Seok Bin Son
Entropy-Aware Similarity for Balanced Clustering: A Case Study with Melanoma Detection
May 11, 2023Abstract:Clustering data is an unsupervised learning approach that aims to divide a set of data points into multiple groups. It is a crucial yet demanding subject in machine learning and data mining. Its successful applications span various fields. However, conventional clustering techniques necessitate the consideration of balance significance in specific applications. Therefore, this paper addresses the challenge of imbalanced clustering problems and presents a new method for balanced clustering by utilizing entropy-aware similarity, which can be defined as the degree of balances. We have coined the term, entropy-aware similarity for balanced clustering (EASB), which maximizes balance during clustering by complementary clustering of unbalanced data and incorporating entropy in a novel similarity formula that accounts for both angular differences and distances. The effectiveness of the proposed approach is evaluated on actual melanoma medial data, specifically the International Skin Imaging Collaboration (ISIC) 2019 and 2020 challenge datasets, to demonstrate how it can successfully cluster the data while preserving balance. Lastly, we can confirm that the proposed method exhibited outstanding performance in detecting melanoma, comparing to classical methods.
Spatio-Temporal Attack Course-of-Action (COA) Search Learning for Scalable and Time-Varying Networks
Sep 02, 2022



Abstract:One of the key topics in network security research is the autonomous COA (Couse-of-Action) attack search method. Traditional COA attack search methods that passively search for attacks can be difficult, especially as the network gets bigger. To address these issues, new autonomous COA techniques are being developed, and among them, an intelligent spatial algorithm is designed in this paper for efficient operations in scalable networks. On top of the spatial search, a Monte-Carlo (MC)- based temporal approach is additionally considered for taking care of time-varying network behaviors. Therefore, we propose a spatio-temporal attack COA search algorithm for scalable and time-varying networks.
Tutorial on Course-of-Action Attack Search Methods in Computer Networks
May 27, 2022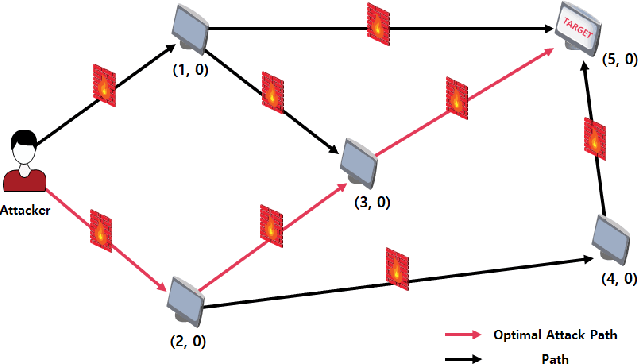

Abstract:In the literature of modern network security research, deriving effective and efficient course-of-action (COA) attach search methods are of interests in industry and academia. As the network size grows, the traditional COA attack search methods can suffer from the limitations to computing and communication resources. Therefore, various methods have been developed to solve these problems, and reinforcement learning (RL)-based intelligent algorithms are one of the most effective solutions. Therefore, we review the RL-based COA attack search methods for network attack scenarios in terms of the trends and their contrib
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge