constellation probabilistic abstract argumentation frameworks. Furthermore, we present a transformation from general constellation probabilistic abstract argumentation frameworks to the presented normal form. In this way we illustrate that the simpler normal form has equal representation power with the general one.
On Looking for Local Expansion Invariants in Argumentation Semantics: a Preliminary Report
Jul 30, 2018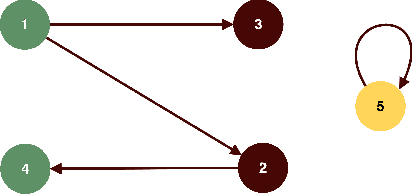
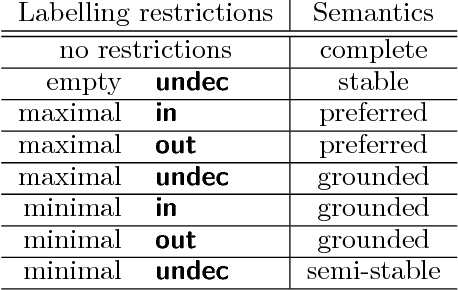
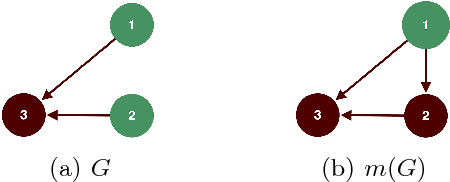
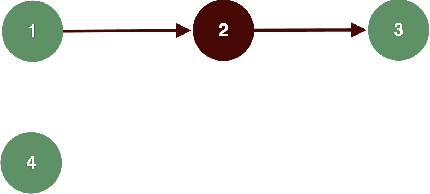
Abstract:We study invariant local expansion operators for conflict-free and admissible sets in Abstract Argumentation Frameworks (AFs). Such operators are directly applied on AFs, and are invariant with respect to a chosen "semantics" (that is w.r.t. each of the conflict free/admissible set of arguments). Accordingly, we derive a definition of robustness for AFs in terms of the number of times such operators can be applied without producing any change in the chosen semantics.
A Matrix Approach for Weighted Argumentation Frameworks: a Preliminary Report
Feb 23, 2018



Abstract:The assignment of weights to attacks in a classical Argumentation Framework allows to compute semantics by taking into account the different importance of each argument. We represent a Weighted Argumentation Framework by a non-binary matrix, and we characterize the basic extensions (such as w-admissible, w- stable, w-complete) by analysing sub-blocks of this matrix. Also, we show how to reduce the matrix into another one of smaller size, that is equivalent to the original one for the determination of extensions. Furthermore, we provide two algorithms that allow to build incrementally w-grounded and w-preferred extensions starting from a w-admissible extension.
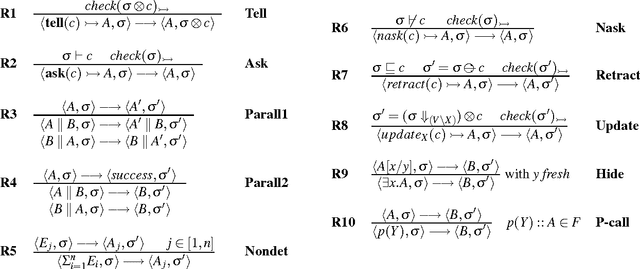
Timed Soft Concurrent Constraint Programs: An Interleaved and a Parallel Approach
Apr 22, 2014



Abstract:We propose a timed and soft extension of Concurrent Constraint Programming. The time extension is based on the hypothesis of bounded asynchrony: the computation takes a bounded period of time and is measured by a discrete global clock. Action prefixing is then considered as the syntactic marker which distinguishes a time instant from the next one. Supported by soft constraints instead of crisp ones, tell and ask agents are now equipped with a preference (or consistency) threshold which is used to determine their success or suspension. In the paper we provide a language to describe the agents behavior, together with its operational and denotational semantics, for which we also prove the compositionality and correctness properties. After presenting a semantics using maximal parallelism of actions, we also describe a version for their interleaving on a single processor (with maximal parallelism for time elapsing). Coordinating agents that need to take decisions both on preference values and time events may benefit from this language. To appear in Theory and Practice of Logic Programming (TPLP).
ConArg: a Tool to Solve Abstract Argumentation Frameworks with Constraints
Jan 16, 2013



Abstract:ConArg is a Constraint Programming-based tool that can be used to model and solve different problems related to Abstract Argumentation Frameworks (AFs). To implement this tool we have used JaCoP, a Java library that provides the user with a Finite Domain Constraint Programming paradigm. ConArg is able to randomly generate networks with small-world properties in order to find conflict-free, admissible, complete, stable grounded, preferred, semi-stable, stage and ideal extensions on such interaction graphs. We present the main features of ConArg and we report the performance in time, showing also a comparison with ASPARTIX [1], a similar tool using Answer Set Programming. The use of techniques for constraint solving can tackle the complexity of the problems presented in [2]. Moreover we suggest semiring-based soft constraints as a mean to parametrically represent and solve Weighted Argumentation Frameworks: different kinds of preference levels related to attacks, e.g., a score representing a "fuzziness", a "cost" or a probability, can be represented by choosing different instantiation of the semiring algebraic structure. The basic idea is to provide a common computational and quantitative framework.
Soft Constraints for Quality Aspects in Service Oriented Architectures
Jun 22, 2009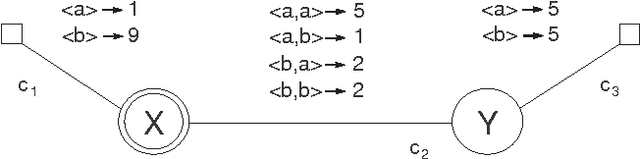
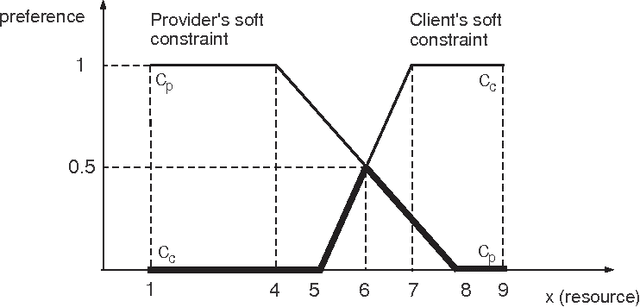
Abstract:We propose the use of Soft Constraints as a natural way to model Service Oriented Architecture. In the framework, constraints are used to model components and connectors and constraint aggregation is used to represent their interactions. The "quality of a service" is measured and considered when performing queries to service providers. Some examples consist in the levels of cost, performance and availability required by clients. In our framework, the QoS scores are represented by the softness level of the constraint and the measure of complex (web) services is computed by combining the levels of the components.
Unicast and Multicast Qos Routing with Soft Constraint Logic Programming
Apr 21, 2008



Abstract:We present a formal model to represent and solve the unicast/multicast routing problem in networks with Quality of Service (QoS) requirements. To attain this, first we translate the network adapting it to a weighted graph (unicast) or and-or graph (multicast), where the weight on a connector corresponds to the multidimensional cost of sending a packet on the related network link: each component of the weights vector represents a different QoS metric value (e.g. bandwidth, cost, delay, packet loss). The second step consists in writing this graph as a program in Soft Constraint Logic Programming (SCLP): the engine of this framework is then able to find the best paths/trees by optimizing their costs and solving the constraints imposed on them (e.g. delay < 40msec), thus finding a solution to QoS routing problems. Moreover, c-semiring structures are a convenient tool to model QoS metrics. At last, we provide an implementation of the framework over scale-free networks and we suggest how the performance can be improved.
Soft Constraint Programming to Analysing Security Protocols
Dec 14, 2003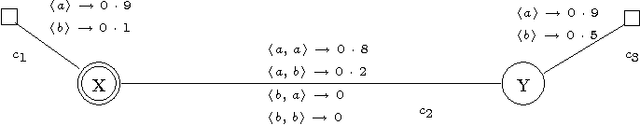

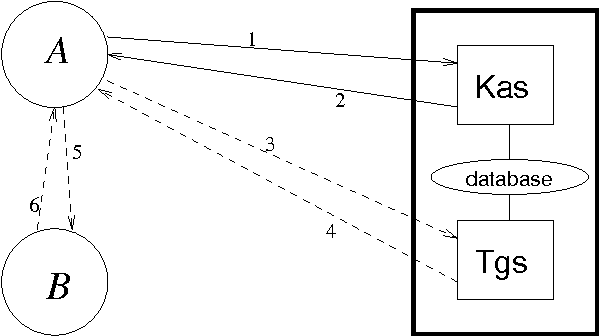
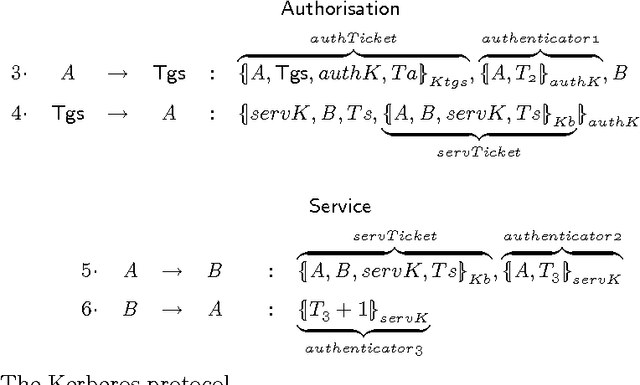
Abstract:Security protocols stipulate how the remote principals of a computer network should interact in order to obtain specific security goals. The crucial goals of confidentiality and authentication may be achieved in various forms, each of different strength. Using soft (rather than crisp) constraints, we develop a uniform formal notion for the two goals. They are no longer formalised as mere yes/no properties as in the existing literature, but gain an extra parameter, the security level. For example, different messages can enjoy different levels of confidentiality, or a principal can achieve different levels of authentication with different principals. The goals are formalised within a general framework for protocol analysis that is amenable to mechanisation by model checking. Following the application of the framework to analysing the asymmetric Needham-Schroeder protocol, we have recently discovered a new attack on that protocol as a form of retaliation by principals who have been attacked previously. Having commented on that attack, we then demonstrate the framework on a bigger, largely deployed protocol consisting of three phases, Kerberos.
* 29 pages, To appear in Theory and Practice of Logic Programming (TPLP) Paper for Special Issue (Verification and Computational Logic)
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge