Simone Raponi
Monitoring of Underwater Critical Infrastructures: the Nord Stream and Other Recent Case Studies
Feb 03, 2023

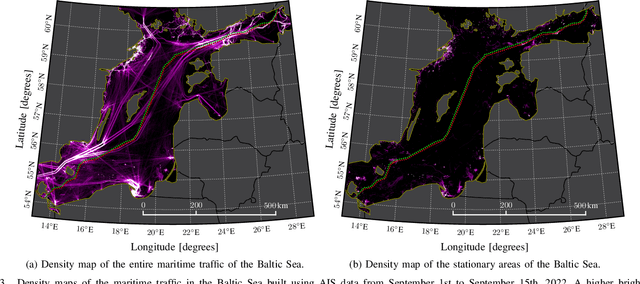

Abstract:The explosions on September 26th, 2022, which damaged the gas pipelines of Nord Stream 1 and Nord Stream 2, have highlighted the need and urgency of improving the resilience of Underwater Critical Infrastructures (UCIs). Comprising gas pipelines and power and communication cables, these connect countries worldwide and are critical for the global economy and stability. An attack targeting multiple of such infrastructures simultaneously could potentially cause significant damage and greatly affect various aspects of daily life. Due to the increasing number and continuous deployment of UCIs, existing underwater surveillance solutions, such as Autonomous Underwater Vehicles (AUVs) or Remotely Operated Vehicles (ROVs), are not adequate enough to ensure thorough monitoring. We show that the combination of information from both underwater and above-water surveillance sensors enables achieving Seabed-to-Space Situational Awareness (S3A), mainly thanks to Artificial Intelligence (AI) and Information Fusion (IF) methodologies. These are designed to process immense volumes of information, fused from a variety of sources and generated from monitoring a very large number of assets on a daily basis. The learned knowledge can be used to anticipate future behaviors, identify threats, and determine critical situations concerning UCIs. To illustrate the capabilities and importance of S3A, we consider three events that occurred in the second half of 2022: the aforementioned Nord Stream explosions, the cutoff of the underwater communication cable SHEFA-2 connecting the Shetland Islands and the UK mainland, and the suspicious activity of a large vessel in the Adriatic Sea. Specifically, we provide analyses of the available data, from Automatic Identification System (AIS) and satellite data, integrated with possible contextual information, e.g., bathymetry, weather conditions, and human intelligence.
PAST-AI: Physical-layer Authentication of Satellite Transmitters via Deep Learning
Oct 12, 2020



Abstract:Physical-layer security is regaining traction in the research community, due to the performance boost introduced by deep learning classification algorithms. This is particularly true for sender authentication in wireless communications via radio fingerprinting. However, previous research efforts mainly focused on terrestrial wireless devices while, to the best of our knowledge, none of the previous work took into consideration satellite transmitters. The satellite scenario is generally challenging because, among others, satellite radio transducers feature non-standard electronics (usually aged and specifically designed for harsh conditions). Moreover, the fingerprinting task is specifically difficult for Low-Earth Orbit (LEO) satellites (like the ones we focus in this paper) since they orbit at about 800Km from the Earth, at a speed of around 25,000Km/h, thus making the receiver experiencing a down-link with unique attenuation and fading characteristics. In this paper, we propose PAST-AI, a methodology tailored to authenticate LEO satellites through fingerprinting of their IQ samples, using advanced AI solutions. Our methodology is tested on real data -- more than 100M I/Q samples -- collected from an extensive measurements campaign on the IRIDIUM LEO satellites constellation, lasting 589 hours. Results are striking: we prove that Convolutional Neural Networks (CNN) and autoencoders (if properly calibrated) can be successfully adopted to authenticate the satellite transducers, with an accuracy spanning between 0.8 and 1, depending on prior assumptions. The proposed methodology, the achieved results, and the provided insights, other than being interesting on their own, when associated to the dataset that we made publicly available, will also pave the way for future research in the area.
Sound of Guns: Digital Forensics of Gun Audio Samples meets Artificial Intelligence
Apr 15, 2020



Abstract:Classifying a weapon based on its muzzle blast is a challenging task that has significant applications in various security and military fields. Most of the existing works rely on ad-hoc deployment of spatially diverse microphone sensors to capture multiple replicas of the same gunshot, which enables accurate detection and identification of the acoustic source. However, carefully controlled setups are difficult to obtain in scenarios such as crime scene forensics, making the aforementioned techniques inapplicable and impractical. We introduce a novel technique that requires zero knowledge about the recording setup and is completely agnostic to the relative positions of both the microphone and shooter. Our solution can identify the category, caliber, and model of the gun, reaching over 90% accuracy on a dataset composed of 3655 samples that are extracted from YouTube videos. Our results demonstrate the effectiveness and efficiency of applying Convolutional Neural Network (CNN) in gunshot classification eliminating the need for an ad-hoc setup while significantly improving the classification performance.
Crypto Mining Makes Noise
Oct 21, 2019



Abstract:A new cybersecurity attack (cryptojacking) is emerging, in both the literature and in the wild, where an adversary illicitly runs Crypto-clients software over the devices of unaware users. This attack has been proved to be very effective given the simplicity of running a Crypto-client into a target device, e.g., by means of web-based Java scripting. In this scenario, we propose Crypto-Aegis, a solution to detect and identify Crypto-clients network traffic--even when it is VPN-ed. In detail, our contributions are the following: (i) We identify and model a new type of attack, i.e., the sponge-attack, being a generalization of cryptojacking; (ii) We provide a detailed analysis of real network traffic generated by 3 major cryptocurrencies; (iii) We investigate how VPN tunneling shapes the network traffic generated by Crypto-clients by considering two major VPNbrands; (iv) We propose Crypto-Aegis, a Machine Learning (ML) based framework that builds over the previous steps to detect crypto-mining activities; and, finally, (v) We compare our results against competing solutions in the literature. Evidence from of our experimental campaign show the exceptional quality and viability of our solution--Crypto-Aegis achieves an F1-score of 0.96 and an AUC of 0.99. Given the extent and novelty of the addressed threat we believe that our approach and our results, other than being interesting on their own, also pave the way for further research in this area.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge