Menglu Li
Millimeter-Wave Position Sensing Using Reconfigurable Intelligent Surfaces: Positioning Error Bound and Phase Shift Configuration
Aug 09, 2025



Abstract:Millimeter-wave (mmWave) positioning has emerged as a promising technology for next-generation intelligent systems. The advent of reconfigurable intelligent surfaces (RISs) has revolutionized high-precision mmWave localization by enabling dynamic manipulation of wireless propagation environments. This paper investigates a three-dimensional (3D) multi-input single-output (MISO) mmWave positioning system assisted by multiple RISs. We introduce a measurement framework incorporating sequential RIS activation and directional beamforming to fully exploit virtual line-of-sight (VLoS) paths. The theoretical performance limits are rigorously analyzed through derivation of the Fisher information and subsequent positioning error bound (PEB). To minimize the PEB, two distinct optimization approaches are proposed for continuous and discrete phase shift configurations of RISs. For continuous phase shifts, a Riemannian manifold-based optimization algorithm is proposed. For discrete phase shifts, a heuristic algorithm incorporating the grey wolf optimizer is proposed. Extensive numerical simulations demonstrate the effectiveness of the proposed algorithms in reducing the PEB and validate the improvement in positioning accuracy achieved by multiple RISs.
Interpretable Temporal Class Activation Representation for Audio Spoofing Detection
Jun 16, 2024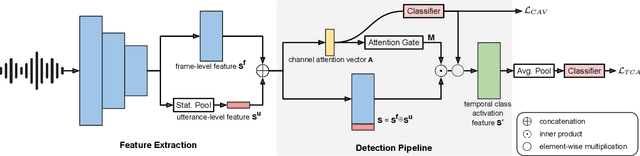
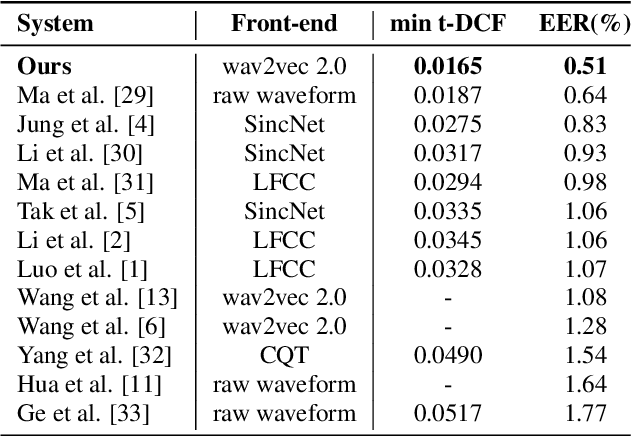
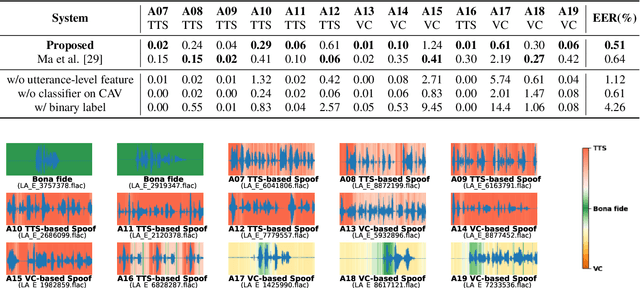
Abstract:Explaining the decisions made by audio spoofing detection models is crucial for fostering trust in detection outcomes. However, current research on the interpretability of detection models is limited to applying XAI tools to post-trained models. In this paper, we utilize the wav2vec 2.0 model and attentive utterance-level features to integrate interpretability directly into the model's architecture, thereby enhancing transparency of the decision-making process. Specifically, we propose a class activation representation to localize the discriminative frames contributing to detection. Furthermore, we demonstrate that multi-label training based on spoofing types, rather than binary labels as bonafide and spoofed, enables the model to learn distinct characteristics of different attacks, significantly improving detection performance. Our model achieves state-of-the-art results, with an EER of 0.51% and a min t-DCF of 0.0165 on the ASVspoof2019-LA set.
Audio Anti-Spoofing Detection: A Survey
Apr 22, 2024



Abstract:The availability of smart devices leads to an exponential increase in multimedia content. However, the rapid advancements in deep learning have given rise to sophisticated algorithms capable of manipulating or creating multimedia fake content, known as Deepfake. Audio Deepfakes pose a significant threat by producing highly realistic voices, thus facilitating the spread of misinformation. To address this issue, numerous audio anti-spoofing detection challenges have been organized to foster the development of anti-spoofing countermeasures. This survey paper presents a comprehensive review of every component within the detection pipeline, including algorithm architectures, optimization techniques, application generalizability, evaluation metrics, performance comparisons, available datasets, and open-source availability. For each aspect, we conduct a systematic evaluation of the recent advancements, along with discussions on existing challenges. Additionally, we also explore emerging research topics on audio anti-spoofing, including partial spoofing detection, cross-dataset evaluation, and adversarial attack defence, while proposing some promising research directions for future work. This survey paper not only identifies the current state-of-the-art to establish strong baselines for future experiments but also guides future researchers on a clear path for understanding and enhancing the audio anti-spoofing detection mechanisms.
Exploring the Use of Data-Driven Approaches for Anomaly Detection in the Internet of Things Environment
Dec 31, 2022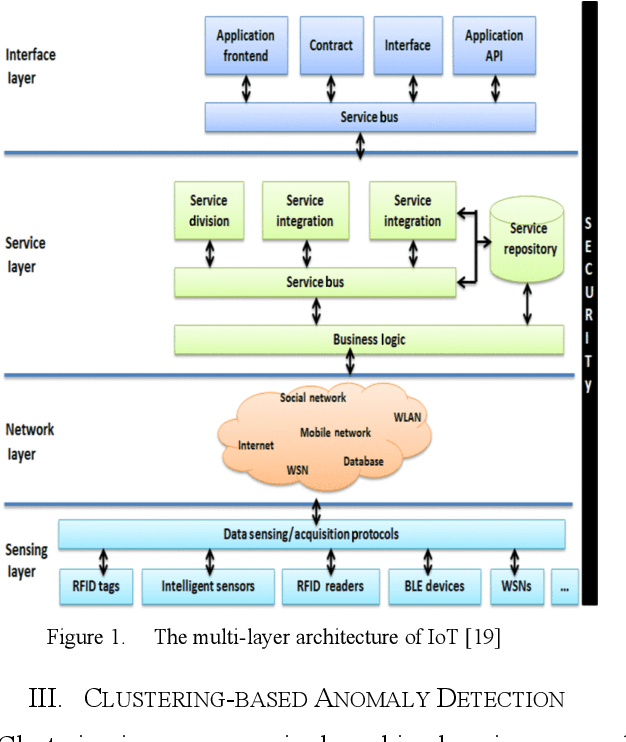
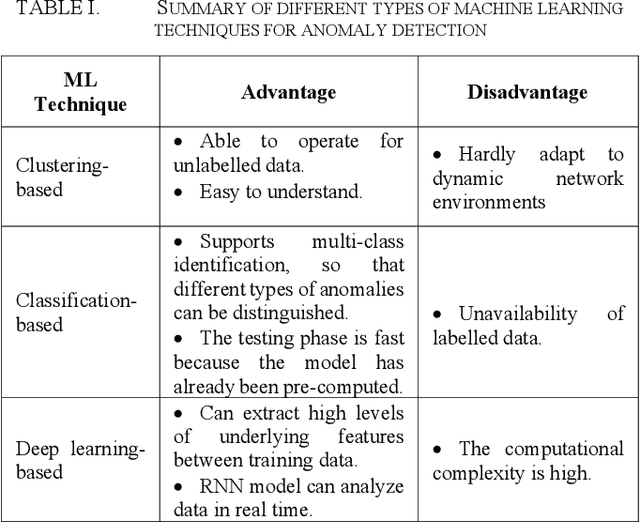
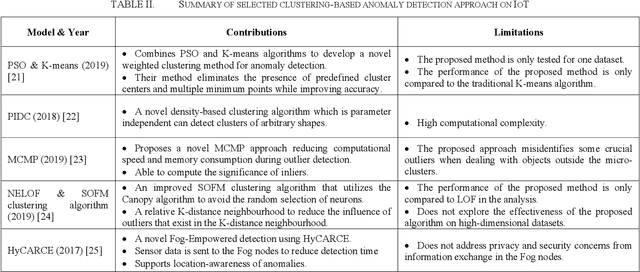
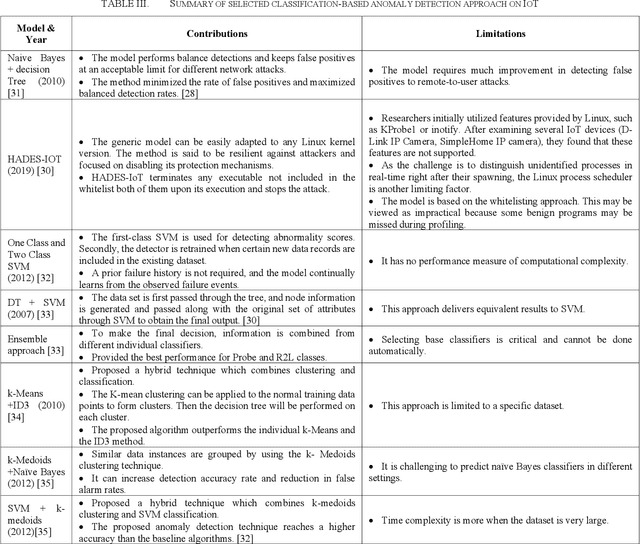
Abstract:The Internet of Things (IoT) is a system that connects physical computing devices, sensors, software, and other technologies. Data can be collected, transferred, and exchanged with other devices over the network without requiring human interactions. One challenge the development of IoT faces is the existence of anomaly data in the network. Therefore, research on anomaly detection in the IoT environment has become popular and necessary in recent years. This survey provides an overview to understand the current progress of the different anomaly detection algorithms and how they can be applied in the context of the Internet of Things. In this survey, we categorize the widely used anomaly detection machine learning and deep learning techniques in IoT into three types: clustering-based, classification-based, and deep learning based. For each category, we introduce some state-of-the-art anomaly detection methods and evaluate the advantages and limitations of each technique.
LSBN: A Large-Scale Bayesian Structure Learning Framework for Model Averaging
Oct 18, 2012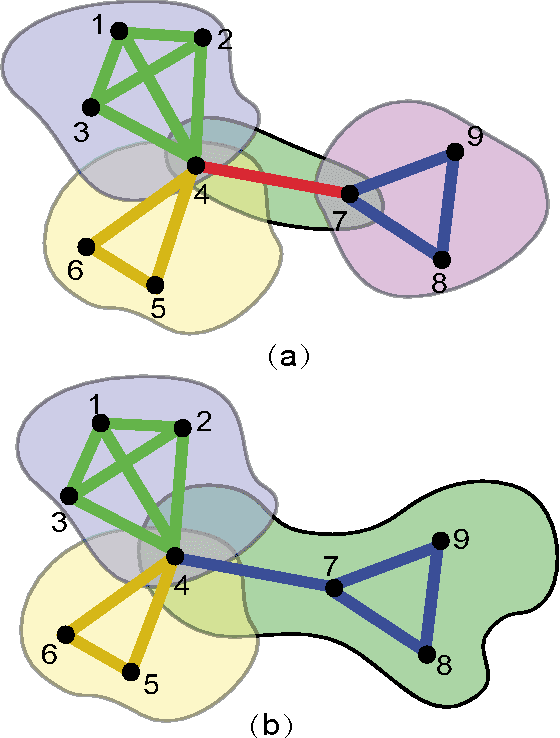
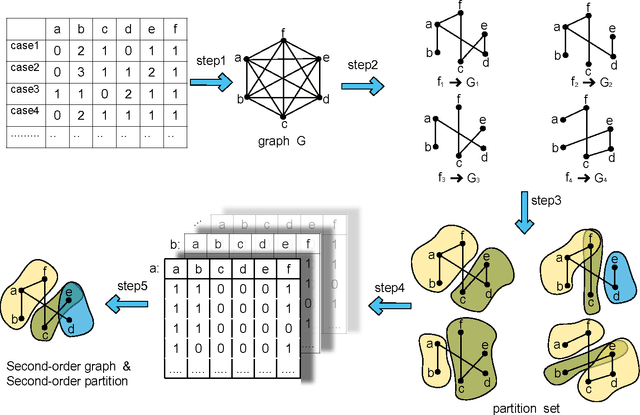
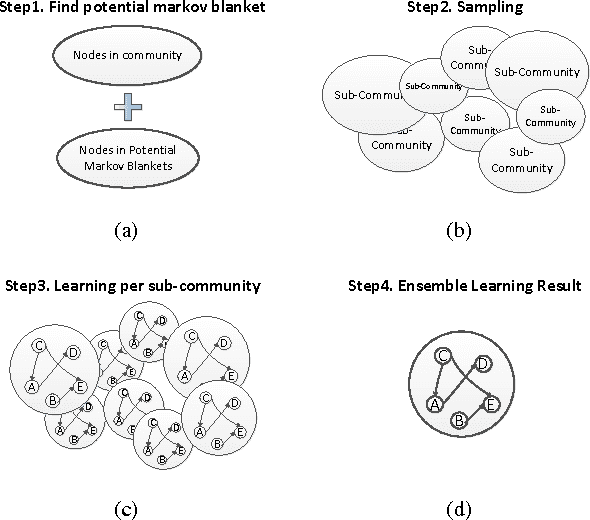
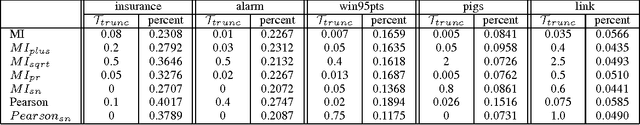
Abstract:The motivation for this paper is to apply Bayesian structure learning using Model Averaging in large-scale networks. Currently, Bayesian model averaging algorithm is applicable to networks with only tens of variables, restrained by its super-exponential complexity. We present a novel framework, called LSBN(Large-Scale Bayesian Network), making it possible to handle networks with infinite size by following the principle of divide-and-conquer. The method of LSBN comprises three steps. In general, LSBN first performs the partition by using a second-order partition strategy, which achieves more robust results. LSBN conducts sampling and structure learning within each overlapping community after the community is isolated from other variables by Markov Blanket. Finally LSBN employs an efficient algorithm, to merge structures of overlapping communities into a whole. In comparison with other four state-of-art large-scale network structure learning algorithms such as ARACNE, PC, Greedy Search and MMHC, LSBN shows comparable results in five common benchmark datasets, evaluated by precision, recall and f-score. What's more, LSBN makes it possible to learn large-scale Bayesian structure by Model Averaging which used to be intractable. In summary, LSBN provides an scalable and parallel framework for the reconstruction of network structures. Besides, the complete information of overlapping communities serves as the byproduct, which could be used to mine meaningful clusters in biological networks, such as protein-protein-interaction network or gene regulatory network, as well as in social network.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge