Nur Imtiazul Haque
A Novel Framework for Threat Analysis of Machine Learning-based Smart Healthcare Systems
Mar 05, 2021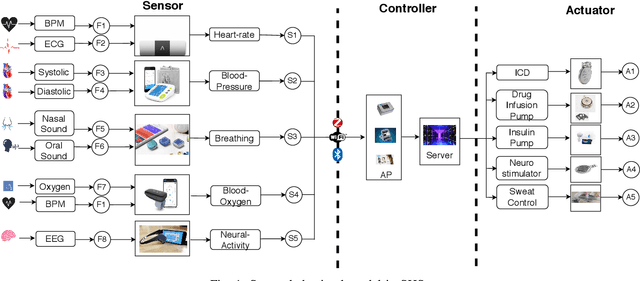
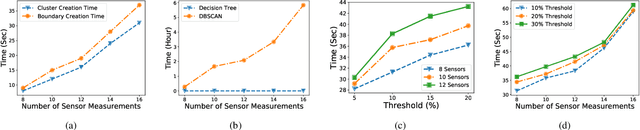
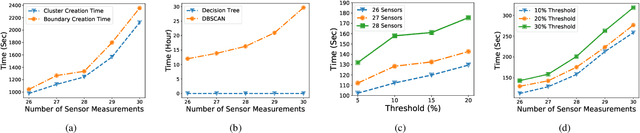
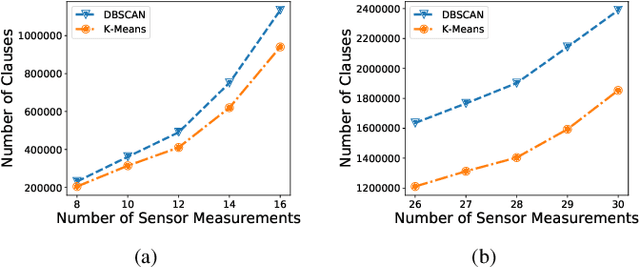
Abstract:Smart healthcare systems (SHSs) are providing fast and efficient disease treatment leveraging wireless body sensor networks (WBSNs) and implantable medical devices (IMDs)-based internet of medical things (IoMT). In addition, IoMT-based SHSs are enabling automated medication, allowing communication among myriad healthcare sensor devices. However, adversaries can launch various attacks on the communication network and the hardware/firmware to introduce false data or cause data unavailability to the automatic medication system endangering the patient's life. In this paper, we propose SHChecker, a novel threat analysis framework that integrates machine learning and formal analysis capabilities to identify potential attacks and corresponding effects on an IoMT-based SHS. Our framework can provide us with all potential attack vectors, each representing a set of sensor measurements to be altered, for an SHS given a specific set of attack attributes, allowing us to realize the system's resiliency, thus the insight to enhance the robustness of the model. We implement SHChecker on a synthetic and a real dataset, which affirms that our framework can reveal potential attack vectors in an IoMT system. This is a novel effort to formally analyze supervised and unsupervised machine learning models for black-box SHS threat analysis.
Adversarial Attacks to Machine Learning-Based Smart Healthcare Systems
Oct 07, 2020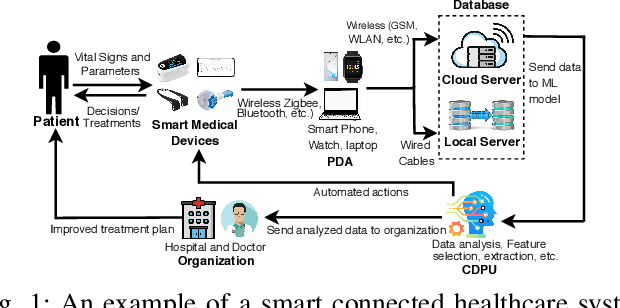
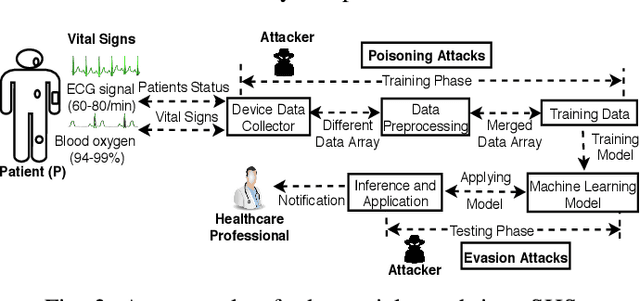
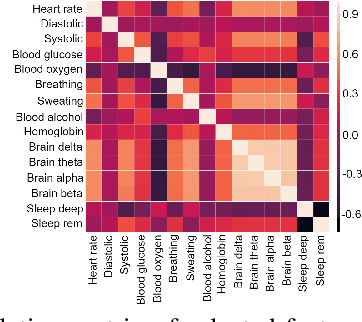
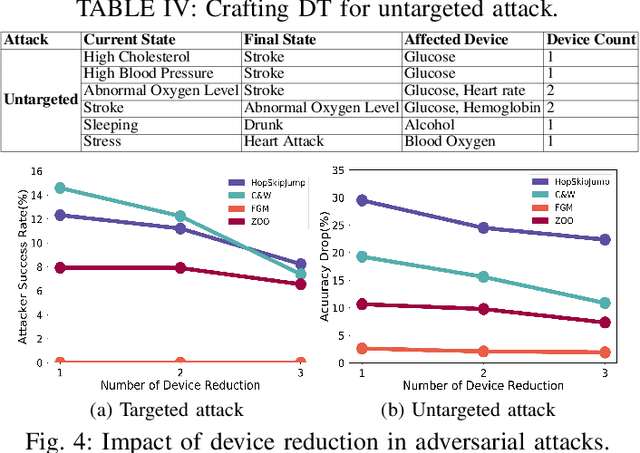
Abstract:The increasing availability of healthcare data requires accurate analysis of disease diagnosis, progression, and realtime monitoring to provide improved treatments to the patients. In this context, Machine Learning (ML) models are used to extract valuable features and insights from high-dimensional and heterogeneous healthcare data to detect different diseases and patient activities in a Smart Healthcare System (SHS). However, recent researches show that ML models used in different application domains are vulnerable to adversarial attacks. In this paper, we introduce a new type of adversarial attacks to exploit the ML classifiers used in a SHS. We consider an adversary who has partial knowledge of data distribution, SHS model, and ML algorithm to perform both targeted and untargeted attacks. Employing these adversarial capabilities, we manipulate medical device readings to alter patient status (disease-affected, normal condition, activities, etc.) in the outcome of the SHS. Our attack utilizes five different adversarial ML algorithms (HopSkipJump, Fast Gradient Method, Crafting Decision Tree, Carlini & Wagner, Zeroth Order Optimization) to perform different malicious activities (e.g., data poisoning, misclassify outputs, etc.) on a SHS. Moreover, based on the training and testing phase capabilities of an adversary, we perform white box and black box attacks on a SHS. We evaluate the performance of our work in different SHS settings and medical devices. Our extensive evaluation shows that our proposed adversarial attack can significantly degrade the performance of a ML-based SHS in detecting diseases and normal activities of the patients correctly, which eventually leads to erroneous treatment.
Machine Learning in Generation, Detection, and Mitigation of Cyberattacks in Smart Grid: A Survey
Sep 01, 2020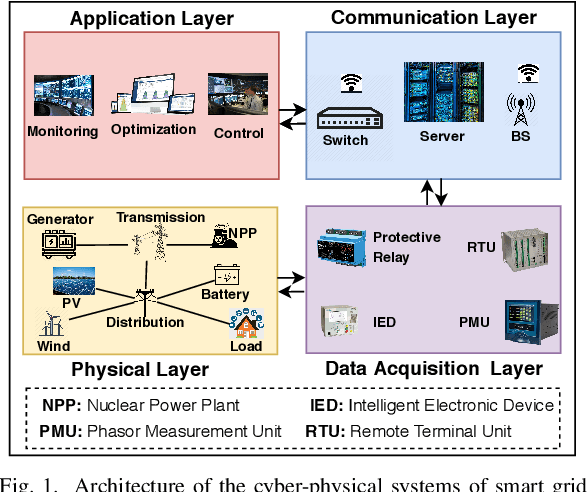
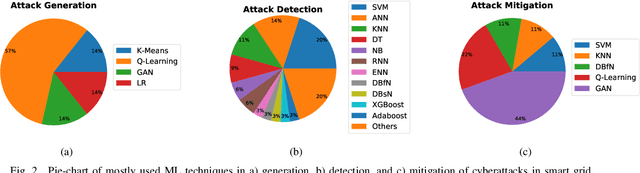
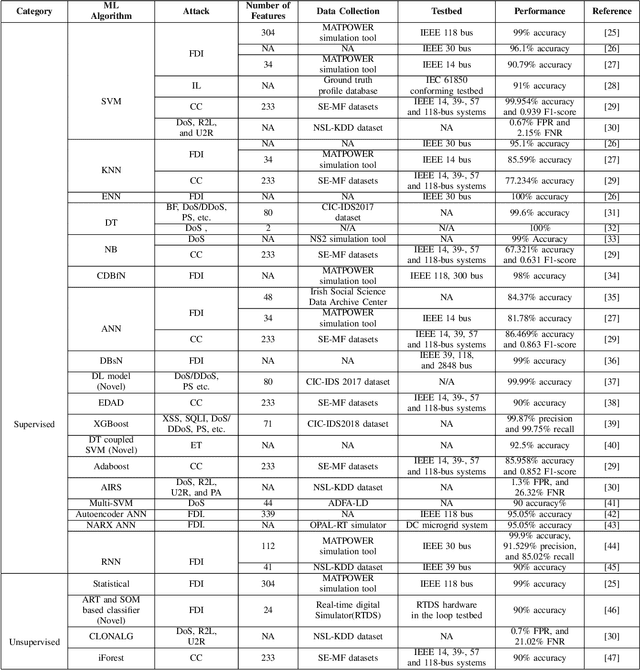
Abstract:Smart grid (SG) is a complex cyber-physical system that utilizes modern cyber and physical equipment to run at an optimal operating point. Cyberattacks are the principal threats confronting the usage and advancement of the state-of-the-art systems. The advancement of SG has added a wide range of technologies, equipment, and tools to make the system more reliable, efficient, and cost-effective. Despite attaining these goals, the threat space for the adversarial attacks has also been expanded because of the extensive implementation of the cyber networks. Due to the promising computational and reasoning capability, machine learning (ML) is being used to exploit and defend the cyberattacks in SG by the attackers and system operators, respectively. In this paper, we perform a comprehensive summary of cyberattacks generation, detection, and mitigation schemes by reviewing state-of-the-art research in the SG domain. Additionally, we have summarized the current research in a structured way using tabular format. We also present the shortcomings of the existing works and possible future research direction based on our investigation.
G-IDS: Generative Adversarial Networks Assisted Intrusion Detection System
Jun 01, 2020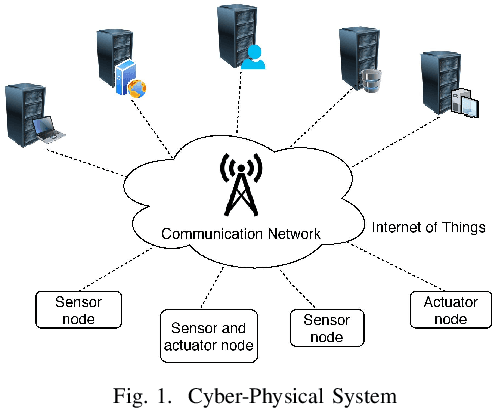
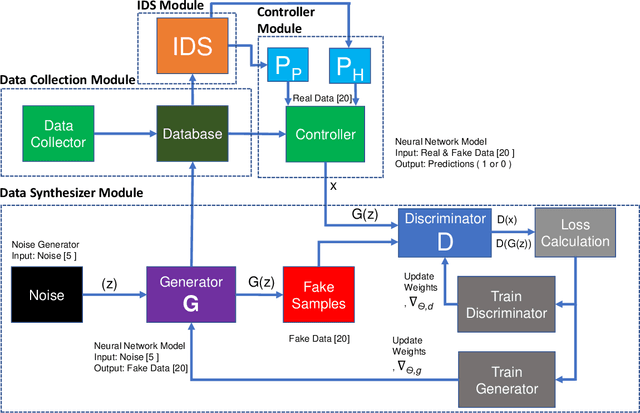
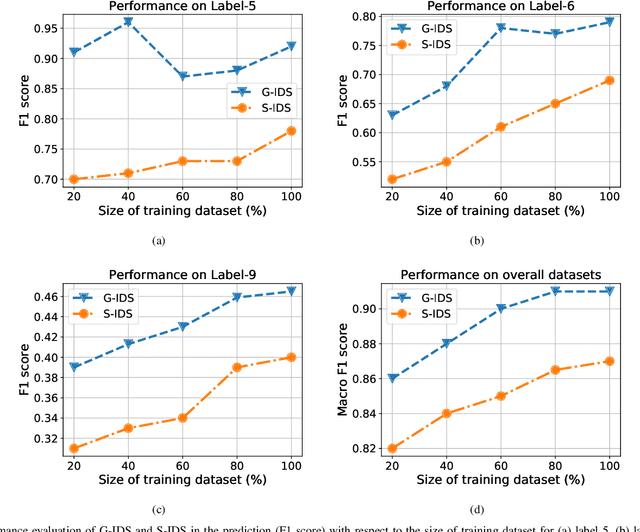
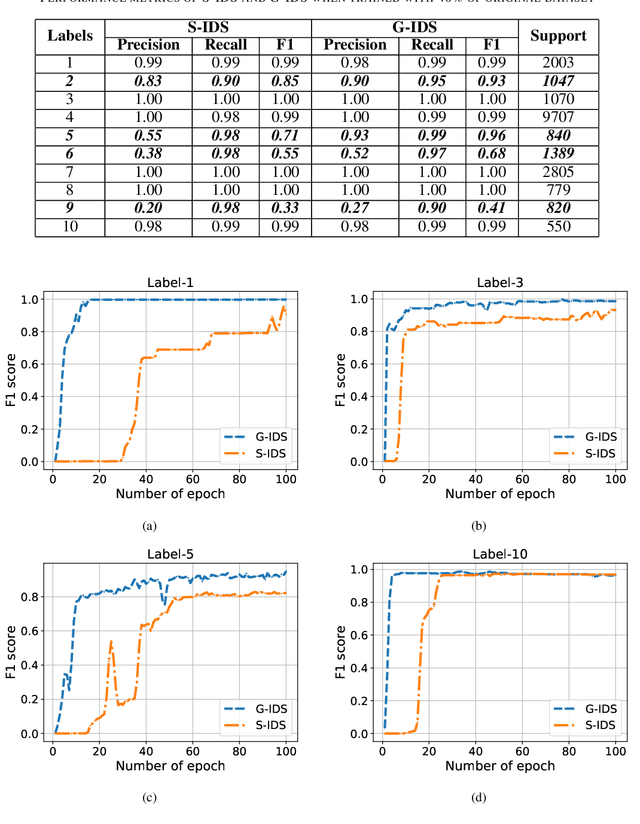
Abstract:The boundaries of cyber-physical systems (CPS) and the Internet of Things (IoT) are converging together day by day to introduce a common platform on hybrid systems. Moreover, the combination of artificial intelligence (AI) with CPS creates a new dimension of technological advancement. All these connectivity and dependability are creating massive space for the attackers to launch cyber attacks. To defend against these attacks, intrusion detection system (IDS) has been widely used. However, emerging CPS technologies suffer from imbalanced and missing sample data, which makes the training of IDS difficult. In this paper, we propose a generative adversarial network (GAN) based intrusion detection system (G-IDS), where GAN generates synthetic samples, and IDS gets trained on them along with the original ones. G-IDS also fixes the difficulties of imbalanced or missing data problems. We model a network security dataset for an emerging CPS using NSL KDD-99 dataset and evaluate our proposed model's performance using different metrics. We find that our proposed G-IDS model performs much better in attack detection and model stabilization during the training process than a standalone IDS.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge